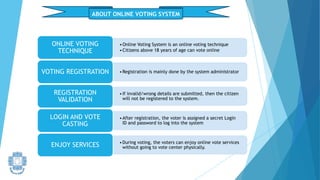
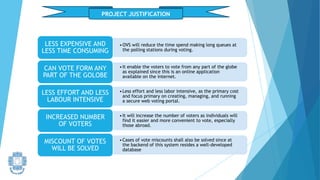
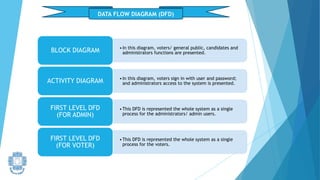
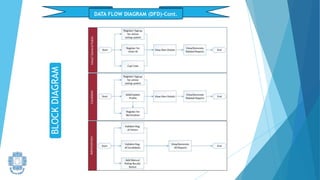
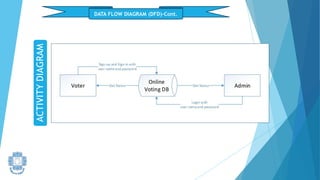
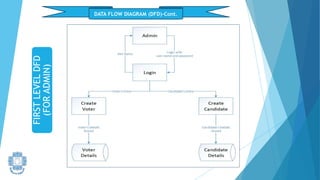
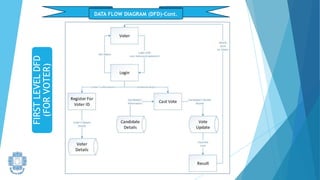
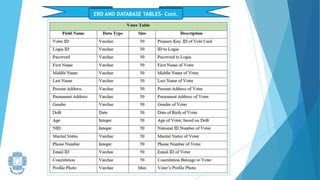
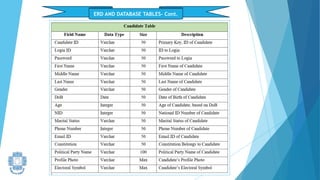
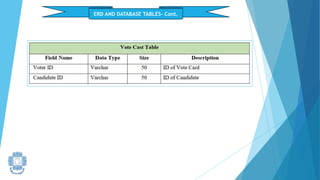
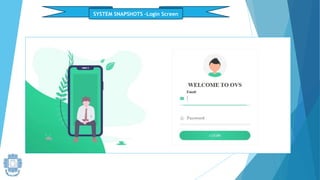
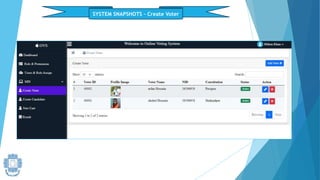
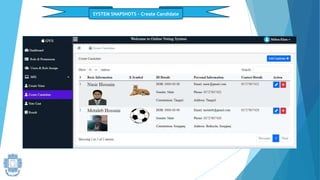
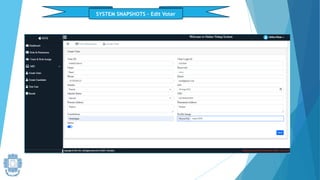
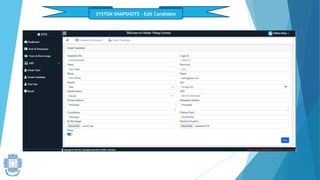
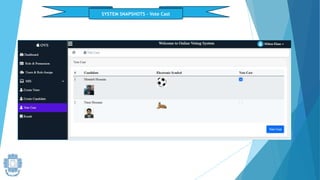
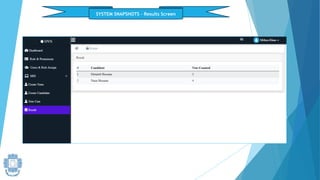
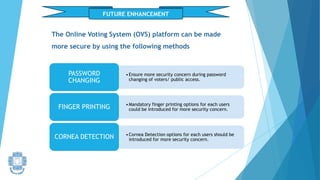
The presentation summarized an online voting system project developed by 4 students. It included an introduction to the online voting technique and its key features like registration and login. It justified the project by explaining how it would reduce time and costs while increasing voter turnout. It presented the data flow diagrams, database tables, and screenshots of the system. It discussed testing measures and security issues addressed. Potential future enhancements were proposed like improved password changing and biometric authentication.