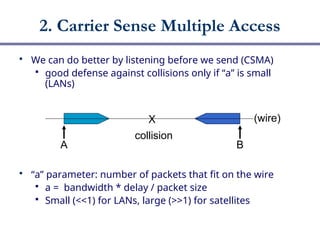
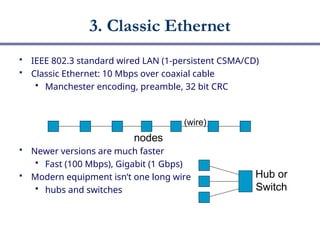
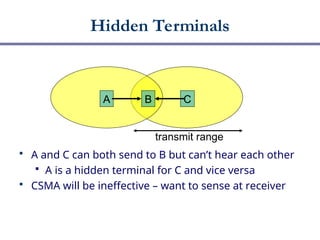
The document discusses multiple access networks, focusing on how various parties can share a communication medium, specifically highlighting medium access control (MAC) protocols. It covers protocols like Aloha, CSMA variants, and Classic Ethernet, explaining their functionalities and efficiencies, particularly in wired vs. wireless communications. Additionally, it addresses challenges in wireless communication such as collision detection and hidden terminals, and introduces contention-free protocols that prevent collisions through methods like token passing.