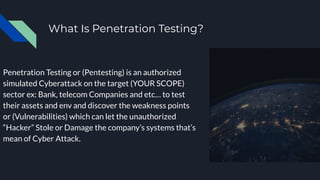
1. Penetration testing (pentesting) involves authorized simulated cyberattacks against a target such as a company to test for vulnerabilities and weaknesses in their systems.
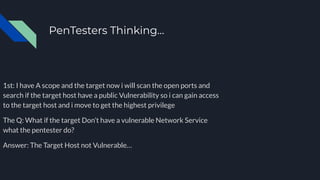
2. Pentesters first understand the business needs and scope, then scan targets to discover vulnerabilities which they attempt to exploit to gain access and highest privileges.
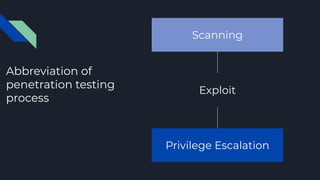
3. The process involves scanning, exploiting vulnerabilities to gain access, and attempting privilege escalation to end with the highest level of access, then cleaning traces of the testing.