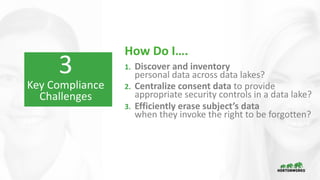
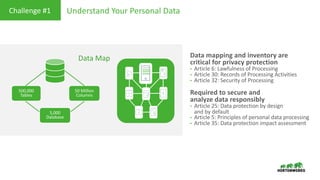
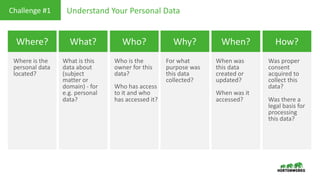
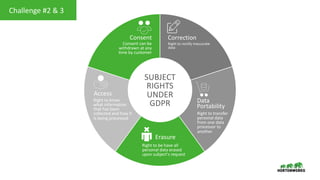
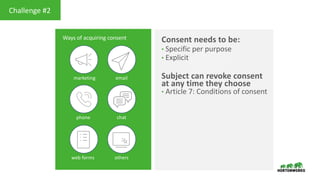
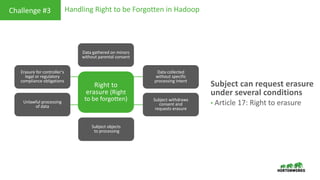
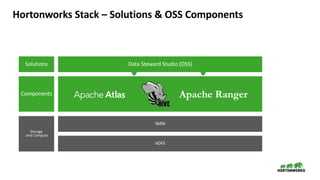
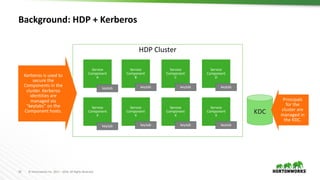
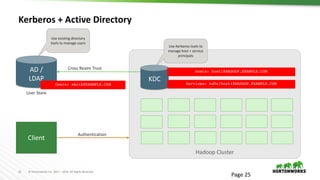
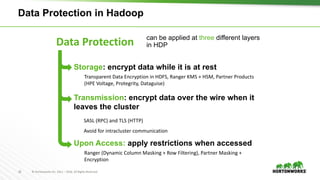
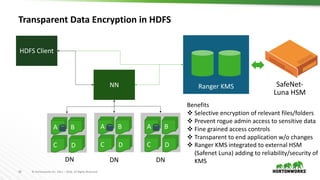
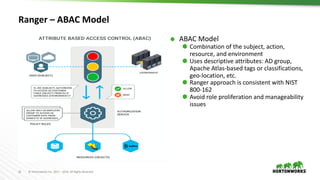
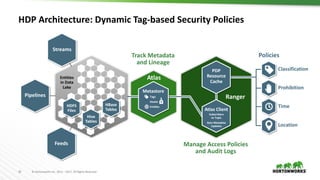
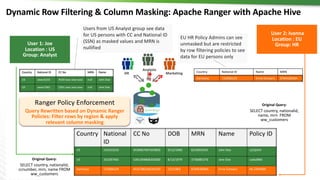
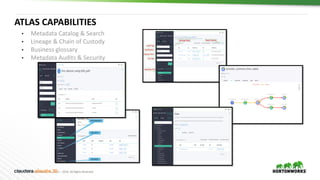
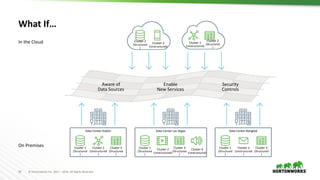
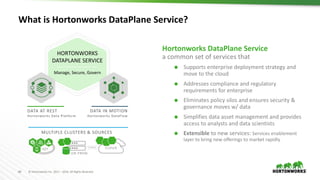
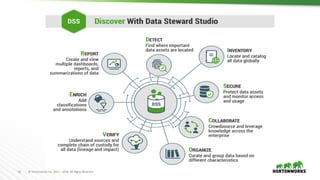
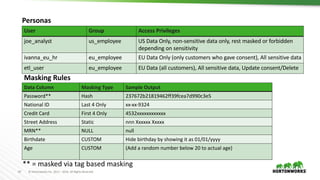
This document provides an overview of how Hortonworks Data Platform (HDP) can help with data governance, security, and compliance requirements. It discusses key challenges around data mapping, consent management, and the right to be forgotten. The document then demonstrates how various HDP components like Apache Atlas, Apache Ranger, Ranger KMS, and Data Steward Studio address these challenges. Specifically, it shows how Atlas can help identify and classify personal data, Ranger provides centralized authorization and auditing, and Ranger KMS supports data encryption. Finally, the document describes a demo scenario and setup to illustrate dynamic row filtering, column masking, and tag-based security policies in HDP.