Embed presentation
Downloaded 38 times

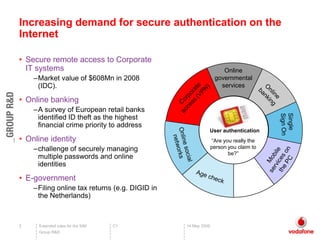









The document discusses using the SIM card for secure authentication on the internet. It notes growing demand for authentication of online banking, corporate systems, and government services. The SIM card provides a secure, standardized platform that over 4 billion users always carry. It could enable mobile operators to become internet security providers by leveraging the SIM card for authentication through technologies like one-time passwords and wireless PKI. A demonstration showed how the SIM could support authentication through OpenID for social networks, banking, and other online services.









