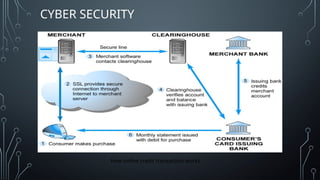
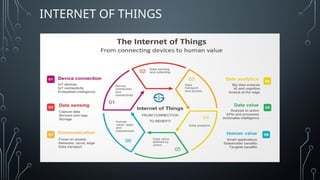
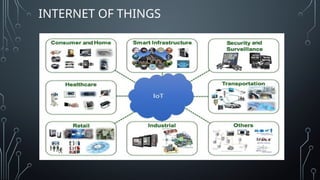
The document covers recent trends in computer science, focusing on virtual reality (VR), augmented reality (AR), mixed reality (MR), cybersecurity, and the Internet of Things (IoT). It explains VR as an immersive experience, AR as enhancing real-world views with digital information, and MR as combining physical and virtual elements. Additionally, it discusses the importance of cybersecurity in protecting sensitive data from digital threats and outlines various applications of these technologies across different sectors.