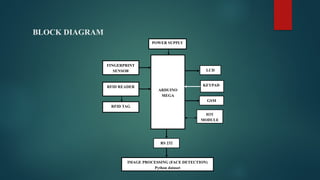
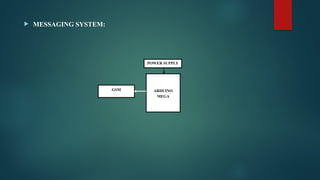
The document discusses the development of a four-level protection voting machine that utilizes biometric identification and RFID technology to enhance voting security and accuracy. It integrates deep learning algorithms for voter verification and aims to eliminate issues related to false voting and unauthorized access. The system is designed to modernize conventional voting methods, ensuring a more secure and reliable electoral experience.




![LITERATURE SURVEY
Title 1: Design and Implementation of Arduino Based Voting Machine
Authors: Santosh Kumar Shaw, Sashank Poddar, Vivek Singh, Sudip Dogra
Year: 2018
Description:
India being the largest democracy faces a lot of issues during elections. Lot of controversies are
reported about voting system, voting machines, authentication of voting, corruptions during
elections etc [1]. In our paper we have described a secured system that can eliminate such
controversies involving elections in our country. In our present work we have developed a
prototype and tested successfully an Arduino UNO based Aadhar facilitated electronic voting
machine possessing a Two-Tier fingerprint security. The main purpose of this system is to give a
straight and fair elections and to curb all other factors that affect it, this goal has been achieved by
providing dual verification of the voters based on their fingerprint and unique id. In this System
all the relevant information are taken from the voters and are stored in the database, then they are
provided with unique ID. The process of verification involves matching of this id and fingerprint
from the database. This is a faster and more secured way of holding elections. Our system is
secured, reliable and also cost- effective.](https://image.slidesharecdn.com/itrfid06ppt-240913103031-ccd1f1cf/85/project-_-for-level-protected-voting-machine_PPT-pptx-7-320.jpg)













![REFERENCES OR BIBLIOGRAPHY:
[1] Z. Zheng, S. Xie, H. Dai, X. Chen, and H. Wang, “An overview of blockchain technology:
Architecture, consensus, and future trends,” in 2017 IEEE international congress on big data (BigData
congress). IEEE, 2017, pp. 557–564.
[2] G.-T. Nguyen and K. Kim, “A survey about consensus algorithms used in blockchain.” Journal of
Information processing systems, vol. 14, no. 1, 2018.
[3] S. Bano, A. Sonnino, M. Al-Bassam, S. Azouvi, P. McCorry, S. Meiklejohn, and G. Danezis,
“Sok: Consensus in the age of blockchains,” in Proceedings of the 1st ACM Conference on Advances
in Financial Technologies, 2019, pp. 183–198. [4] S. Nakamoto and A. Bitcoin, “A peer-to-peer
electronic cash system,” Bitcoin.–URL: https://bitcoin. org/bitcoin. pdf, vol. 4, 2008.
[5] A. M. Antonopoulos, Mastering Bitcoin: Programming the open blockchain. ” O’Reilly Media,
Inc.”, 2017.](https://image.slidesharecdn.com/itrfid06ppt-240913103031-ccd1f1cf/85/project-_-for-level-protected-voting-machine_PPT-pptx-27-320.jpg)
![ [6] V. Gramoli, “From blockchain consensus back to byzantine consensus,” Future Generation
Computer Systems, vol. 107, pp. 760–769, 2020.
[7] M. Castro, B. Liskov et al., “Practical byzantine fault tolerance,” in OSDI, vol. 99, no. 1999, 1999,
pp. 173–186.
[8] E. Buchman, “Tendermint: Byzantine fault tolerance in the age of blockchains,” Ph.D. dissertation,
2016.
[9] G. Wood et al., “Ethereum: A secure decentralised generalised transaction ledger,” Ethereum project
yellow paper, vol. 151, no. 2014, pp. 1–32, 2014.
[10] D. Schwartz, N. Youngs, A. Britto et al., “The ripple protocol consensus algorithm,” Ripple Labs
Inc White Paper, vol. 5, no. 8, 2014.](https://image.slidesharecdn.com/itrfid06ppt-240913103031-ccd1f1cf/85/project-_-for-level-protected-voting-machine_PPT-pptx-28-320.jpg)