Embed presentation
Downloaded 342 times
































































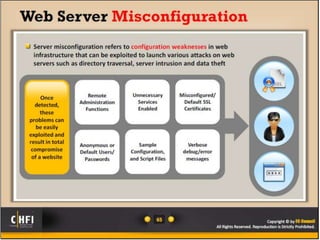



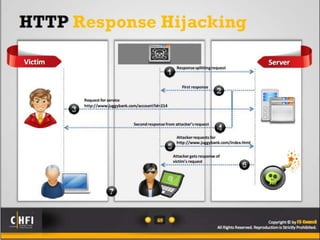


























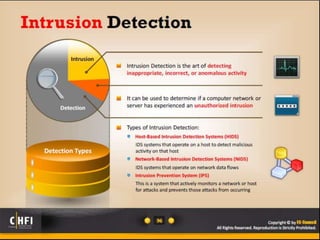




















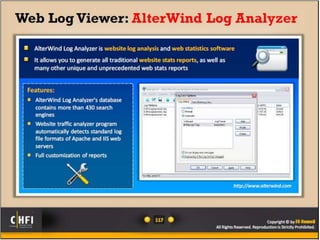










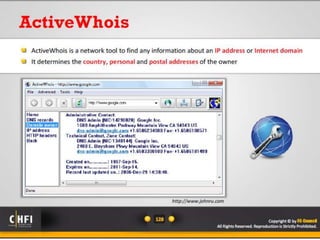





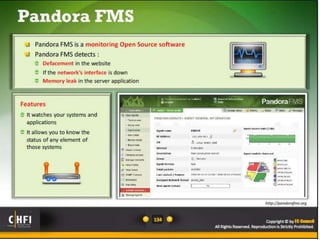



The document discusses the benefits of exercise for both physical and mental health. Regular exercise can improve cardiovascular health, reduce stress and anxiety, boost mood, and reduce the risk of diseases. It recommends that adults get at least 150 minutes of moderate exercise or 75 minutes of vigorous exercise per week to gain these benefits.








































































































































