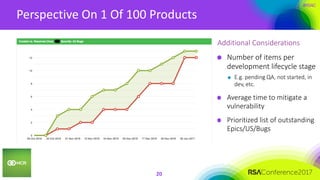
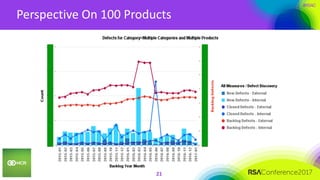
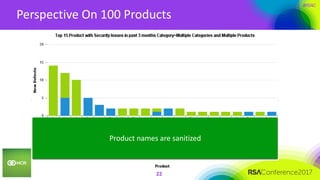
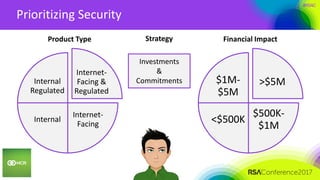
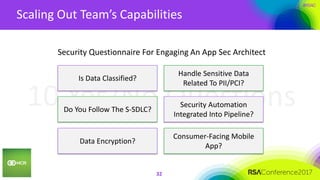
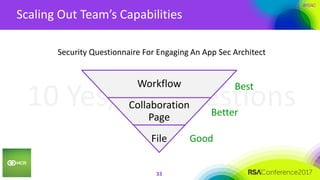
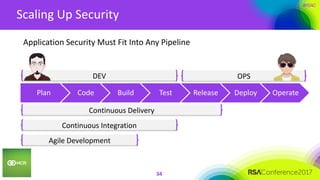
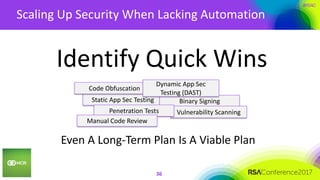
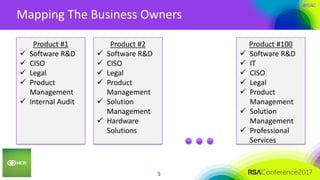
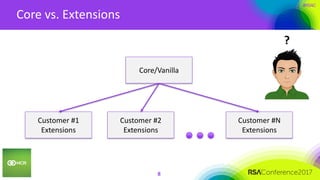
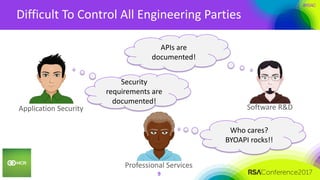
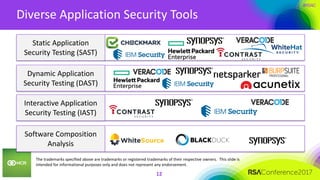
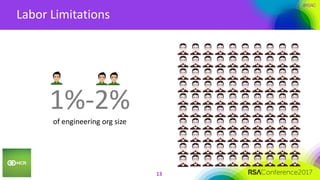
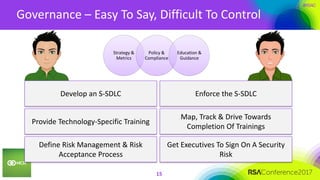
This document summarizes a presentation on securing 100 products. It discusses the challenges of securing multiple products, including mapping responsibilities, diverse technologies, and resource limitations. It provides approaches for prioritizing security based on product type and risk level. These include developing a security maturity program, product strategy, and correctly budgeting security resources. Automating security tools and finding partnerships can help scale efforts. Measuring effectiveness over time is also important.








![#RSAC
Verification – Roadblocks Ahead!
17
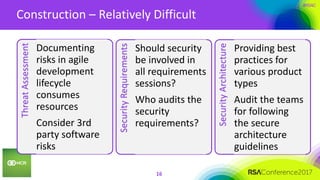
•Get the/a design diagram from engineering teams… lots of teams!!!
•Working with many smart engineering people – they know everything!
Design Review
•Utilizing automation is great if ALL bug tracking, code repo, and build systems are centralized
•Scaling automation for 100 products is nearly impossible (technology & labor wise)
Code Review
•Automation = [sophisticated] vulnerability scanning. Manual work = penetration test!
•$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$
Security Testing](https://image.slidesharecdn.com/asd-w10fsecuring-100-products-how-hard-can-it-be-170420061844/85/Securing-100-products-How-hard-can-it-be-17-320.jpg)