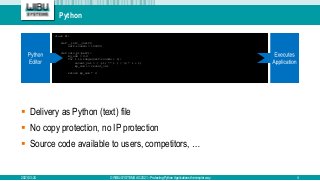
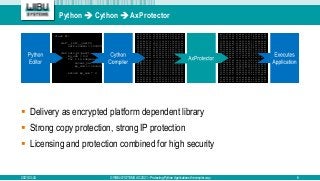
The document discusses the AxProtector Python, which provides a high-security solution for protecting Python applications with simplified integration for developers. It emphasizes on modular licenses and strong encryption capabilities while retaining the option for a classical method through Cython. The presentation highlights the advantages of using AxProtector, including enhanced IP protection, licensing models, and platform independence.