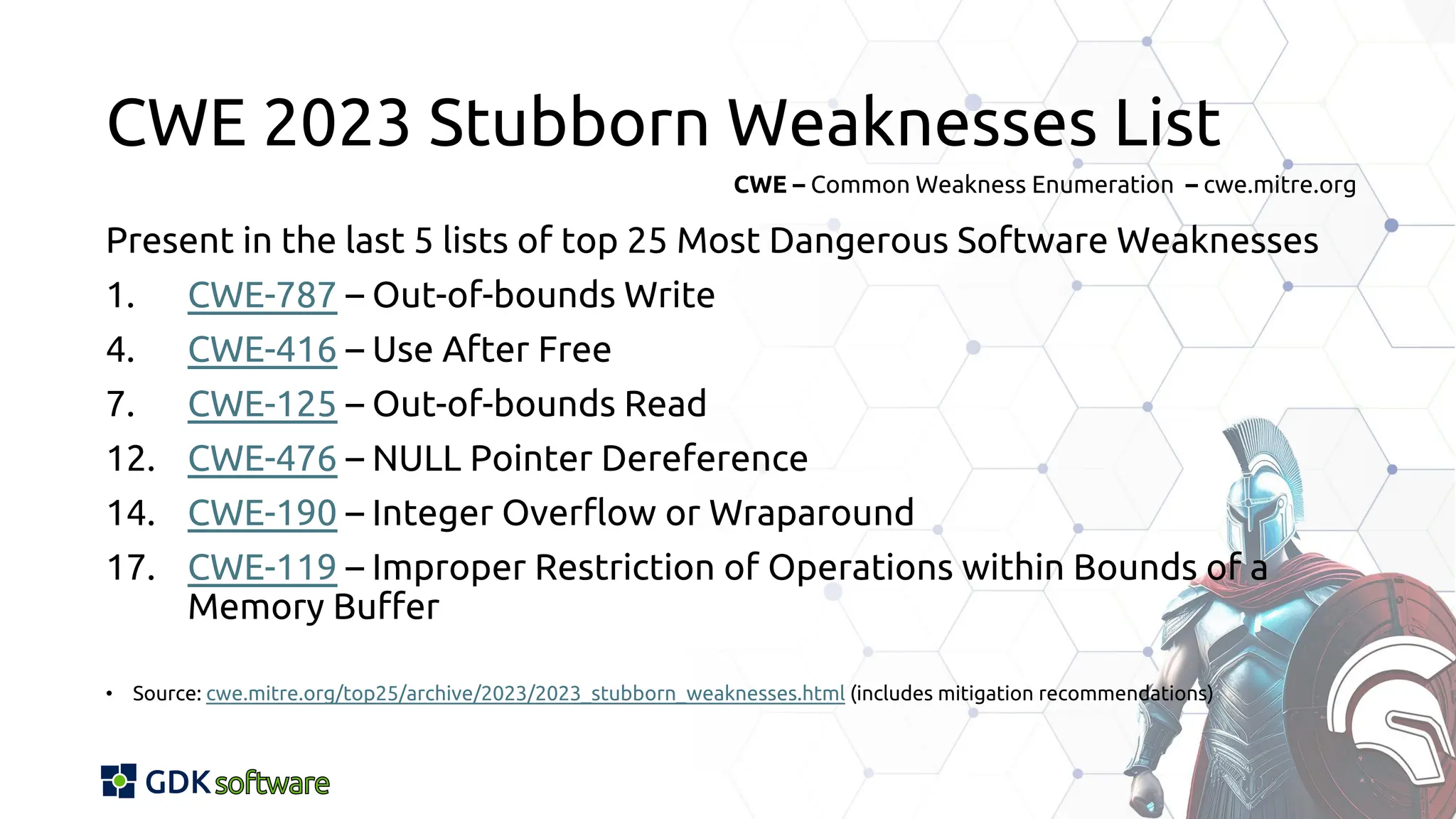
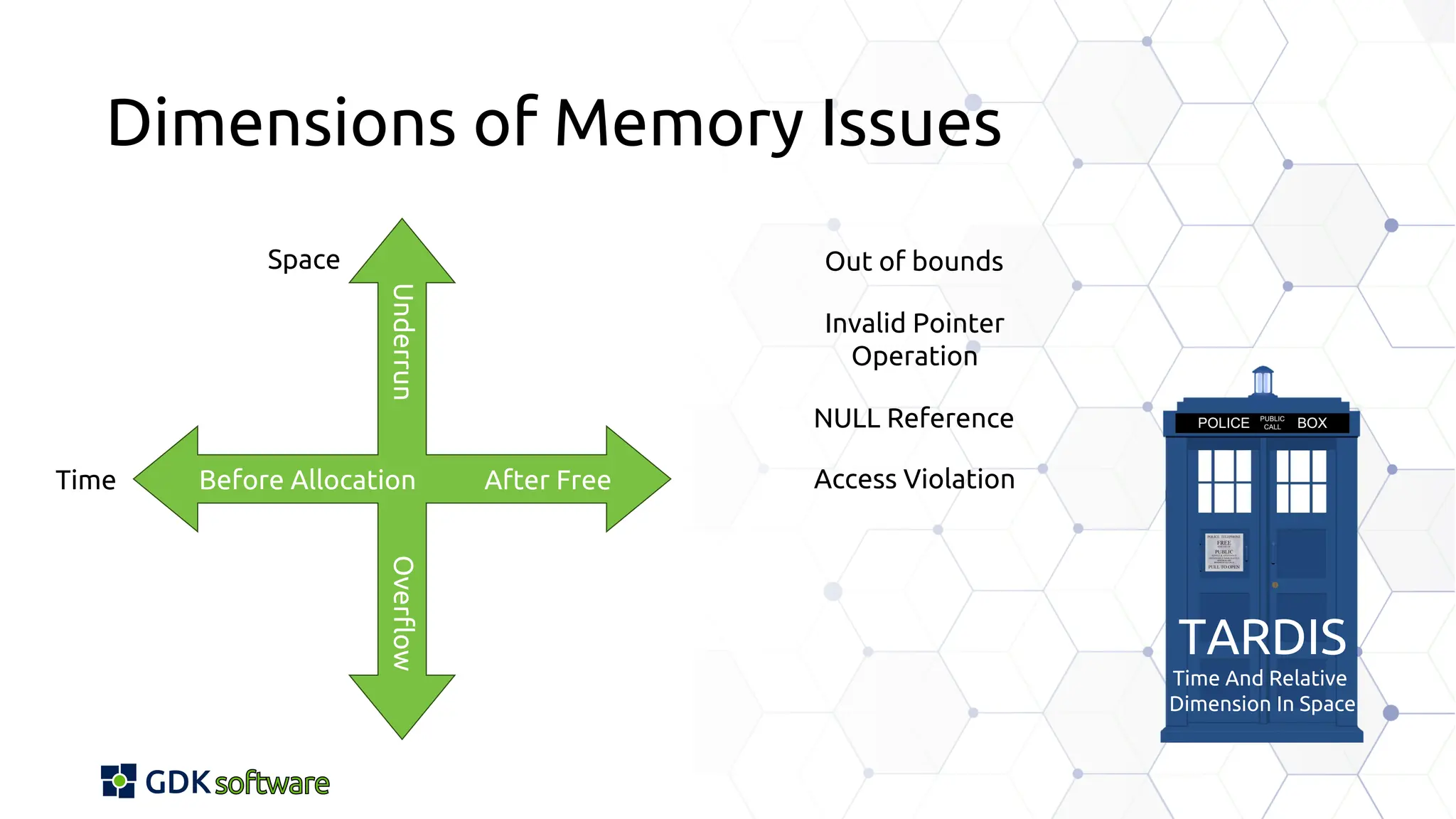
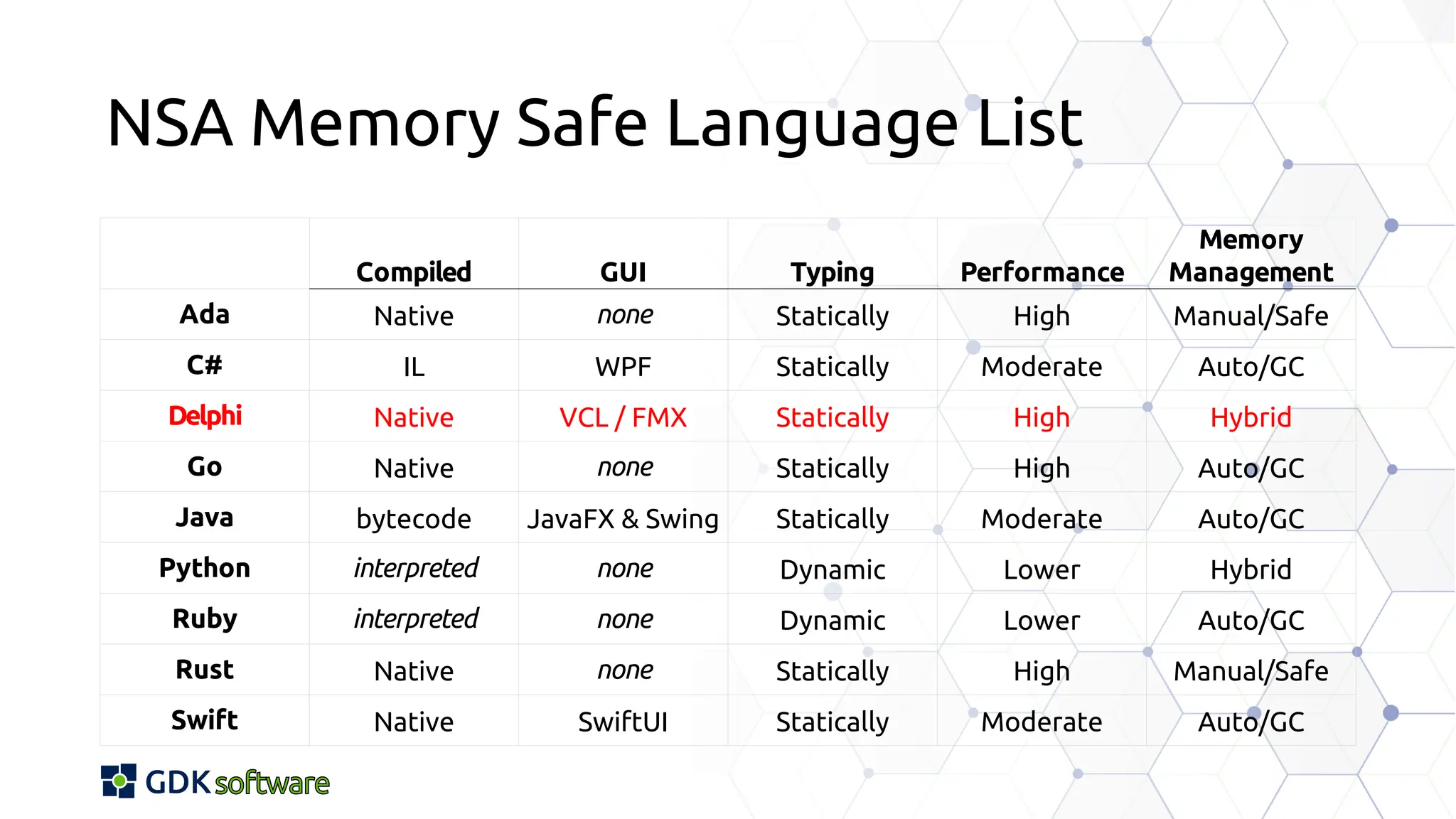
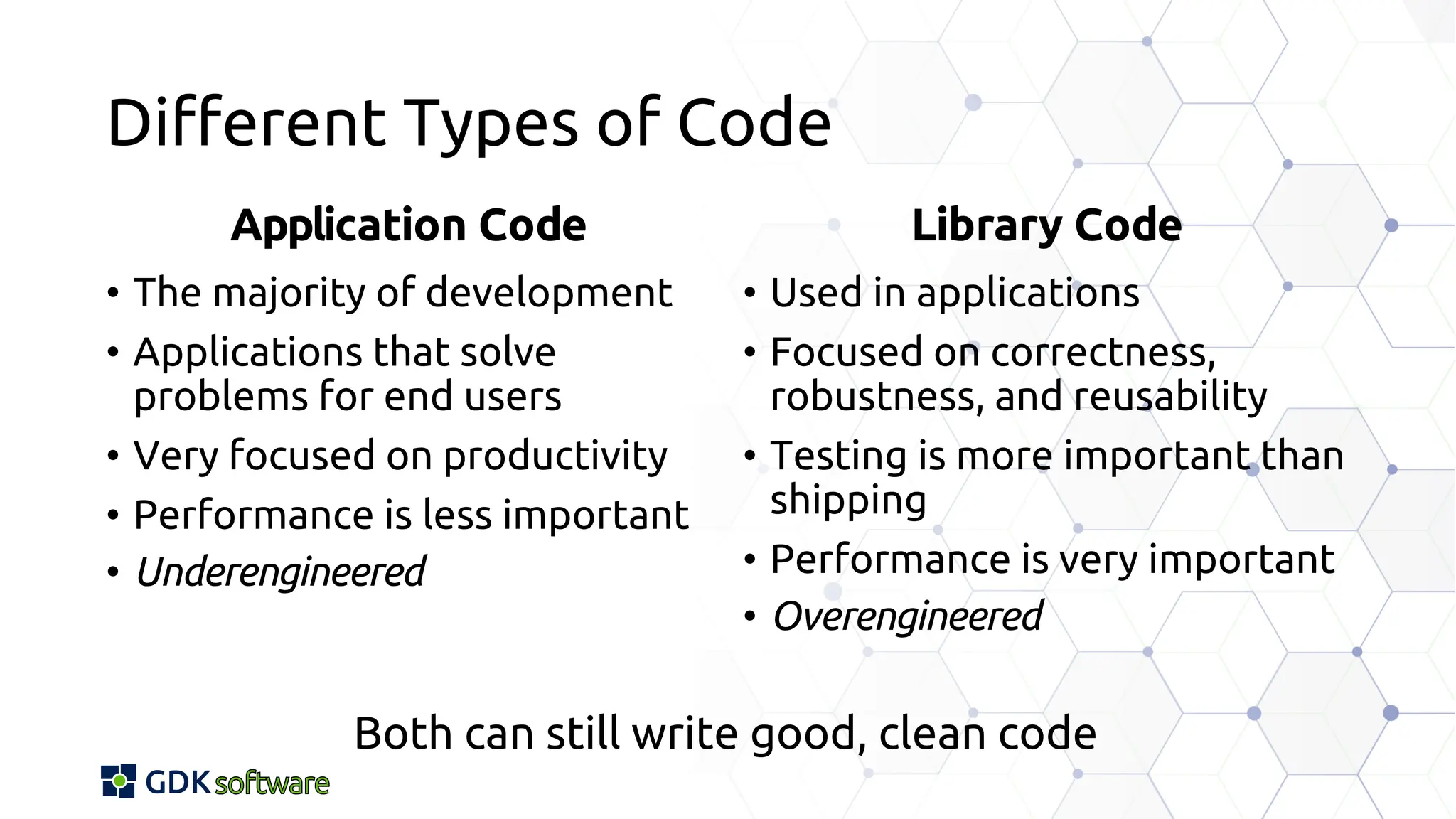
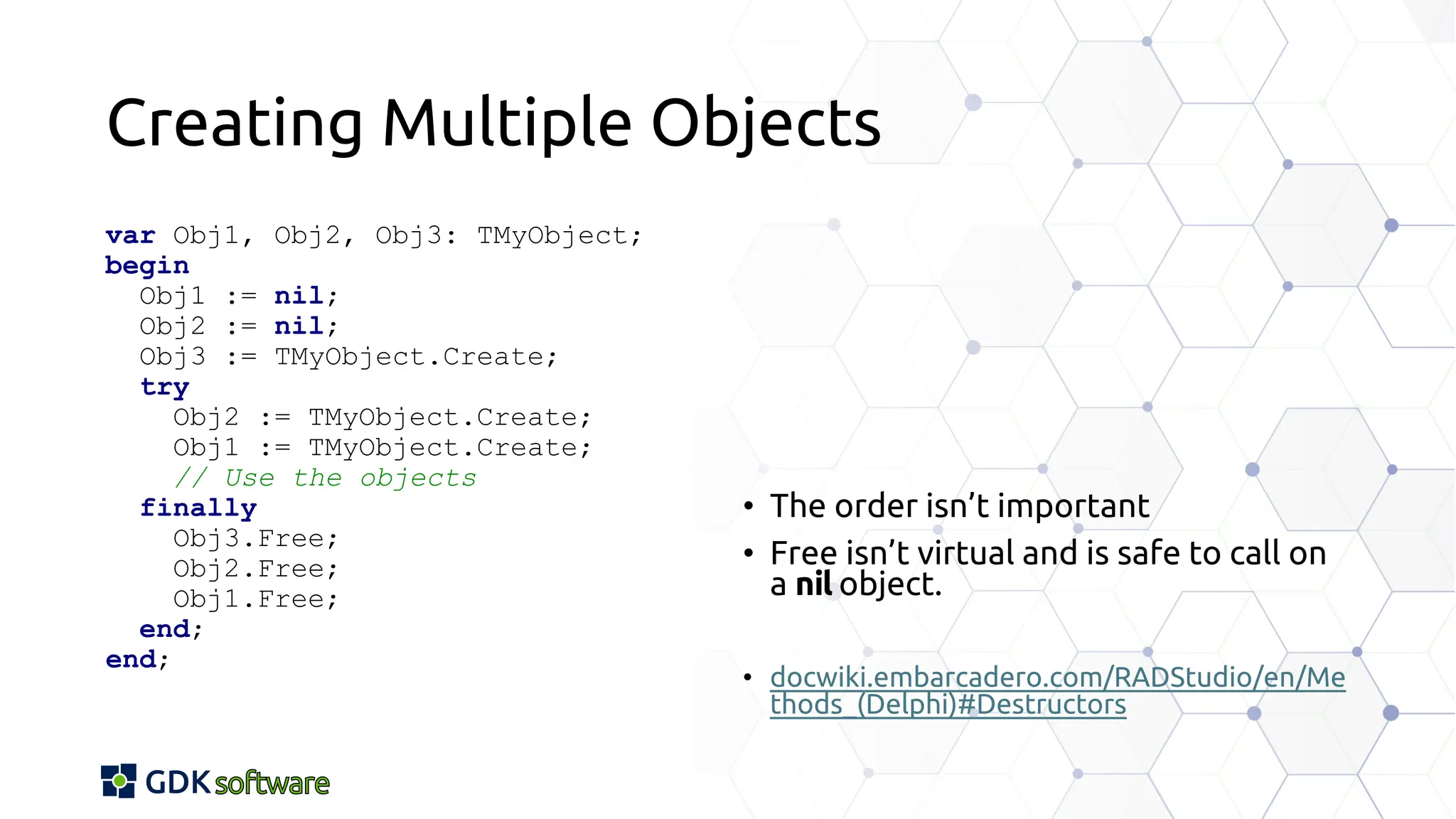
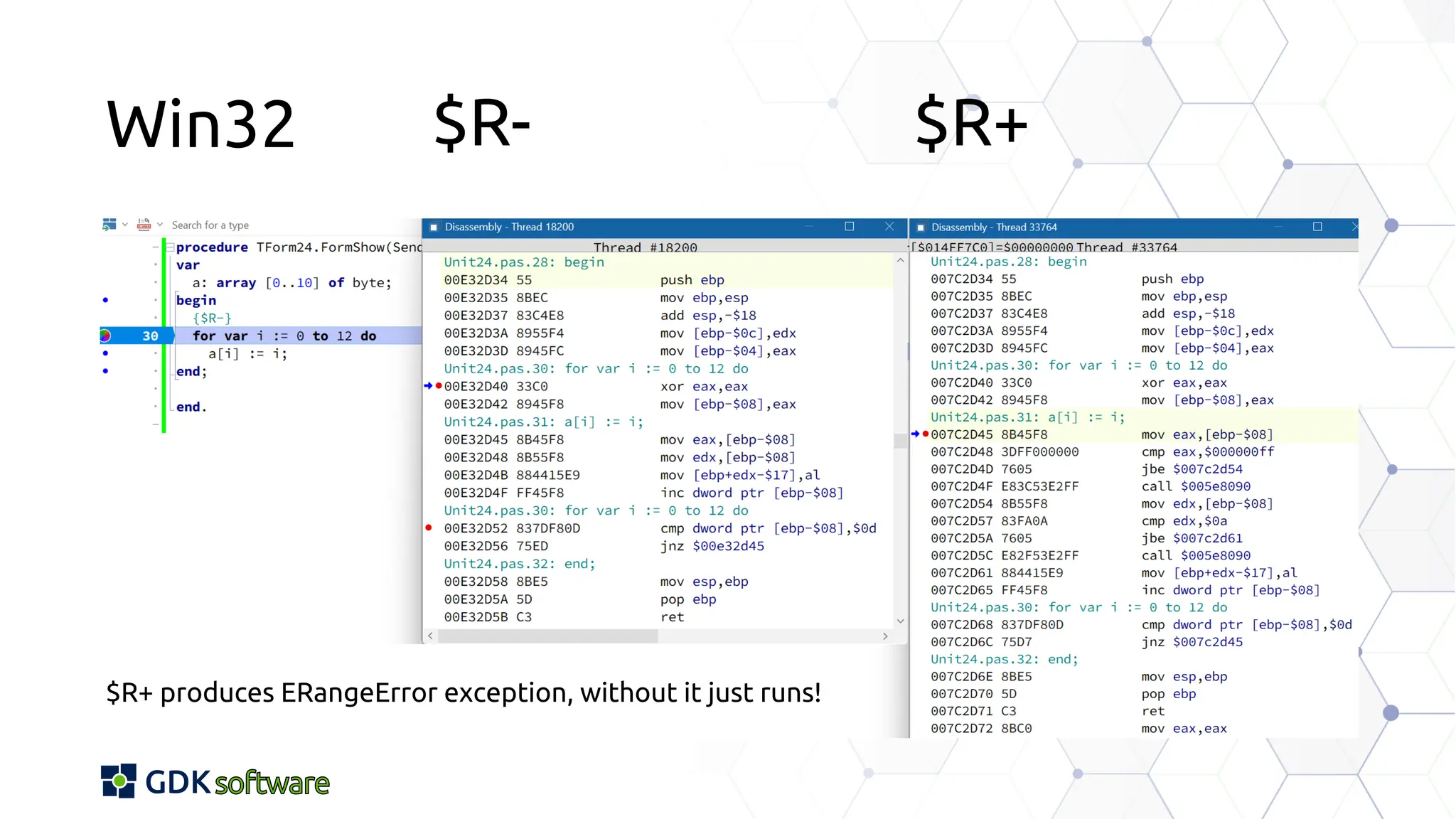
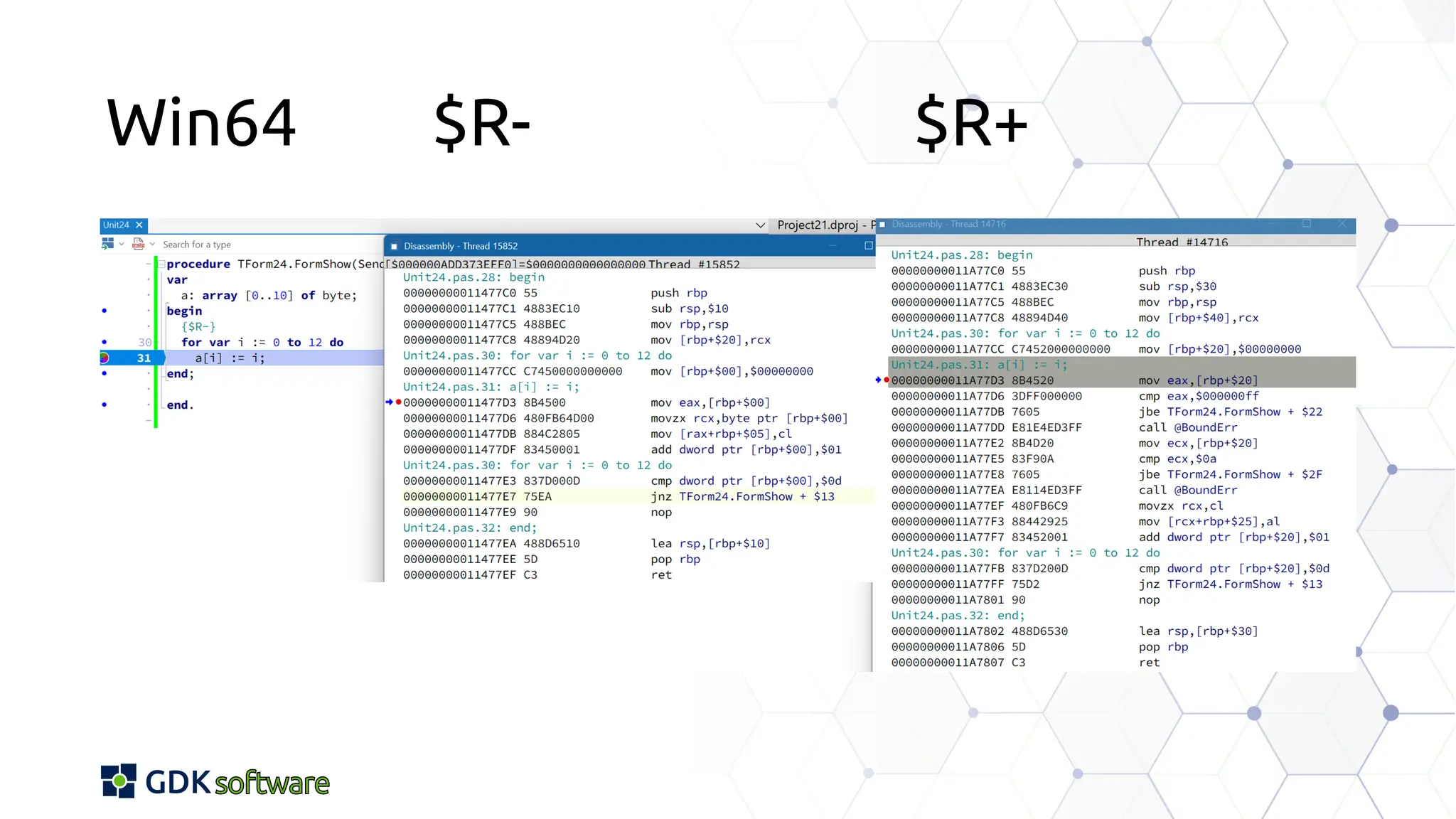
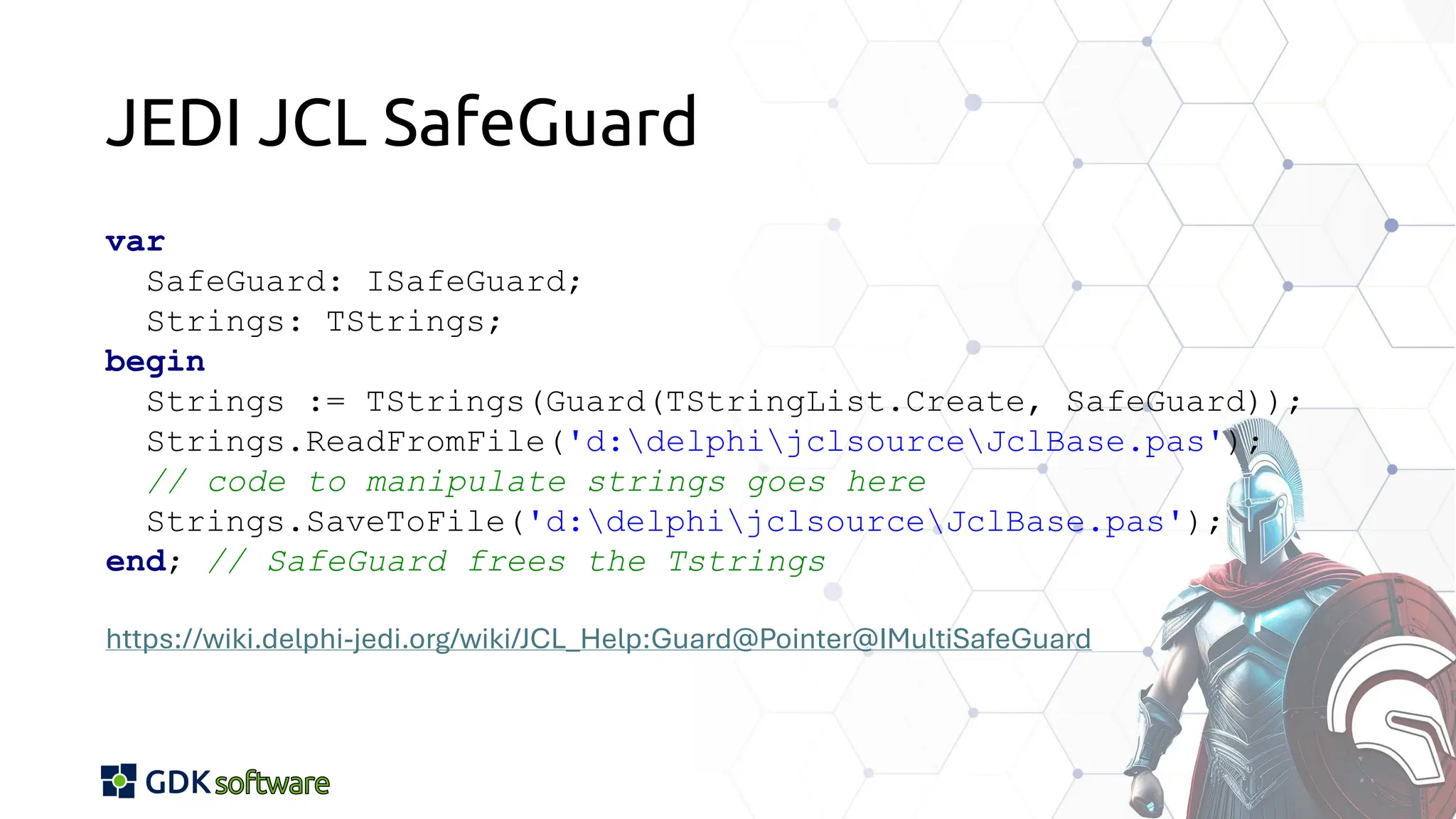
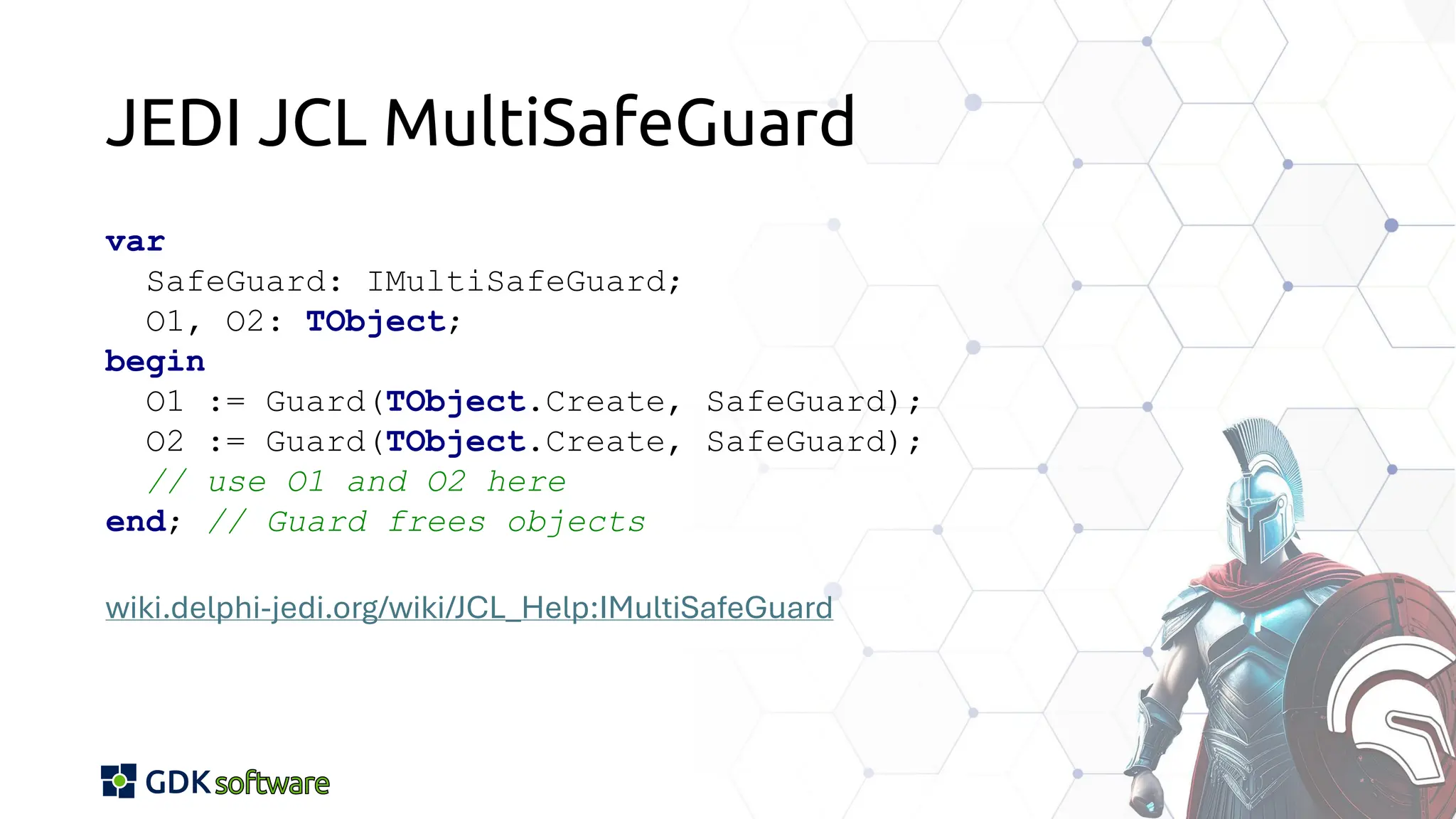
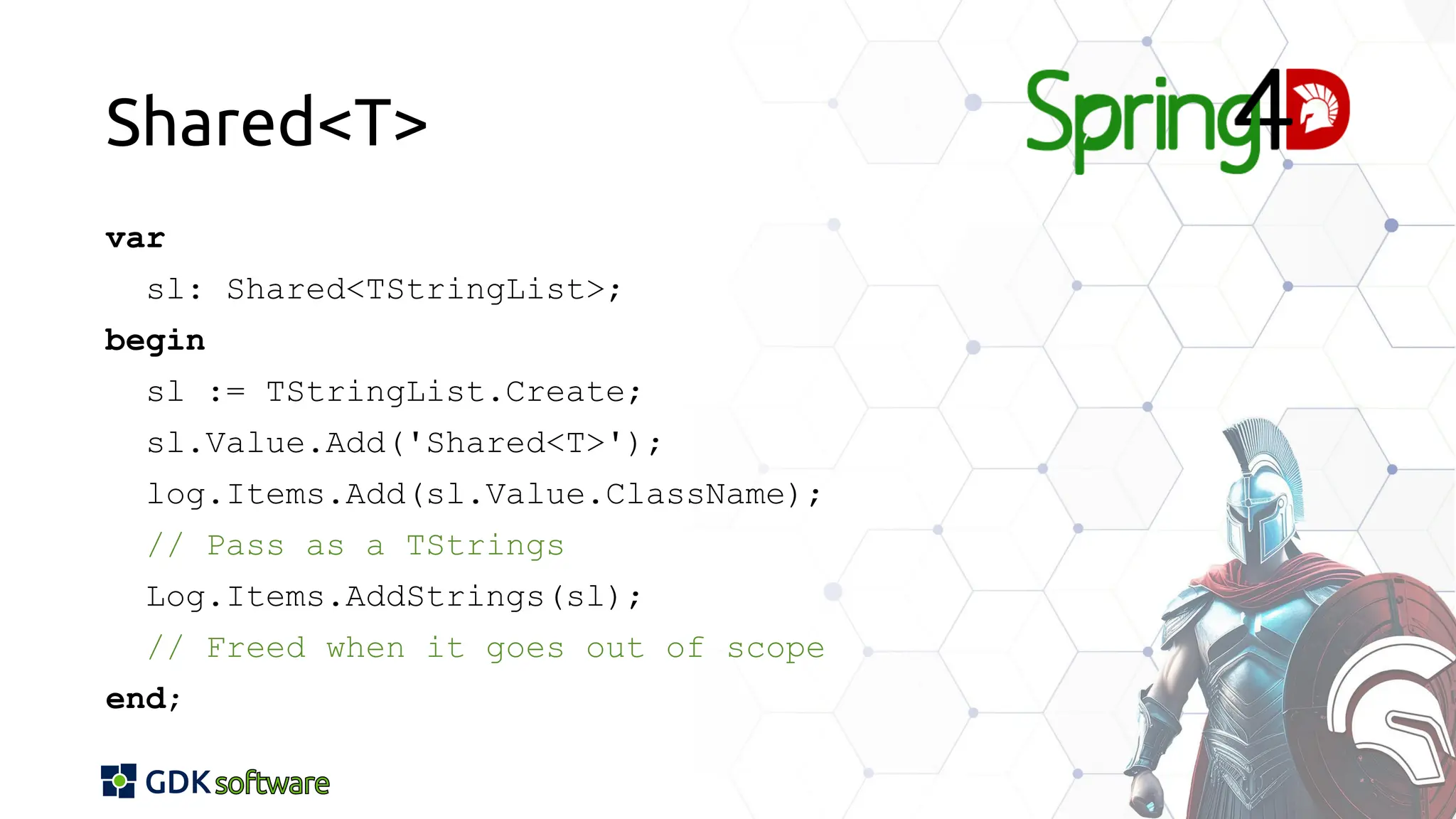
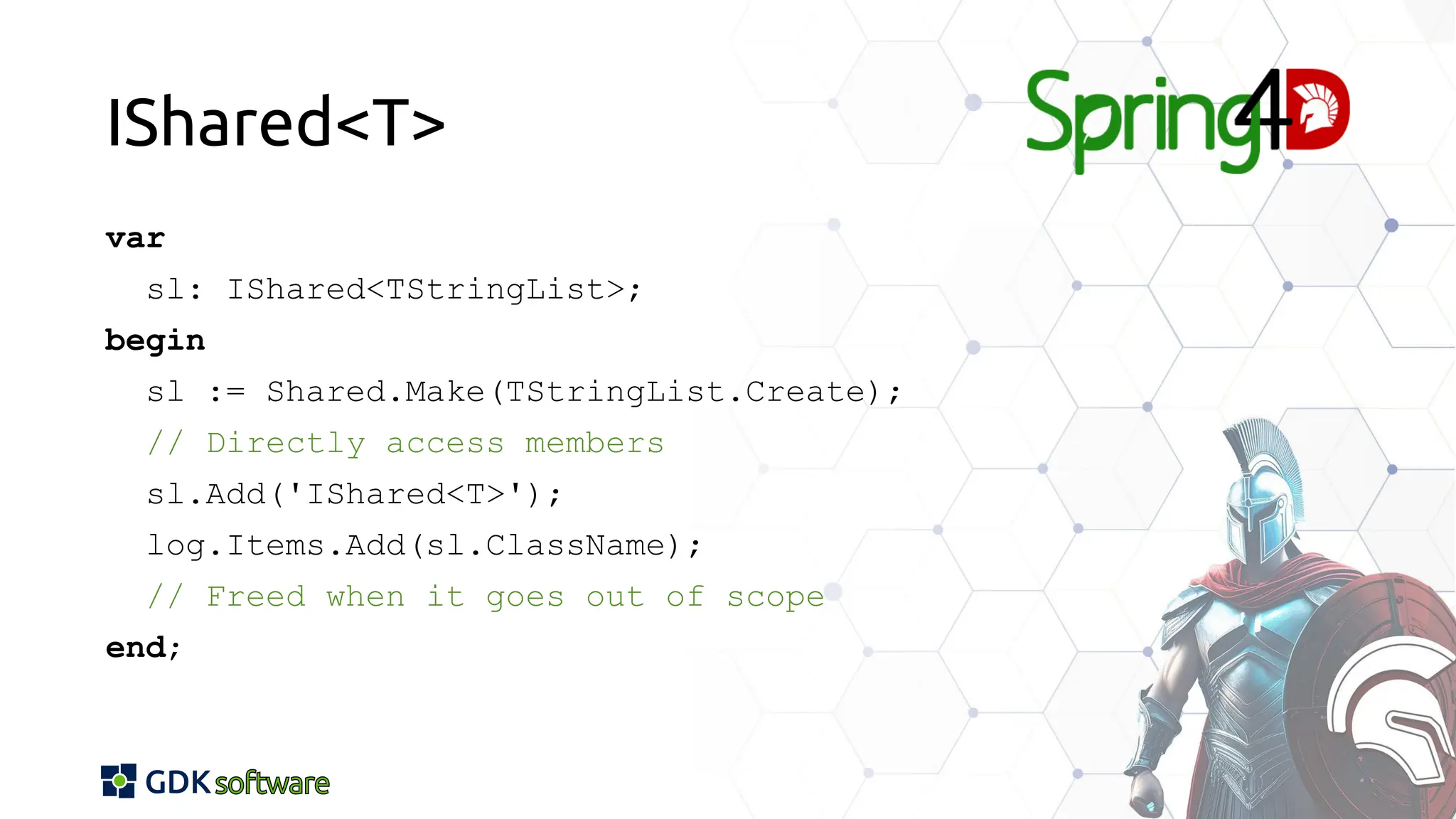
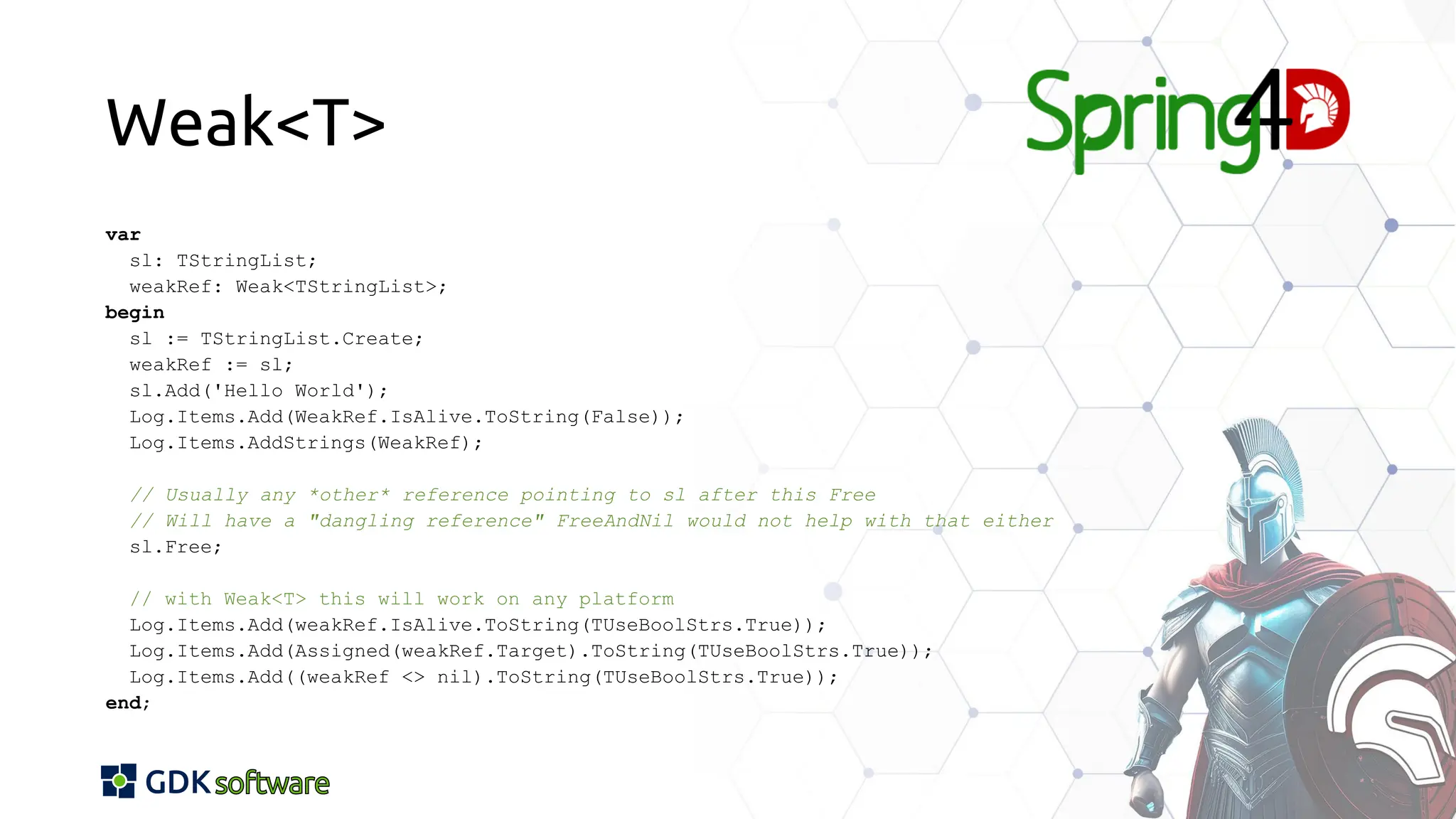
The document discusses memory safety in Delphi, covering essential practices, tools, and techniques for preventing memory-related vulnerabilities. It highlights the importance of strong typing, array bounds checking, and various memory management strategies to mitigate risks like buffer overflows and memory leaks. Additionally, it references a 2024 report emphasizing the significance of memory safety in software development and outlines best practices and resources for Delphi developers.