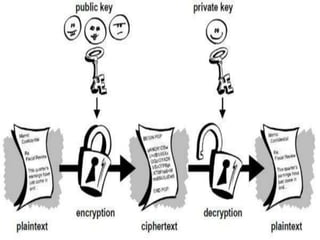
Allnet Solutions asked for help implementing email encryption options across its offices in New Zealand. The options should work with Lotus Notes, Pegasus, Outlook, and GroupWise. PGP and S/MIME are common encryption methods that use public/private key pairs to encrypt messages. While encryption provides security benefits, it also faces challenges around key management, costs, compatibility, and unrealistic requirements. Strategic planning is needed to ensure encryption is manageable for IT and users. Professional secure email services can help overcome simplicity and compatibility issues.