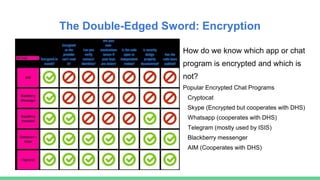
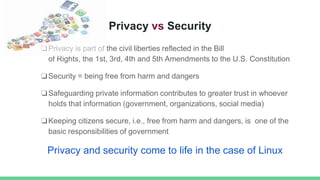
The document discusses the relationship between privacy and security. It defines privacy as civil liberties protected by the constitution, while security means freedom from harm. While privacy and security can be at odds, open source projects like Linux aim to balance them. Linux started as a hobby but became widely adopted. However, its kernel is now a target for cyber attacks. Solutions like SELinux and hardened versions of Linux have been proposed to improve security, but these come at the cost of privacy. The document also discusses encryption technologies and how they can be used for both good and bad purposes, complicating policy debates around law enforcement access.

![The Case of Linux
exible and free
source: Created in the spirit of “naive
mentation”, just for fun [Just for Fun, 1992]
ed from 10,000 to 19 million lines of code
ssing the cognitive surplus of an unruly
who tailored the operating system to their
stes and purpose](https://image.slidesharecdn.com/8e59b347-b325-4abc-ae09-fa8285d131c7-160829041651/85/Privacy-vs-Security-4-320.jpg)







![The Cybersecurity Information Sharing Act
❏The fact of our times: private information is no longer secure
❏Congress wades in into the privacy vs. security debate with a new
cybersecurity bill, the CyberSecurity Information Sharing (CISA)
❏“A system that lets companies share evidence of hackers’
footsteps among themselves and with the U.S. government
without the risk of being sued for breaking privacy
protection or anti-trust laws” [Laura Hautala]](https://image.slidesharecdn.com/8e59b347-b325-4abc-ae09-fa8285d131c7-160829041651/85/Privacy-vs-Security-12-320.jpg)
![The Cybersecurity Information Sharing Act
“Critics, including more than 20 of the biggest
companies in the tech industry argue that the bill does
not do enough to protect the privacy of individuals and
could lead to mass government surveillance” [Laura
Hautala]](https://image.slidesharecdn.com/8e59b347-b325-4abc-ae09-fa8285d131c7-160829041651/85/Privacy-vs-Security-13-320.jpg)