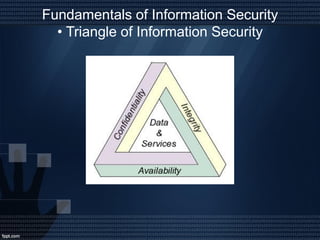
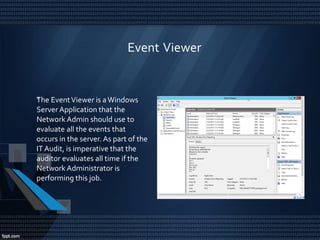
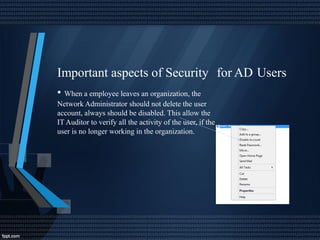
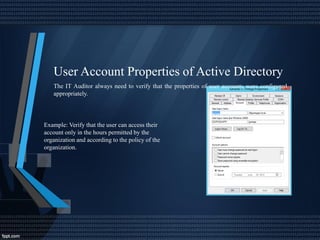
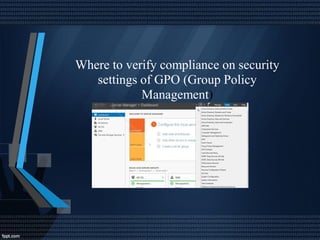
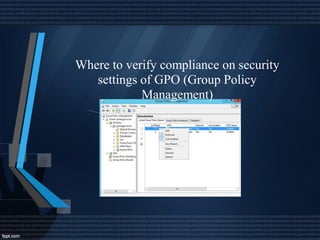
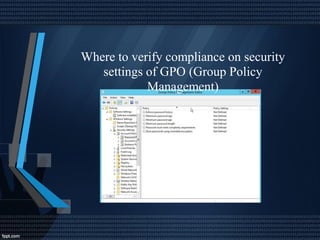
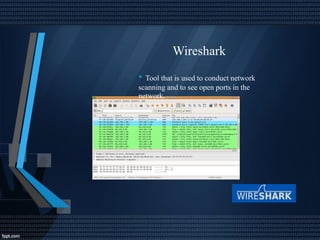
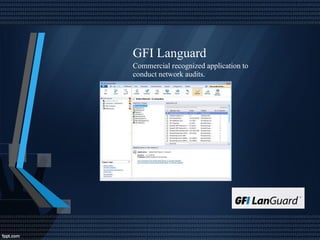
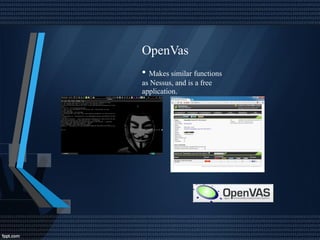
This document discusses network security and auditing Windows servers. It provides background on the speaker and defines information security. It outlines fundamentals of information security like the triangle of security. It describes important documents, regulations and standards, and the purpose of auditing Windows servers for compliance, risk reduction, health, and performance. It discusses evaluating event logs, active directory, user account properties, and group policy settings. It recommends tools for auditing like Wireshark, GFI Languard, Nessus, and OpenVas and maintaining server documentation, backups, and patches.