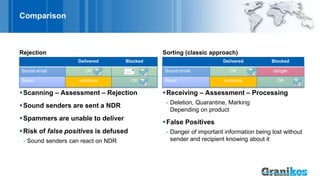
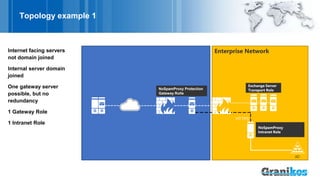
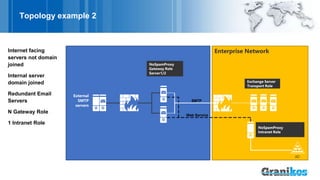
The document presents the nospamproxy® protection system as a modern anti-spam solution that focuses on email rejection rather than sorting, minimizing the impact of spam on productivity and storage. It highlights the high percentage of spam in email traffic, the negative effects of spam on business processes, and the customizable, self-learning features of the nospamproxy system which ensure legal compliance. Additionally, it offers integrated options for email encryption and large file exchanges, making it a scalable and resource-efficient solution for organizations.