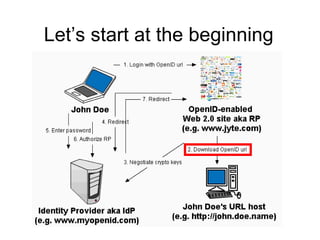
This document summarizes security issues with single sign-on systems like OpenID and provides recommendations. It describes 7 attacks that can occur: (1) observing username/password combinations, (2) choosing misleading URLs, (3) exploiting weaknesses in crypto protocols, (4) phishing through malicious sites, (5) privacy issues from sharing login data, (6) replay attacks despite nonces, and (7) cross-site request forgery. While having a single sign-on is useful, the document argues flexibility must be reduced and security strengthened to prevent these attacks, such as using client certificates. Overall, OpenID can work but needs more focus on privacy and security issues.
![Single Sign-On for the Internet: A Security Story [email_address] [email_address] BlackHat USA, Las Vegas 2007](https://image.slidesharecdn.com/openid-security4030/85/OpenID-Security-1-320.jpg)






















































![Thanks! [email_address] [email_address] Try it today. http://www.openid.net/ http://www.freeyourid.com/](https://image.slidesharecdn.com/openid-security4030/85/OpenID-Security-57-320.jpg)