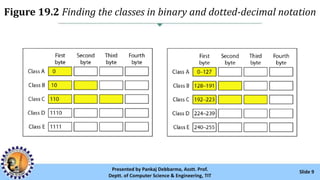
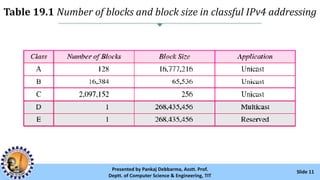
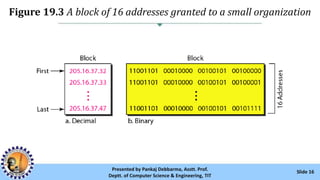
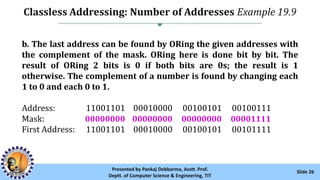
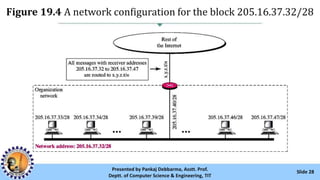
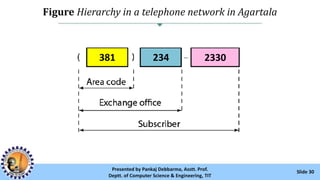
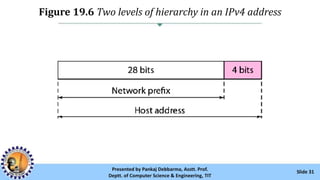
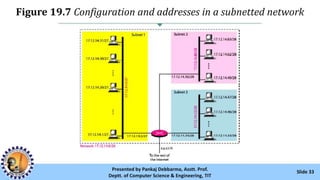
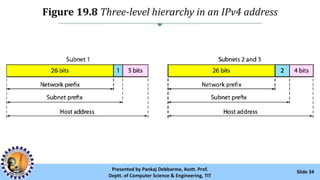
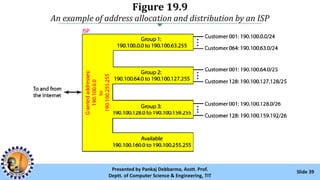
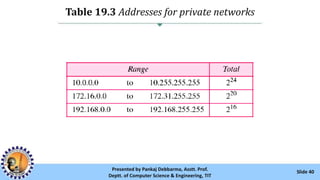
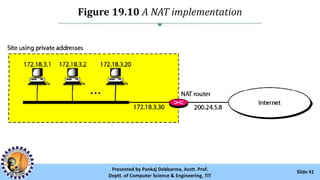
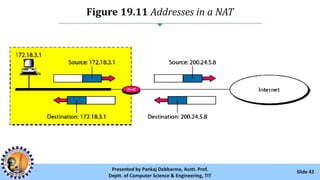
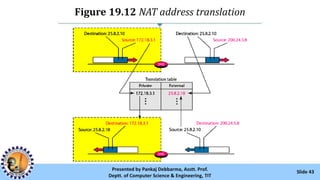
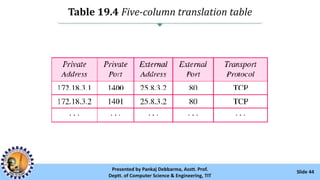
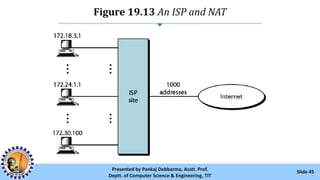
The document provides an overview of IPv4 addressing, detailing its structure as a 32-bit address that uniquely identifies devices on the internet. It covers the conversion of IPv4 addresses between binary and dotted-decimal formats, common errors in address formatting, and the principles of classful and classless addressing. Additionally, it discusses address allocation by Internet Service Providers (ISPs) and includes practical examples of subnetting and hierarchical addressing.