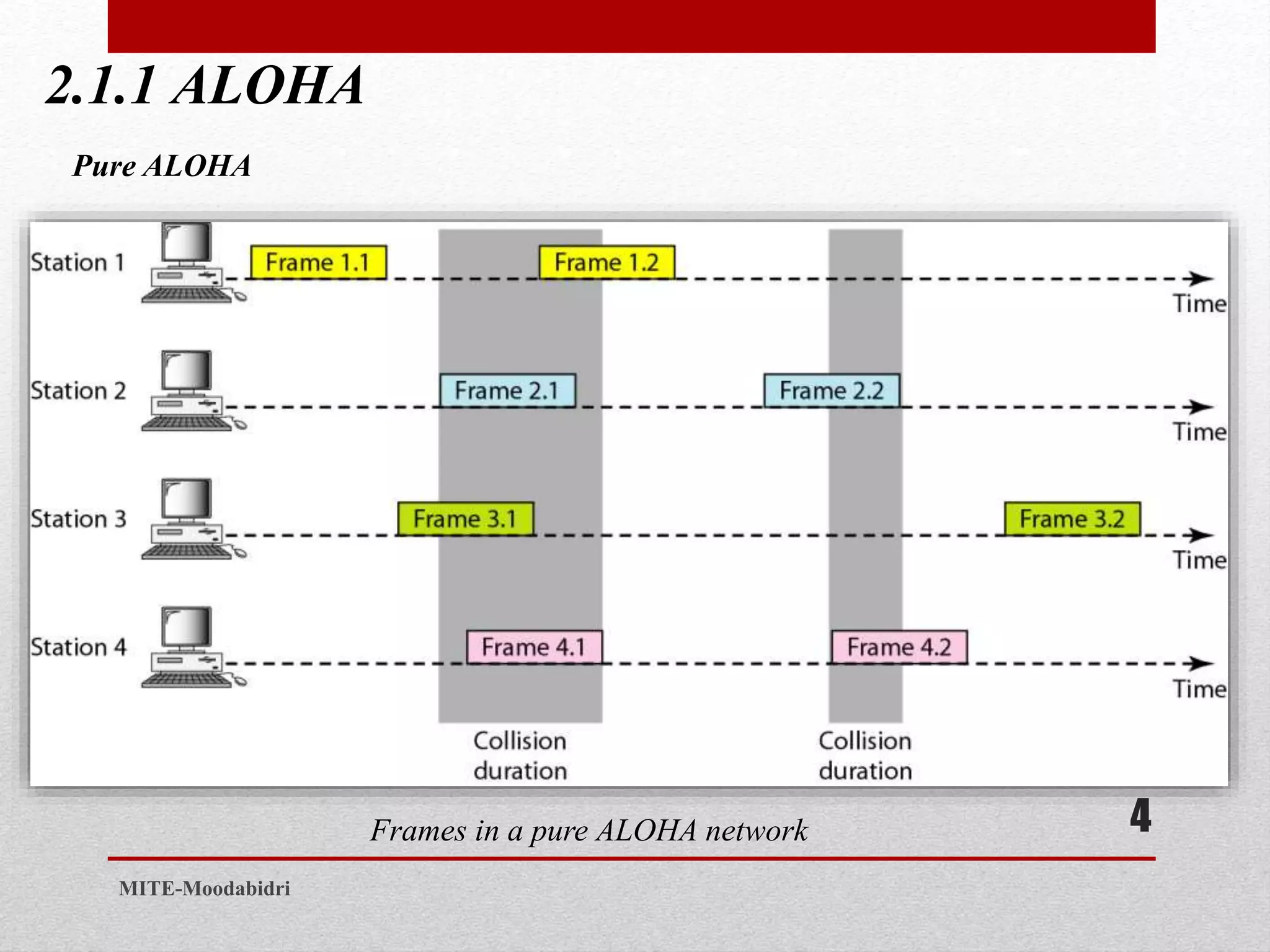
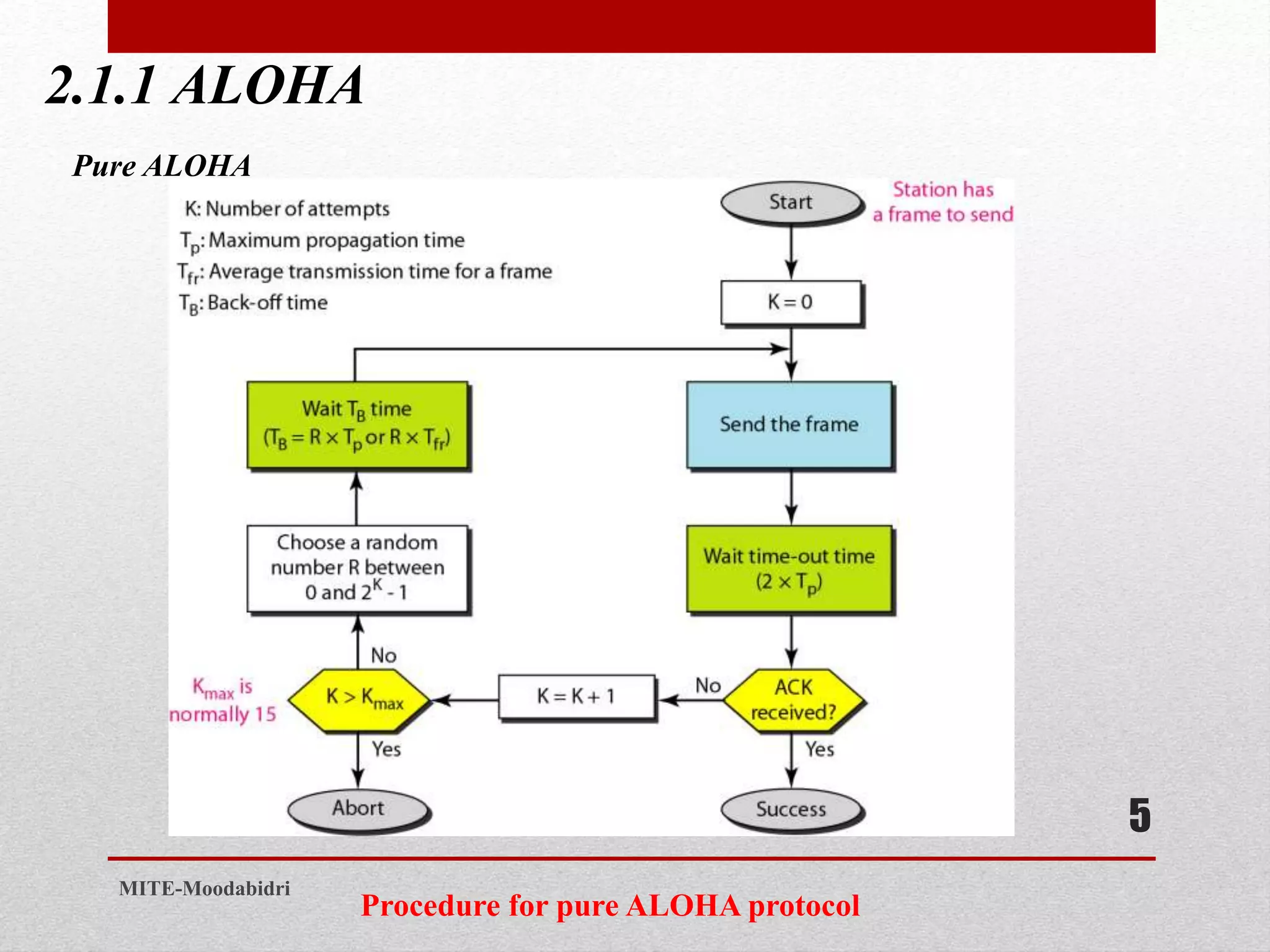
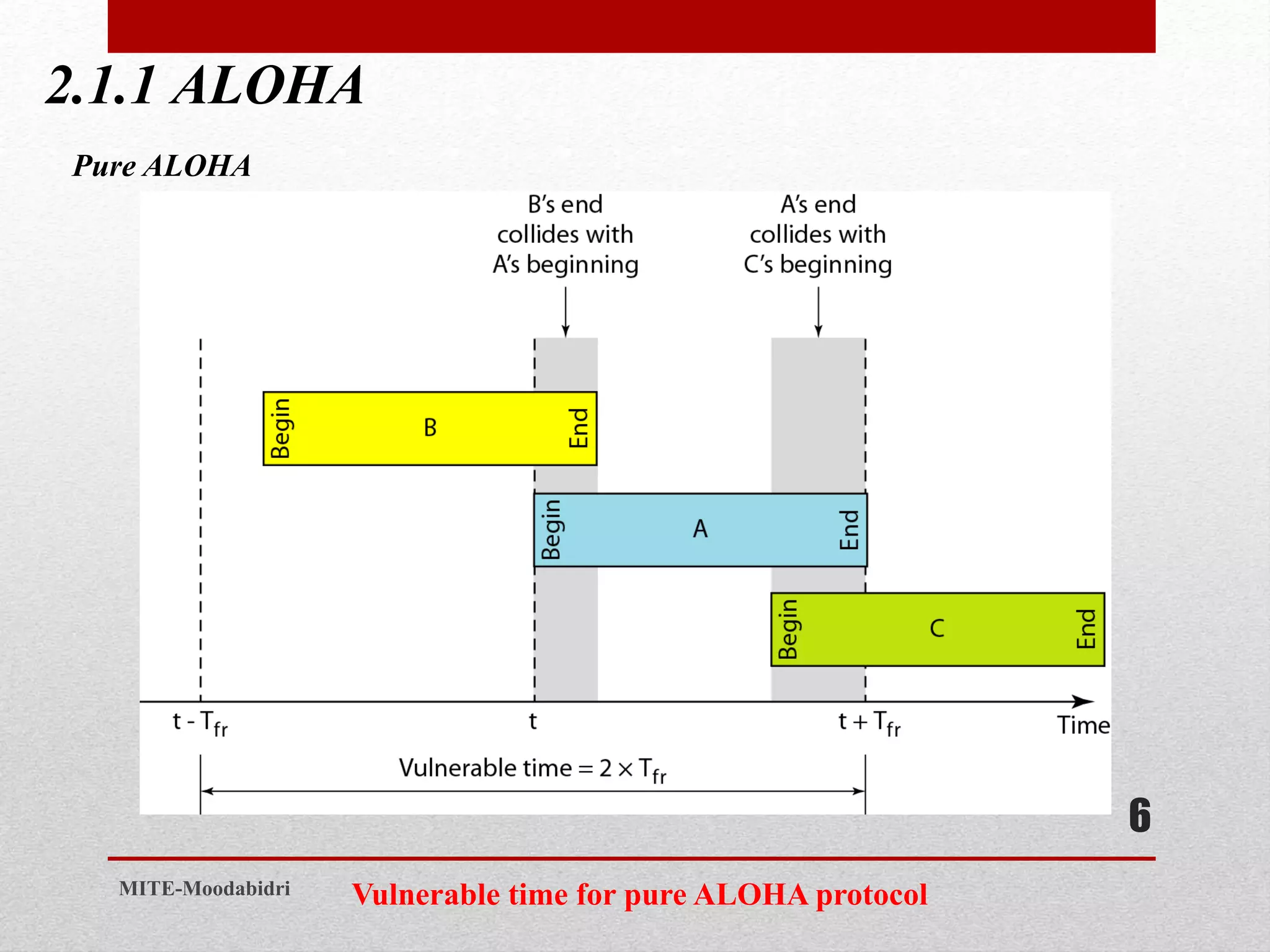
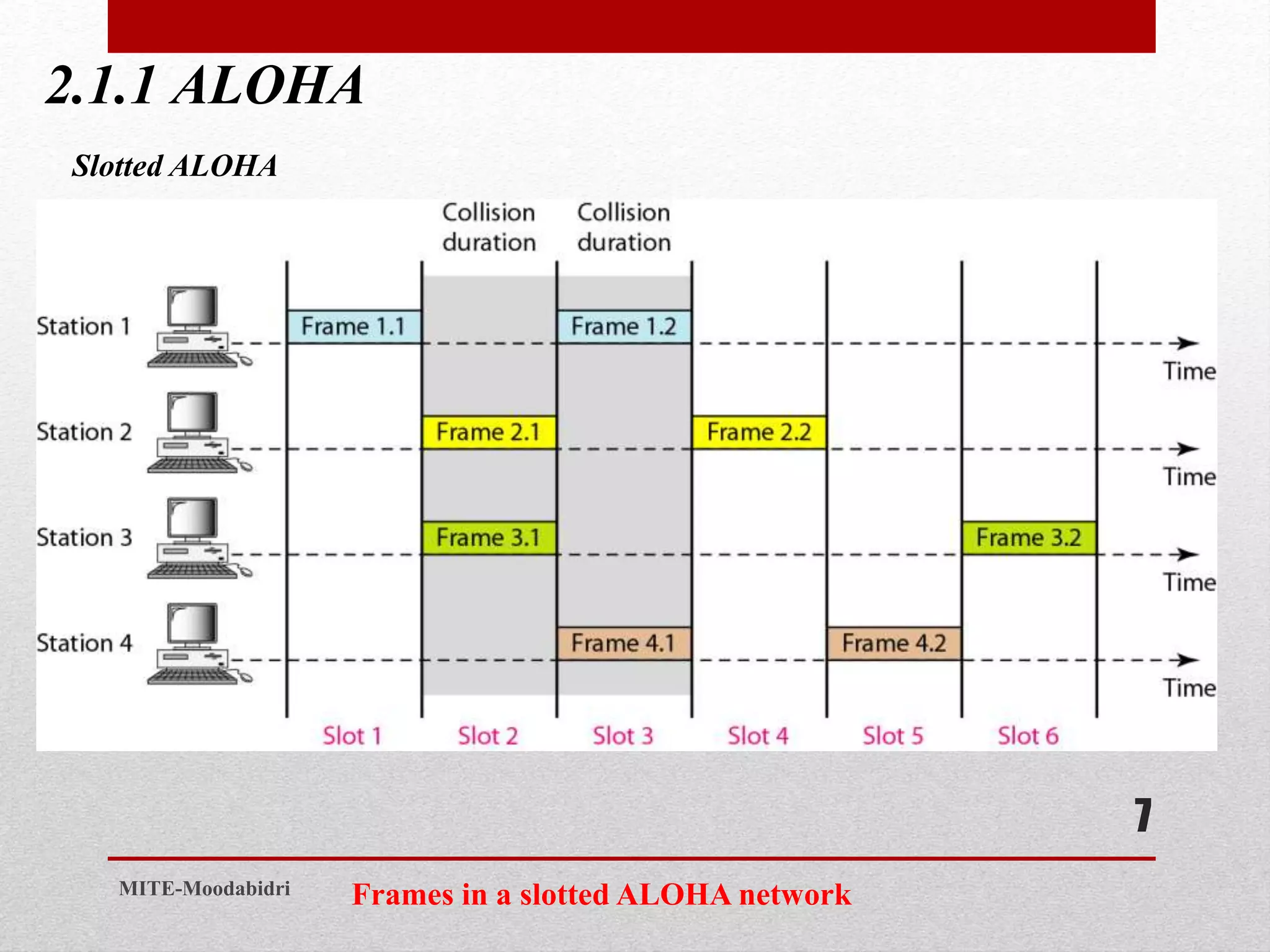
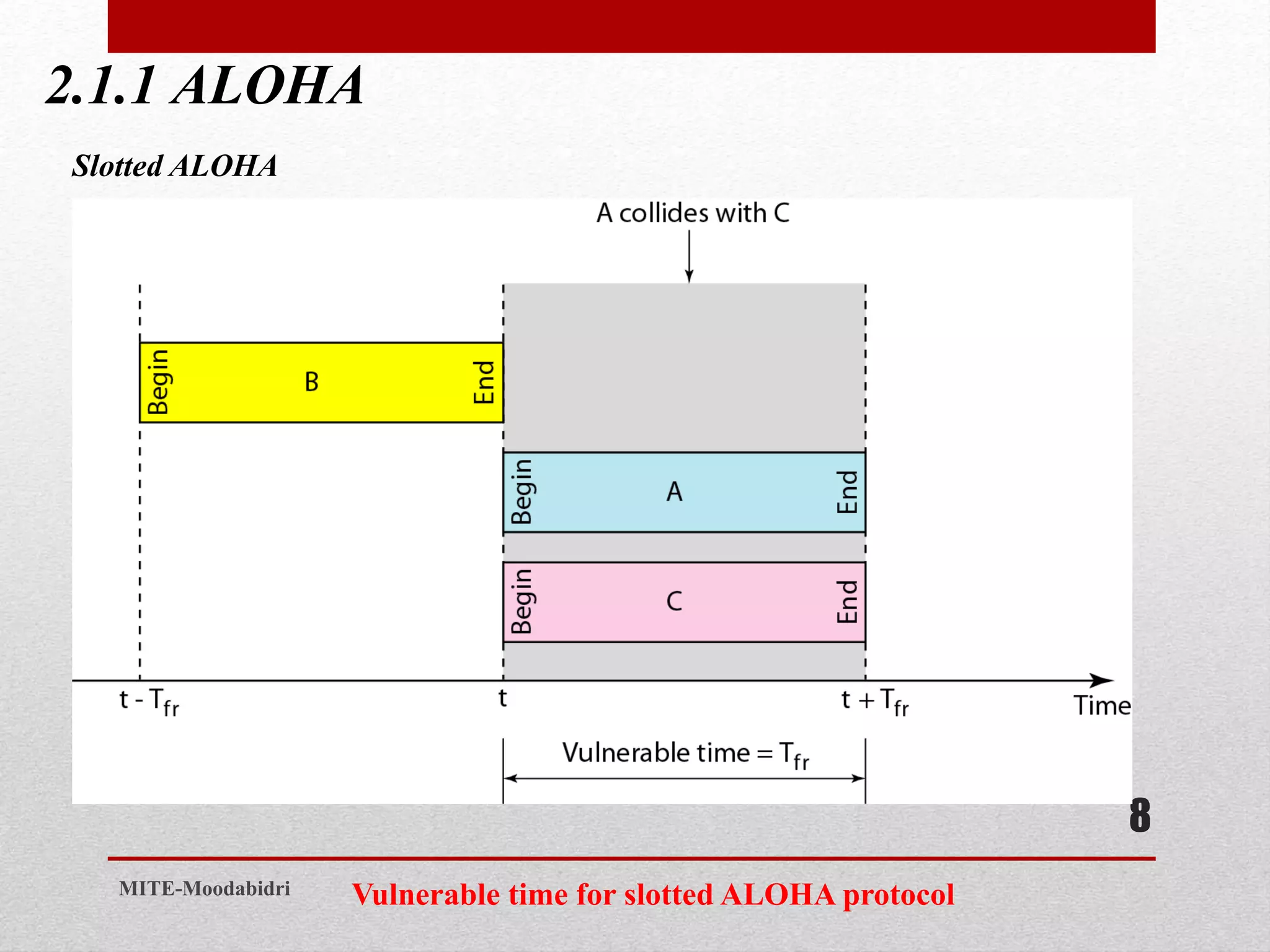
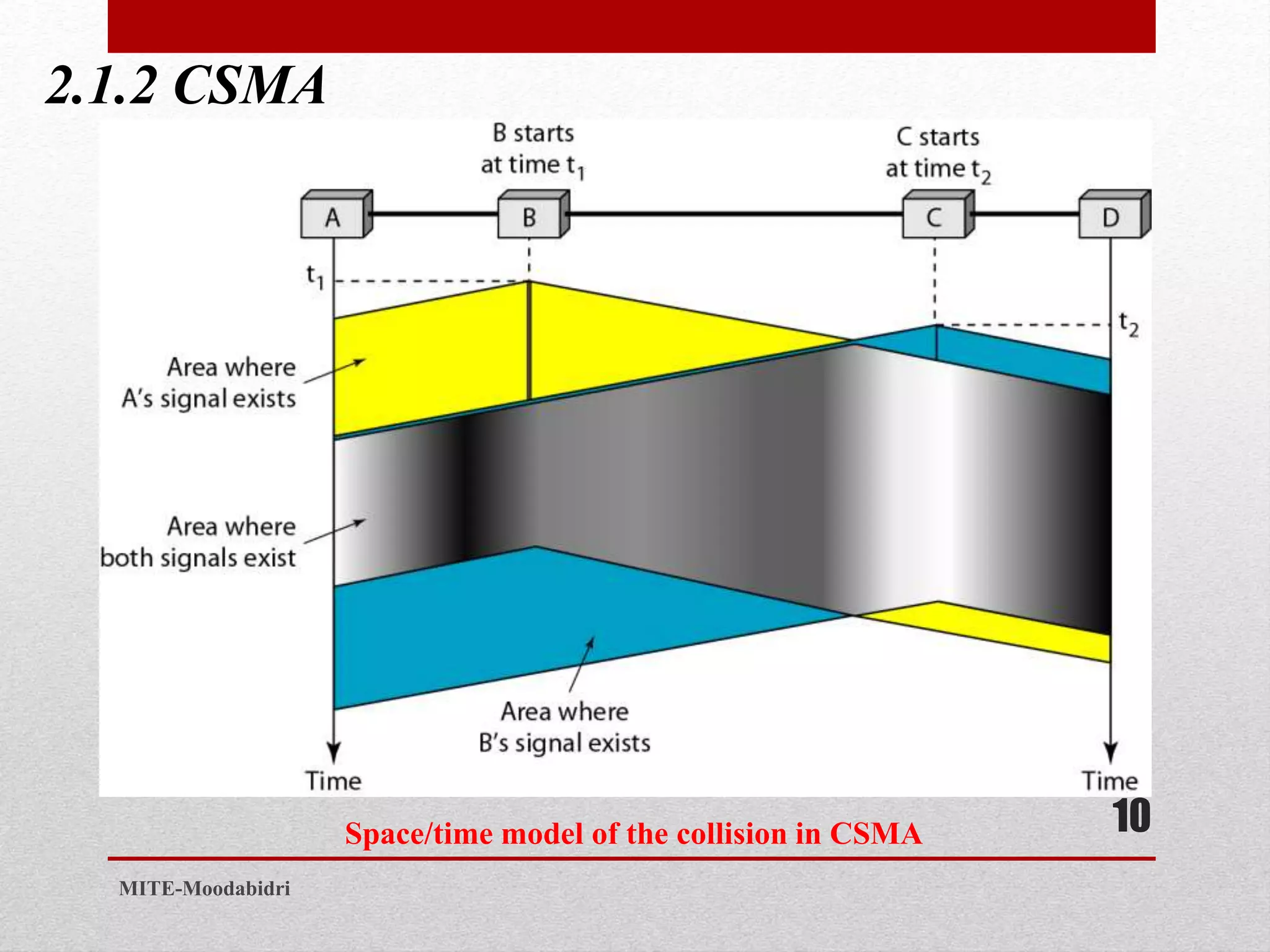
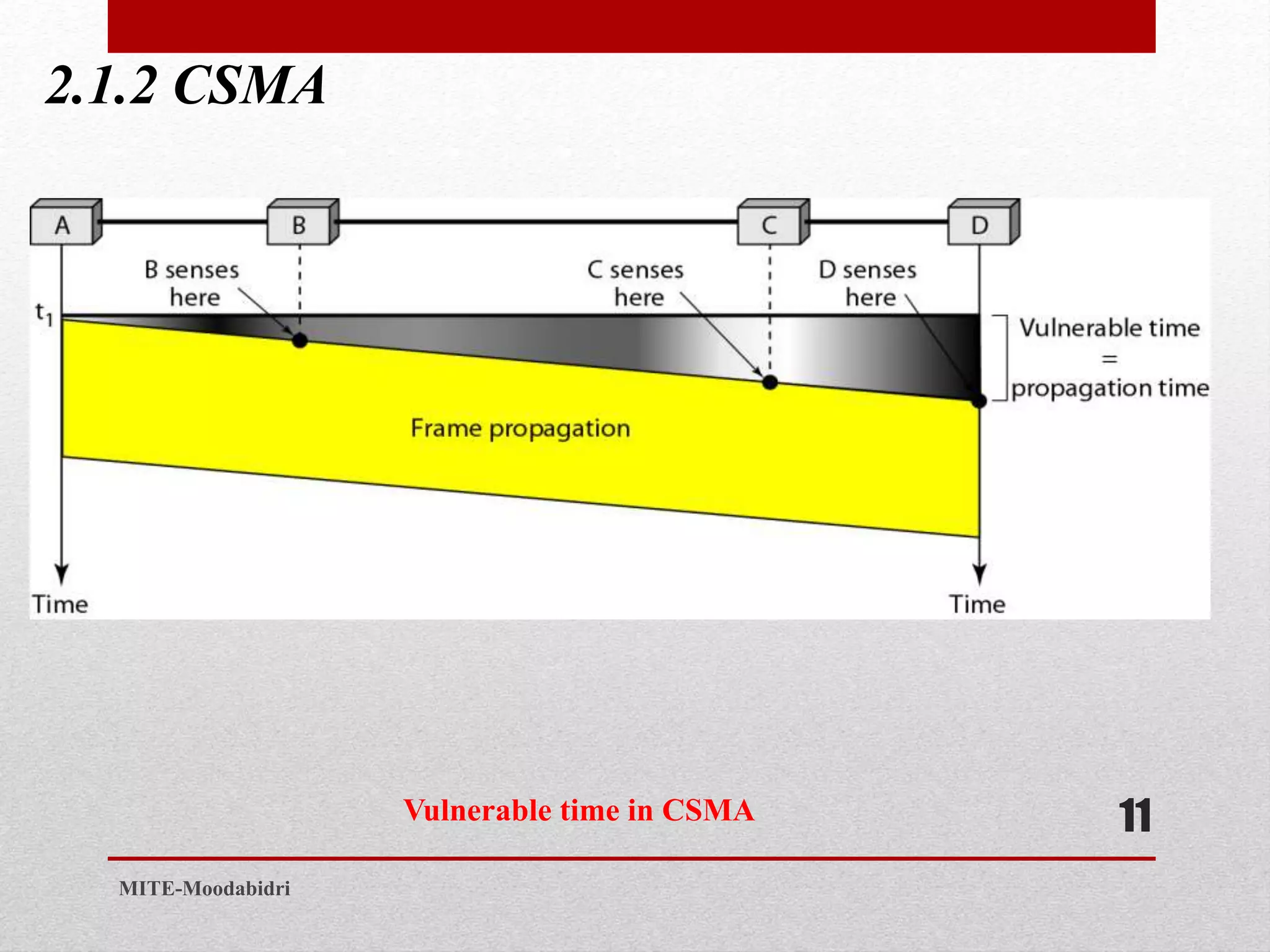
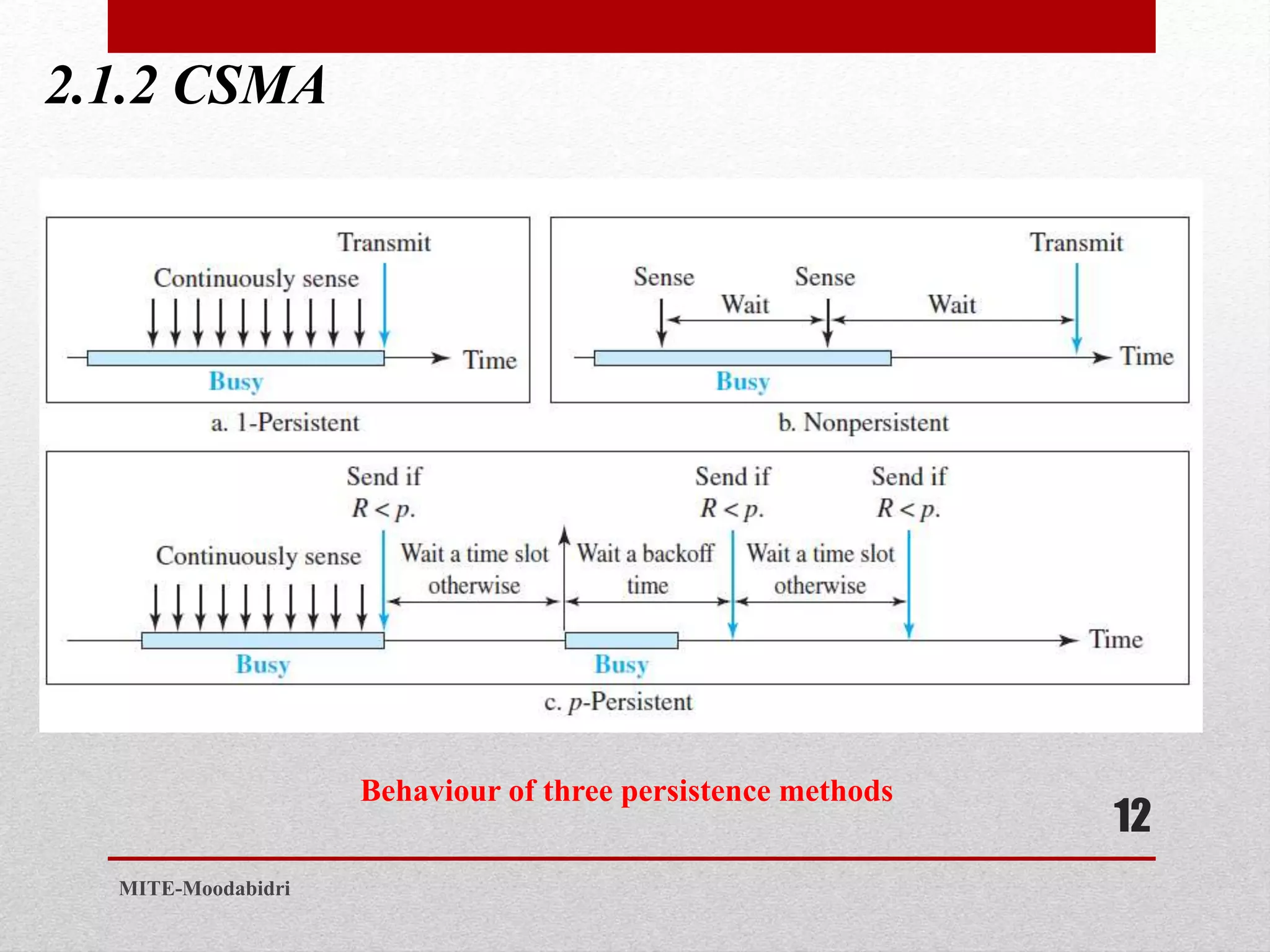
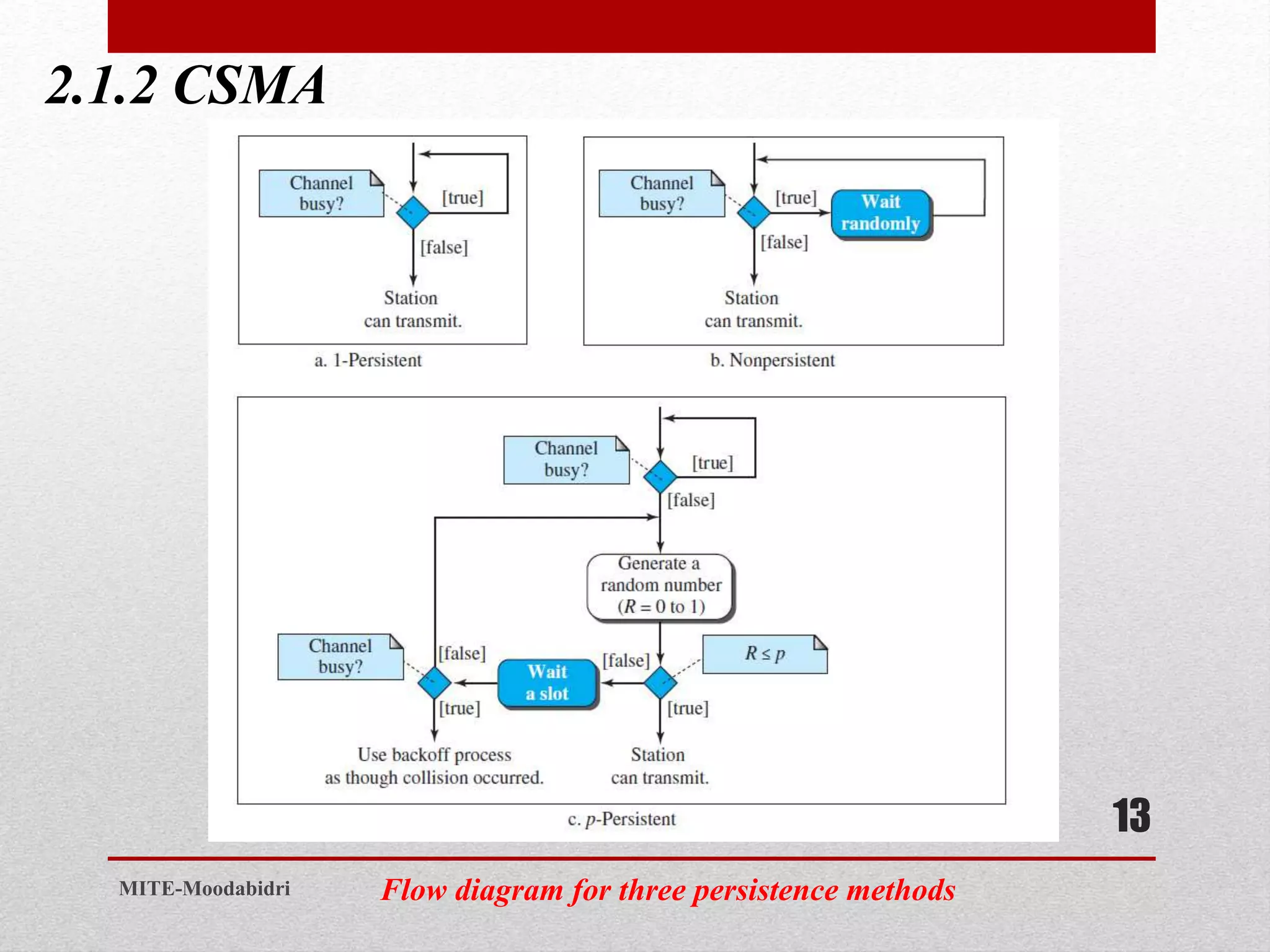
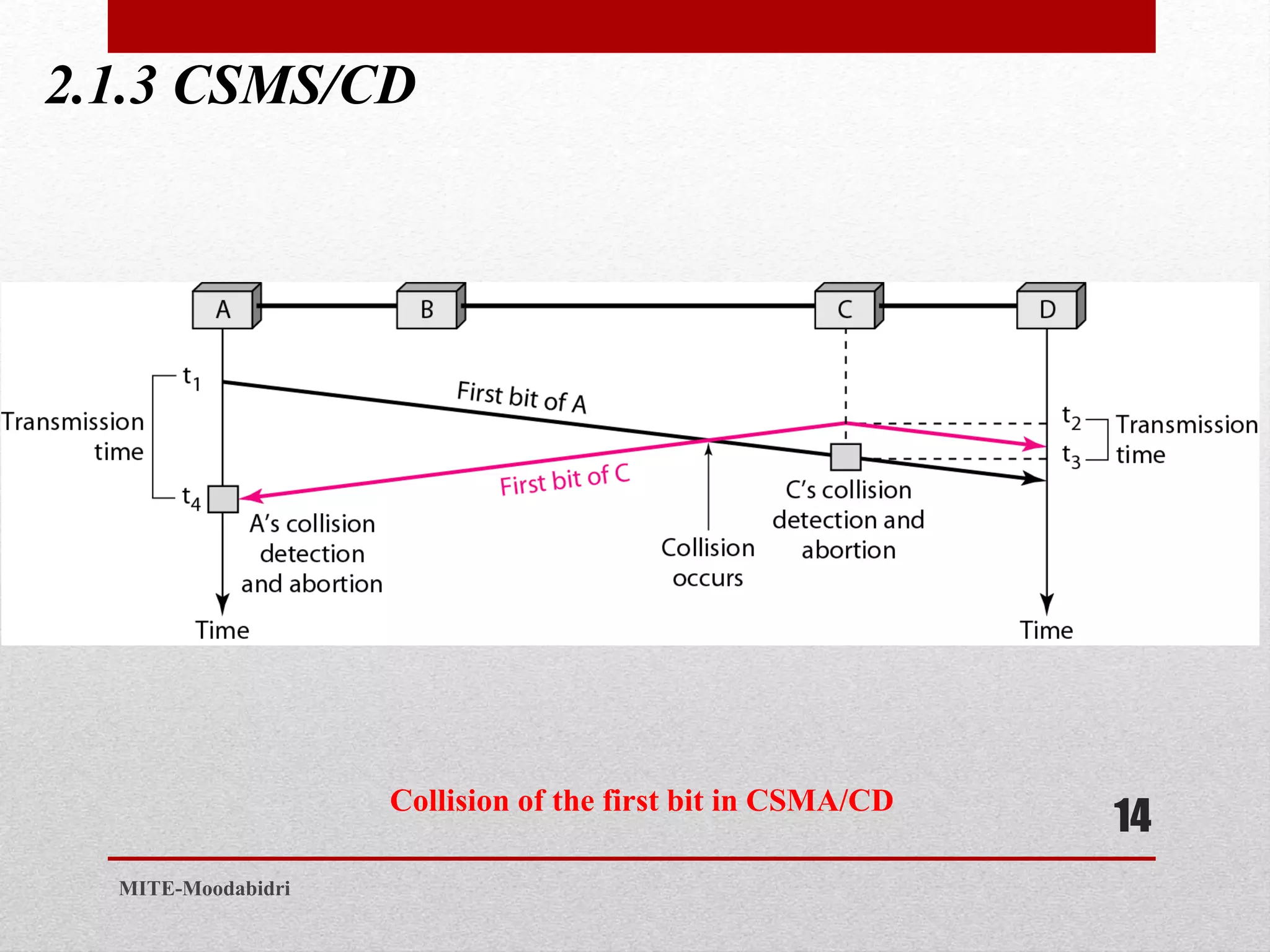
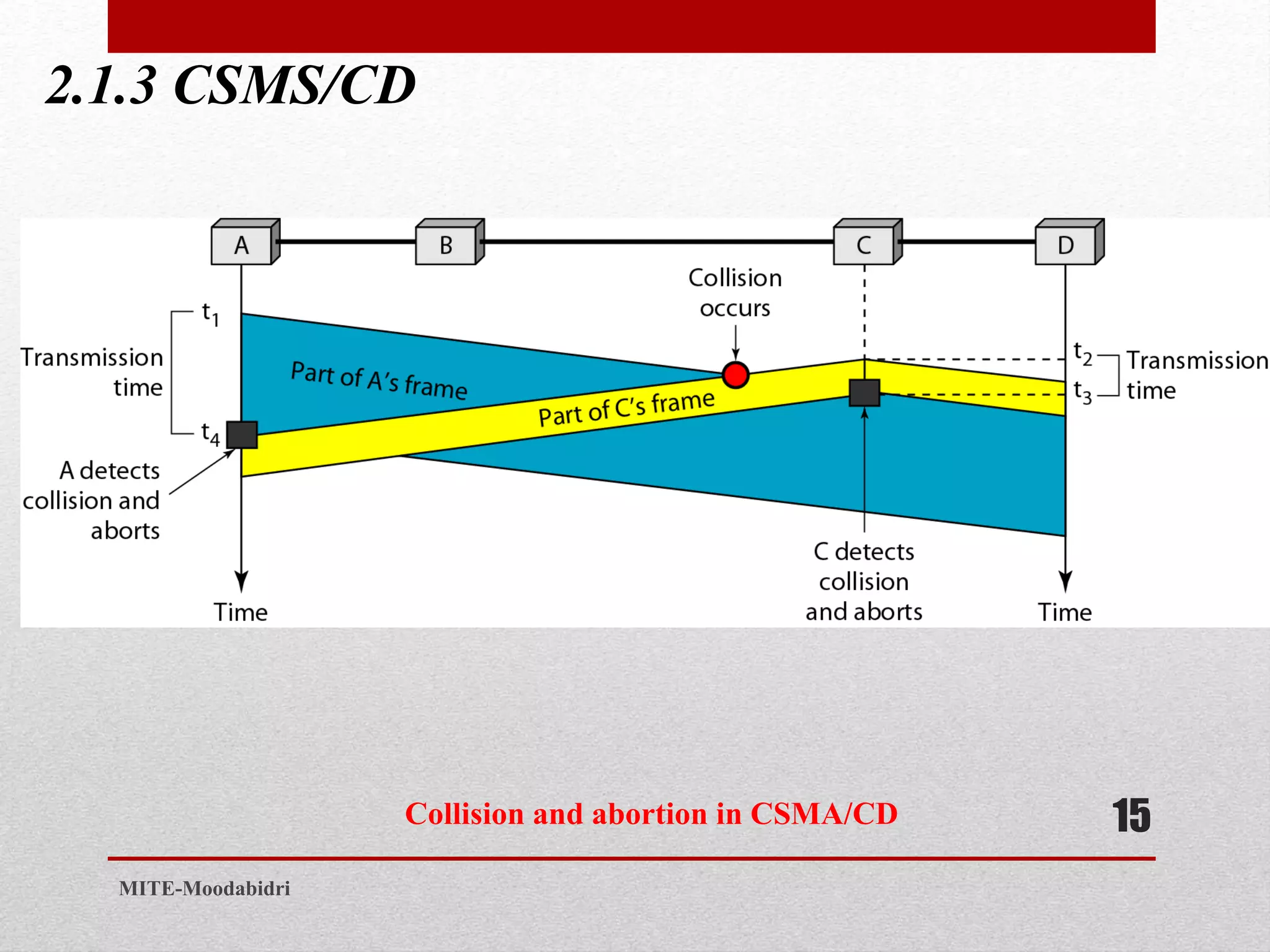
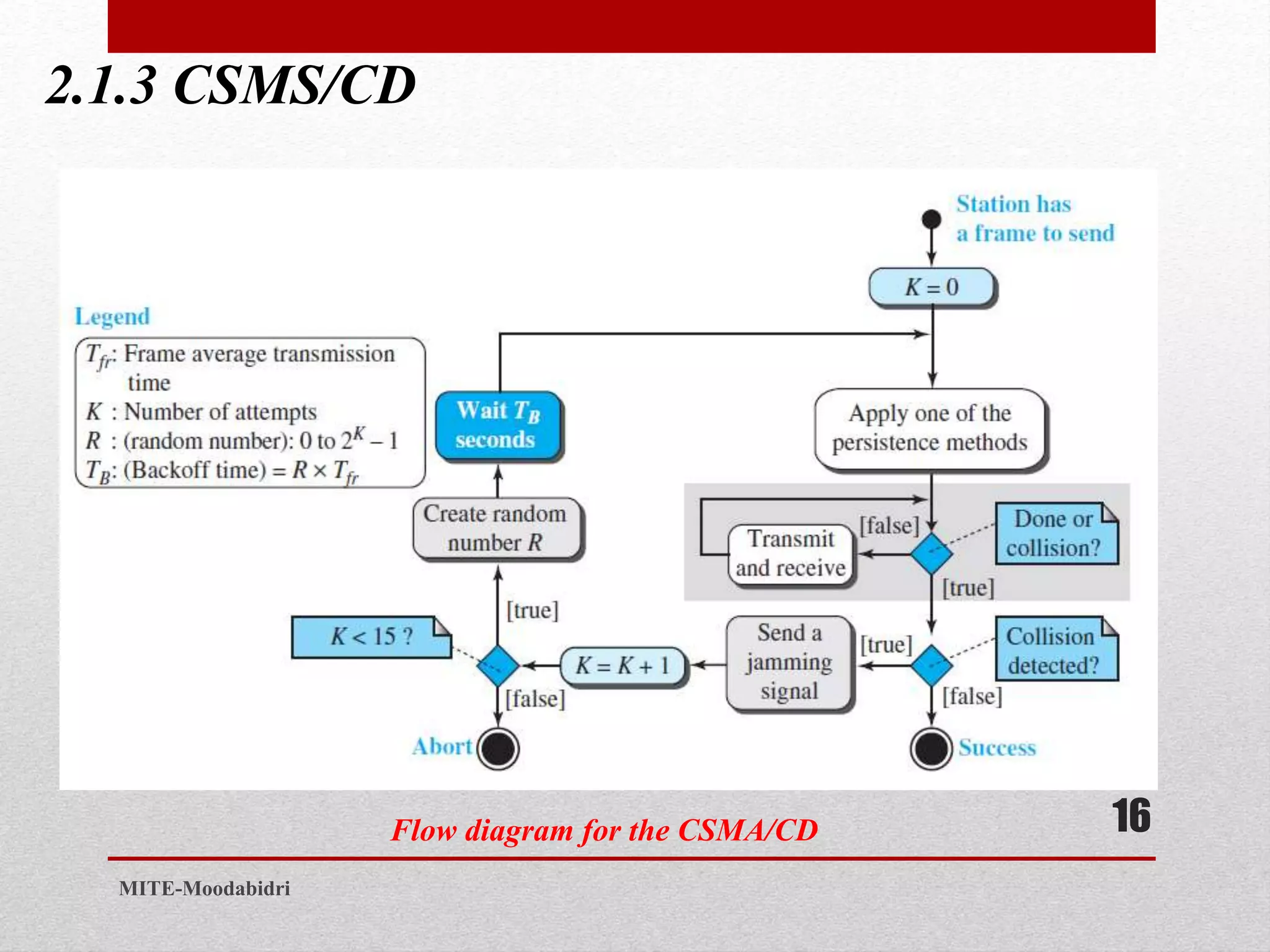
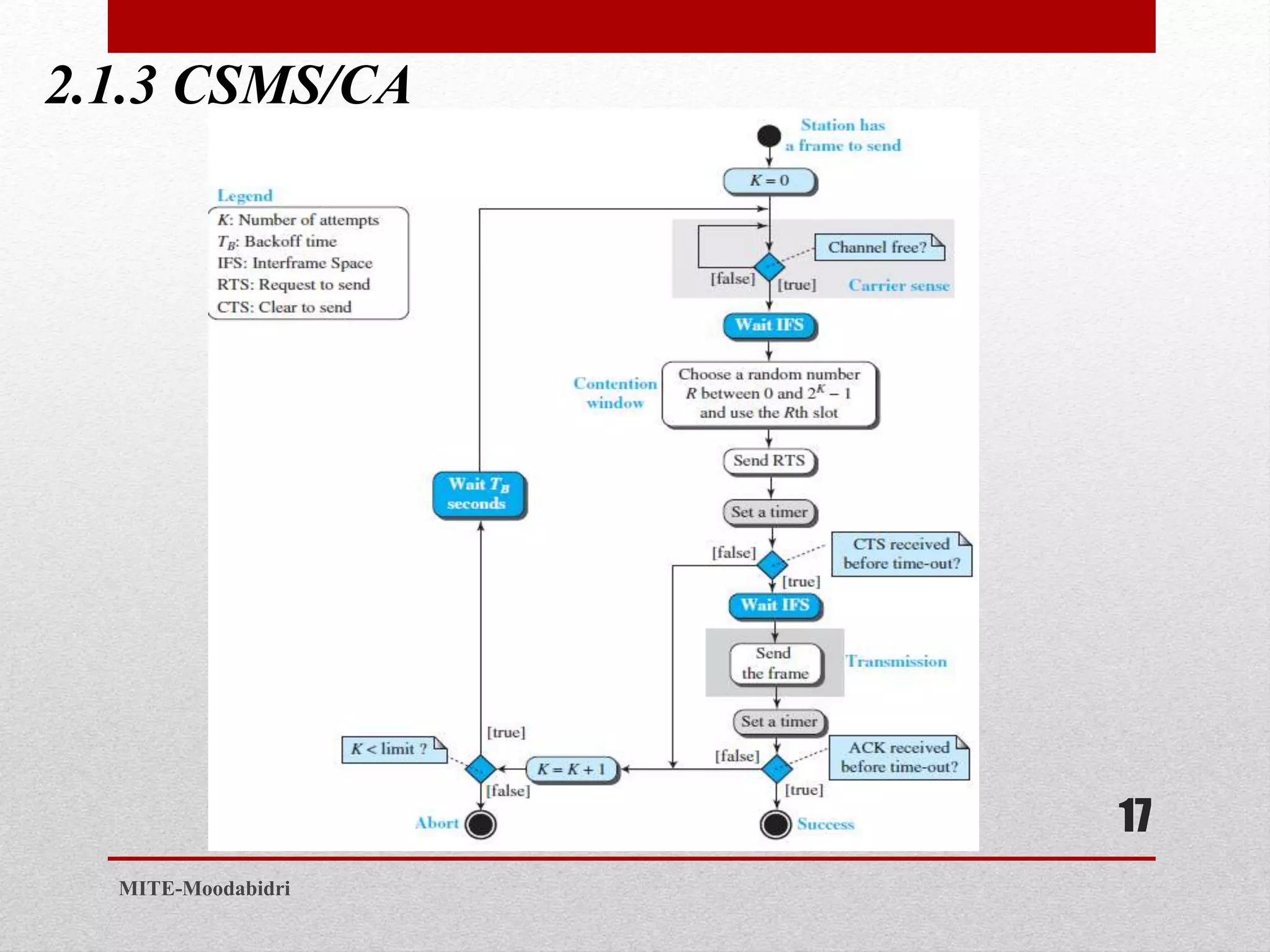
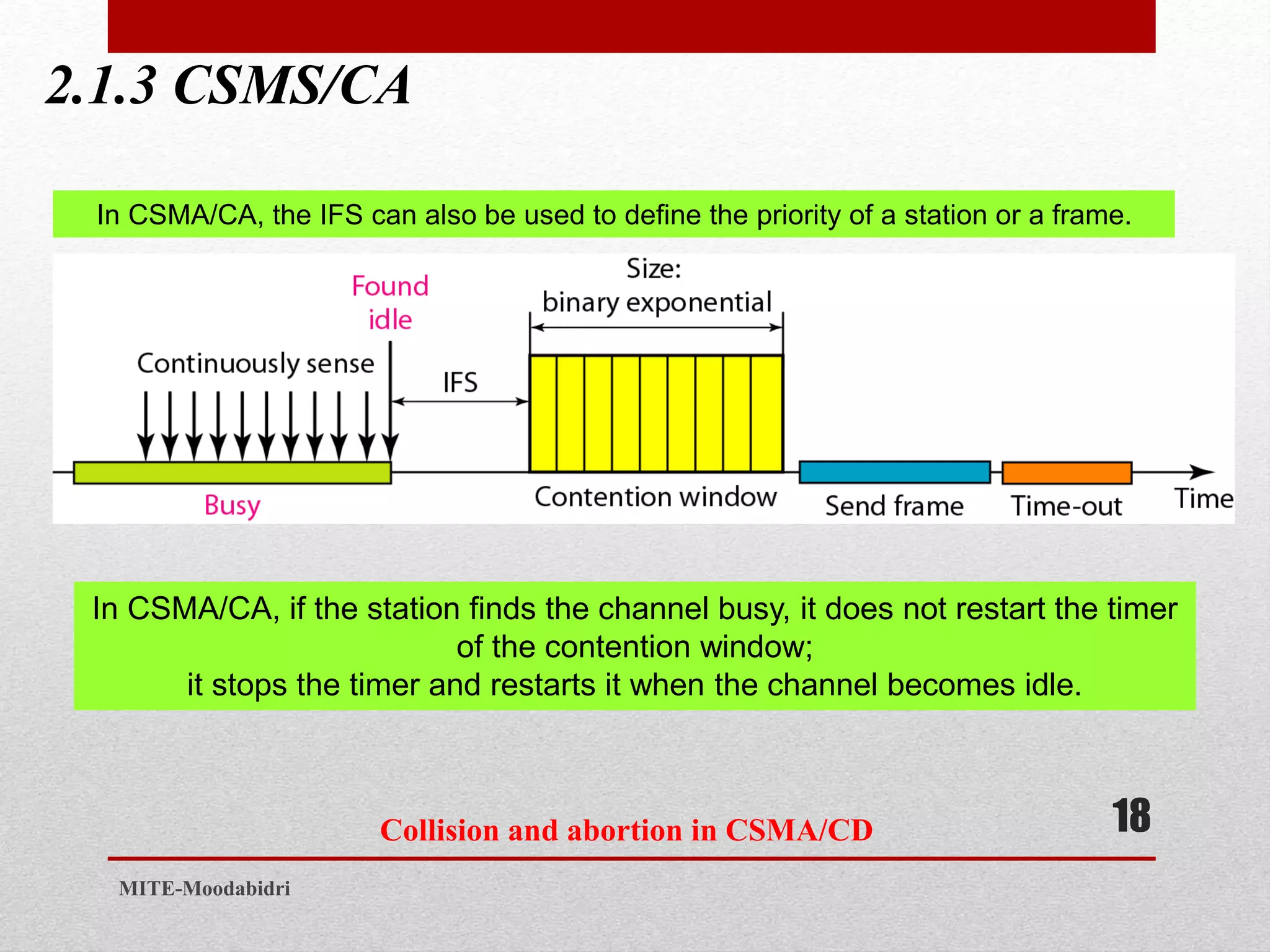
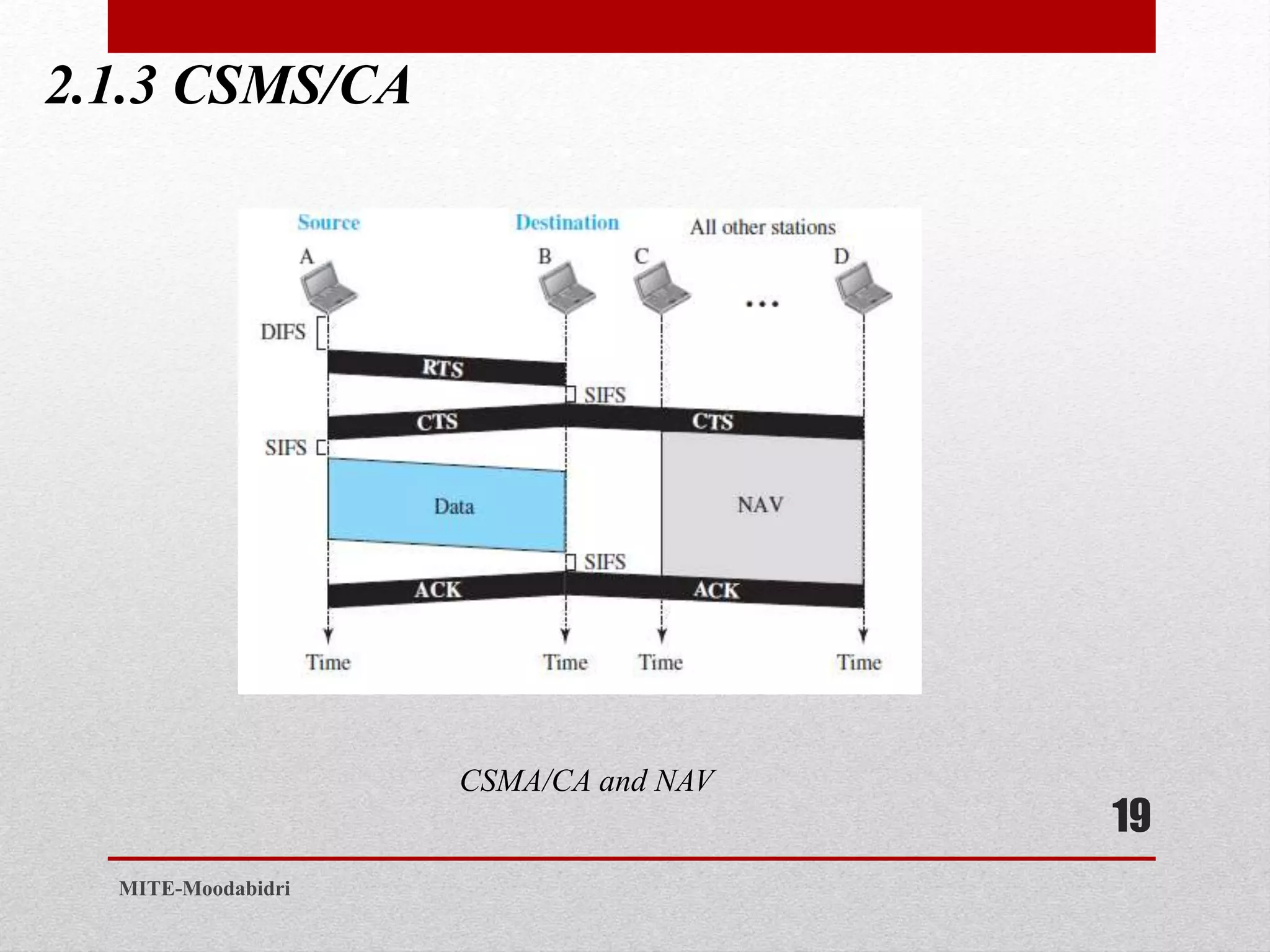
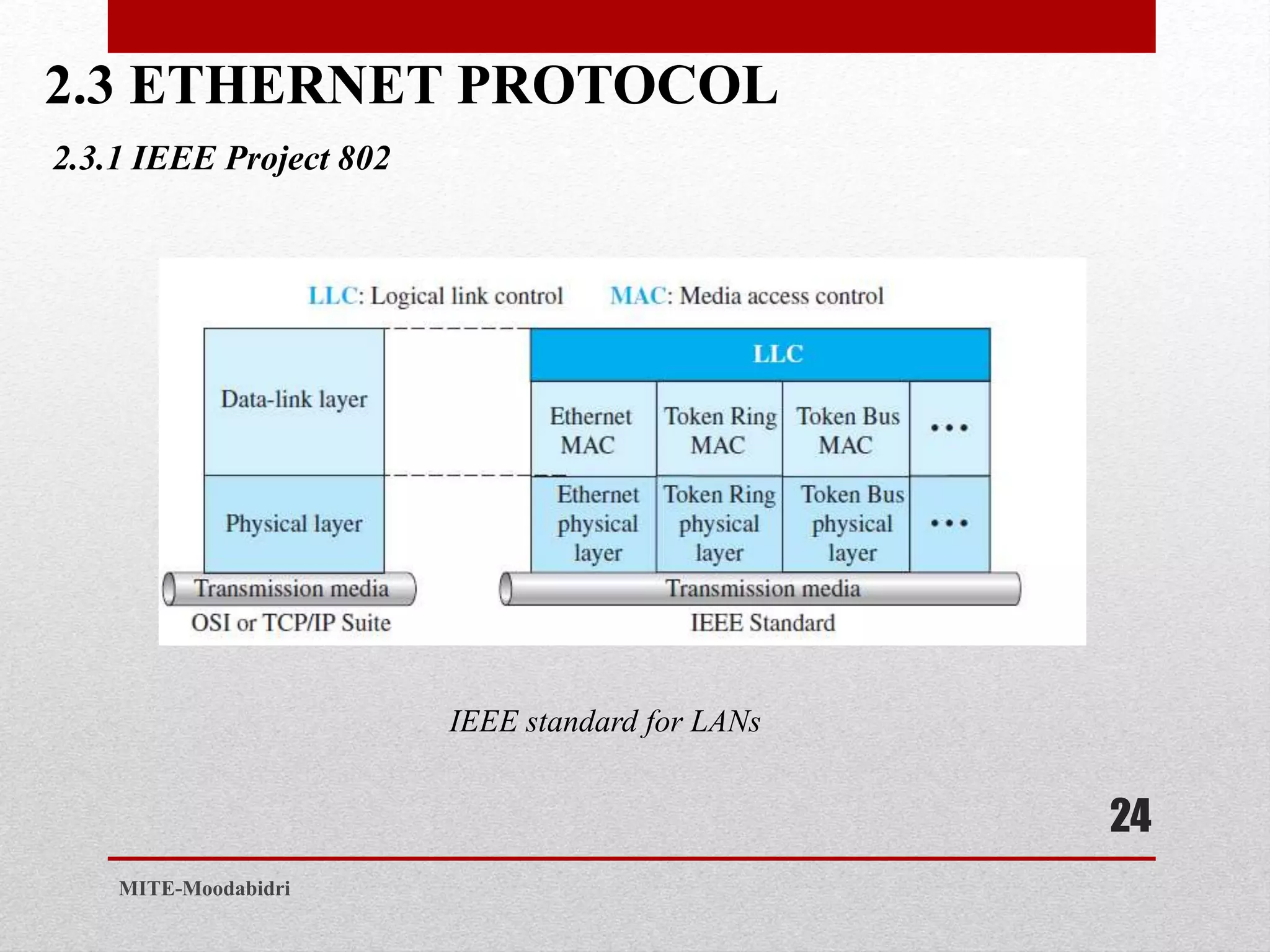
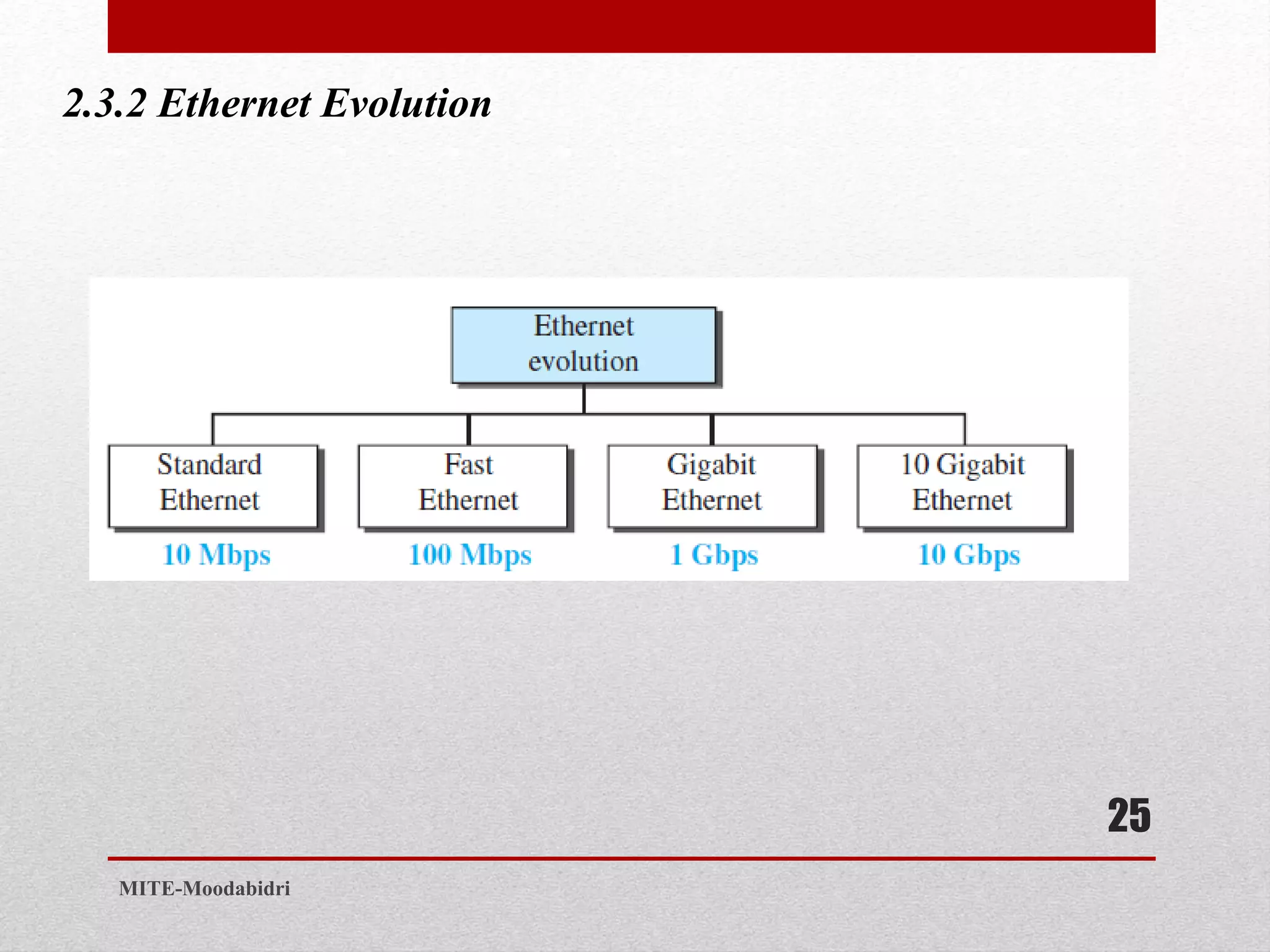
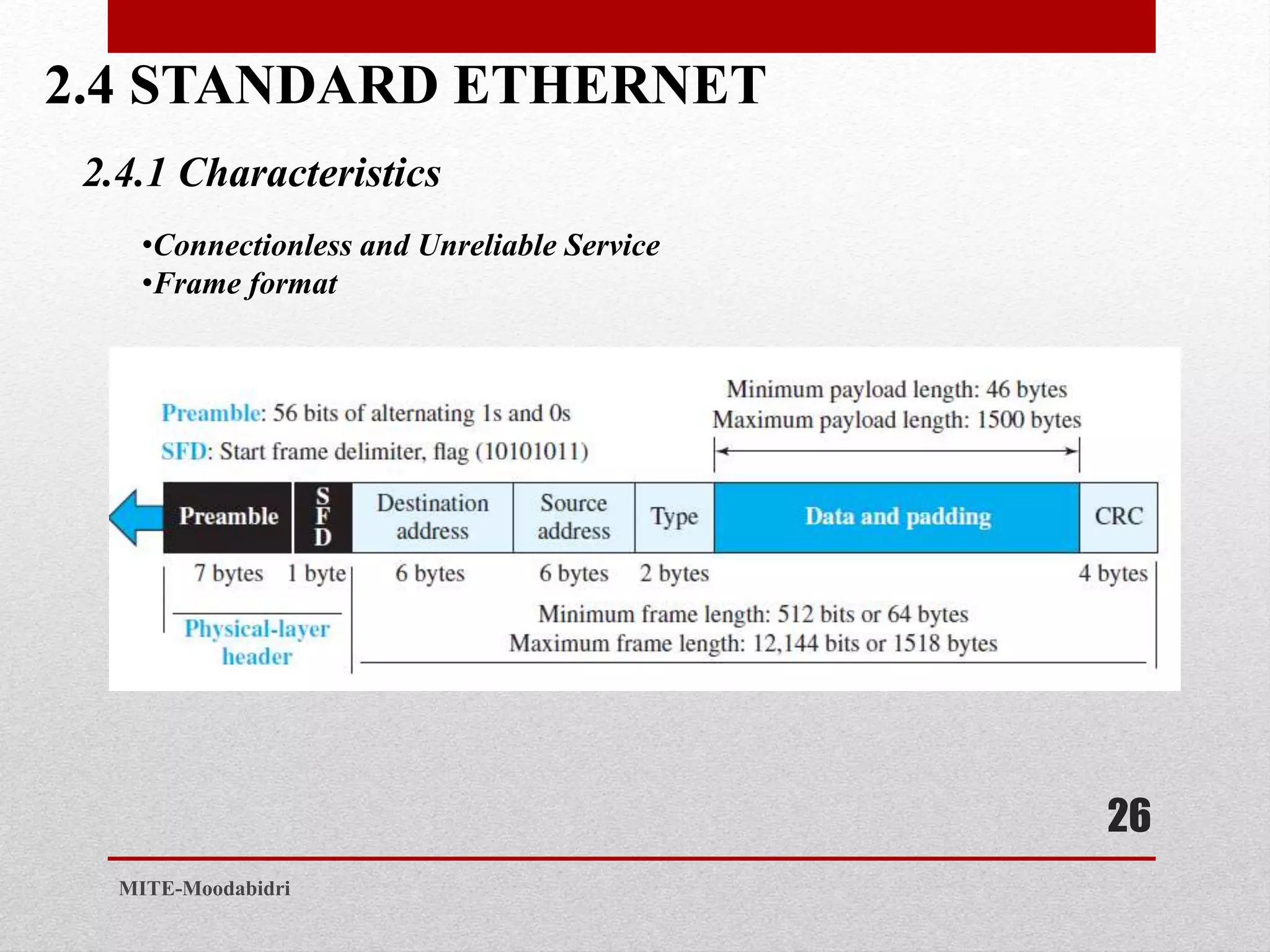
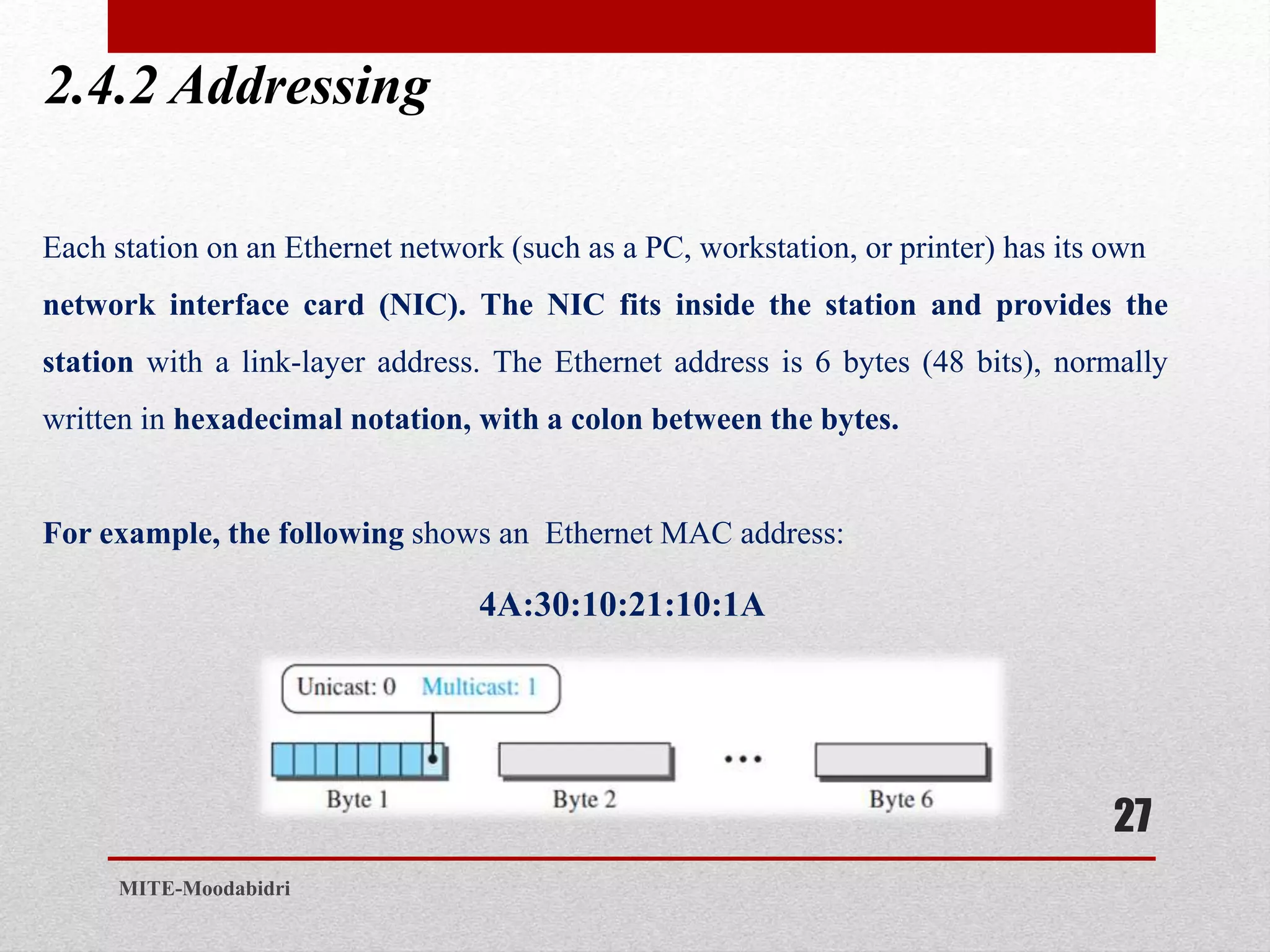
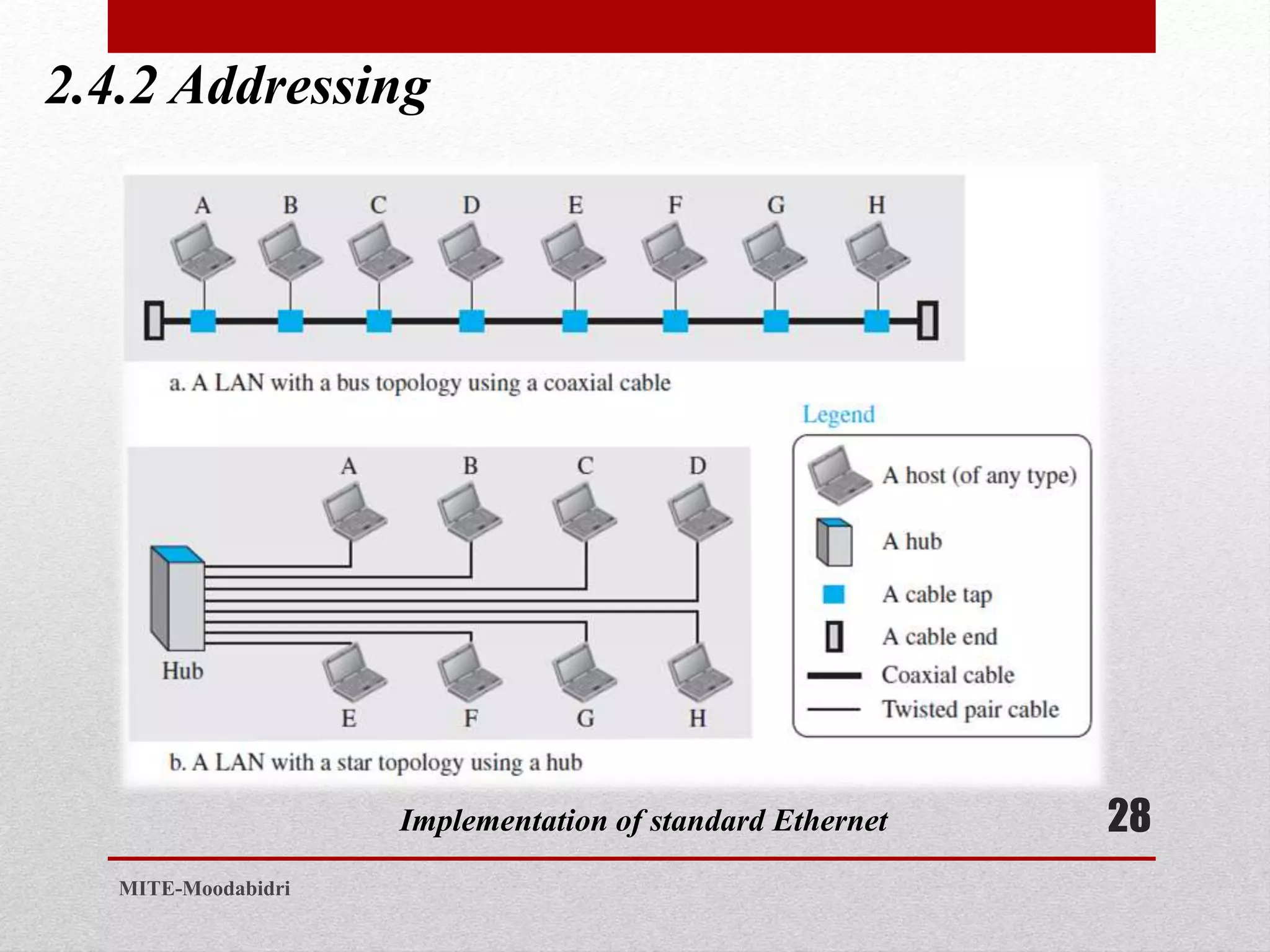
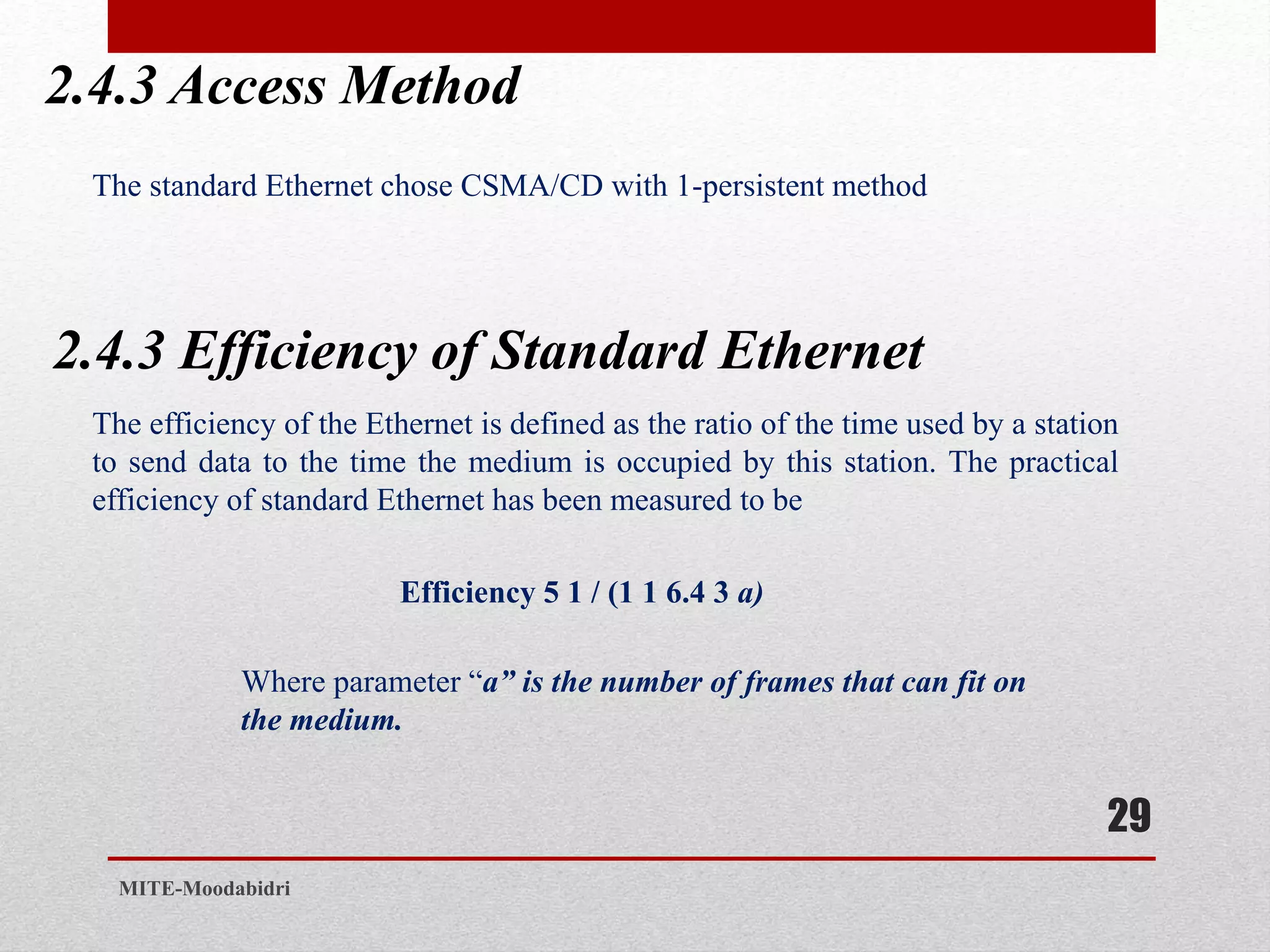
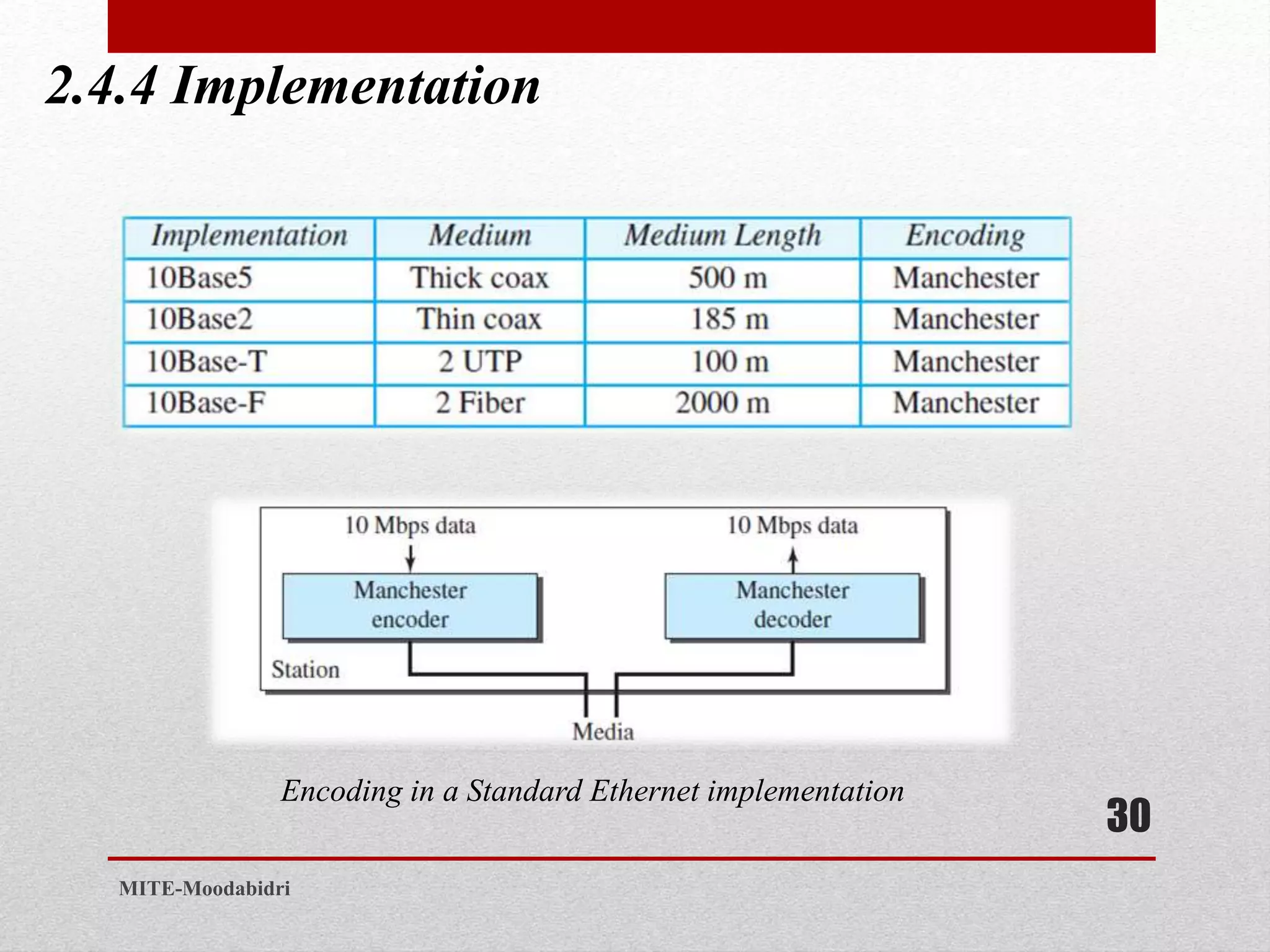
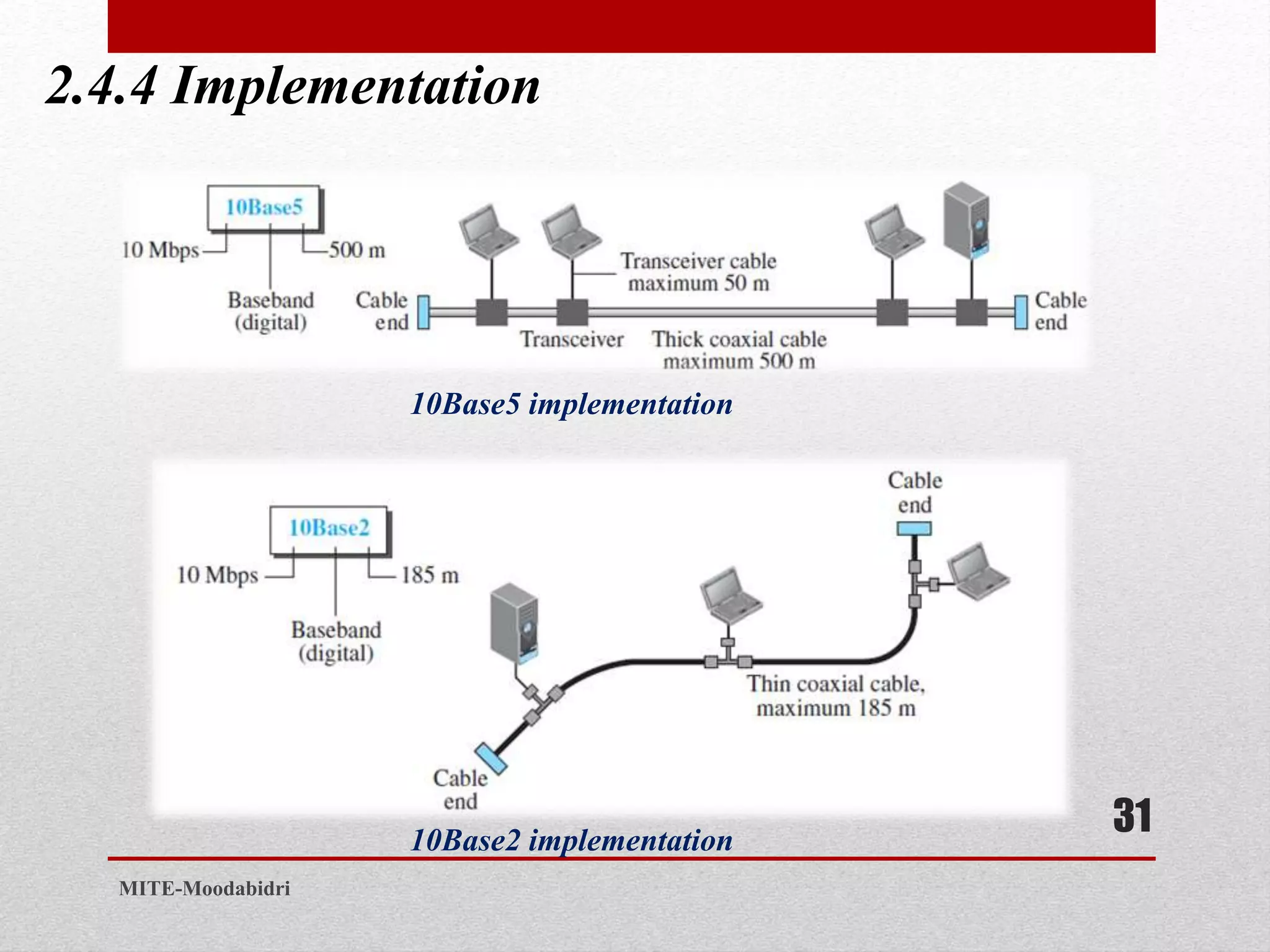
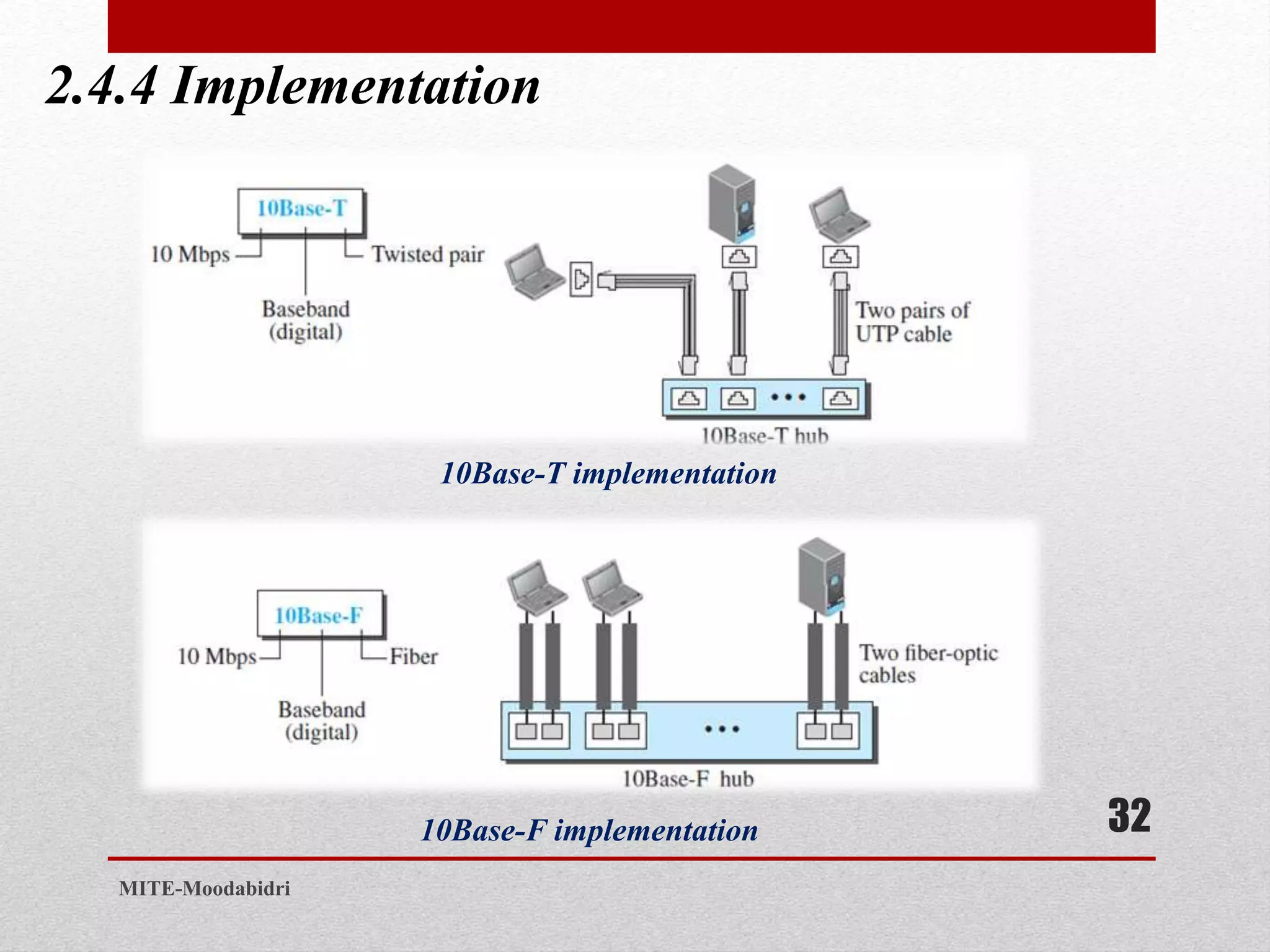
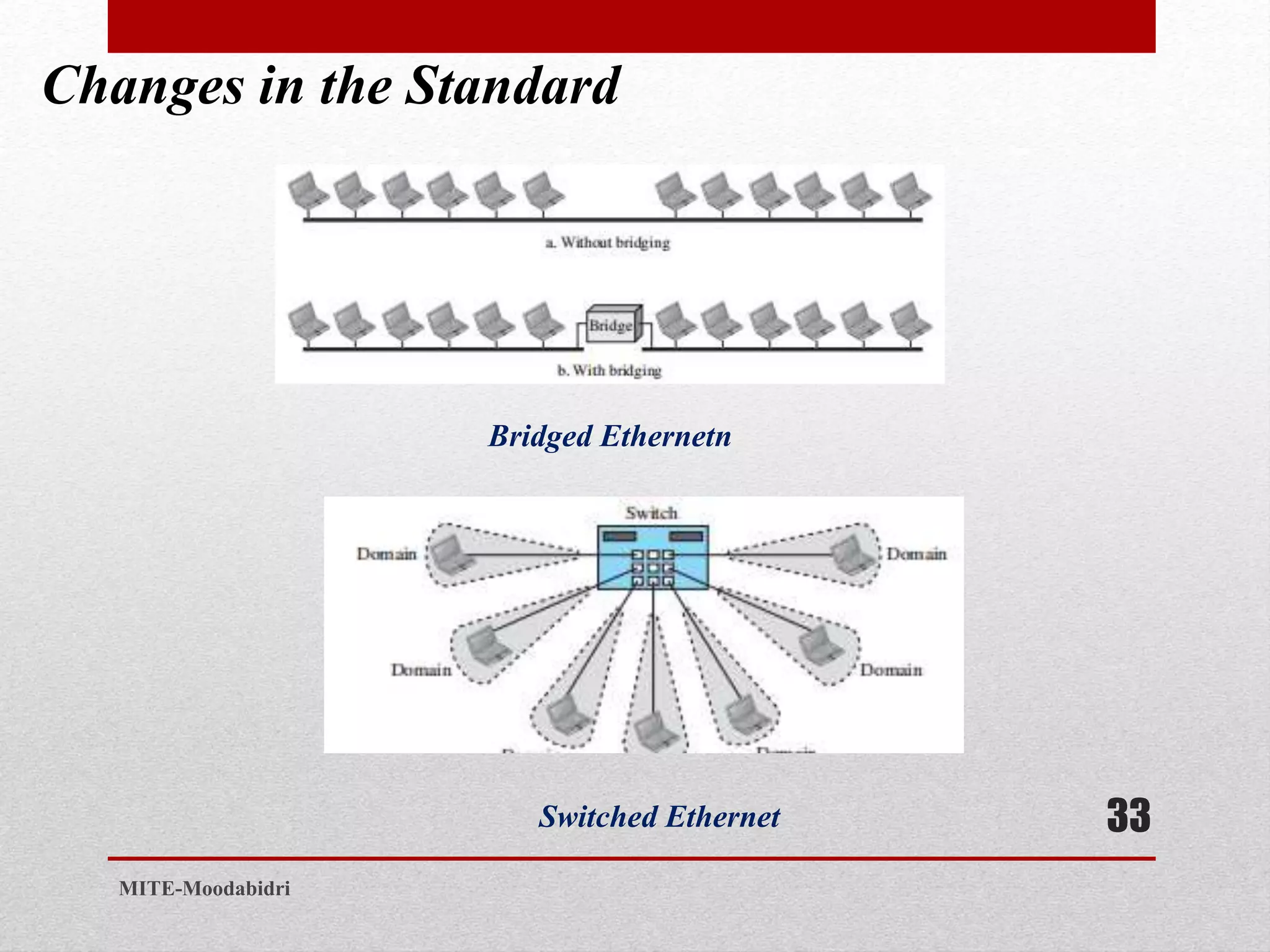
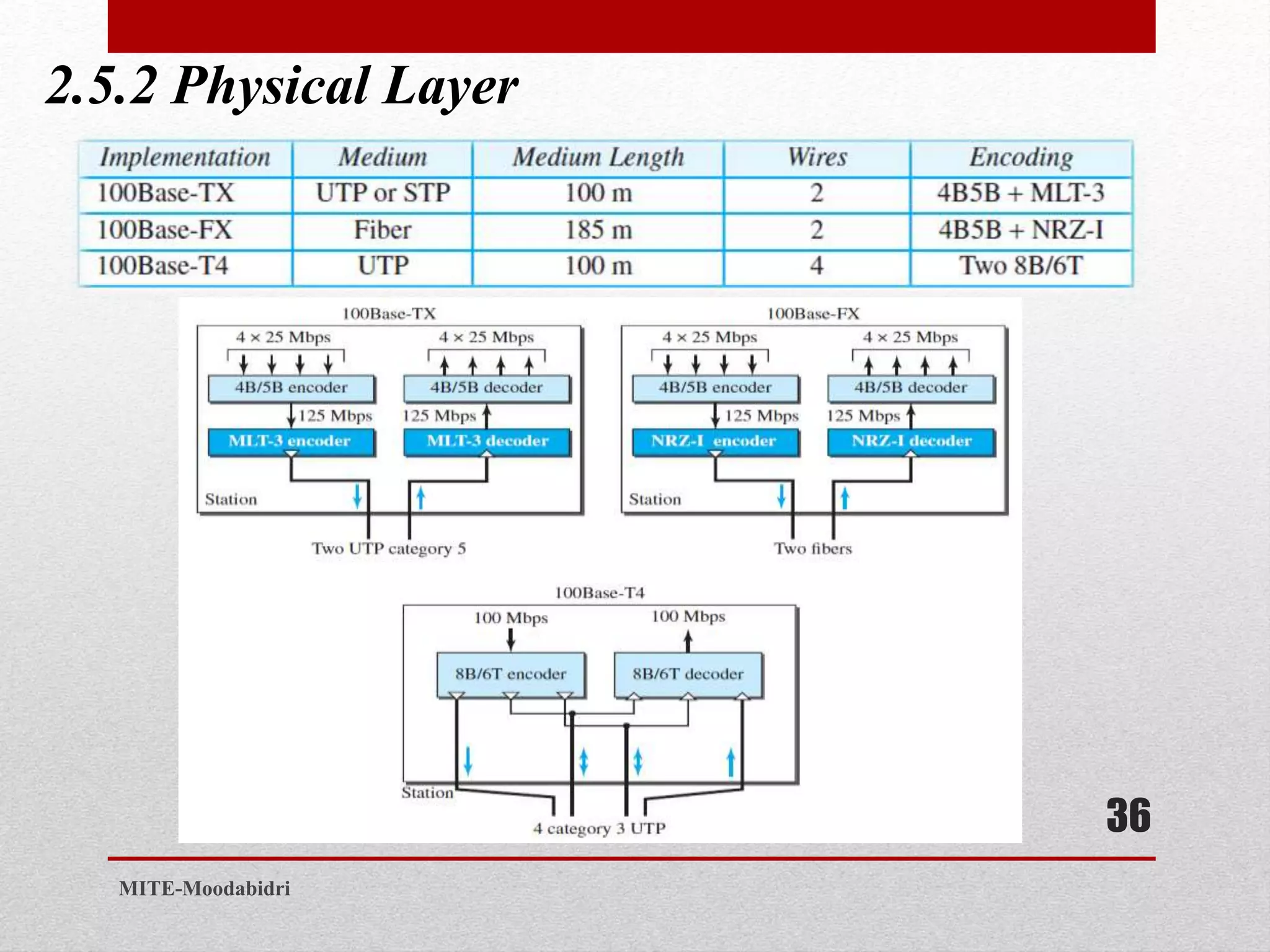
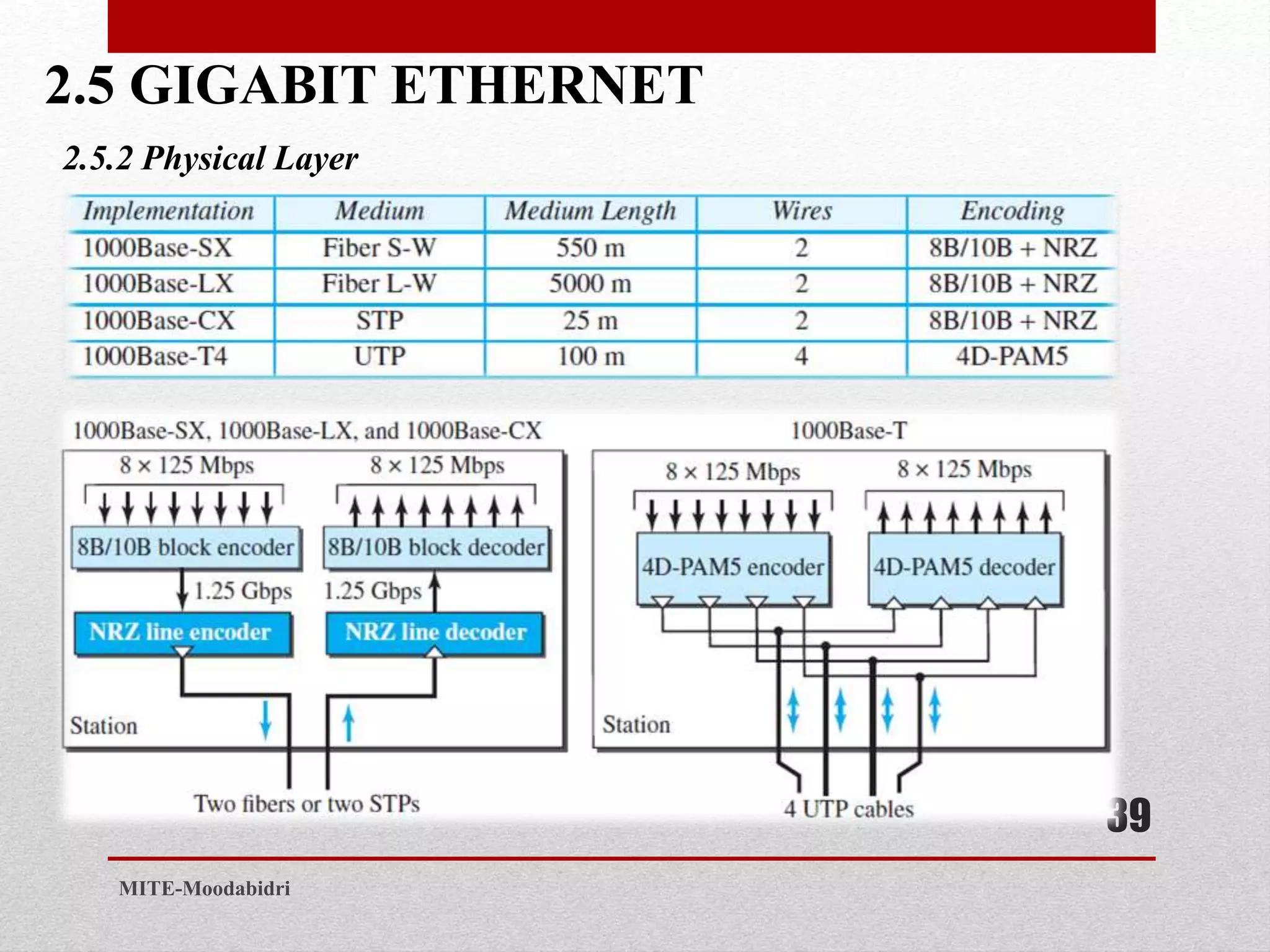
This document discusses media access control and the evolution of Ethernet. It covers random access methods like ALOHA, CSMA, CSMA/CD, and CSMA/CA. It also discusses controlled access methods like reservation, polling, and token passing. The document then covers the evolution of Ethernet including standard Ethernet, Fast Ethernet, Gigabit Ethernet, and 10 Gigabit Ethernet. It describes aspects like their addressing, access methods, frame formats, and physical layers.