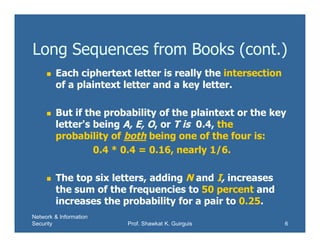
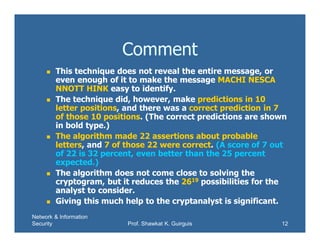
This document discusses using books as a source for one-time pads for encryption. Specifically, it proposes using phone books by selecting digits from phone numbers or using passages of text as a key. However, this is not truly random and can be broken by analyzing letter frequencies in the ciphertext and key text. The document then demonstrates how to analyze a ciphertext using a reduced table of the six most common letters to find possible plaintext letters. It also discusses dual-message encryption to add ambiguity for the cryptanalyst.