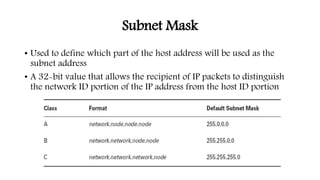
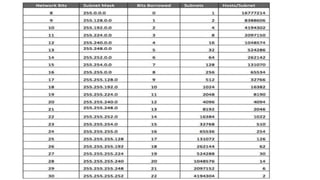
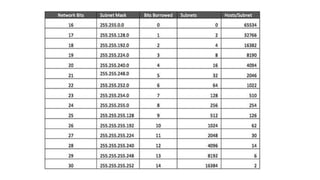
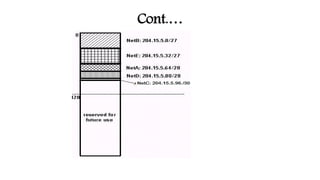
This document provides an introduction to IP addressing and subnetting. It discusses key topics including IP addresses and versions IPv4 and IPv6, network classes in IPv4, subnet masks, private addresses, Classless Inter-Domain Routing (CIDR), gateway addresses, and subnetting including variable length subnet masks. Examples are provided to illustrate subnetting networks and determining valid subnets, broadcast addresses, and host ranges.