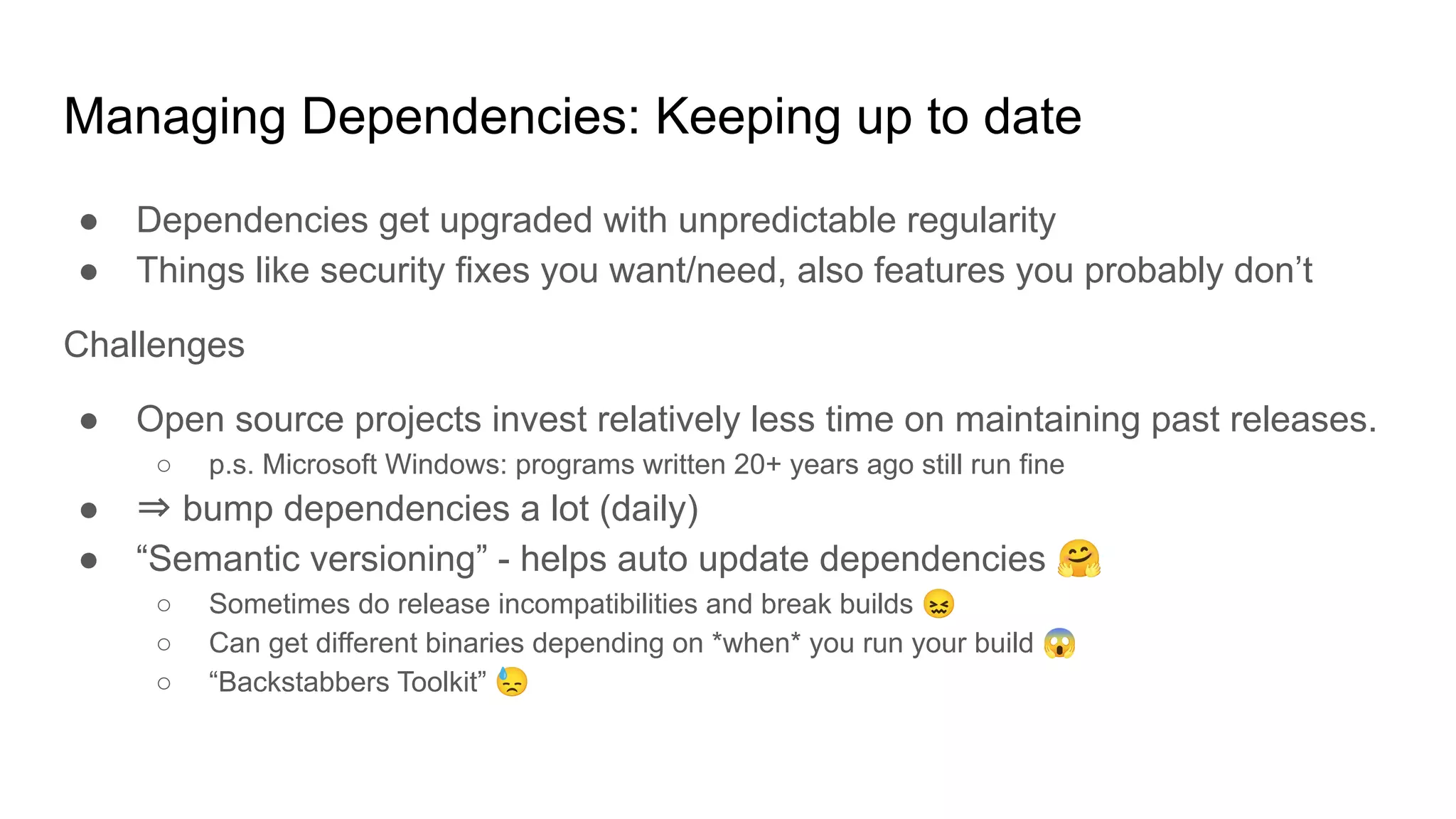
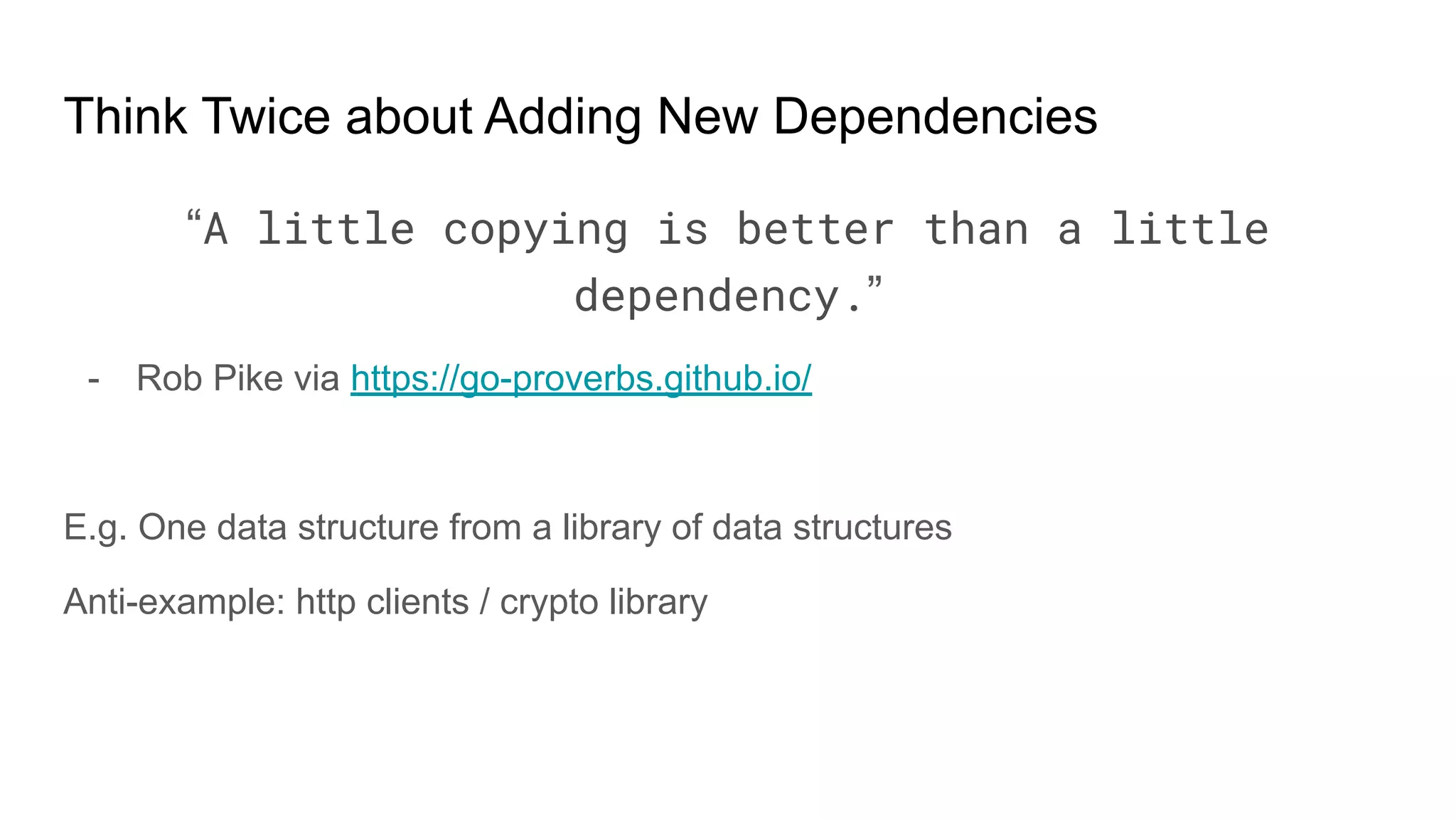
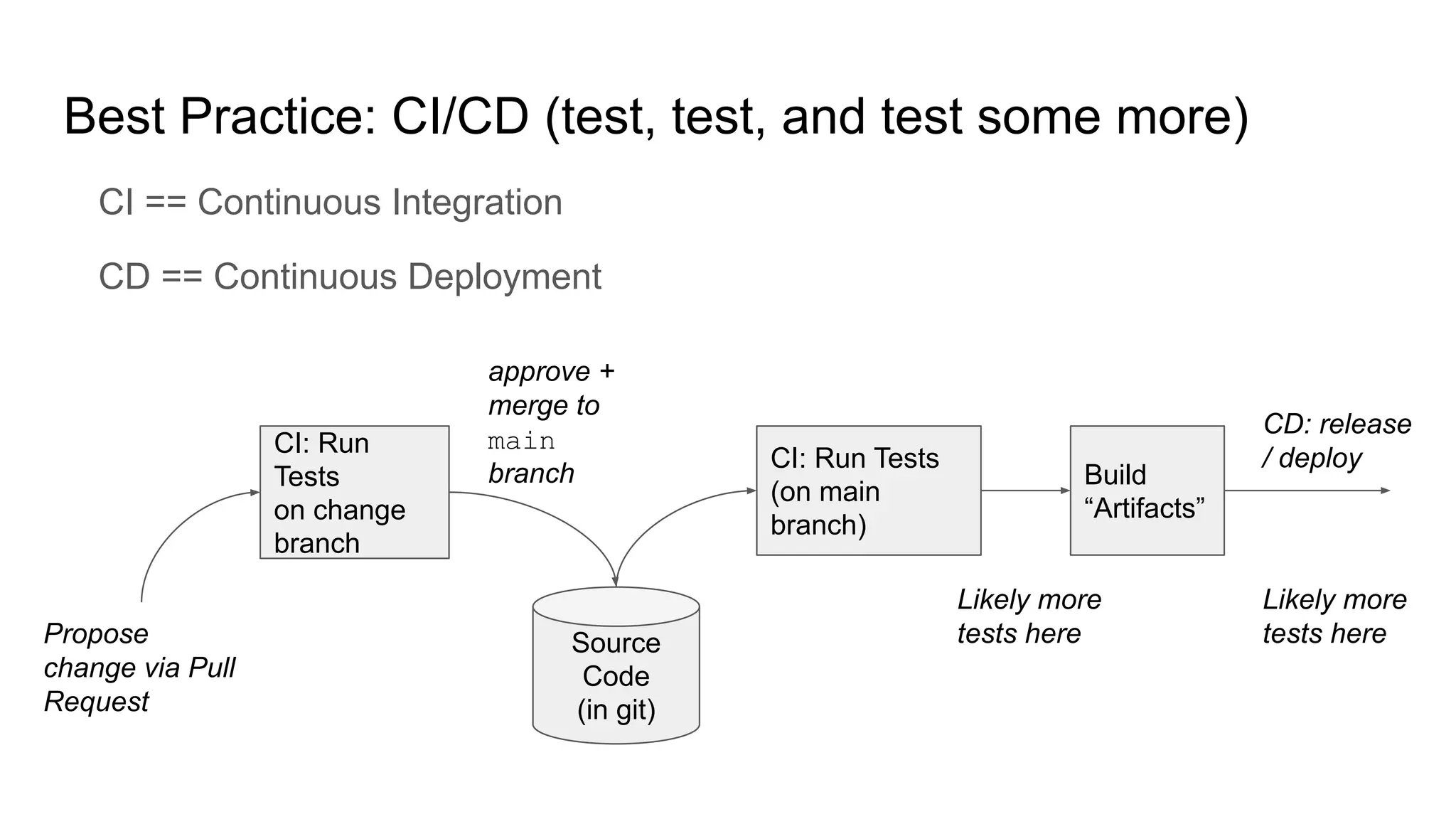
This document discusses managing software dependencies and supply chains. It provides perspectives from commercial and open-source development. While dependencies can lower costs by reusing code, they also introduce risks around licensing, quality, security, build times, packaging, and keeping dependencies up to date. Best practices for managing dependencies include thinking critically about new dependencies, continuous integration and testing, using package managers, keeping dependencies up to date, investing in dependent libraries, and containerization for packaging.











![Readings (tentative):
https://ieeexplore-ieee-org.libproxy.mit.edu/stamp/stamp.jsp?tp=&arnumber=242525 – software maturity
https://www.oreilly.com/library/view/understanding-open-source/0596005814/ch06.html – reasonably thorough overview of software licensing
https://arxiv.org/pdf/2005.09535.pdf – supply-chain attacks
https://blog.npmjs.org/post/141577284765/kik-left-pad-and-npm.html – specific example of how easy/common broad supply-chain breaks are today
[optional] https://blogs.sap.com/2020/06/26/attacks-on-open-source-supply-chains-how-hackers-poison-the-well/
[optional] https://www.gnu.org/licenses/license-compatibility.en.html
[optional] https://www.tandfonline.com/doi/pdf/10.1080/14783360500235819?needAccess=true – software maturity](https://image.slidesharecdn.com/managingsoftwaredependenciesandthesupplychainmitem-220410121748/75/Managing-Software-Dependencies-and-the-Supply-Chain_-MIT-EM-S20-pdf-23-2048.jpg)