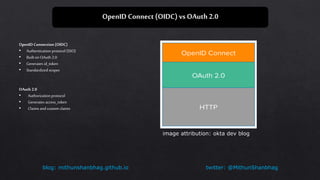
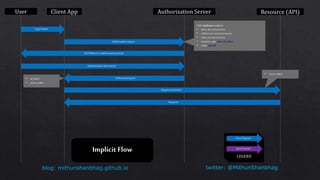
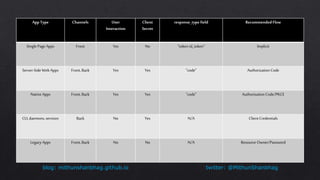
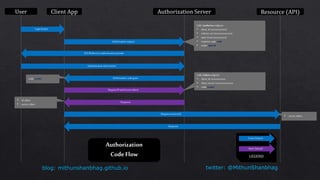
The document compares OpenID Connect (OIDC) and OAuth 2.0, explaining that OIDC is an authentication protocol built on OAuth 2.0 that generates id_tokens and is suitable for Single Sign-On (SSO), while OAuth 2.0 serves as an authorization protocol generating access_tokens. It outlines the authorization flow, including request structures for different app types, and describes various OIDC endpoints that handle user consent, token retrieval, and others. Additionally, the document covers the structure of JWT (JSON Web Tokens) indicating how signatures are generated and verified for secure communication.