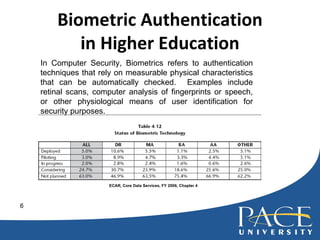
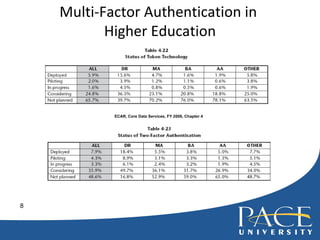
The document discusses authentication practices for online systems at Pace University. It provides an overview of authentication methods ranging from no authentication to multi-factor authentication. It also summarizes Pace's current complex password rules and recommendations for improving authentication, which include assigning risk categories to users and enforcing more frequent password changes for high-risk users. The document also discusses the use of biometrics and multi-factor authentication at other universities.








![Questions? More information is available from the Division of Information Technology: phone: 914 – 773 - 3648 via web: http:// doithelpdesk.pace.edu [email_address] , 914-923-2658](https://image.slidesharecdn.com/recommendation-for-improving-authentication-for-our-online-systems-at-pace-v20-1233004523650810-3/85/Recommendation-For-Improving-Authentication-For-Our-Online-Systems-At-Pace-V2-0-11-320.jpg)