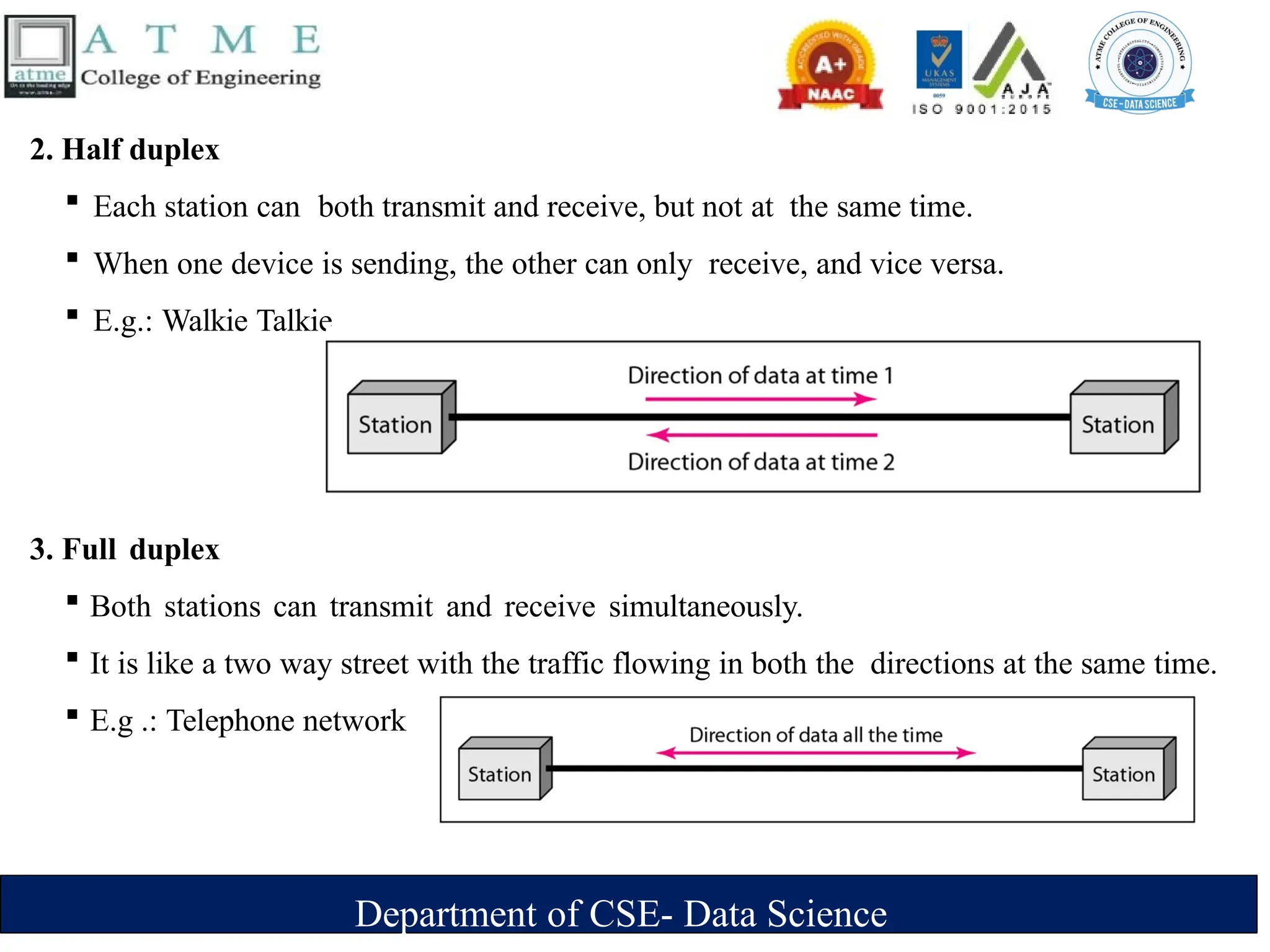
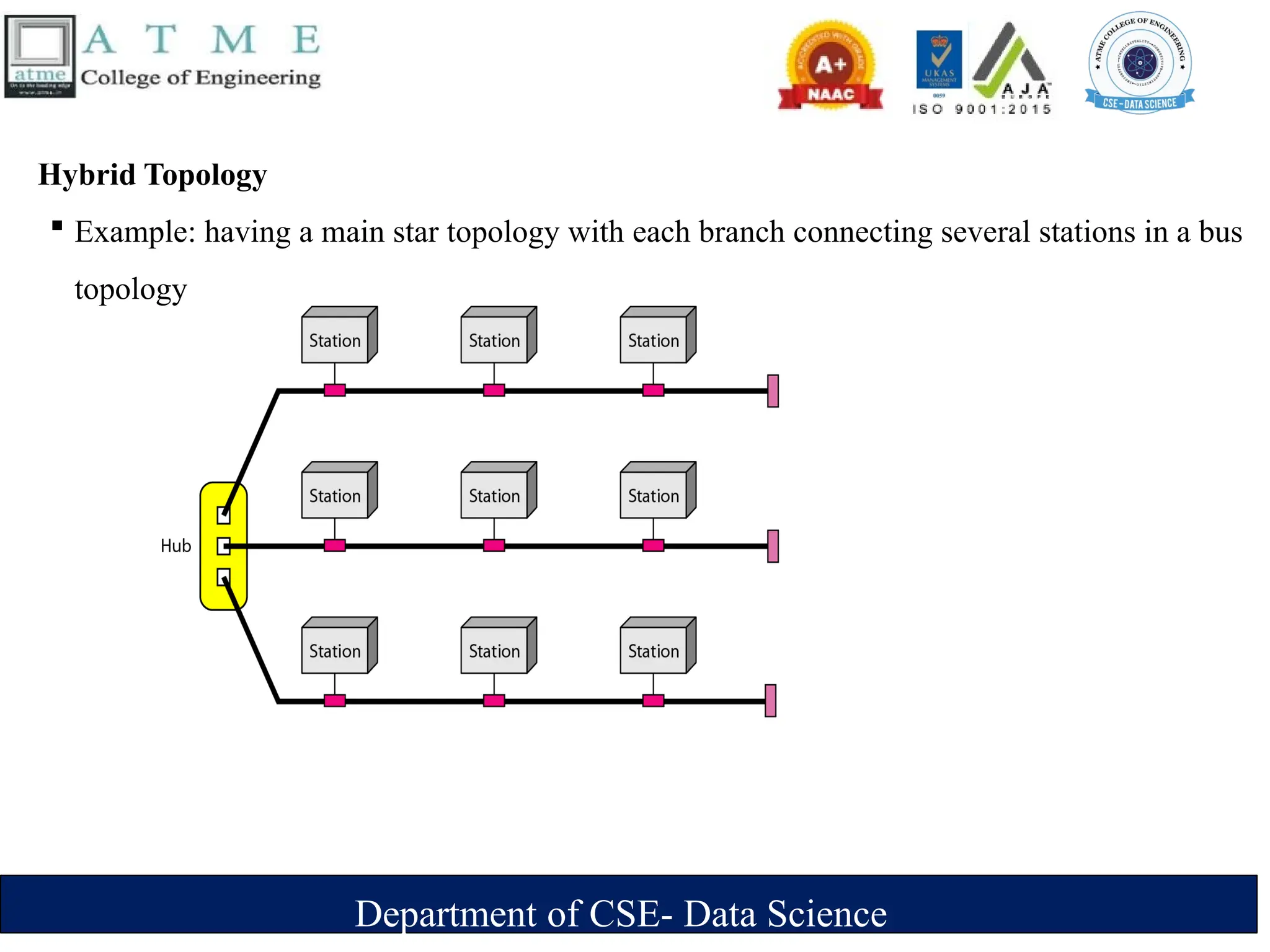
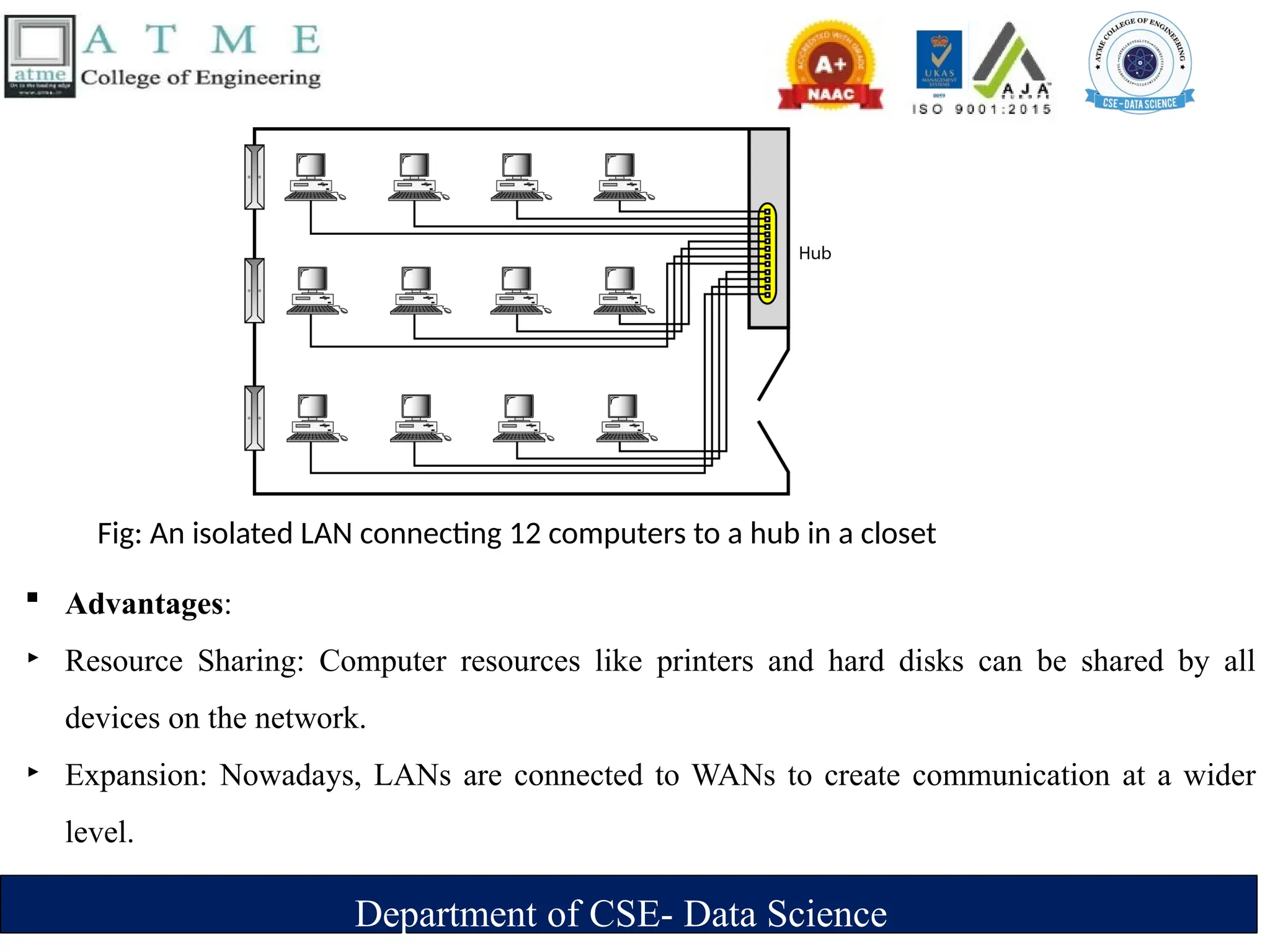
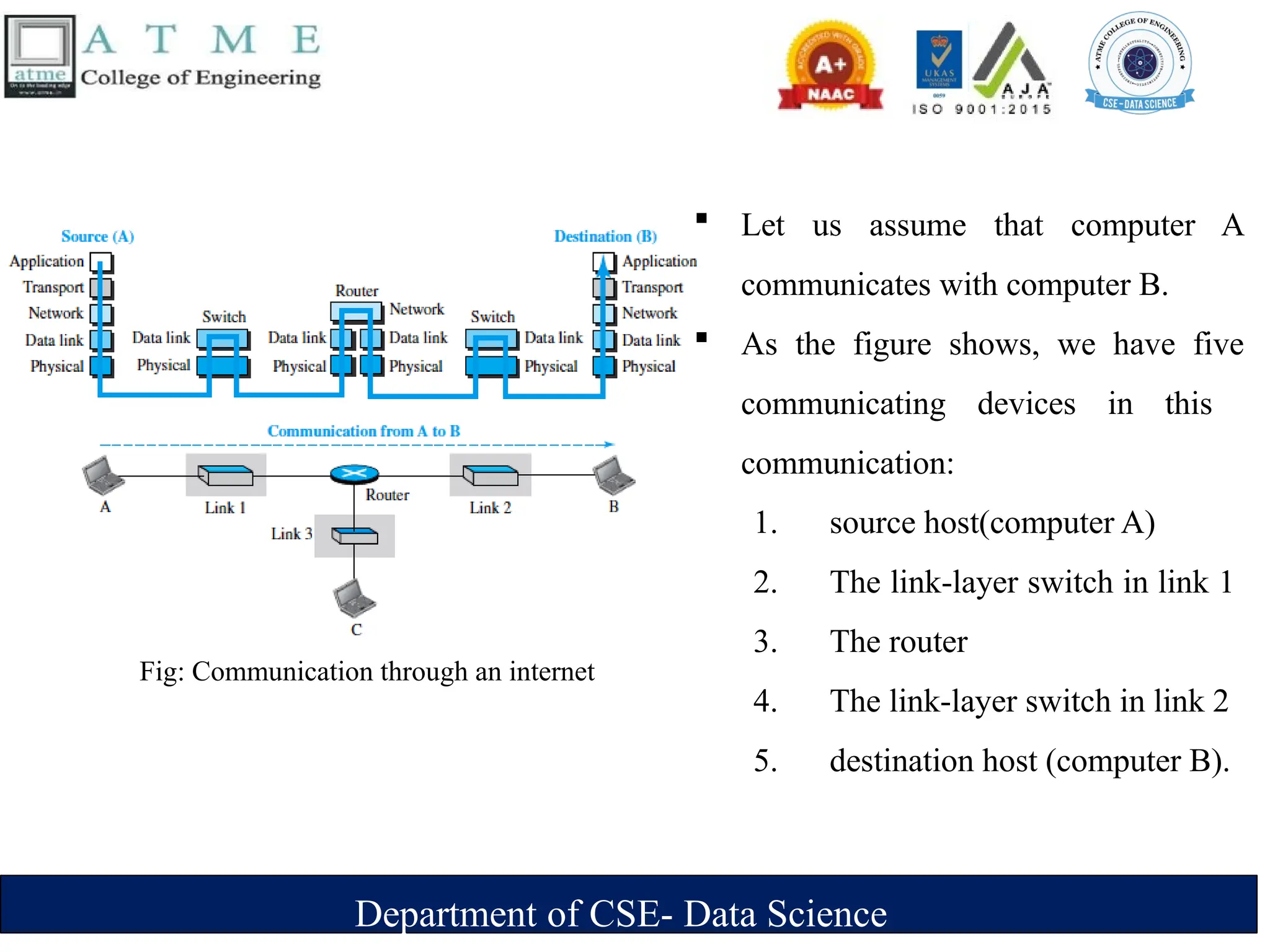
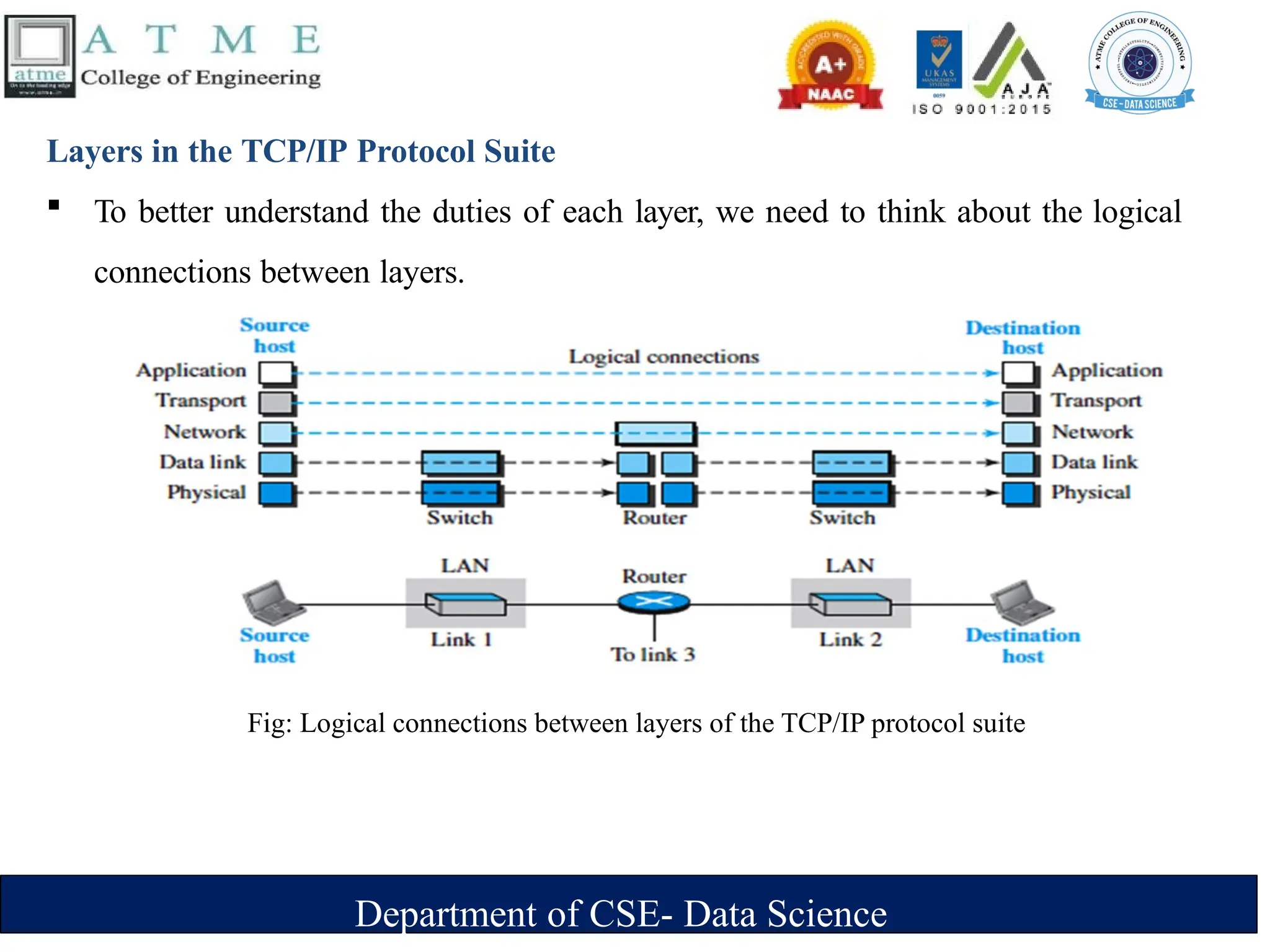
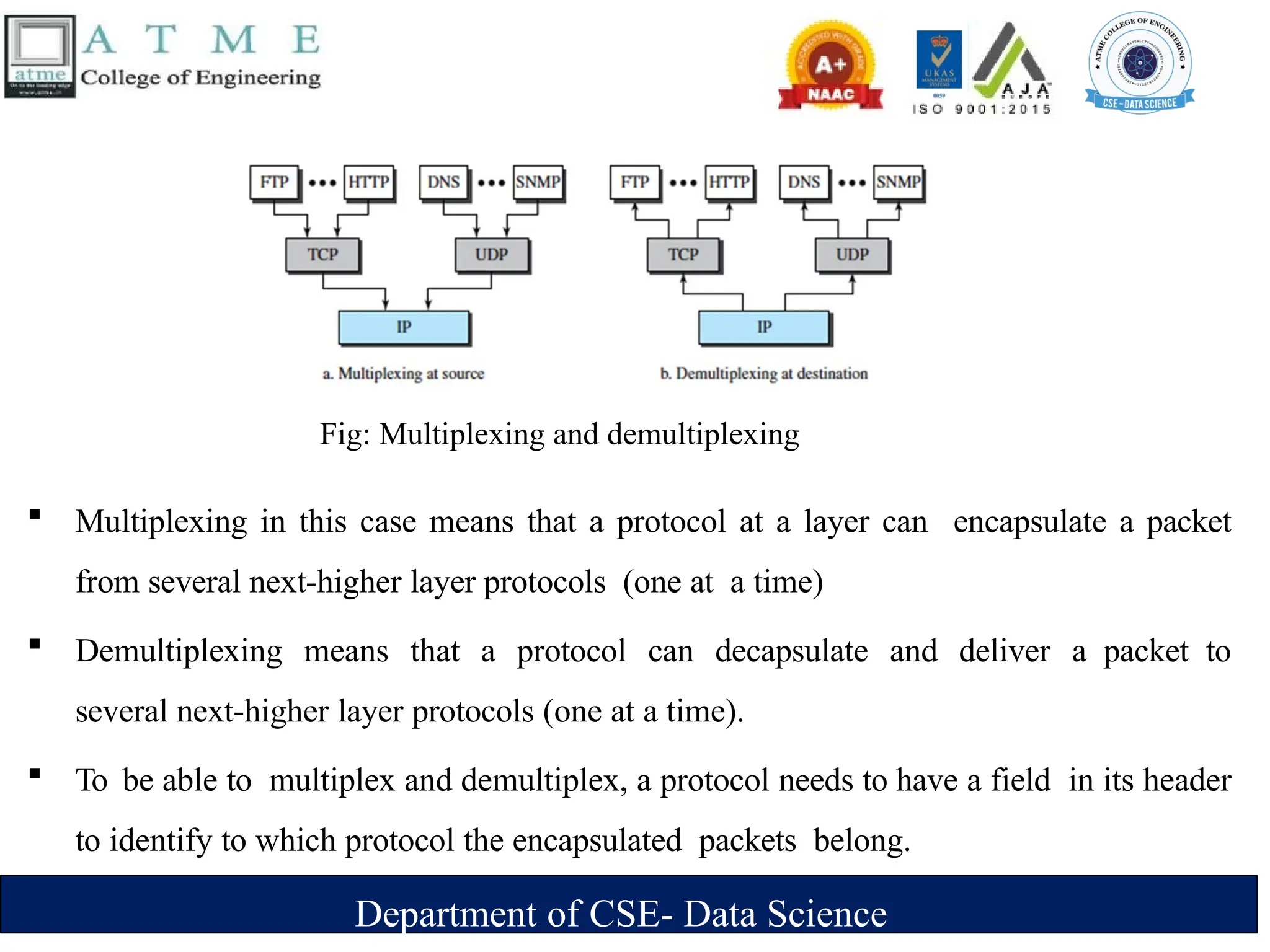
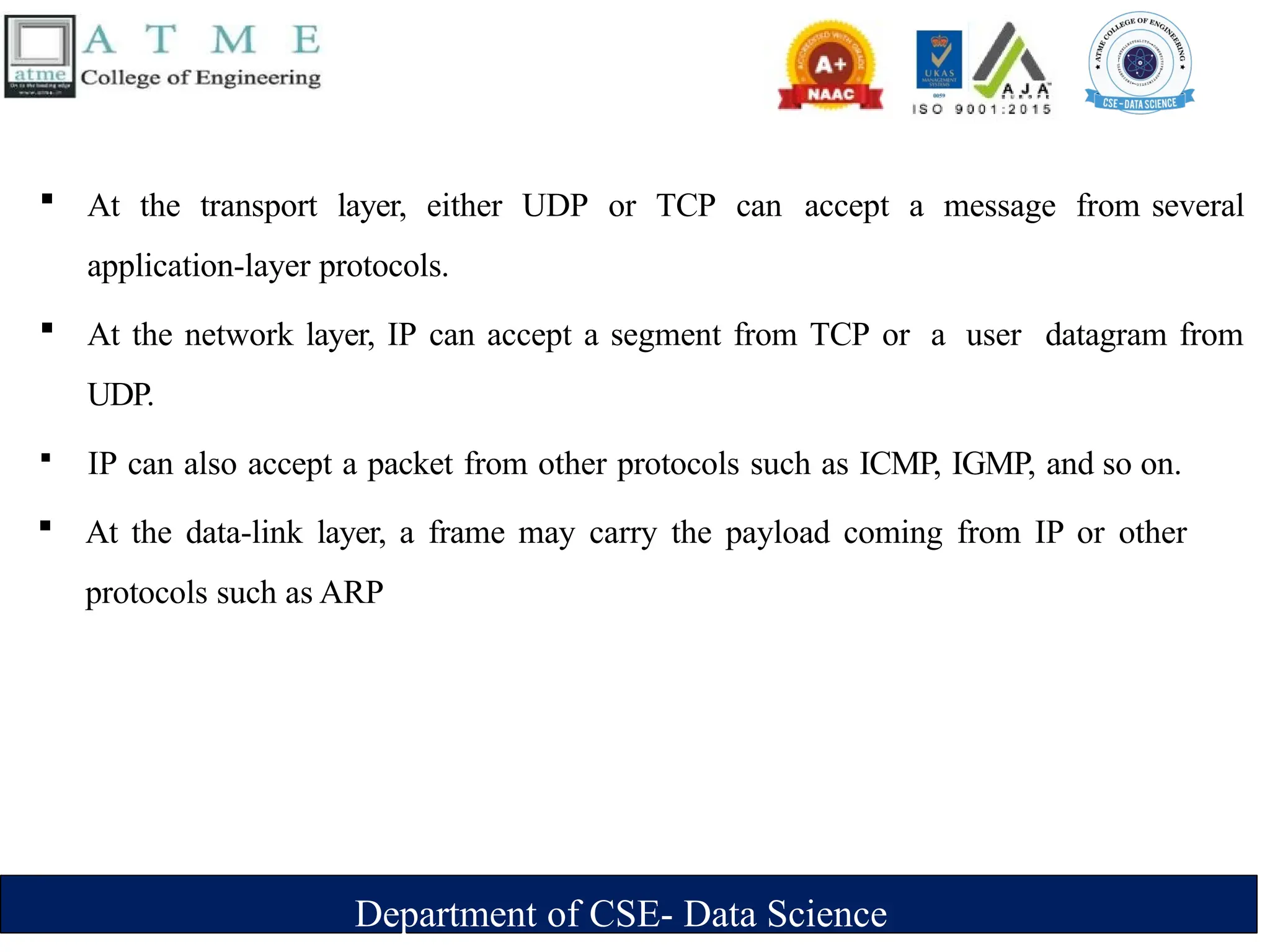
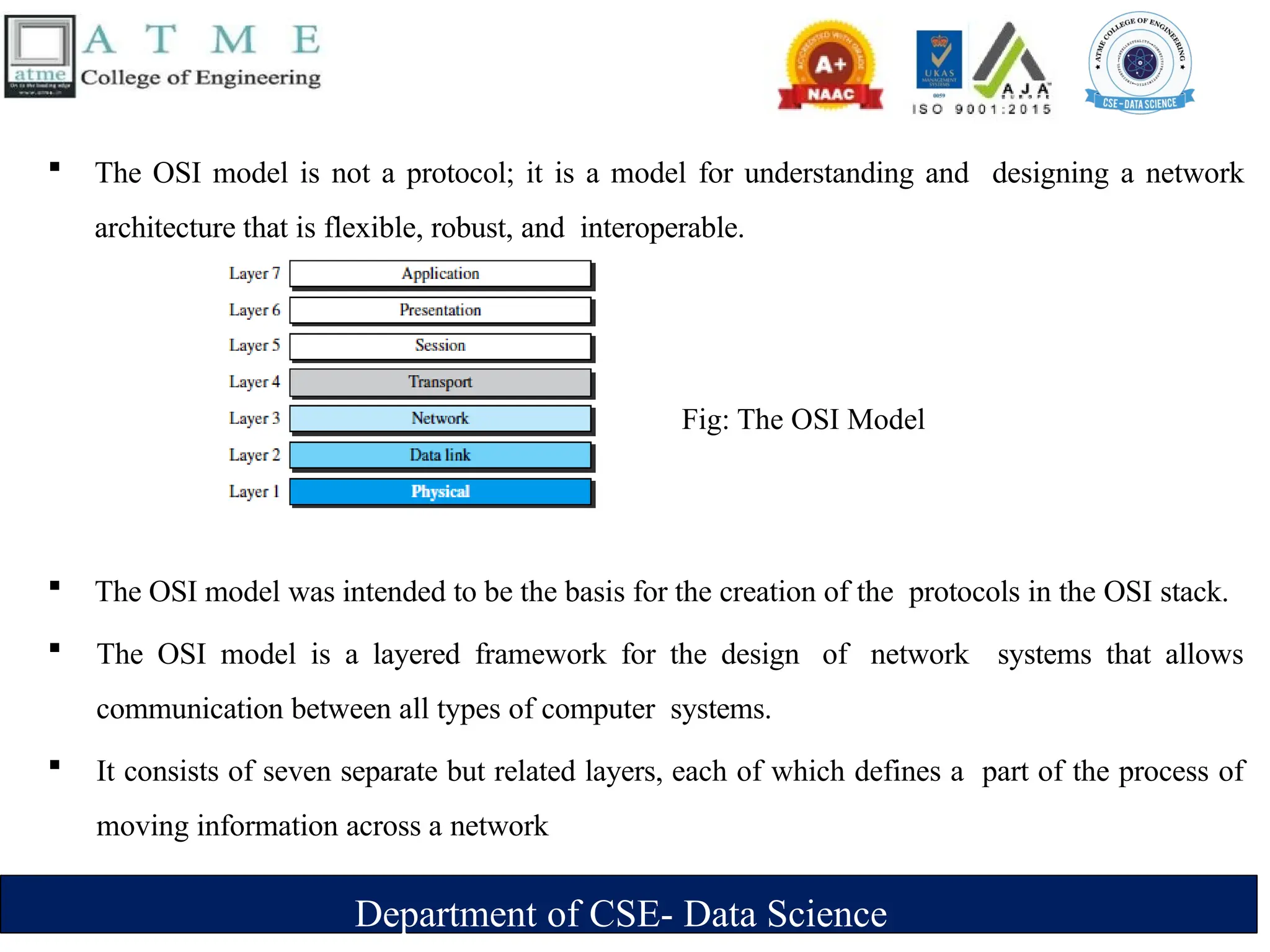
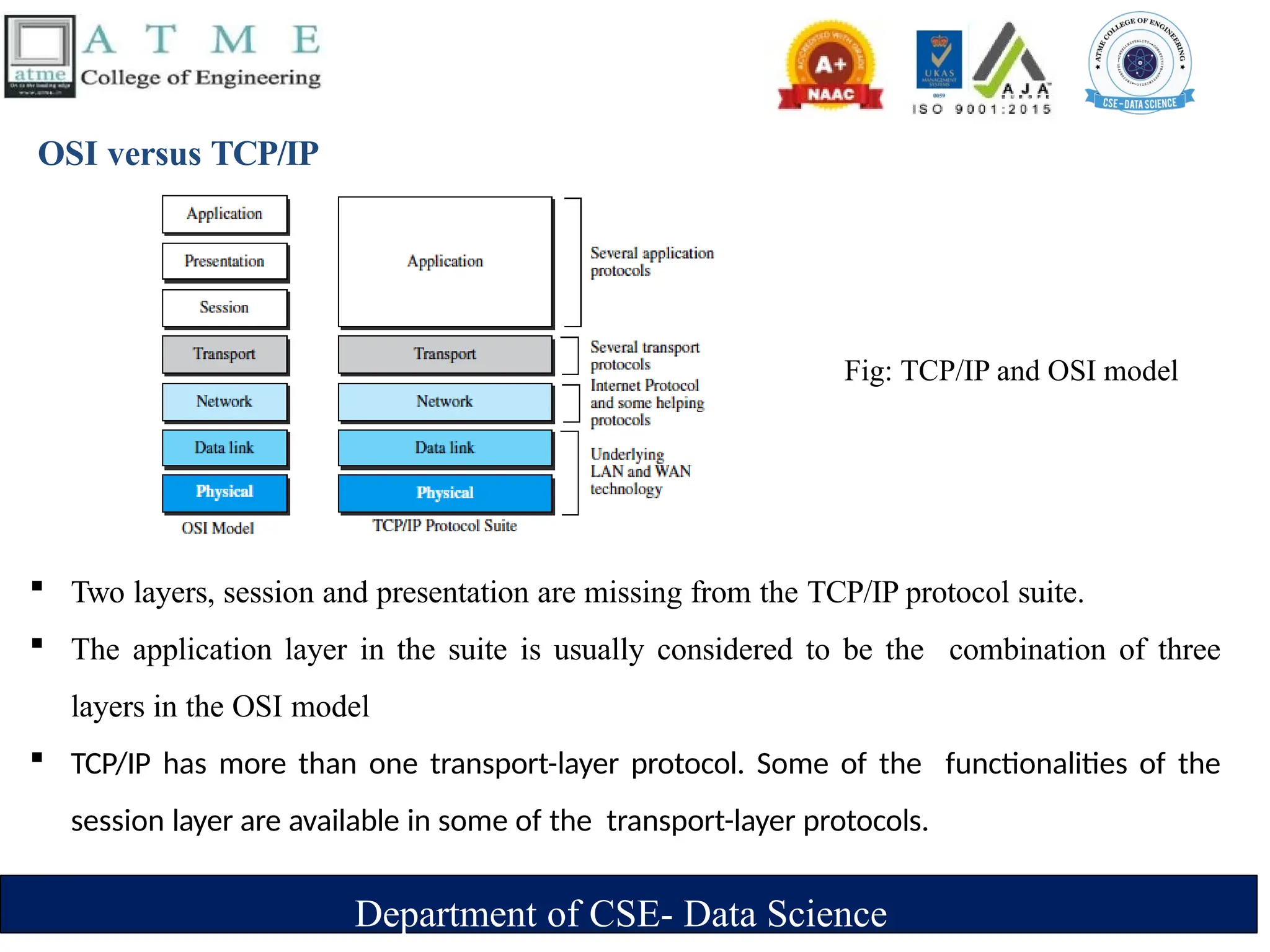
The document is an introduction to data communications covering key concepts of networking, data transmission, and various network topologies. It explains the characteristics of data communication systems, describes the different types of networks such as LANs, WANs, and MANs, and outlines their advantages and disadvantages. Furthermore, it discusses switching methods like circuit and packet switching, as well as components essential for effective data communication.

![Department of CSE- Data Science
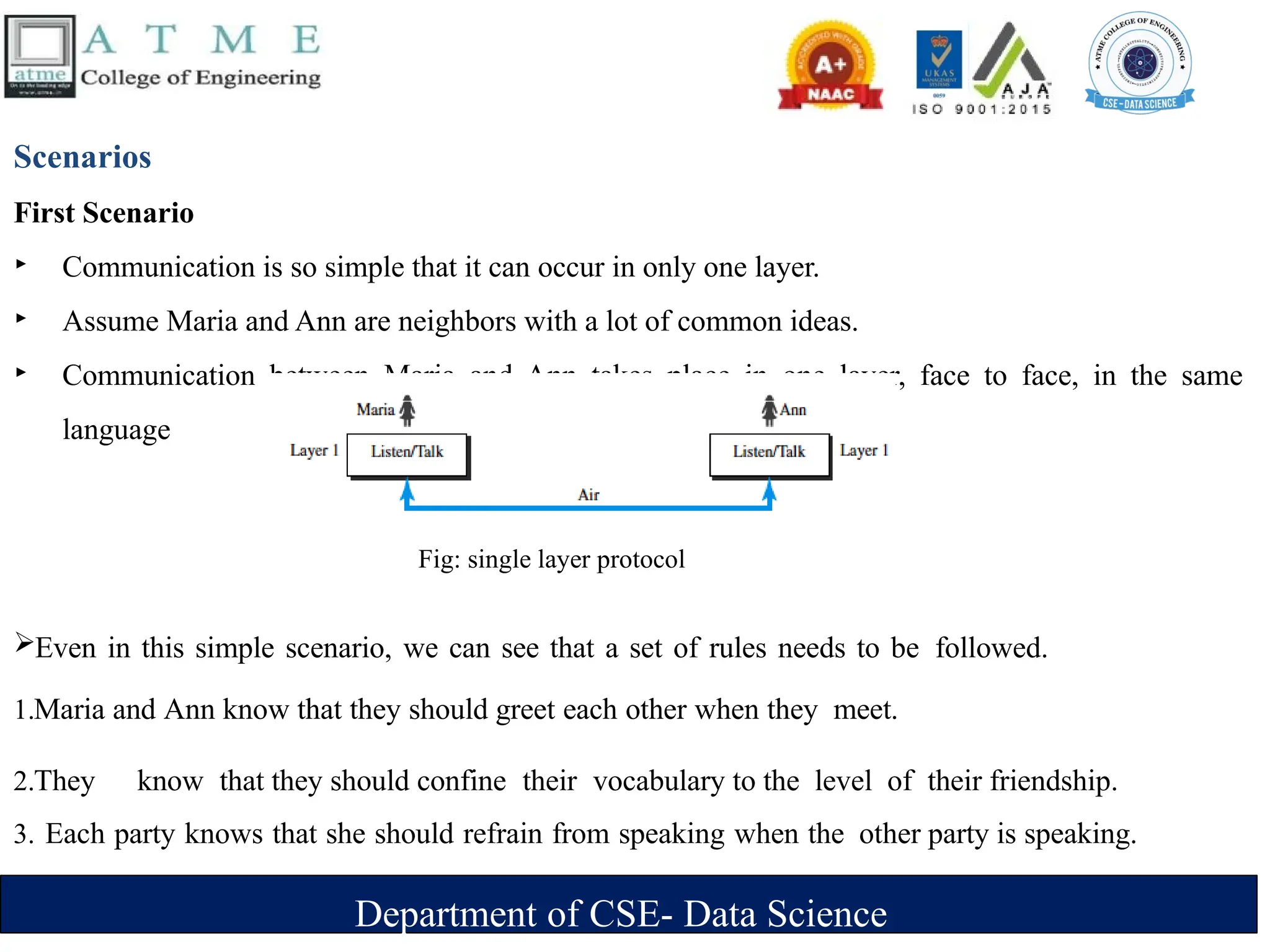
Video
‣ Recording or broadcasting of picture or a movie
‣ Produced as :
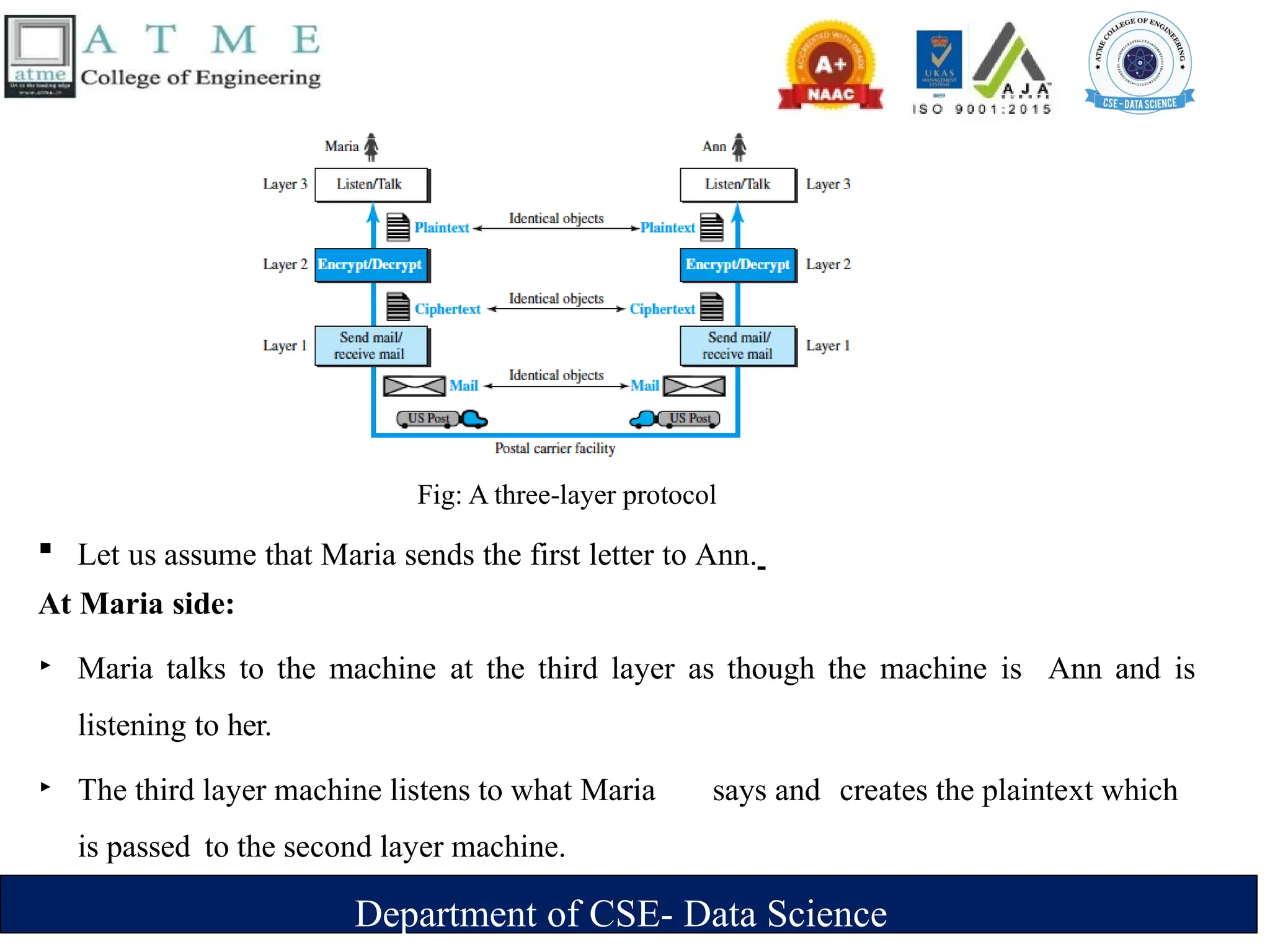
‣ Continuous entity [TV camera]
‣ Combination of images-discrete entity
Images
‣ Represented as bit pattern
‣ Image is divided into matrix of pixels(smallest element of an image)
‣ Each pixel is assigned a bit pattern (size and value of pattern depend on image)
‣ Ex: black and white dots (chessboard) -1 bit pattern is enough to represent a pixel, gray
scale- 2 bit pattern.
‣ Several methods to represent colour images : RGB,YCM](https://image.slidesharecdn.com/module-1introductiontodatacommunications-240915145039-7510d8b0/75/Module-1_Introduction-to-Data-Communications-pptx-7-2048.jpg)