Problem mapping example
•Download as PPTX, PDF•
0 likes•892 views
Dit is een beschrijving
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (6)
Top 10 proposals engineer interview questions and answers

Top 10 proposals engineer interview questions and answers
Research work on Green Human Resource practices & Organization's Performance.

Research work on Green Human Resource practices & Organization's Performance.
Viewers also liked
Viewers also liked (10)
Wolstencroft the Bear by Karen Lewis - Illustrated by Michael S. 

Wolstencroft the Bear by Karen Lewis - Illustrated by Michael S.
32 Ways a Digital Marketing Consultant Can Help Grow Your Business

32 Ways a Digital Marketing Consultant Can Help Grow Your Business
Similar to Problem mapping example
Similar to Problem mapping example (20)
Stop hiding behind your privacy policy: build consumer trust (ADM.be, 2015)

Stop hiding behind your privacy policy: build consumer trust (ADM.be, 2015)
Banning Whining, Avoiding Cyber Wolves, and Creating Warrior

Banning Whining, Avoiding Cyber Wolves, and Creating Warrior
An empirical study on factors influencing consumers’ trust in e commerce

An empirical study on factors influencing consumers’ trust in e commerce
An empirical study on factors influencing consumers’ trust in e commerce

An empirical study on factors influencing consumers’ trust in e commerce
An empirical study on factors influencing consumers’ trust in e commerce

An empirical study on factors influencing consumers’ trust in e commerce
Right-Sizing the Security and Information Assurance for Companies, a Core-ver...

Right-Sizing the Security and Information Assurance for Companies, a Core-ver...
Discussing Cyber Risk Coverage With Your Commercial Clients by Steve Robinson...

Discussing Cyber Risk Coverage With Your Commercial Clients by Steve Robinson...
PSFK Presents the Future of Digital Safety & Security

PSFK Presents the Future of Digital Safety & Security
Портфель решений TNS в области Innovation & Product Development

Портфель решений TNS в области Innovation & Product Development
Yours Anecdotally: Developing a Cybersecurity Problem Space

Yours Anecdotally: Developing a Cybersecurity Problem Space
Hidden security and privacy consequences around mobility (Infosec 2013)

Hidden security and privacy consequences around mobility (Infosec 2013)
Security Awareness Training for Community Colleges 2009

Security Awareness Training for Community Colleges 2009
Recently uploaded
Nepali Escort Girl Kakori \ 9548273370 Indian Call Girls Service Lucknow ₹,9517

Nepali Escort Girl Kakori \ 9548273370 Indian Call Girls Service Lucknow ₹,9517Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Recently uploaded (20)
Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...

Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...
Socio-economic-Impact-of-business-consumers-suppliers-and.pptx

Socio-economic-Impact-of-business-consumers-suppliers-and.pptx
The Coffee Bean & Tea Leaf(CBTL), Business strategy case study

The Coffee Bean & Tea Leaf(CBTL), Business strategy case study
Russian Faridabad Call Girls(Badarpur) : ☎ 8168257667, @4999

Russian Faridabad Call Girls(Badarpur) : ☎ 8168257667, @4999
Nepali Escort Girl Kakori \ 9548273370 Indian Call Girls Service Lucknow ₹,9517

Nepali Escort Girl Kakori \ 9548273370 Indian Call Girls Service Lucknow ₹,9517
Insurers' journeys to build a mastery in the IoT usage

Insurers' journeys to build a mastery in the IoT usage
The CMO Survey - Highlights and Insights Report - Spring 2024

The CMO Survey - Highlights and Insights Report - Spring 2024
Call Girls in Gomti Nagar - 7388211116 - With room Service

Call Girls in Gomti Nagar - 7388211116 - With room Service
Tech Startup Growth Hacking 101 - Basics on Growth Marketing

Tech Startup Growth Hacking 101 - Basics on Growth Marketing
Creating Low-Code Loan Applications using the Trisotech Mortgage Feature Set

Creating Low-Code Loan Applications using the Trisotech Mortgage Feature Set
Call Girls Pune Just Call 9907093804 Top Class Call Girl Service Available

Call Girls Pune Just Call 9907093804 Top Class Call Girl Service Available
Grateful 7 speech thanking everyone that has helped.pdf

Grateful 7 speech thanking everyone that has helped.pdf
Vip Dewas Call Girls #9907093804 Contact Number Escorts Service Dewas

Vip Dewas Call Girls #9907093804 Contact Number Escorts Service Dewas
VIP Call Girl Jamshedpur Aashi 8250192130 Independent Escort Service Jamshedpur

VIP Call Girl Jamshedpur Aashi 8250192130 Independent Escort Service Jamshedpur
Problem mapping example
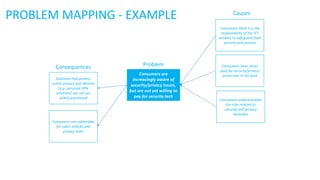
- 1. PROBLEM MAPPING - EXAMPLE Consumers are vulnerable for cyber attacks and privacy leaks Solutions that protect online privacy and identity (e.g. personal VPN solutions) are not yet widely purchased Consumers are increasingly aware of security/privacy issues, but are not yet willing to pay for security tech Consumers underestimate the risks related to security and privacy breaches ProblemConsequences Causes Consumers have never paid for security/privacy protection in the past Consumers think it is the responsibility of the ICT vendors to safeguard their security and privacy
- 2. FORCEFIELD ANALYSIS - EXAMPLE Consumers value security and privacy more than in the past There is an increasing awareness related to security and privacy issues amongst consumers Consumers have never paid for security/privacy protection in the past Problem Driving forces Restraining forces Consumers don’t want to pay for it Consumers have no experience with the selection of security or privacy solutions Consumers don’t think it is their responsibility to take care of their security and privacy Consumers often think: ‘what are the chances it will happen to me’
- 3. FORCEFIELD ANALYSIS - EXAMPLE Consumers value security and privacy more than in the past There is an increasing awareness related to security and privacy issues amongst consumers Consumers have never paid for security/privacy protection in the past Problem Driving forces Restraining forces Consumers don’t want to pay for it Consumers have no experience with the selection of security or privacy solutions Consumers don’t think it is their responsibility to take care of their security and privacy Consumers often think: ‘what are the chances it will happen to me’ Action: Create more awareness related to security and privacy issues Action: Provide more information on the solutions available, what is it used for and how to use it Action: Offer a pricing model which allows billing the customers for the security they actually used (e.g. based on the number of security breaches the solution prevented) Action: Developers of security solutions should cooperate with ICT vendors to be able to offer the consumer a complete offer Action: Make it mandatory for everyone to take a minimum level of security measures depending on their risk
- 4. SOURCES Forstadt, L. A., Doore, B. (2012). Program Planning with Problem Mapping to Better Understand Need. Tools of the Trade, February 2012, Vol. 50, nr. 1.