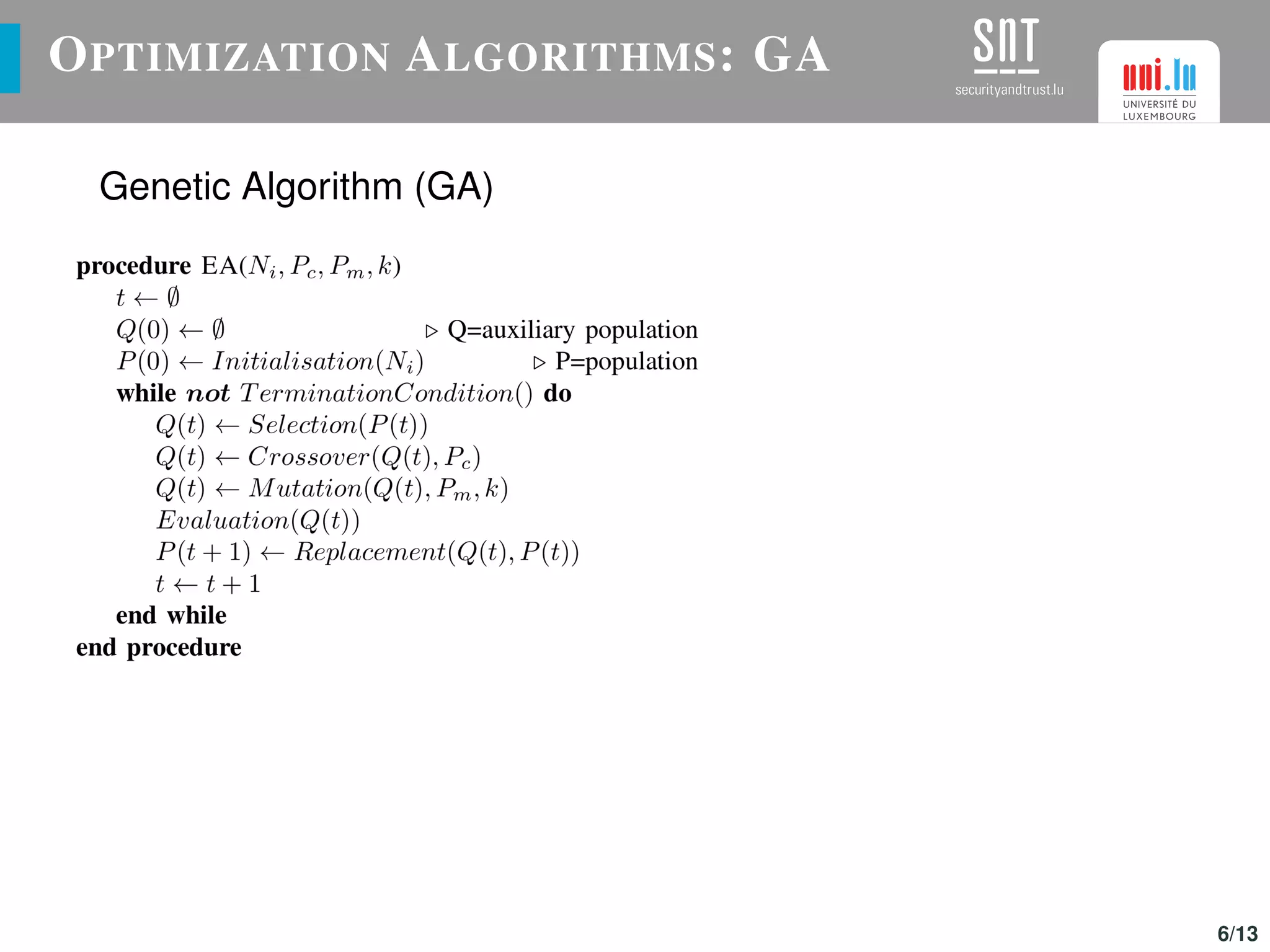
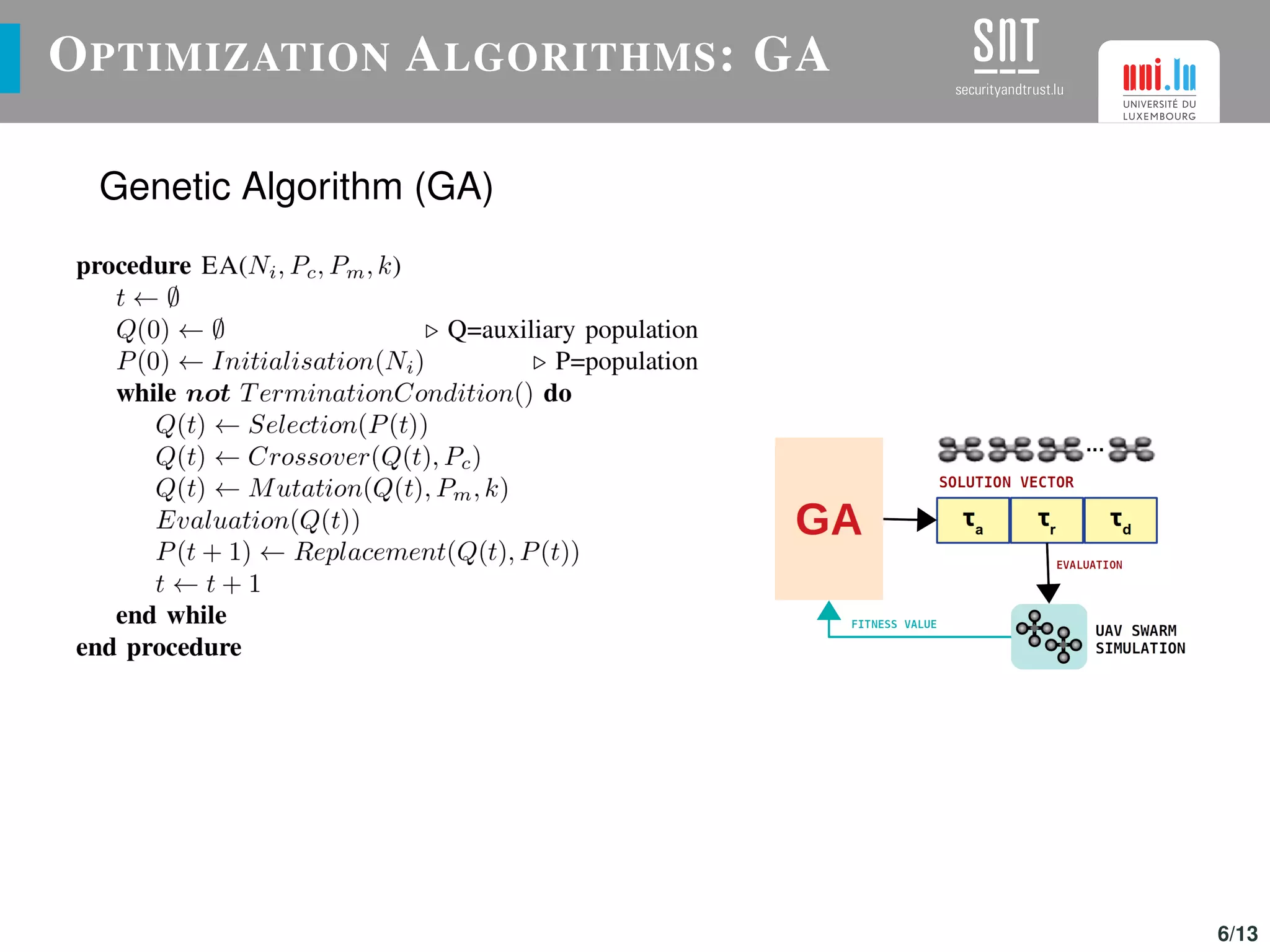
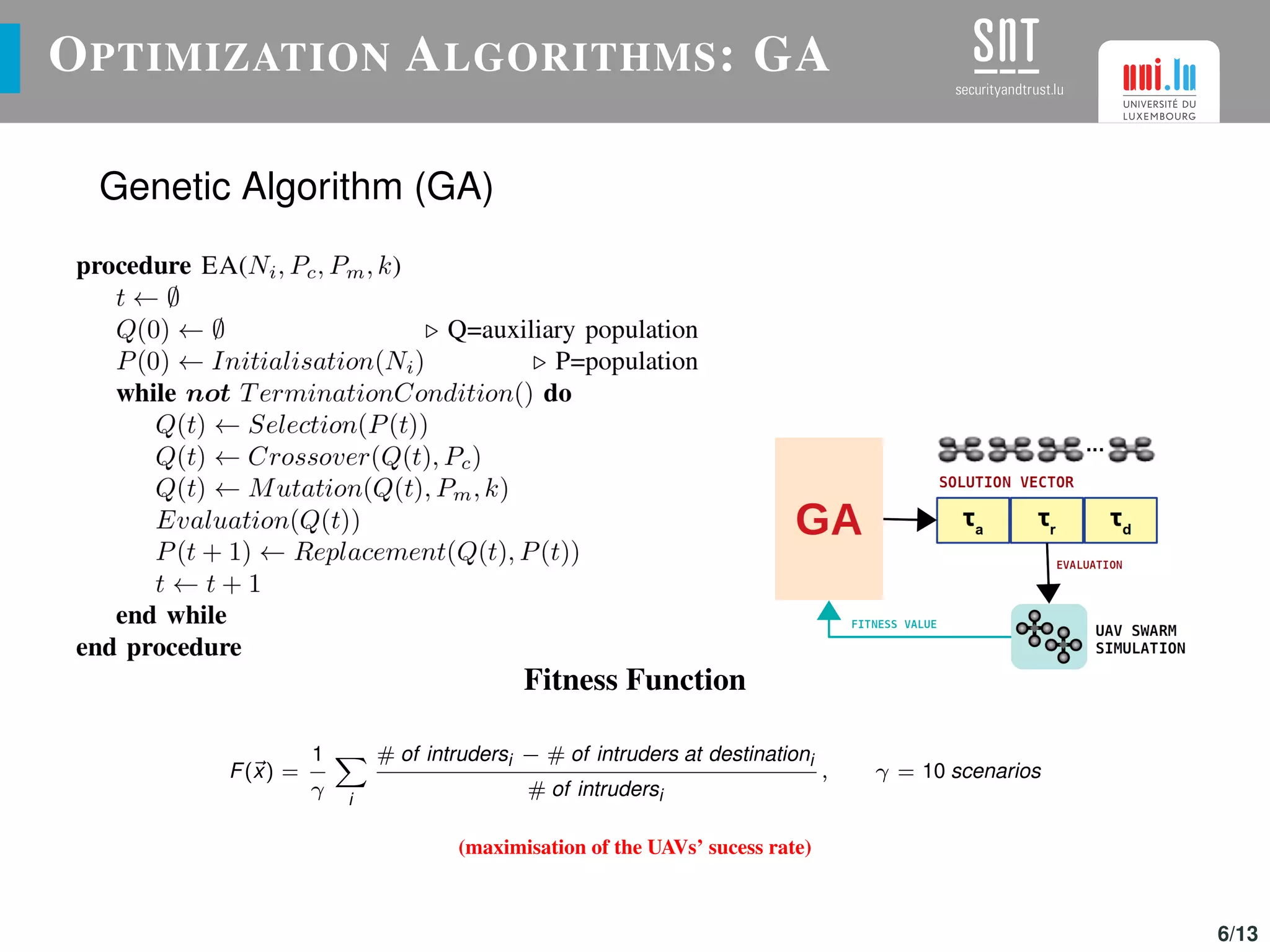
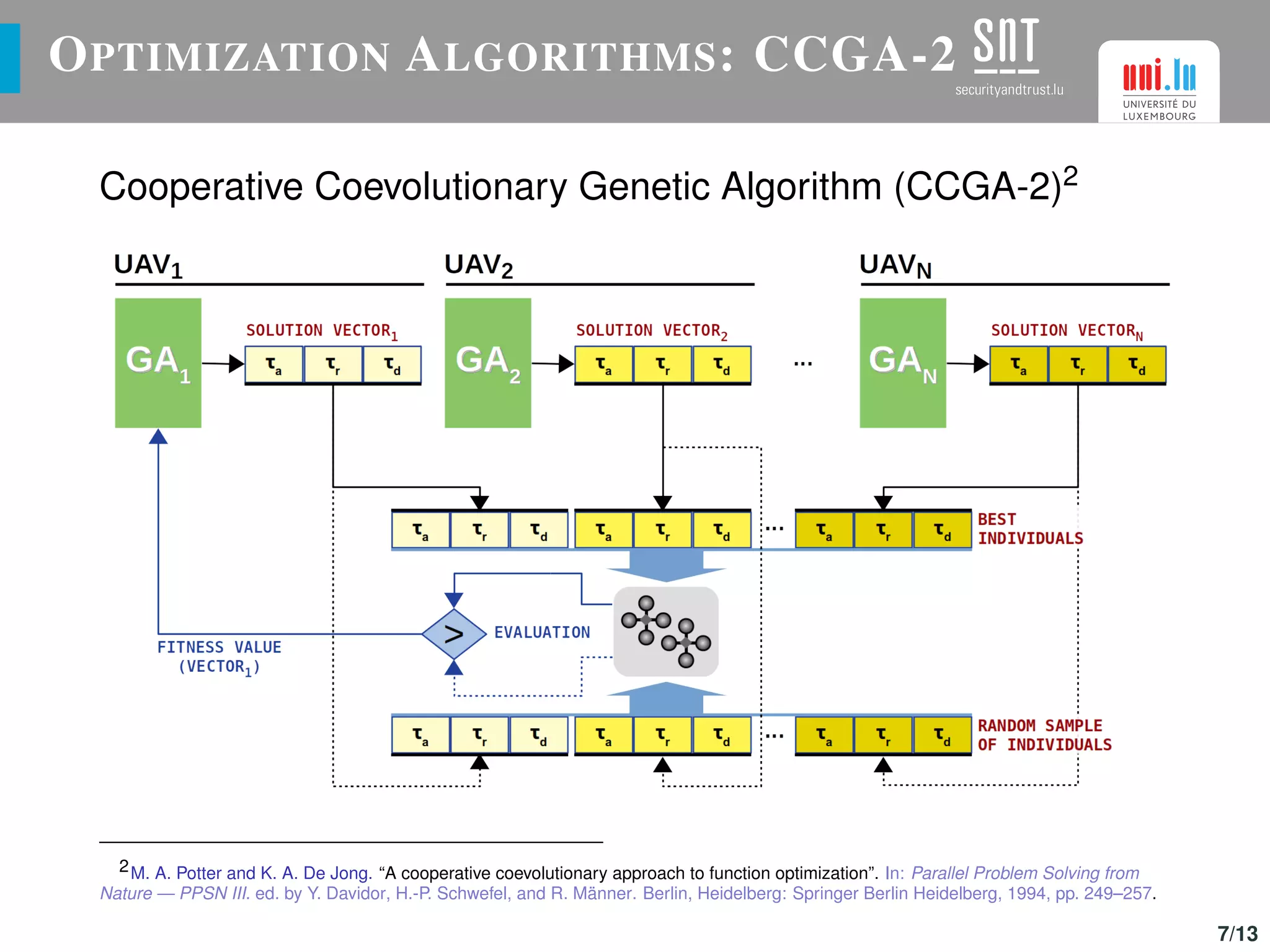
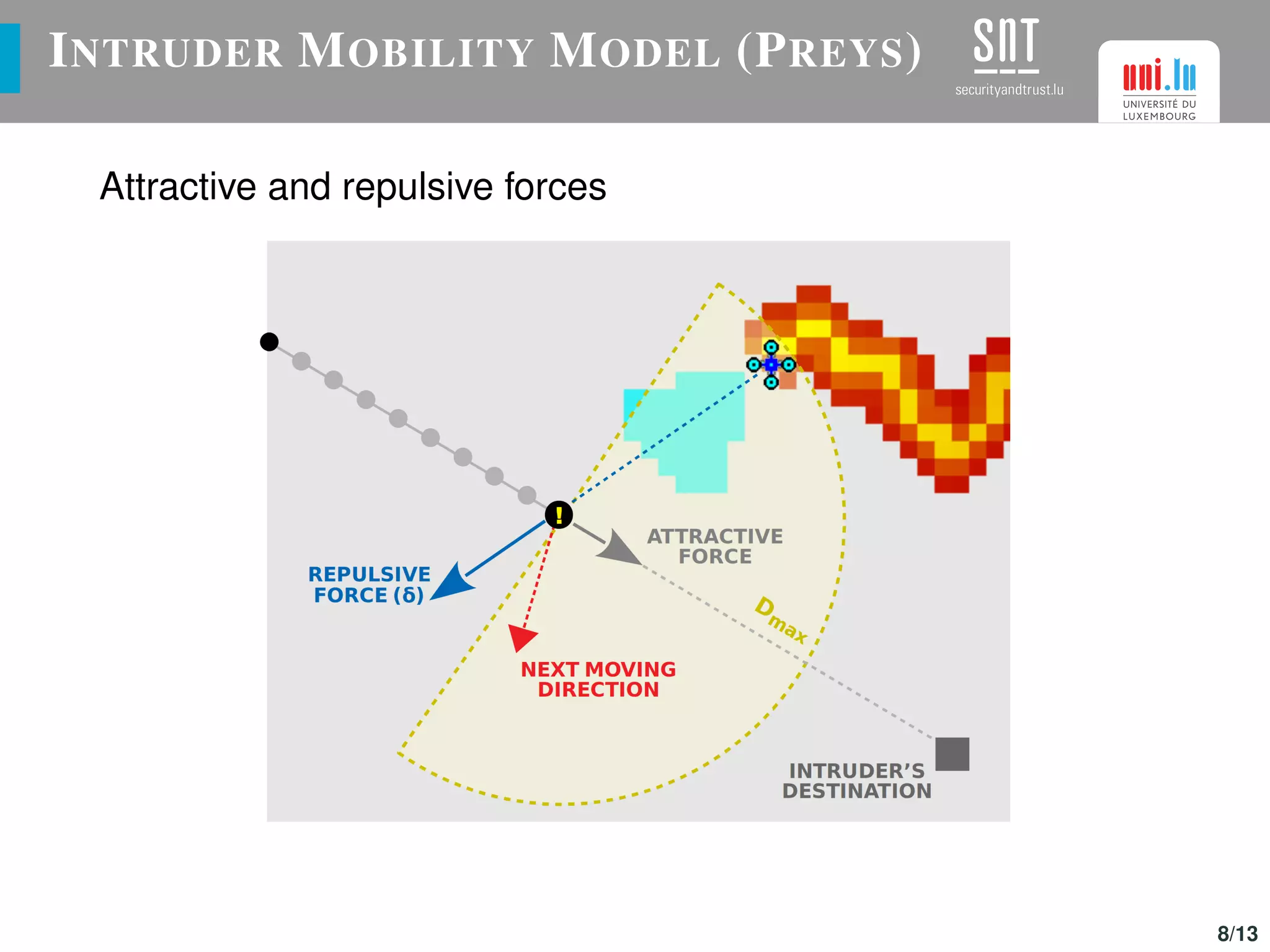
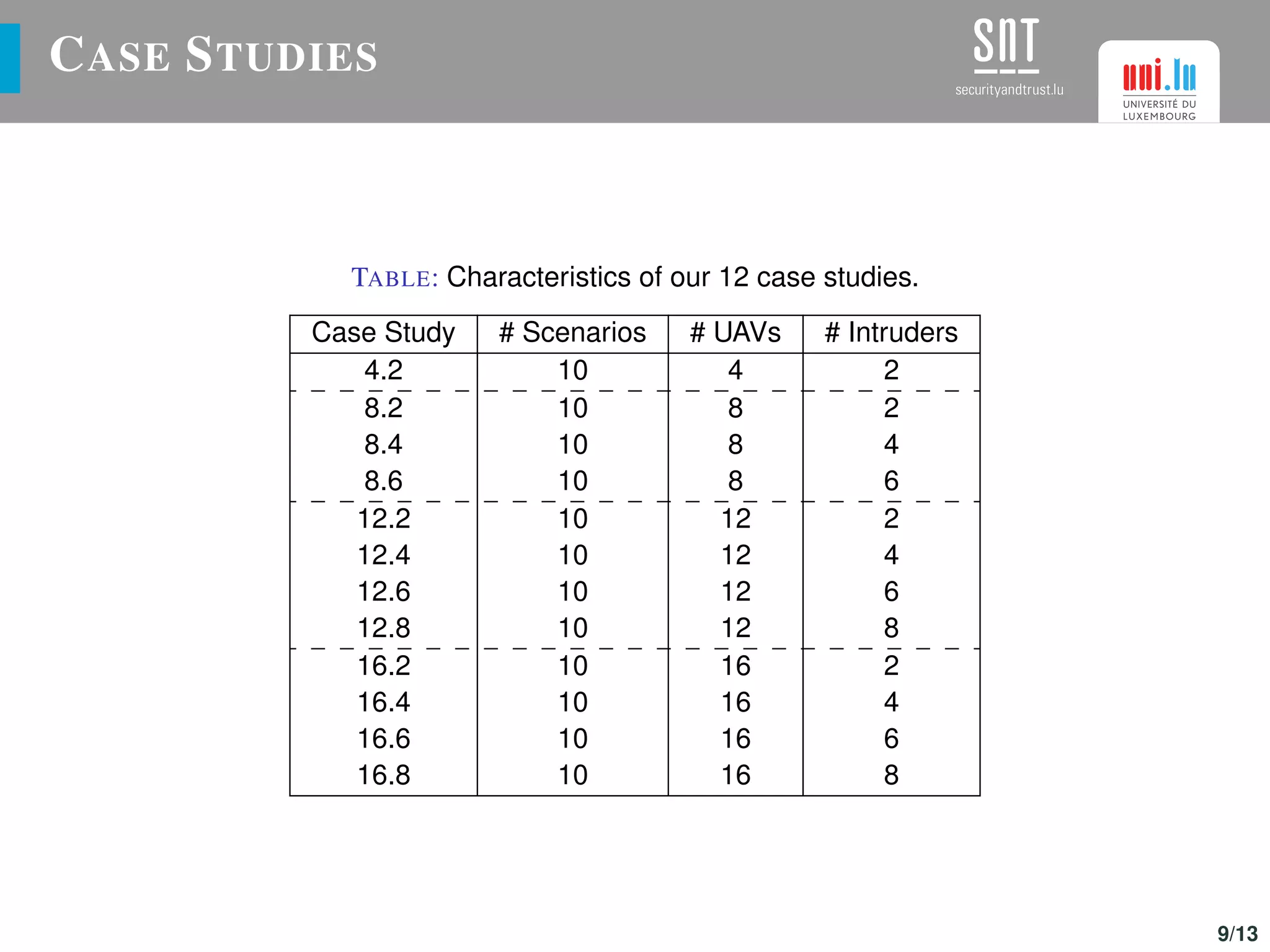
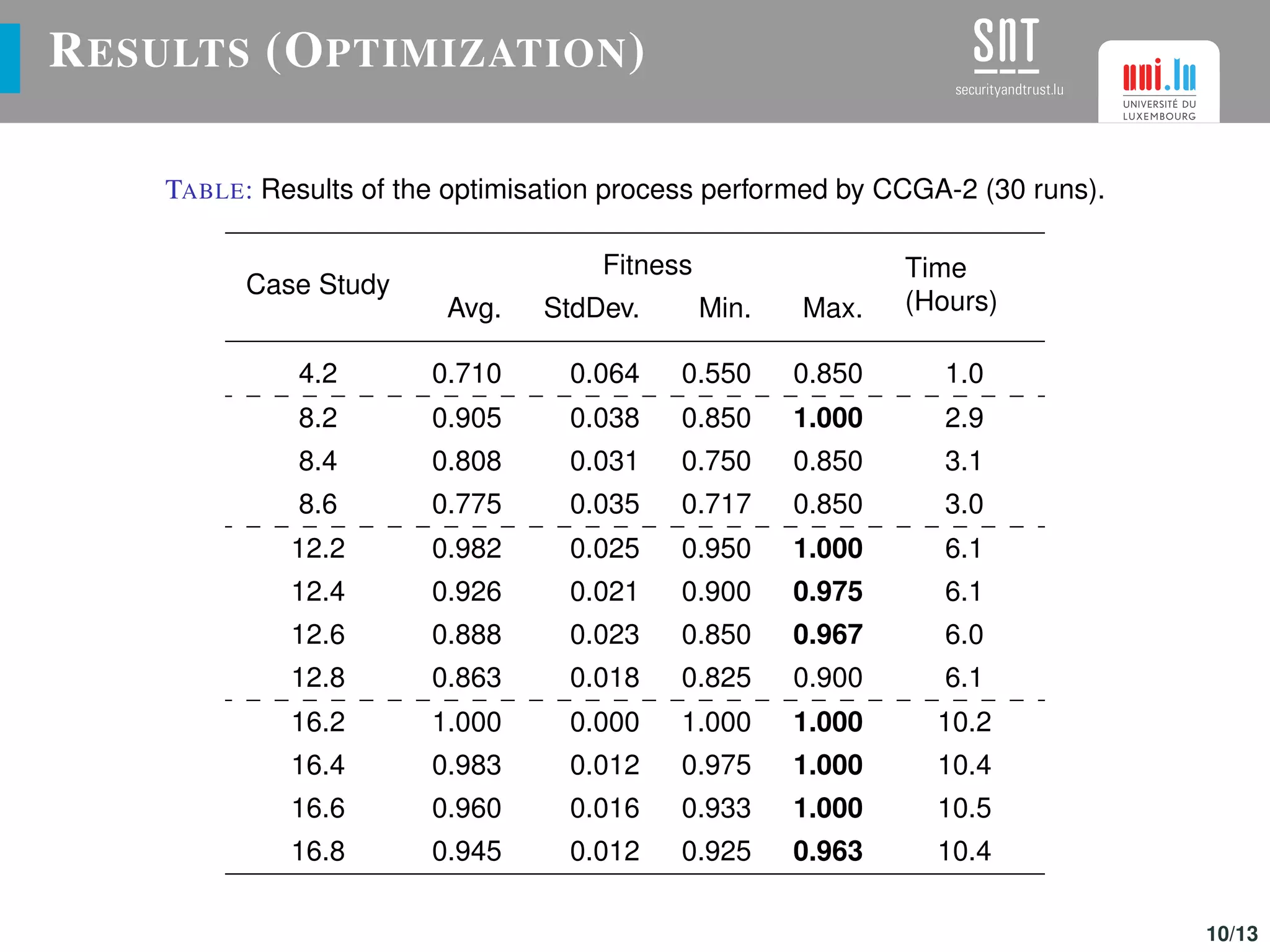
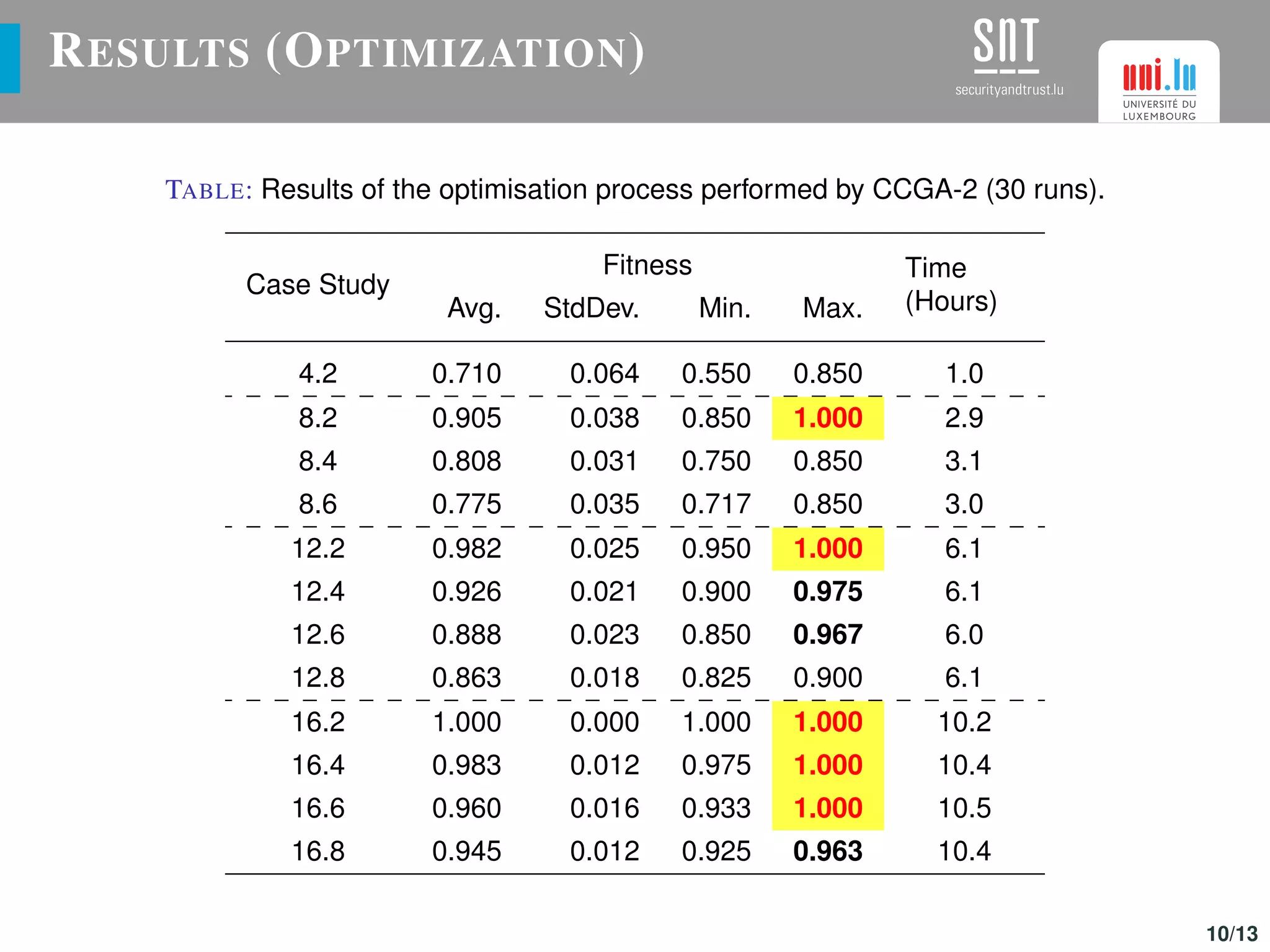
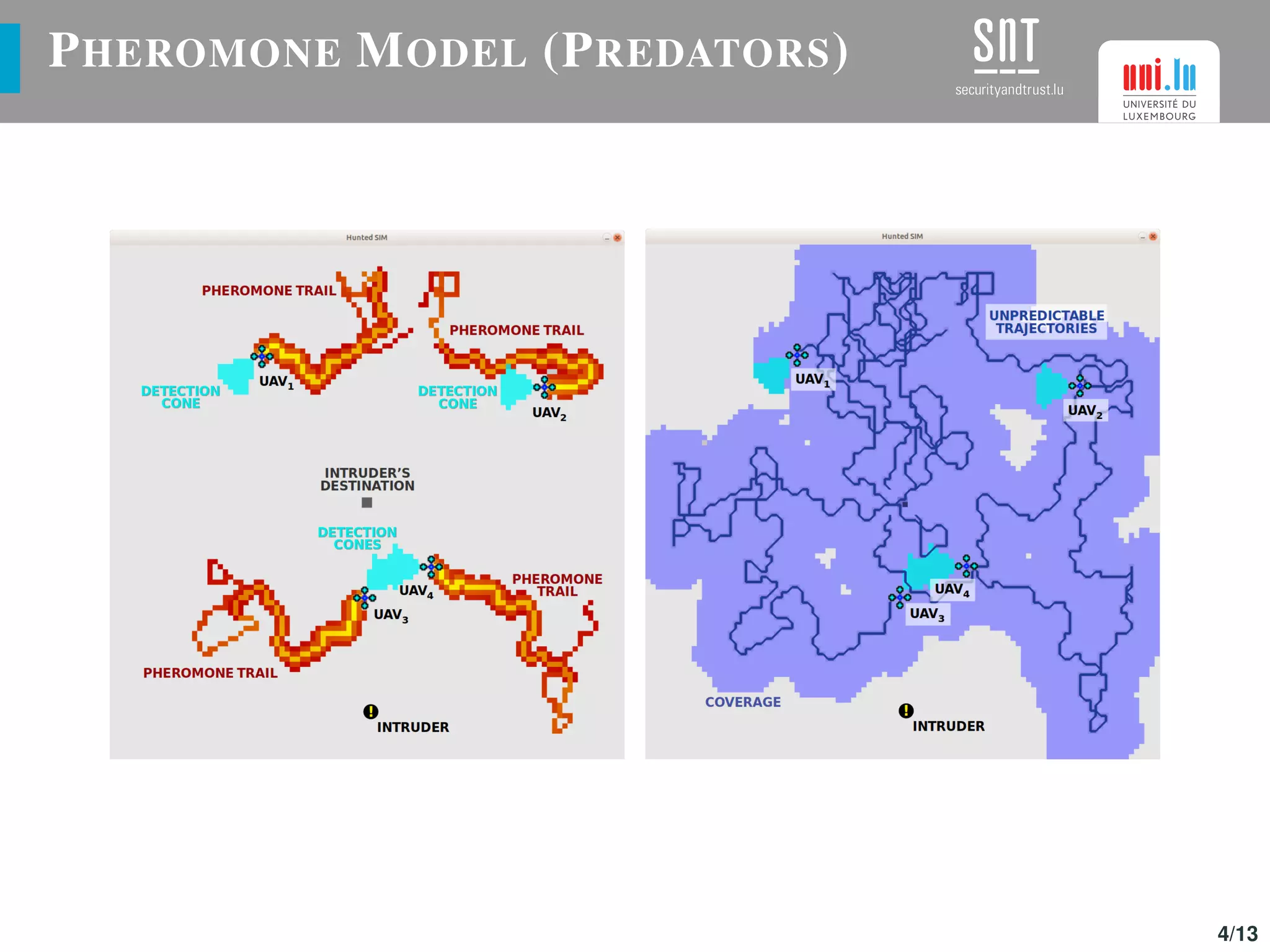
The document discusses the optimization of UAV (drone) swarms for intruder detection using the CACO model and genetic algorithms. It presents a comprehensive introduction to UAV applications, the model's parameters, results from optimization, and future enhancements planned for inter-swarm collaborations. The research indicates improved detection rates and plans to expand the model's use across different scenarios.






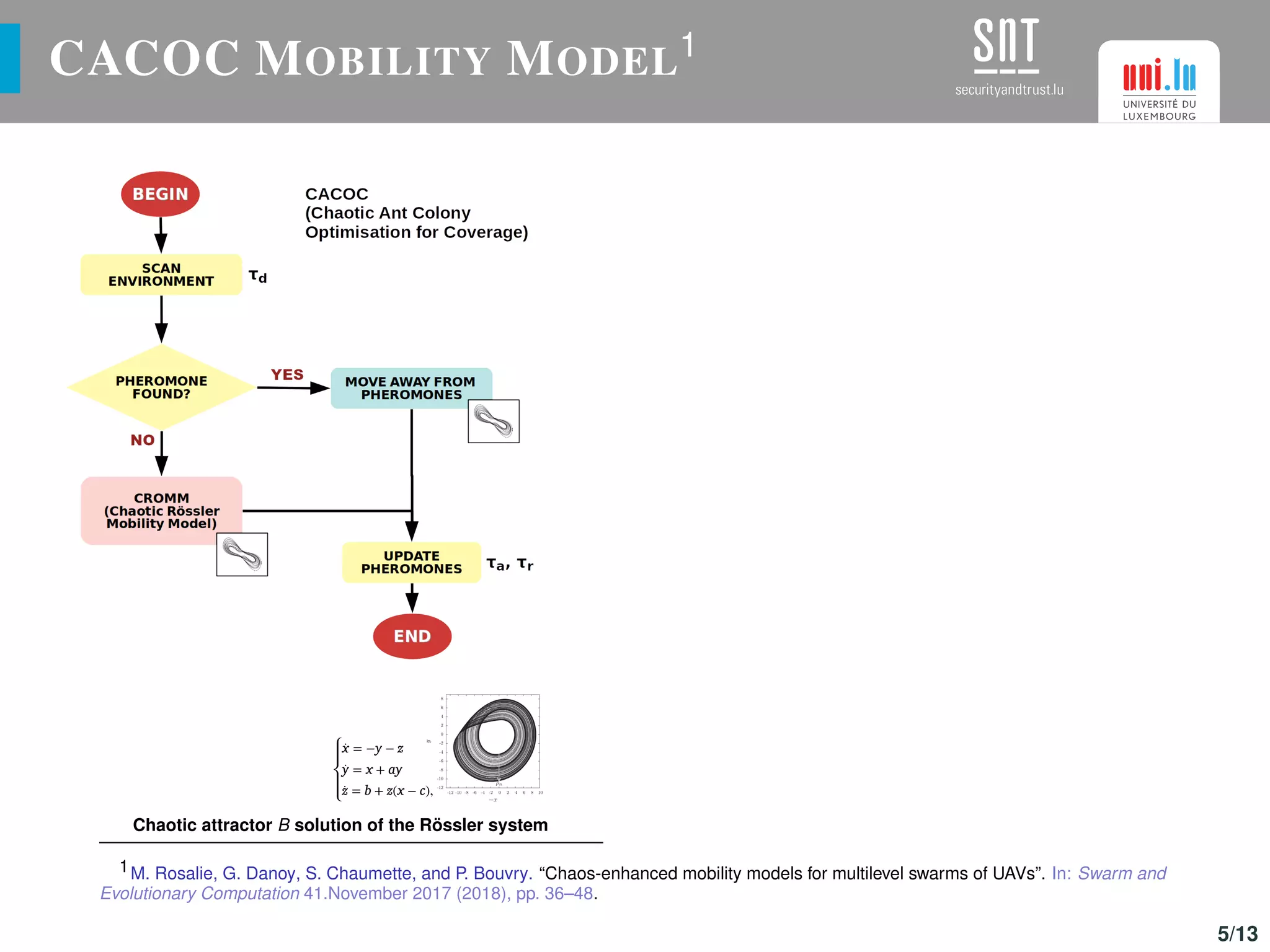
![CACOC MOBILITY MODEL1
Chaotic attractor B solution of the Rössler system
TABLE: Parameters proposed for CACOC.
Parameter Units Range
Pheromone amount (τa) % [1 − 100]
Pheromone radius (τr ) cells [0.5 − 2.5]
Pheromone scan depth (τd ) cells [1 − 10]
1M. Rosalie, G. Danoy, S. Chaumette, and P. Bouvry. “Chaos-enhanced mobility models for multilevel swarms of UAVs”. In: Swarm and
Evolutionary Computation 41.November 2017 (2018), pp. 36–48.
5/13](https://image.slidesharecdn.com/ola-200225133027/75/Optimizing-the-Performance-of-an-Unpredictable-UAV-Swarm-for-Intruder-Detection-17-2048.jpg)