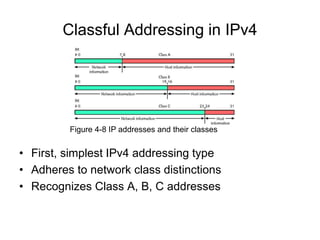
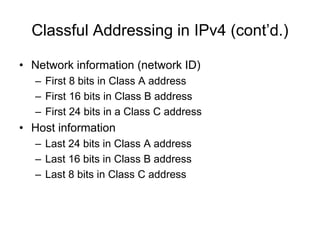
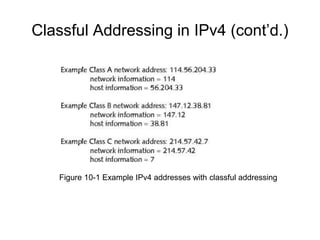
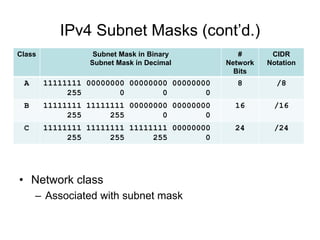
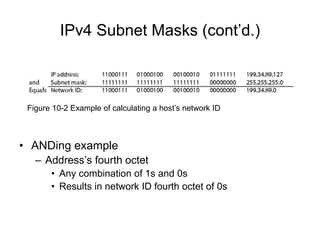
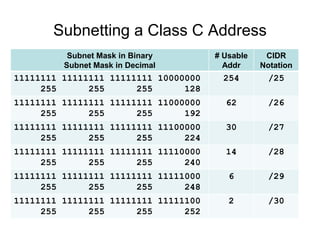
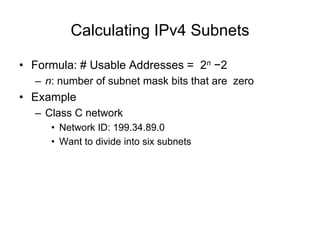
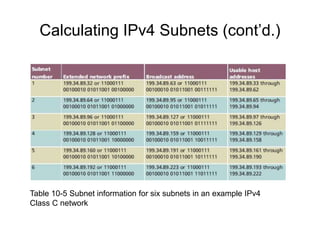
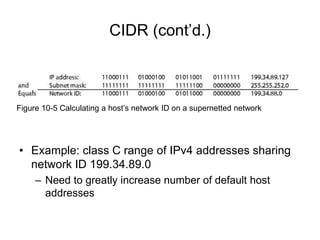
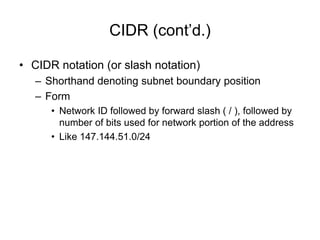
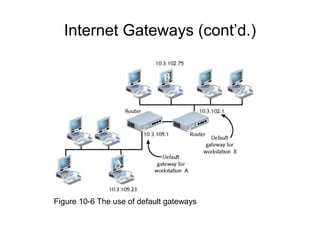
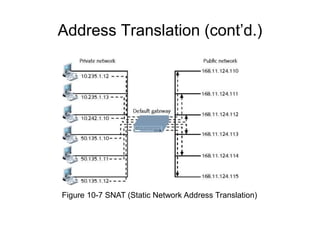
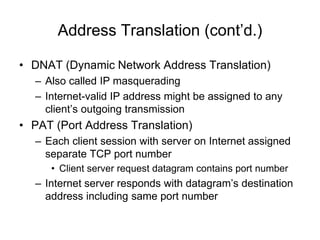
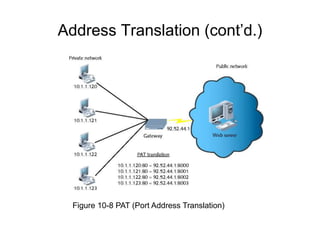
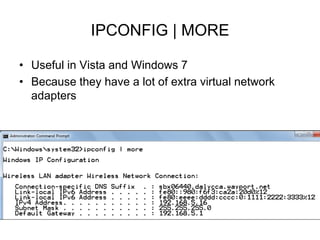
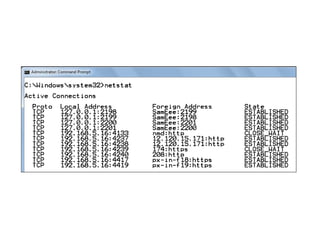
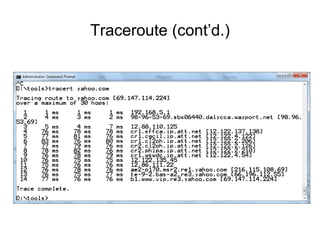
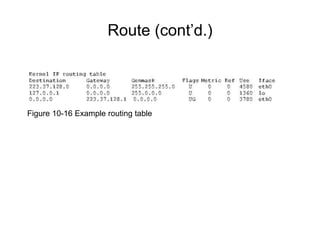
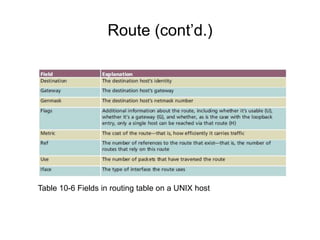
Chapter 10 of the Network+ Guide to Networks covers TCP/IP networking design, detailing concepts like subnetting, classful addressing, and address translation. It explains the differences between public and private networks, as well as protocols for email communication like SMTP, POP3, and IMAP4. The chapter also discusses various TCP/IP utilities for network troubleshooting, including IP configuration commands and diagnostic tools.