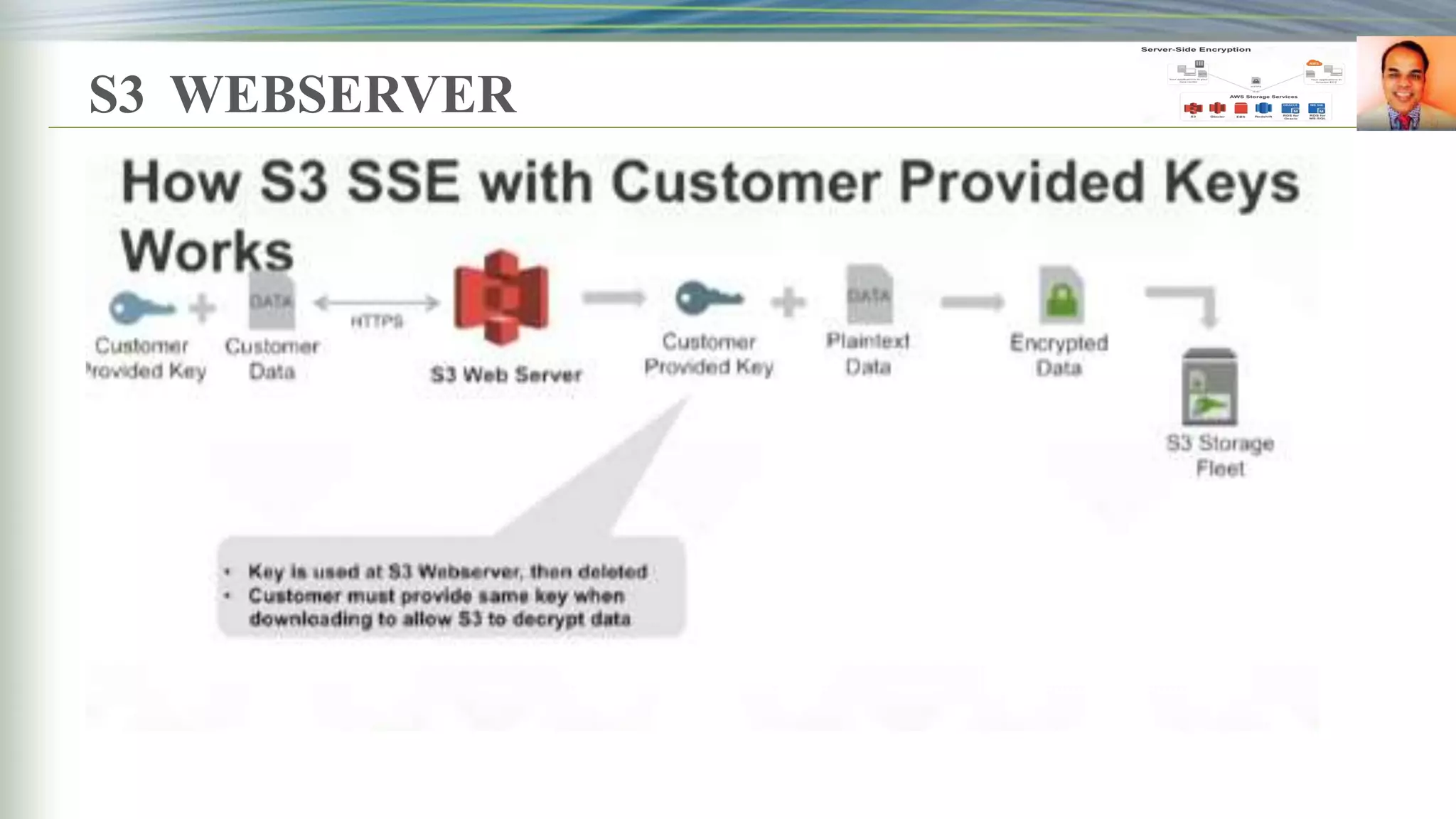
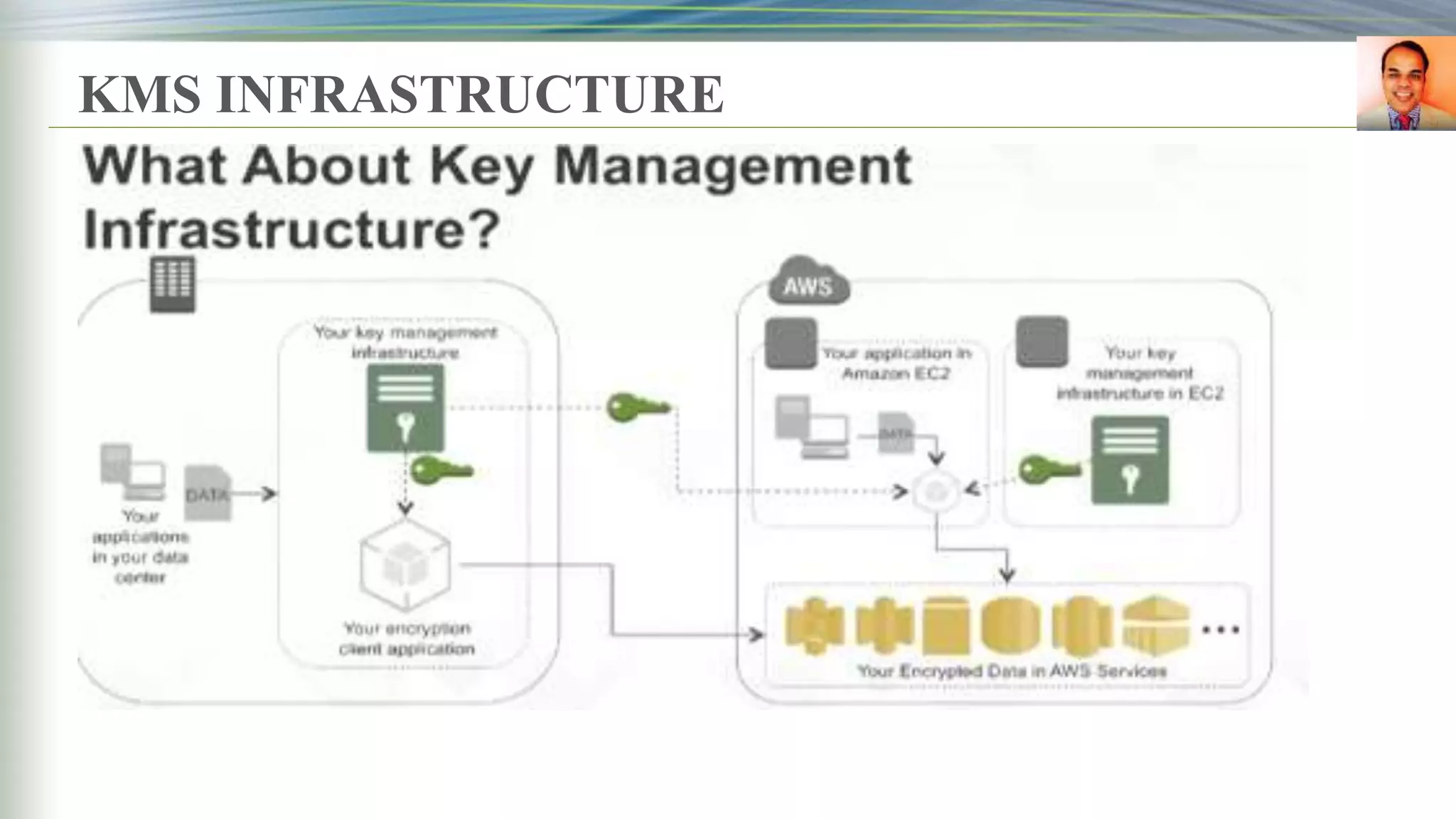
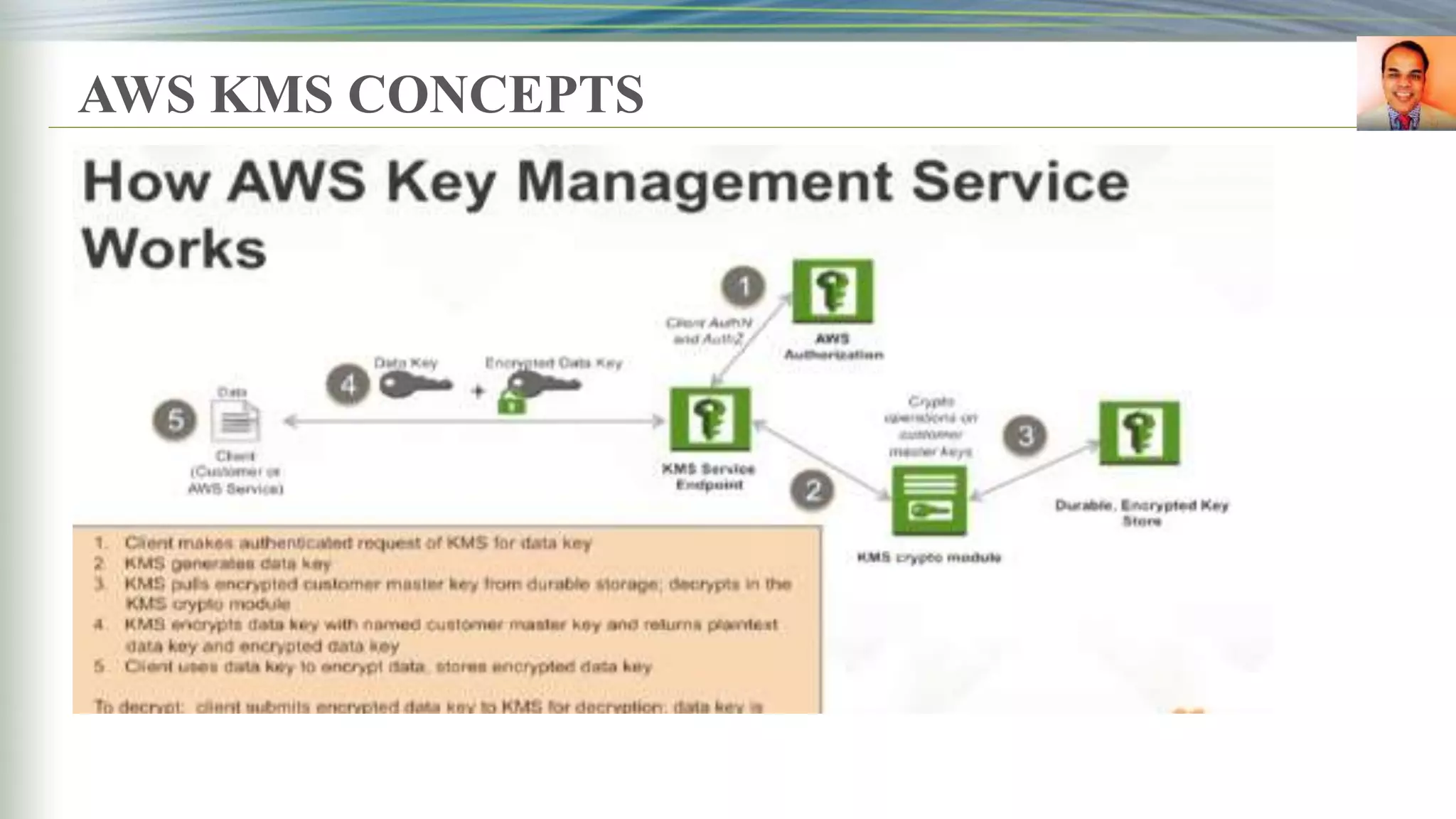
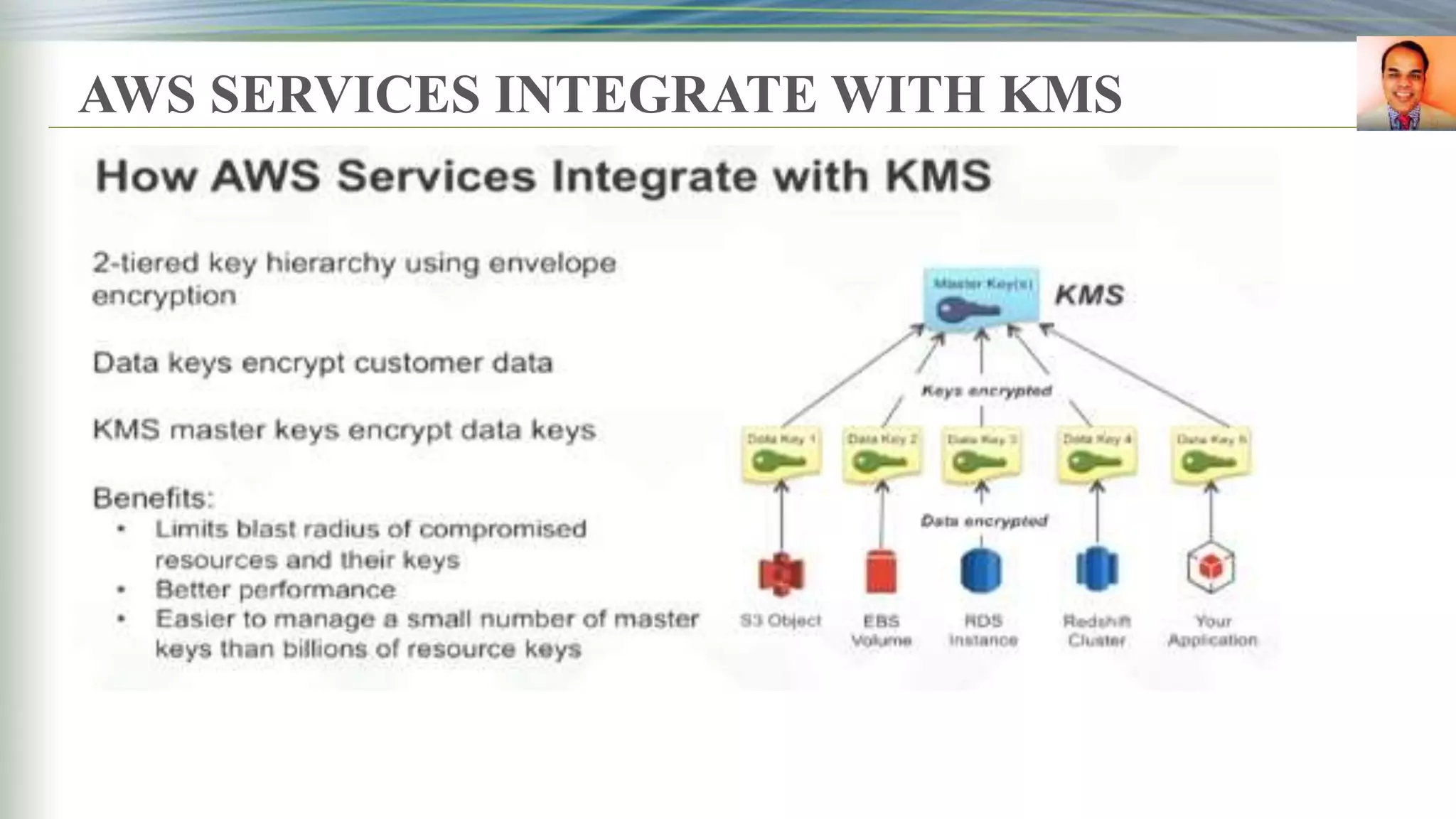
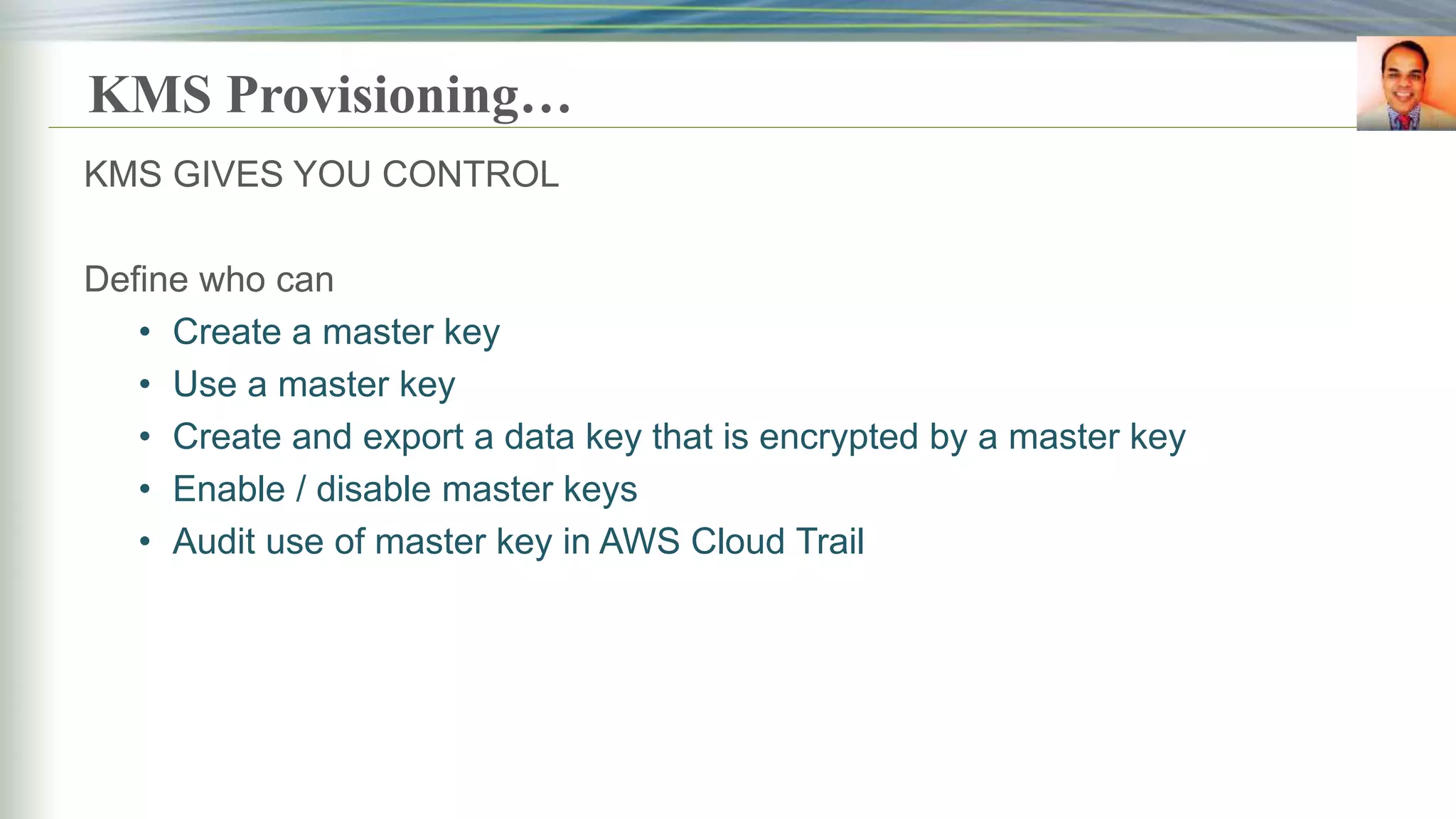
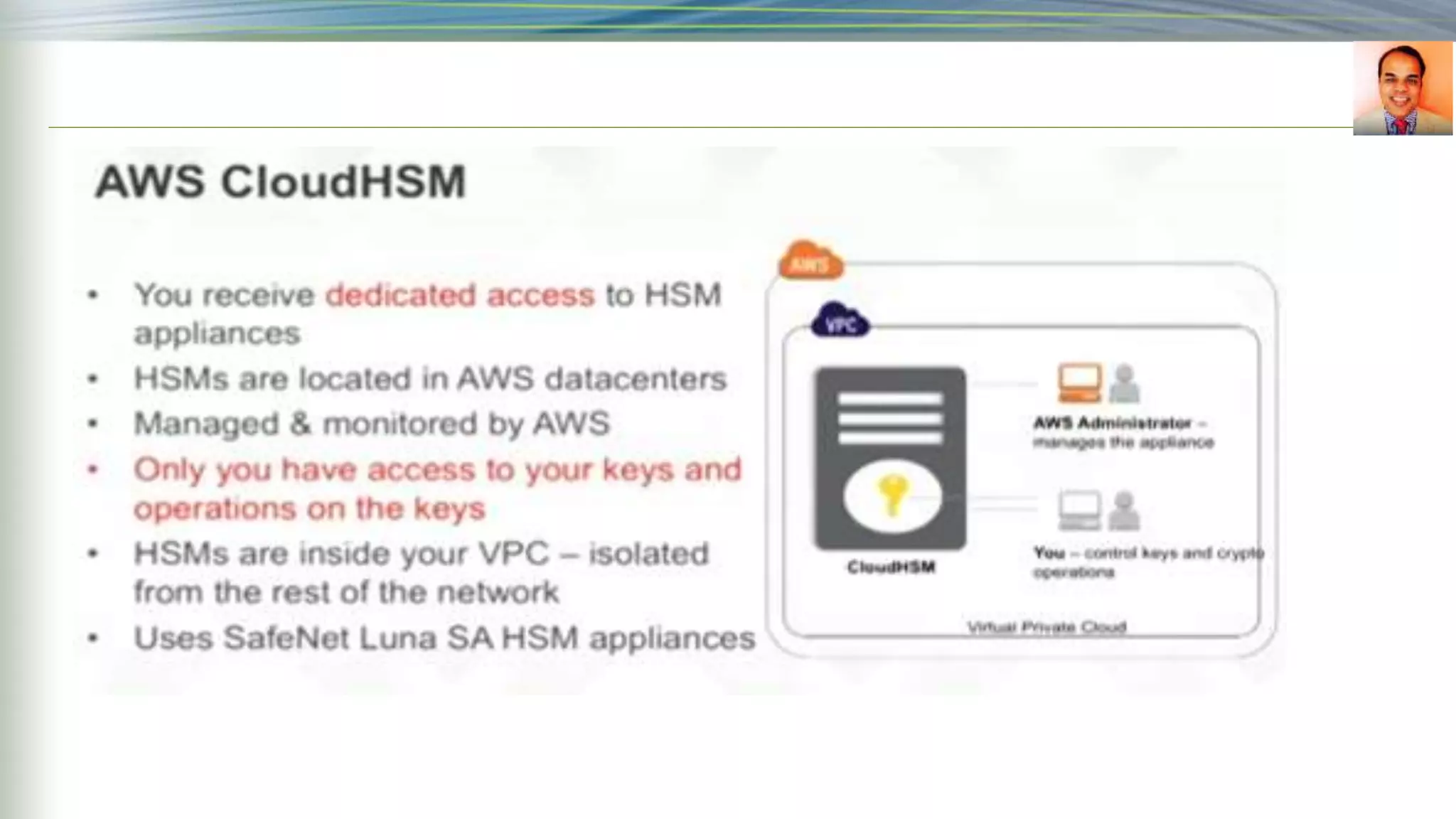
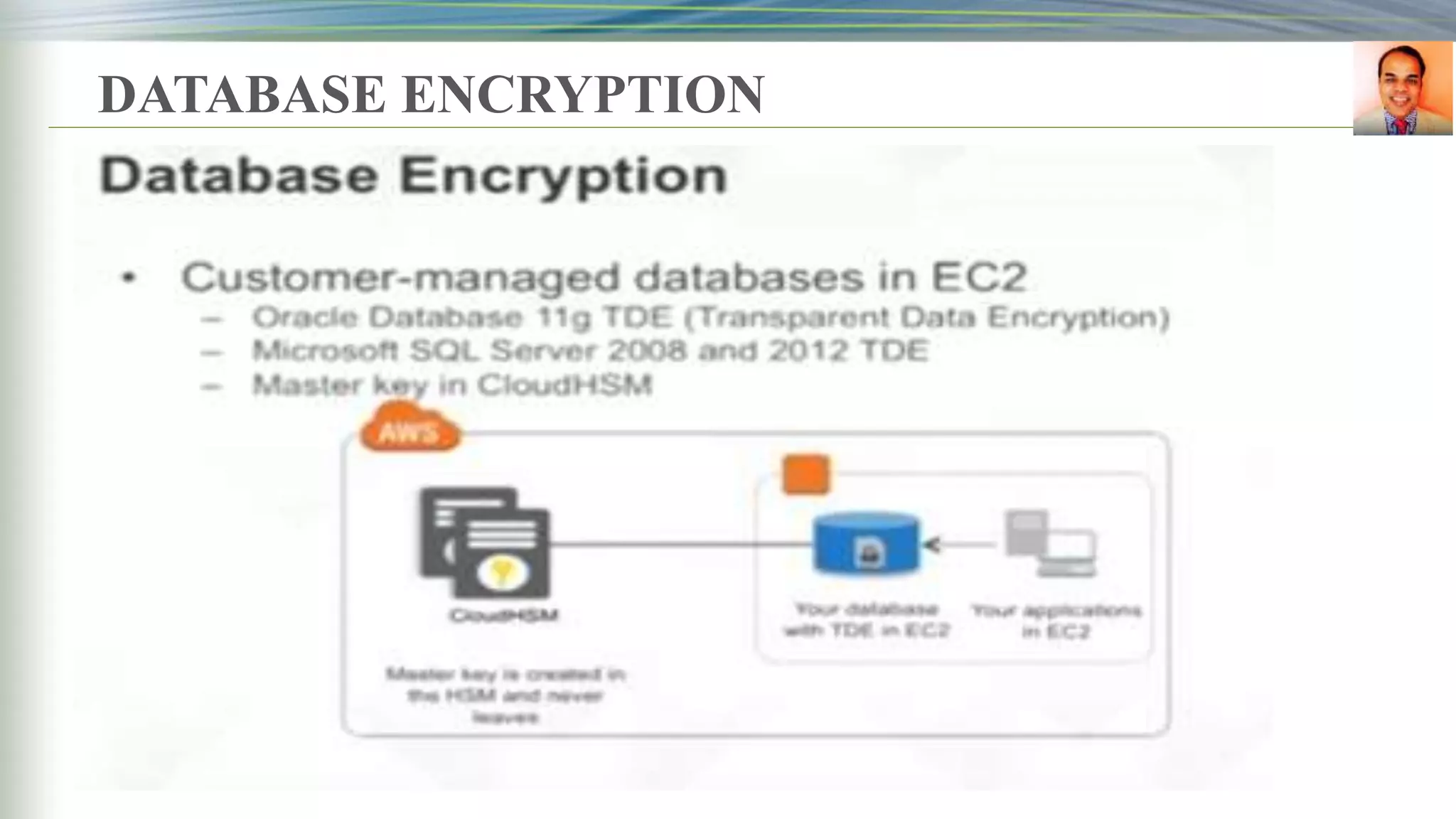
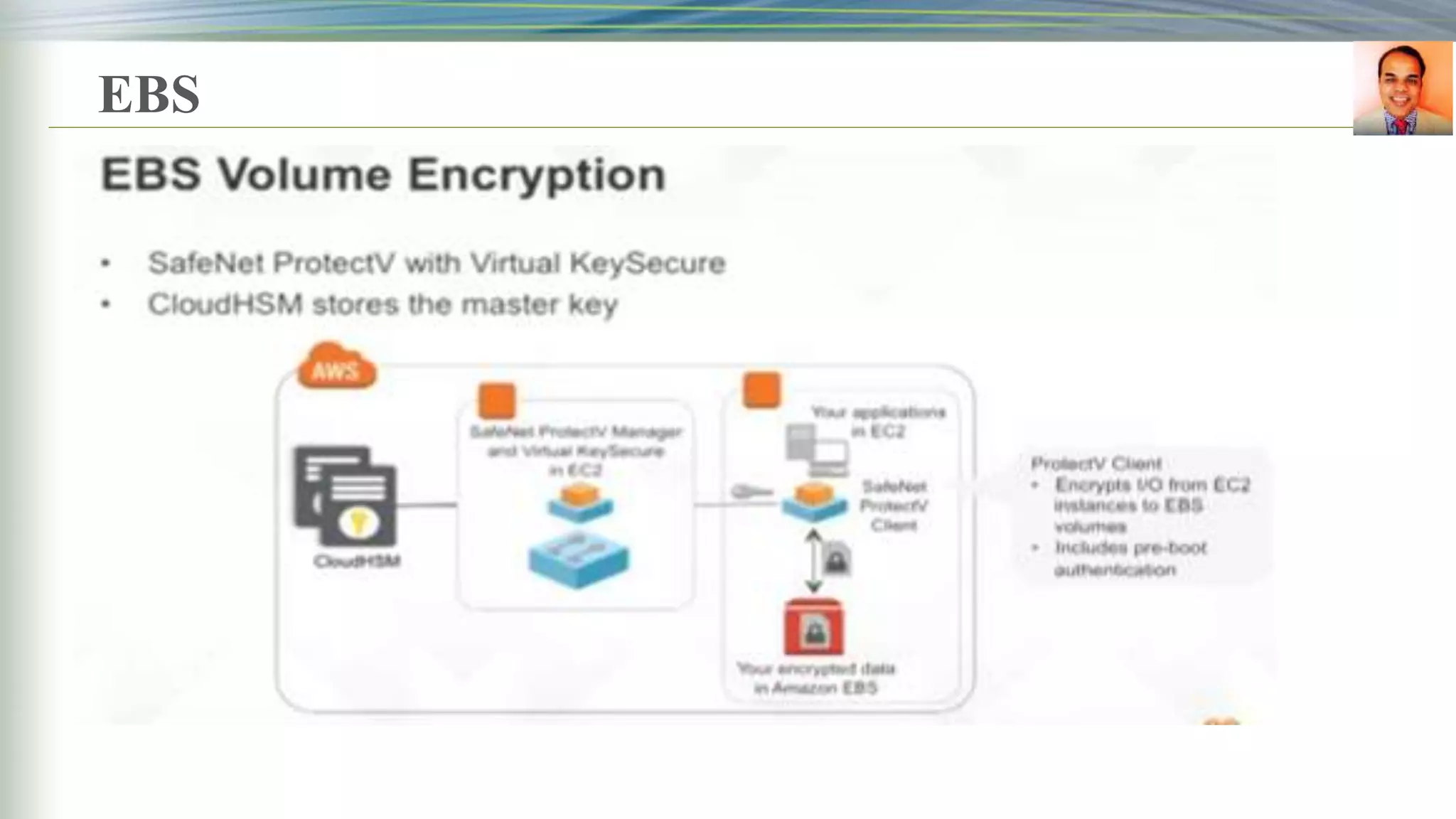
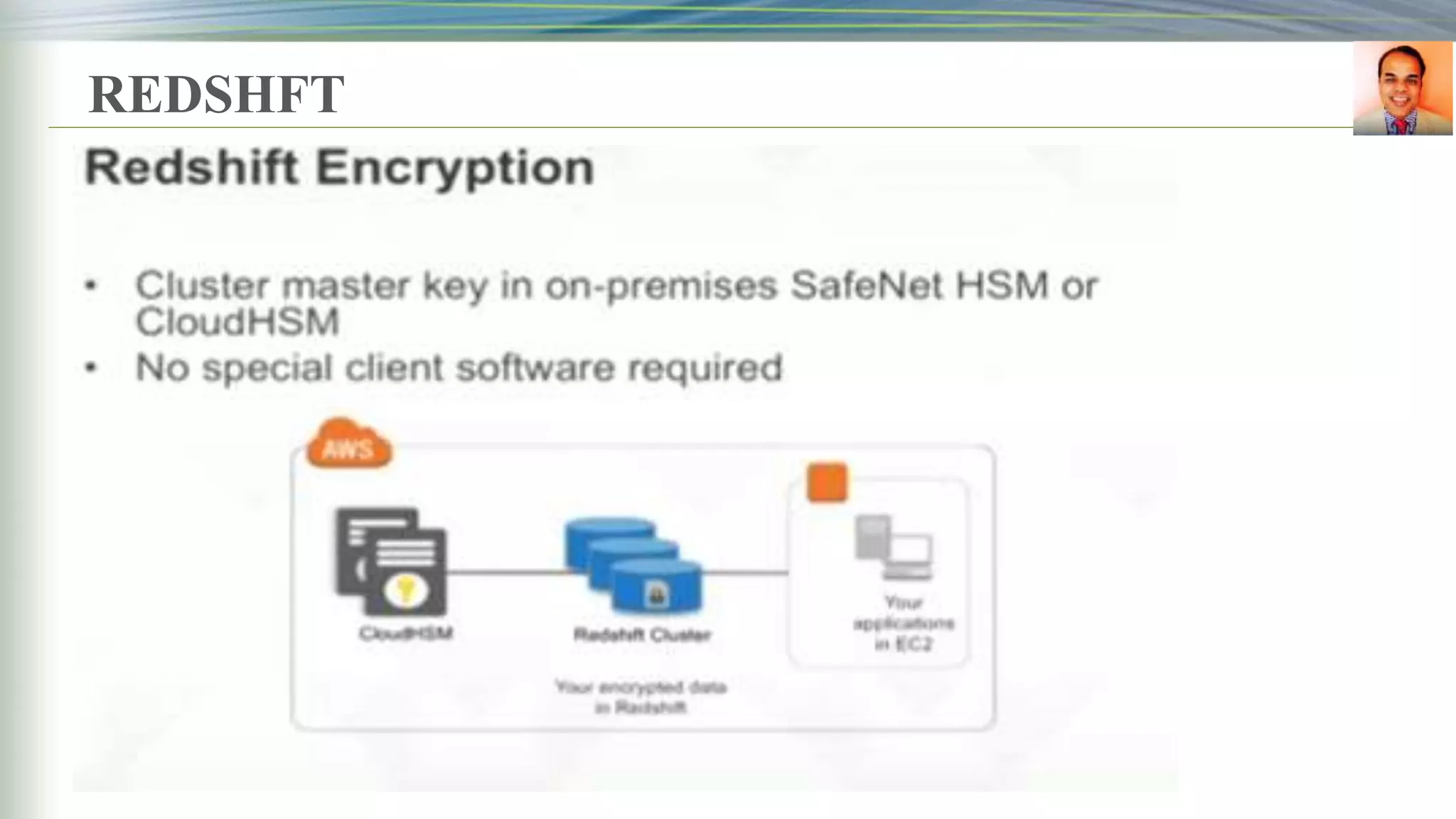
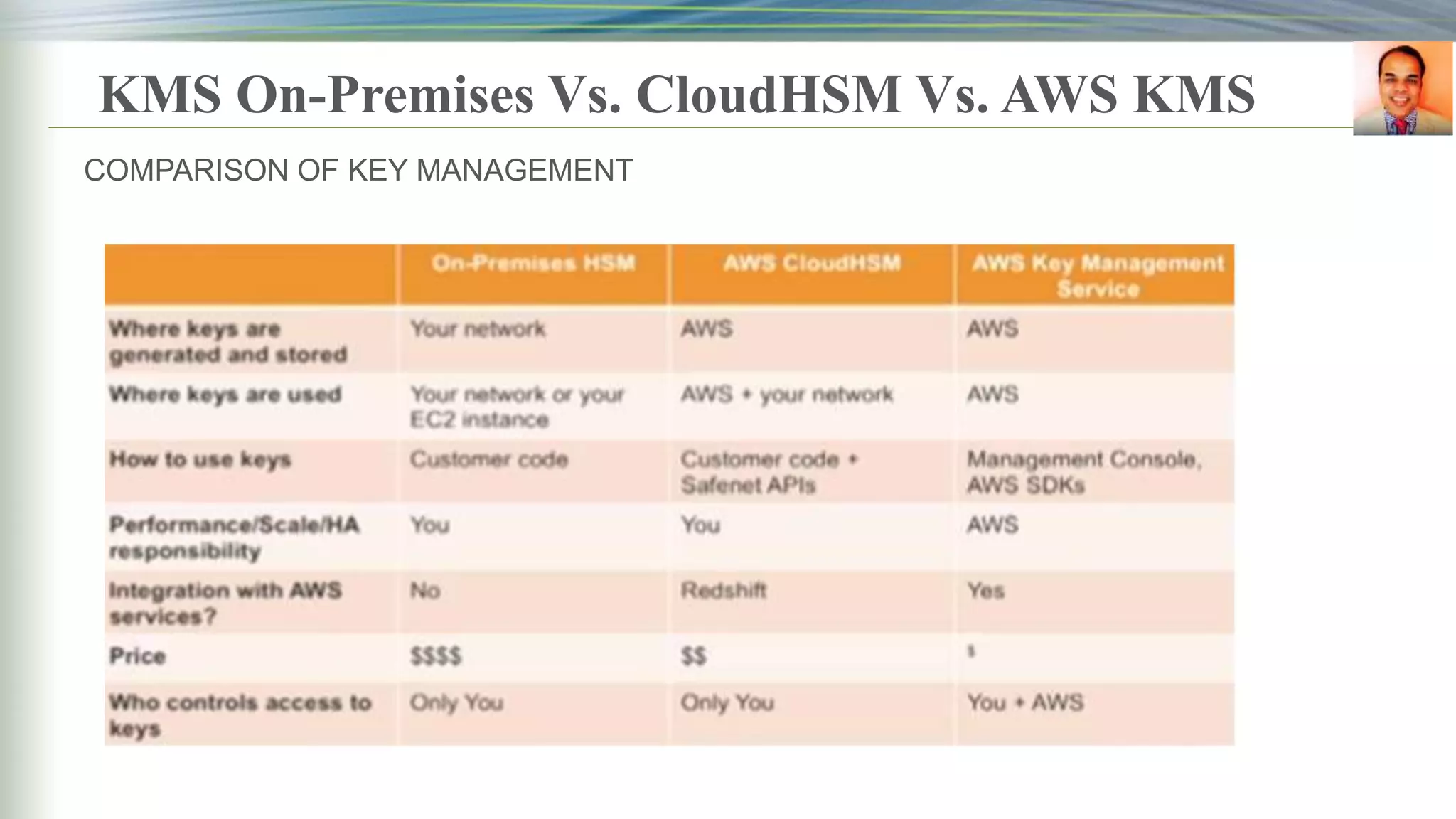
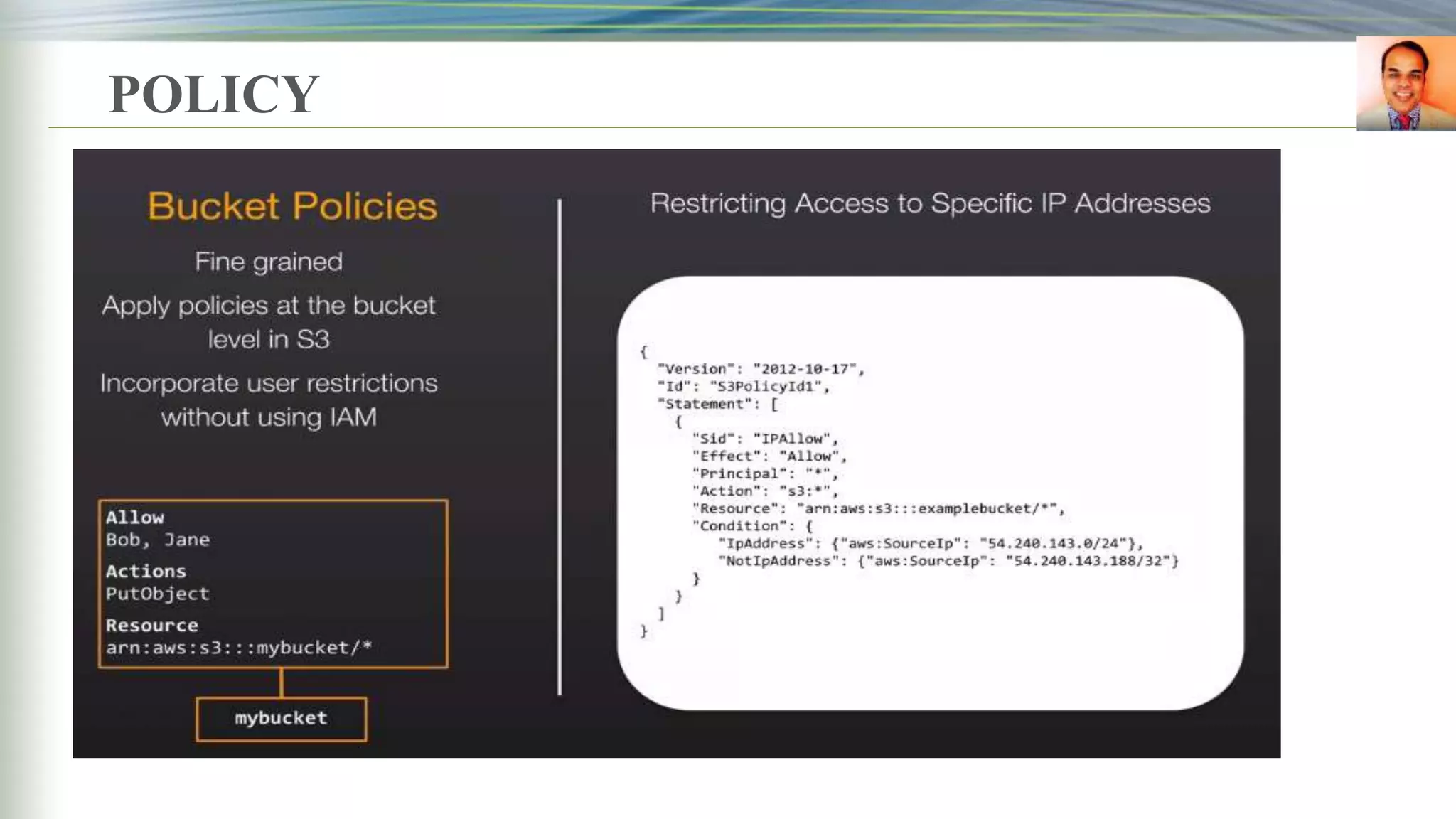
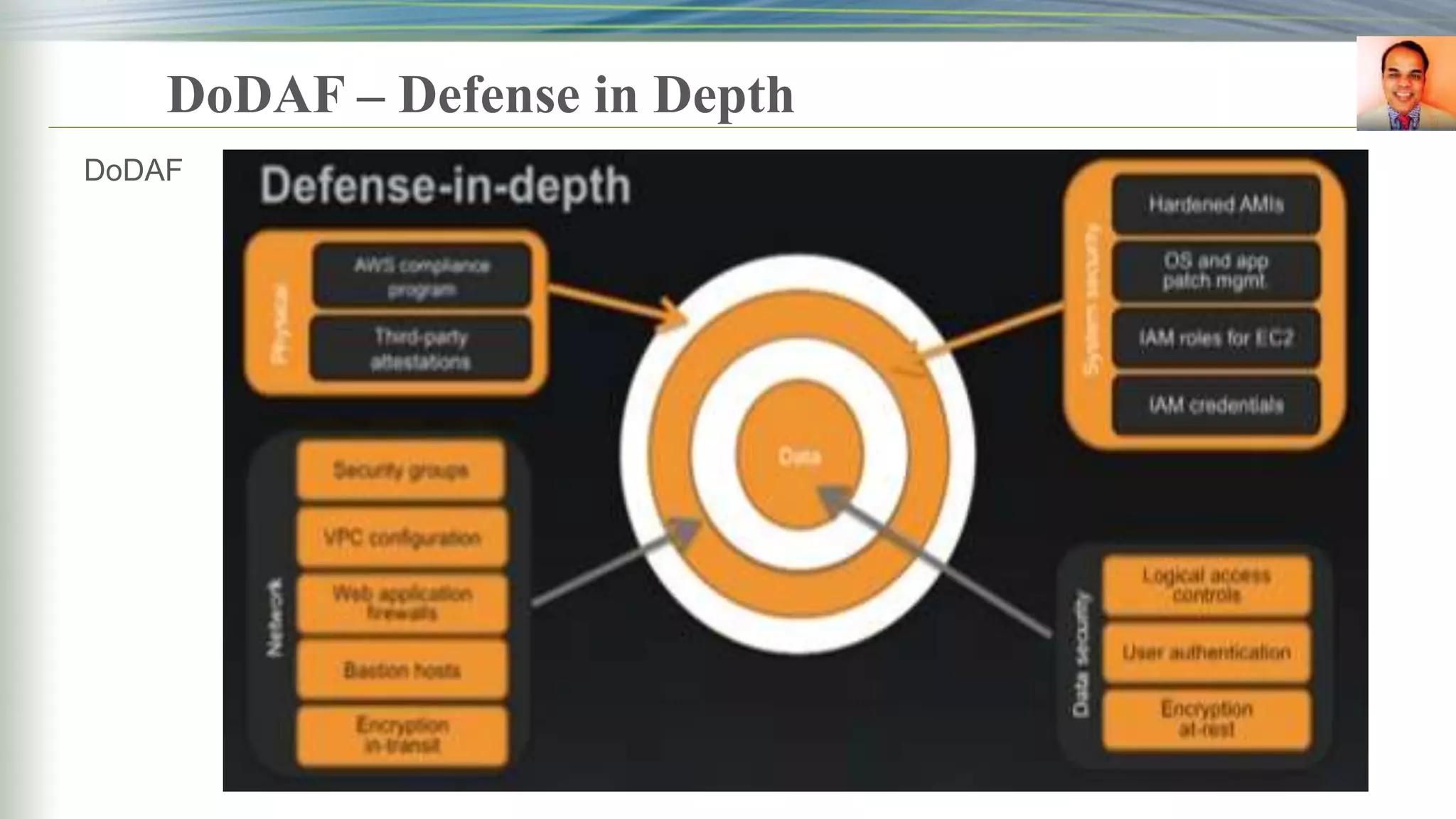
This document discusses key management systems and cloud migration. It begins with an overview of encryption at rest using DoDAF and various AWS services like S3, EBS, RDS, and Redshift. It then provides details on the AWS Key Management Service (KMS), how it allows users to create and manage encryption keys to protect data on supported AWS services. KMS ensures keys are securely stored and accessible only by authorized users or services. The document also discusses how database encryption can be implemented using KMS and compares KMS to on-premises key management and CloudHSM. It concludes with topics on identity and access management policies, standards for archiving to Glacier, and server-side encryption options on S3

![ENCRYPTION DATA @ REST
Encryption Data at REST
Volume Encryption
Object Encryption
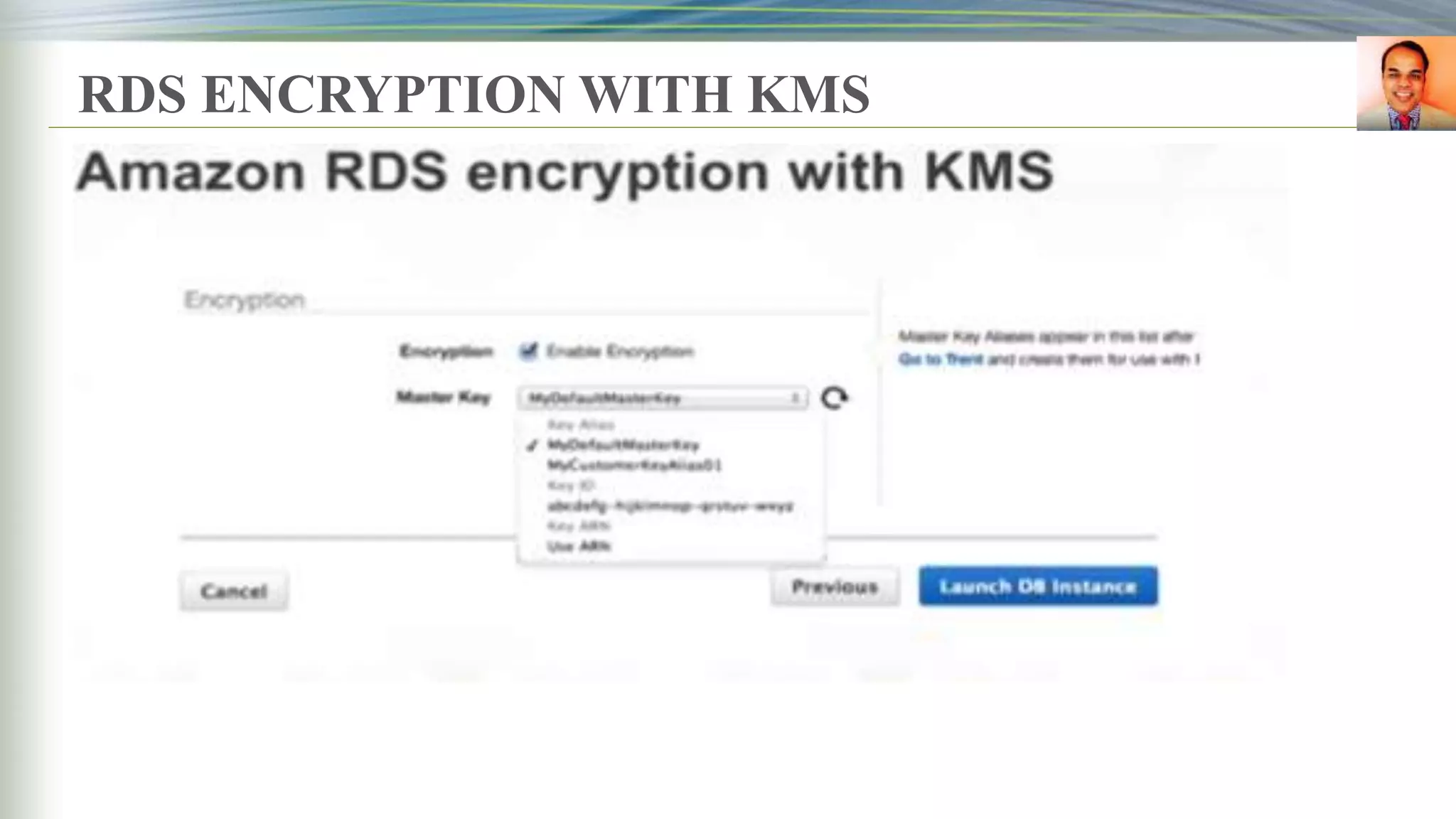
Database Encryption
EBS encryption OS Tools
AWS marketplace/
partnr
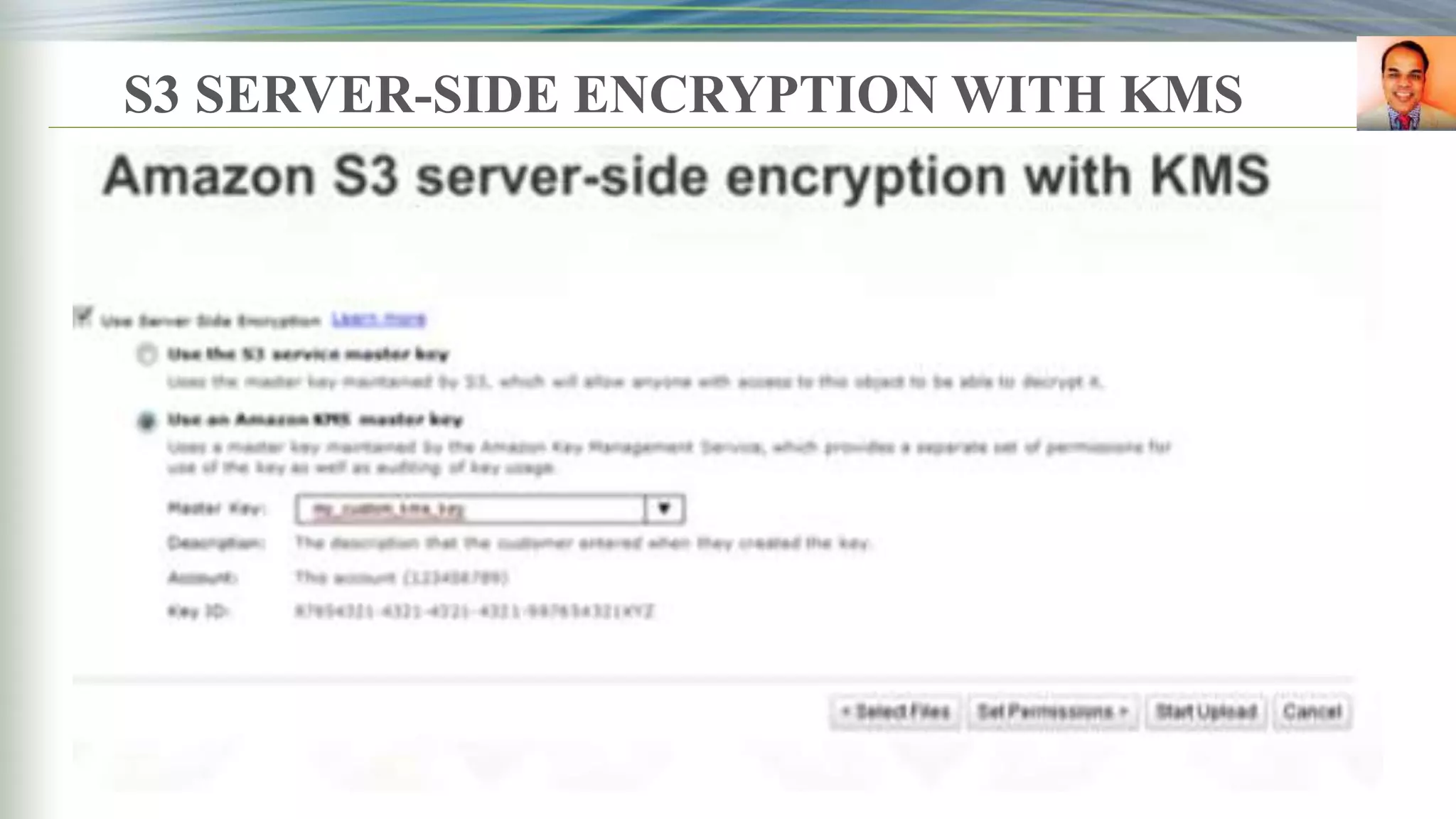
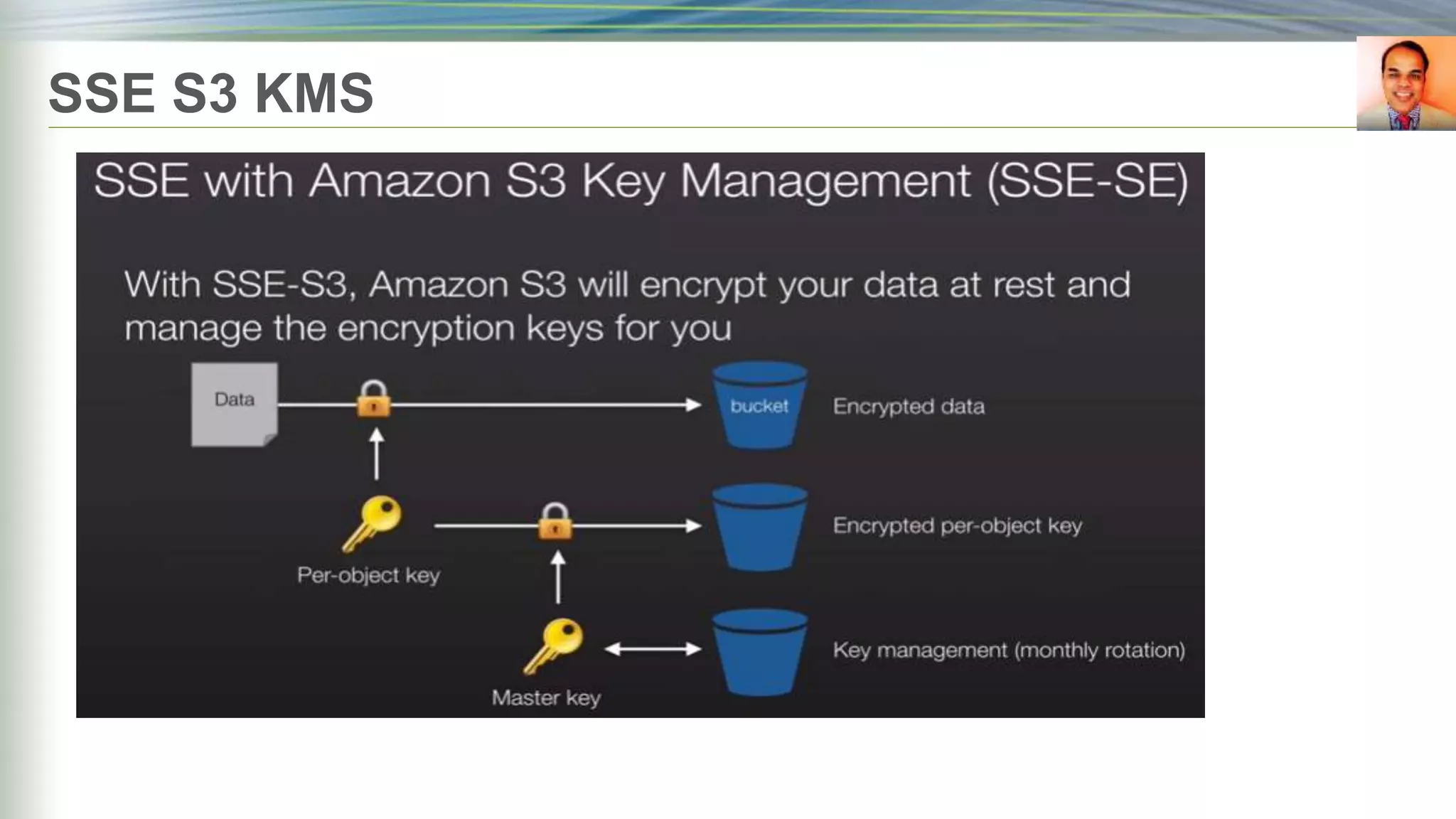
S3 server side
encryption[sse]
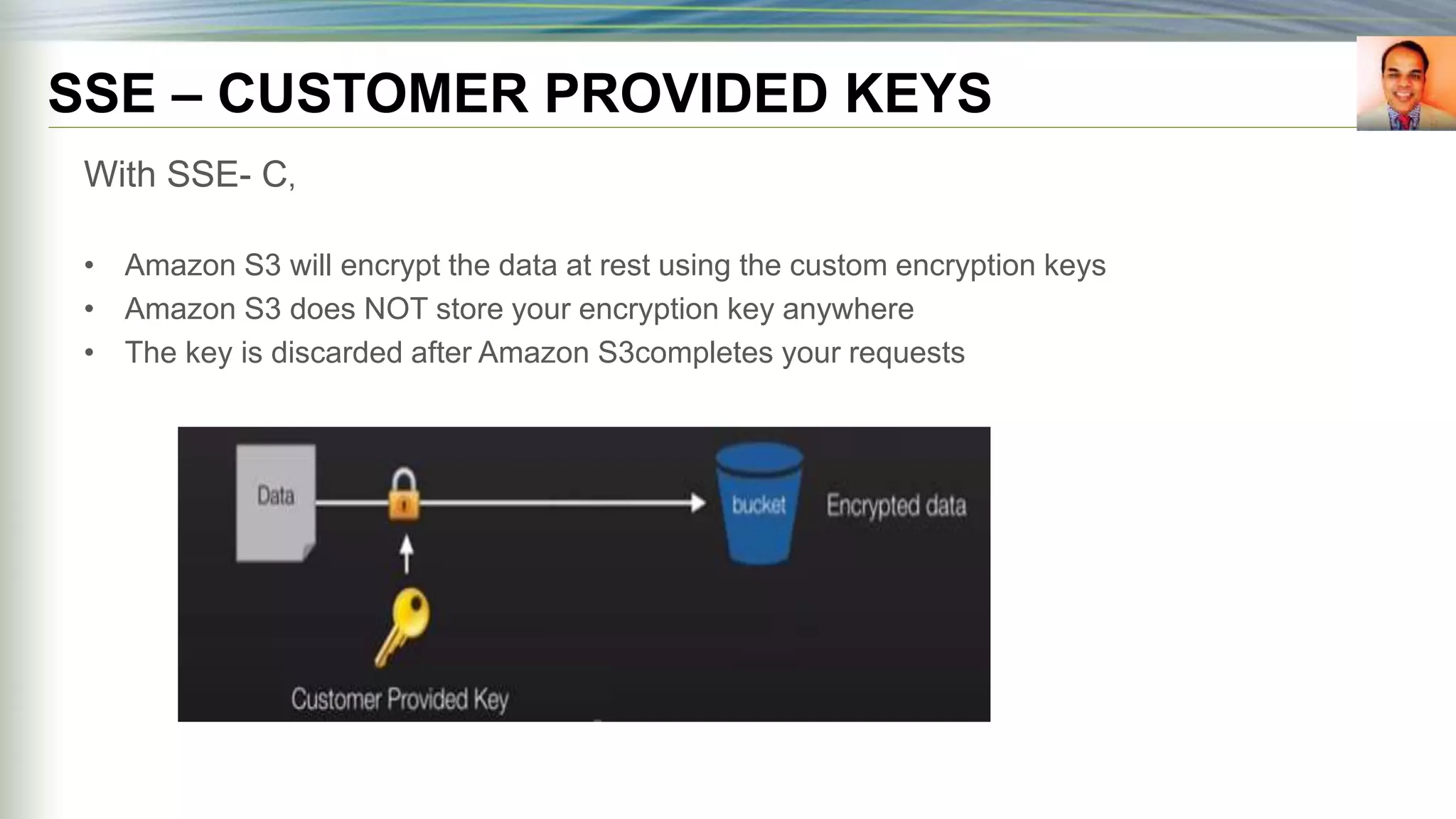
S3 SSE w/ customer
provided keys
Client side encryption
RDS ORACLE
TDE HSM
RDS MSSQL
TDE
RDS MYSQL
KMS
RDSPostgreSQL
KMS
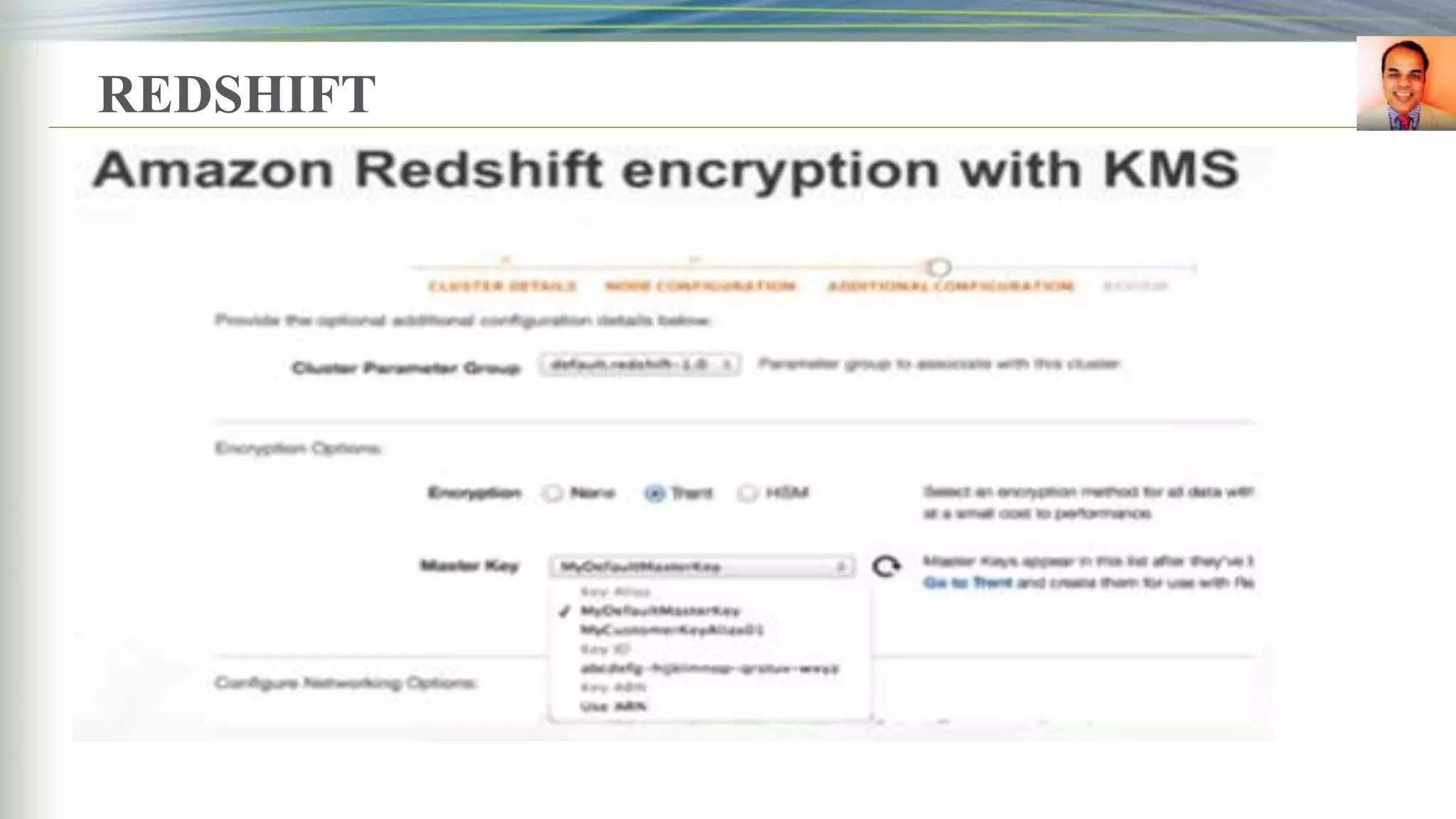
Anazon Redshift
encryption](https://image.slidesharecdn.com/presentationbyrbeheraonkms-aws-181216064635/75/Presentation-by-R-Behera-on-KMS-aws-4-2048.jpg)
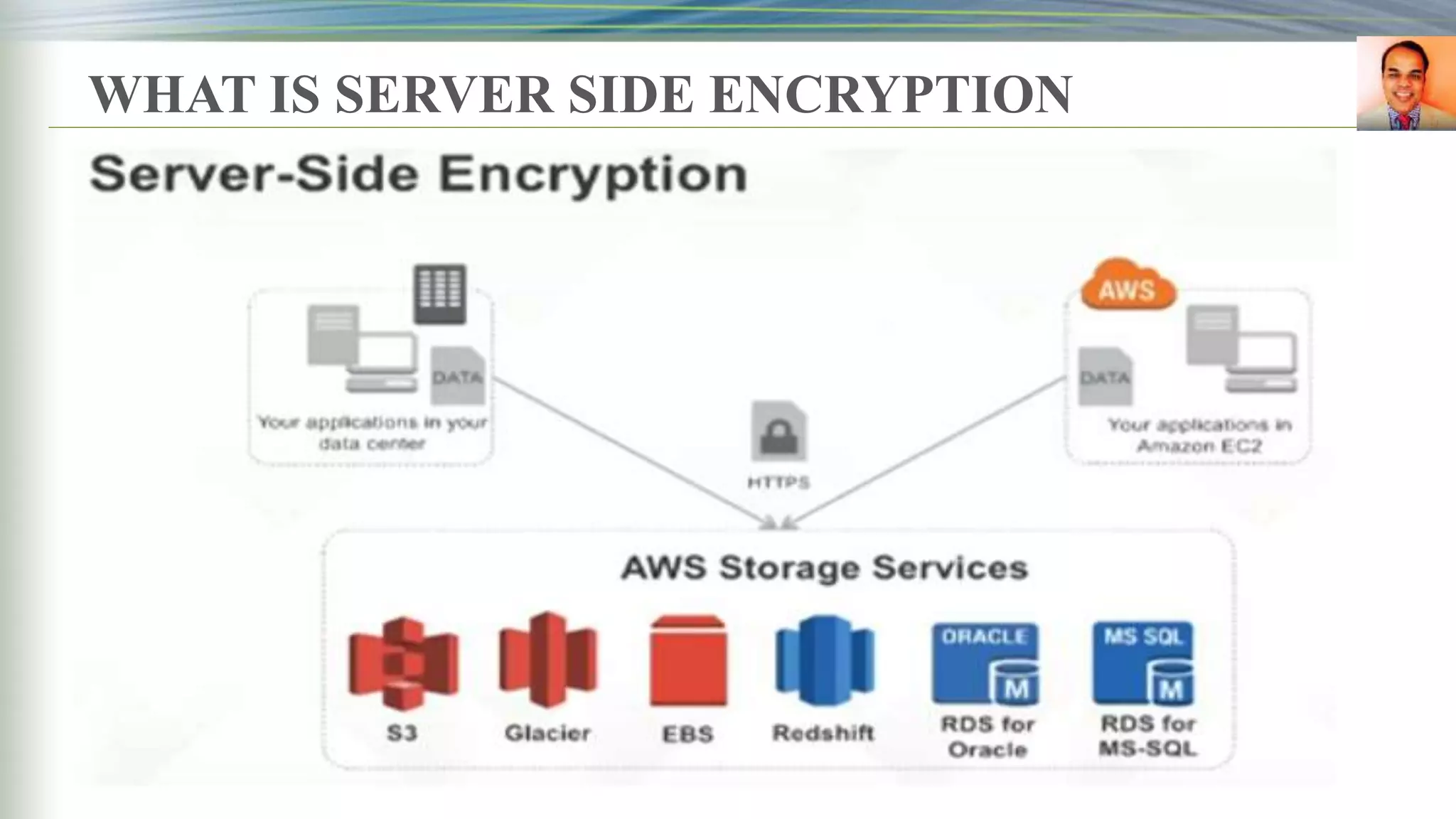
![SERVER SIDE ENCRYPTION [S3]](https://image.slidesharecdn.com/presentationbyrbeheraonkms-aws-181216064635/75/Presentation-by-R-Behera-on-KMS-aws-7-2048.jpg)
![SERVER-SIDE ENCRYPTION SSE [S3]](https://image.slidesharecdn.com/presentationbyrbeheraonkms-aws-181216064635/75/Presentation-by-R-Behera-on-KMS-aws-8-2048.jpg)