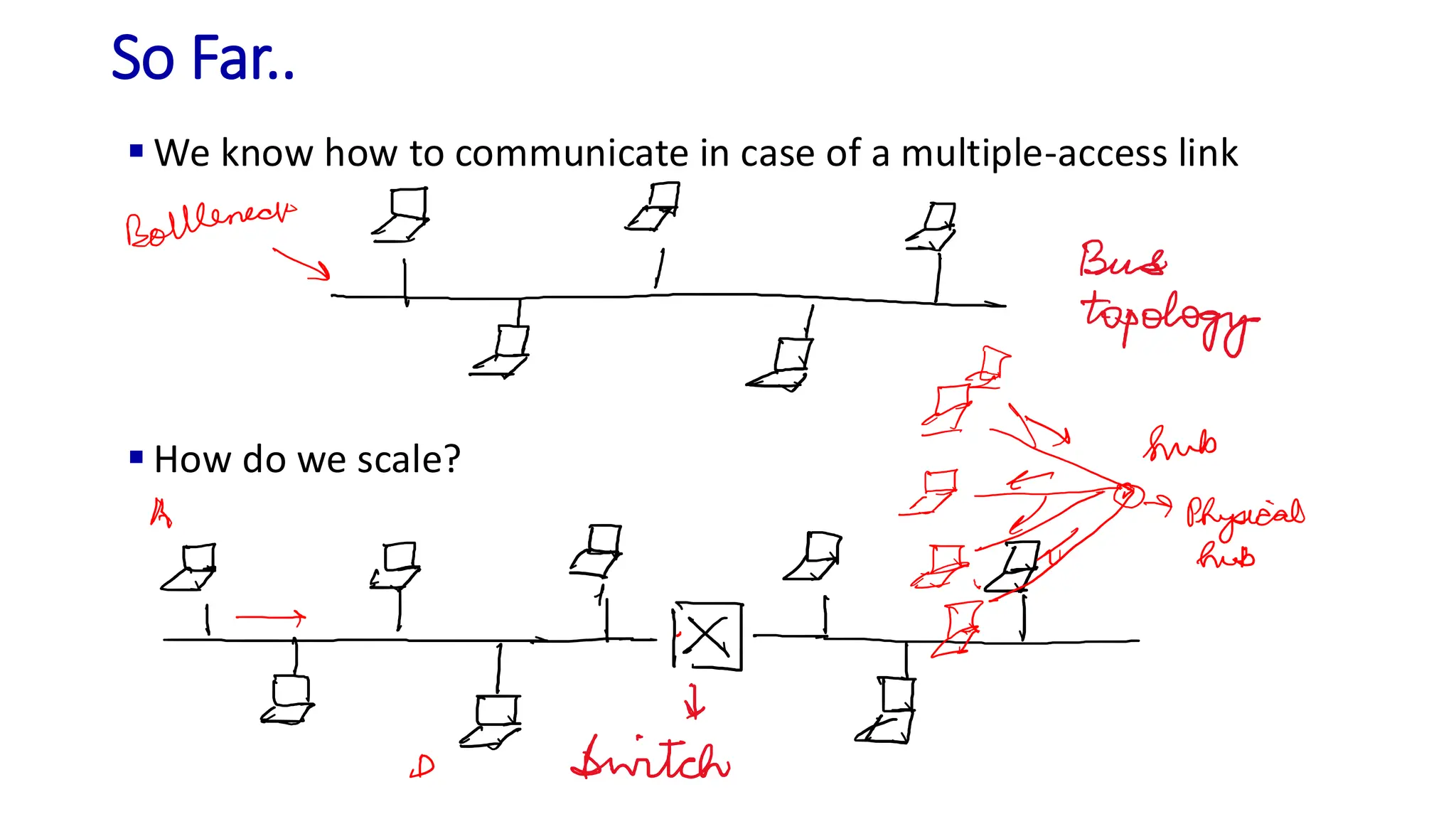
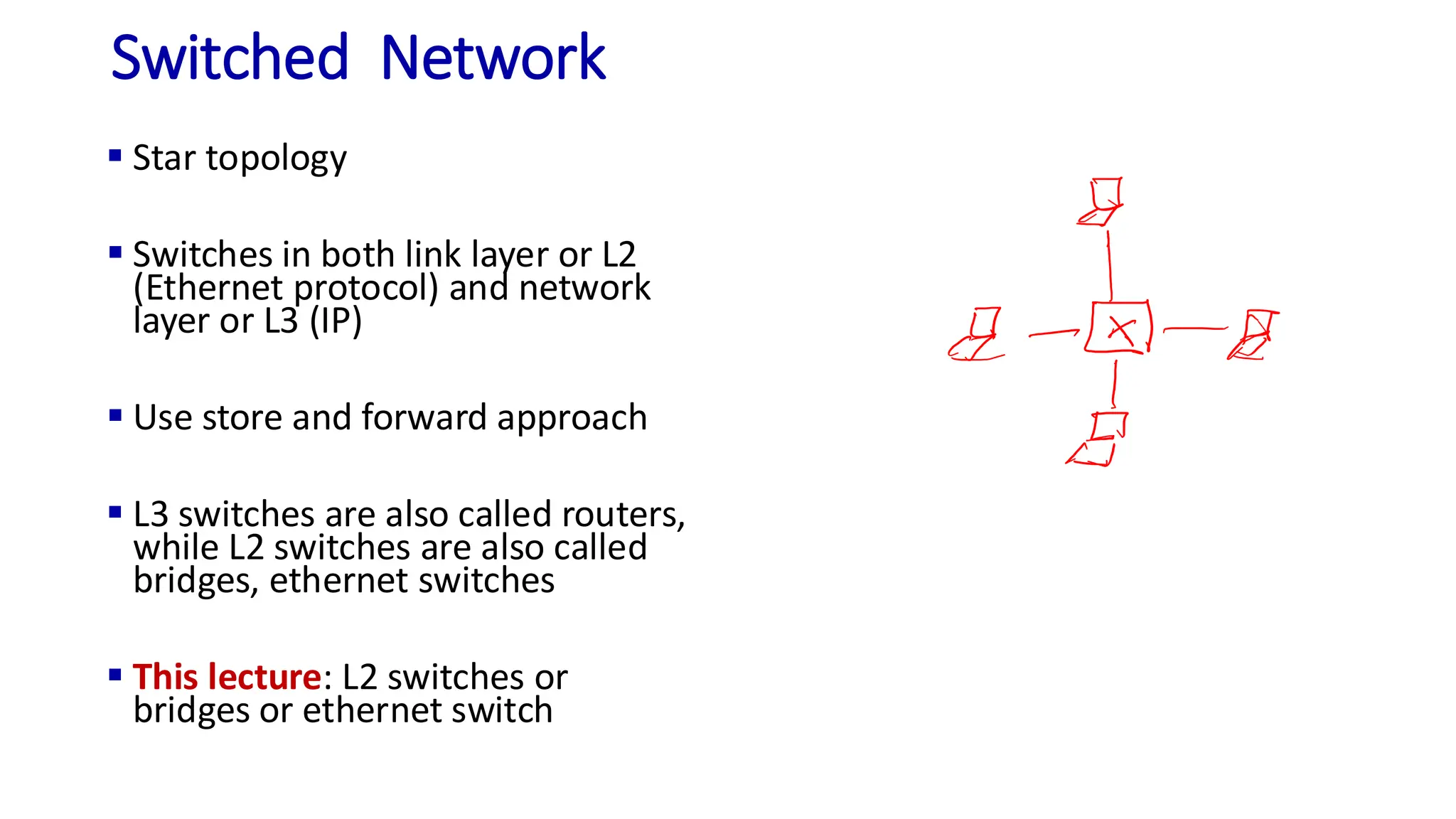
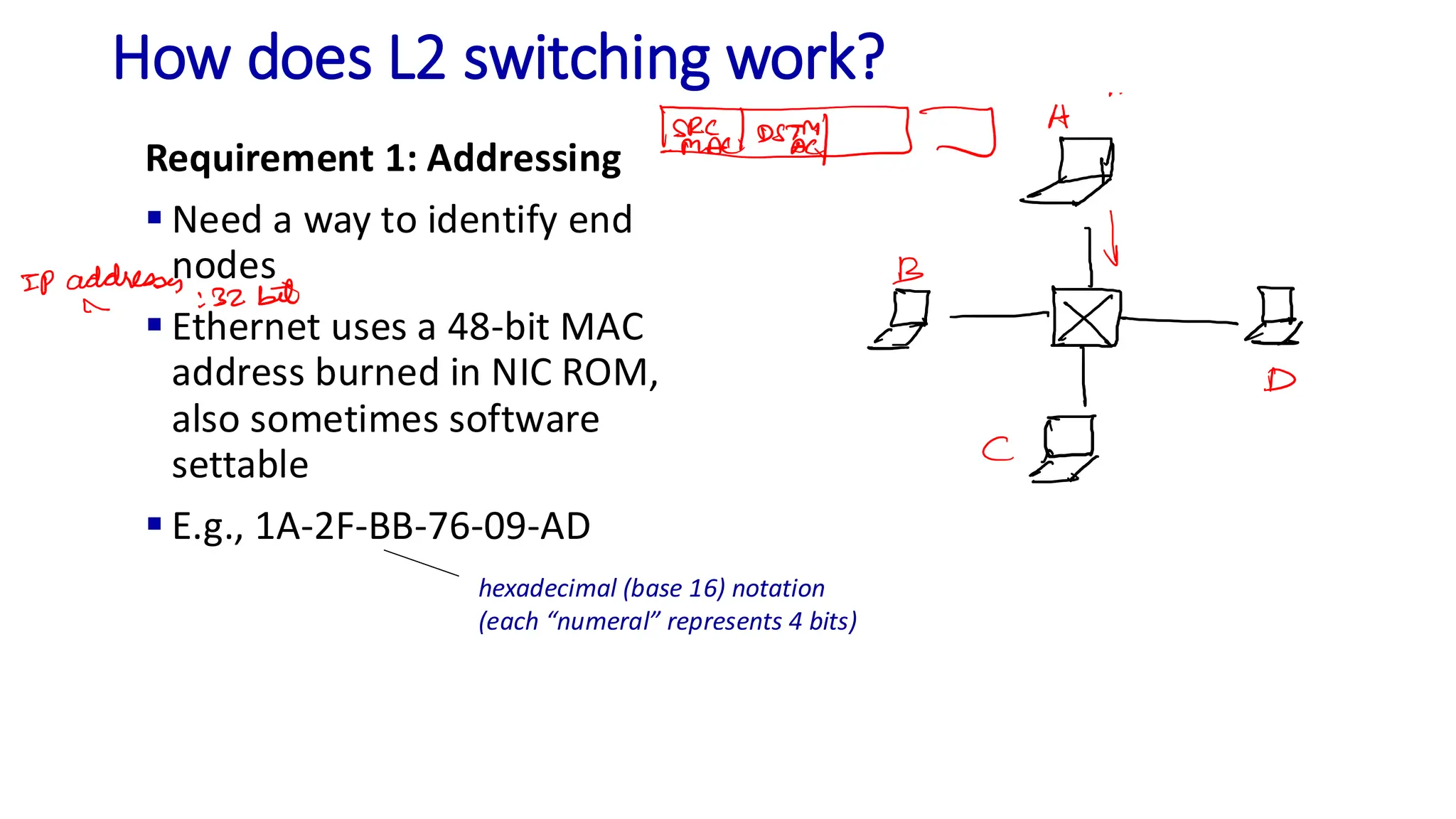
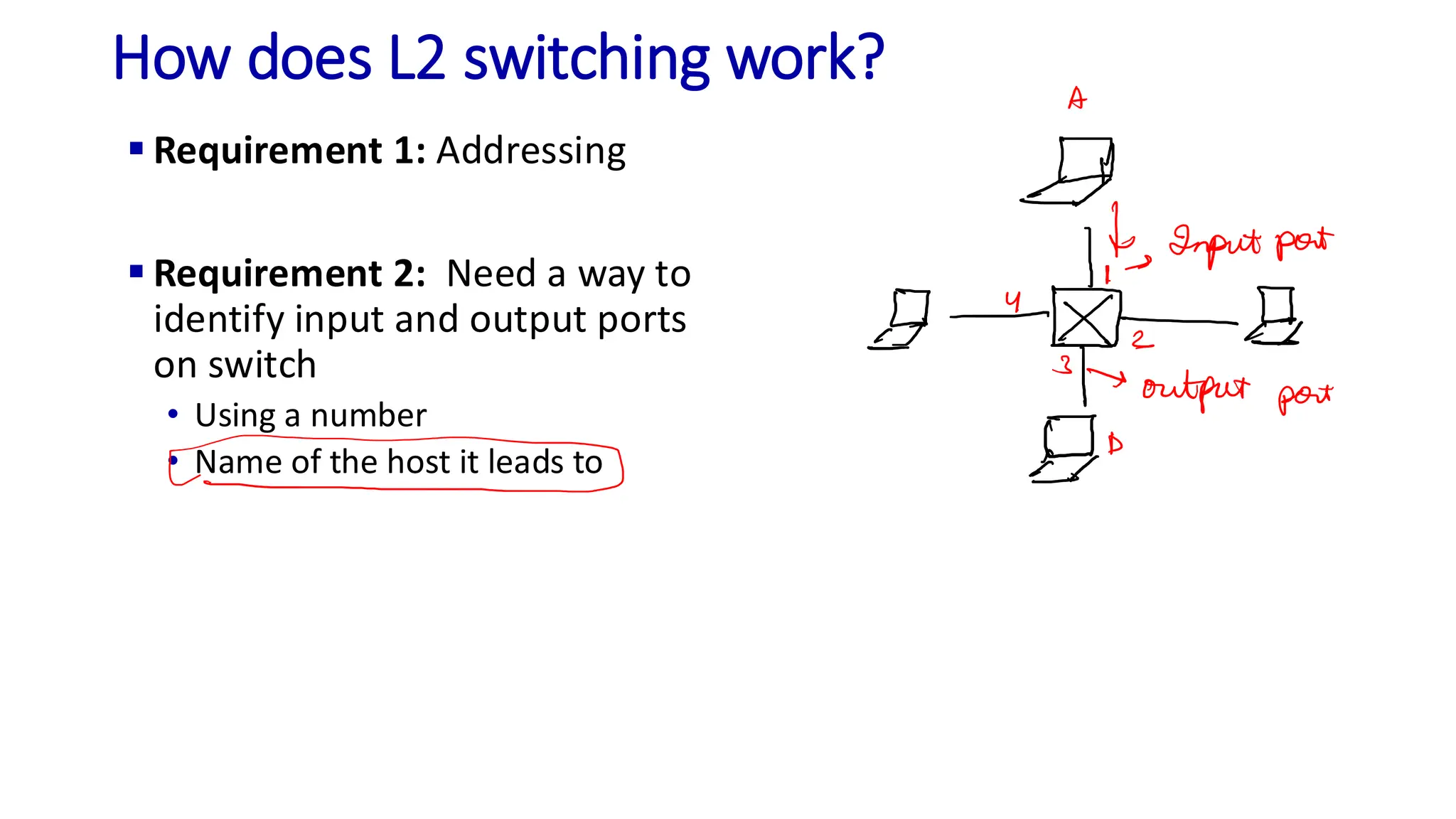
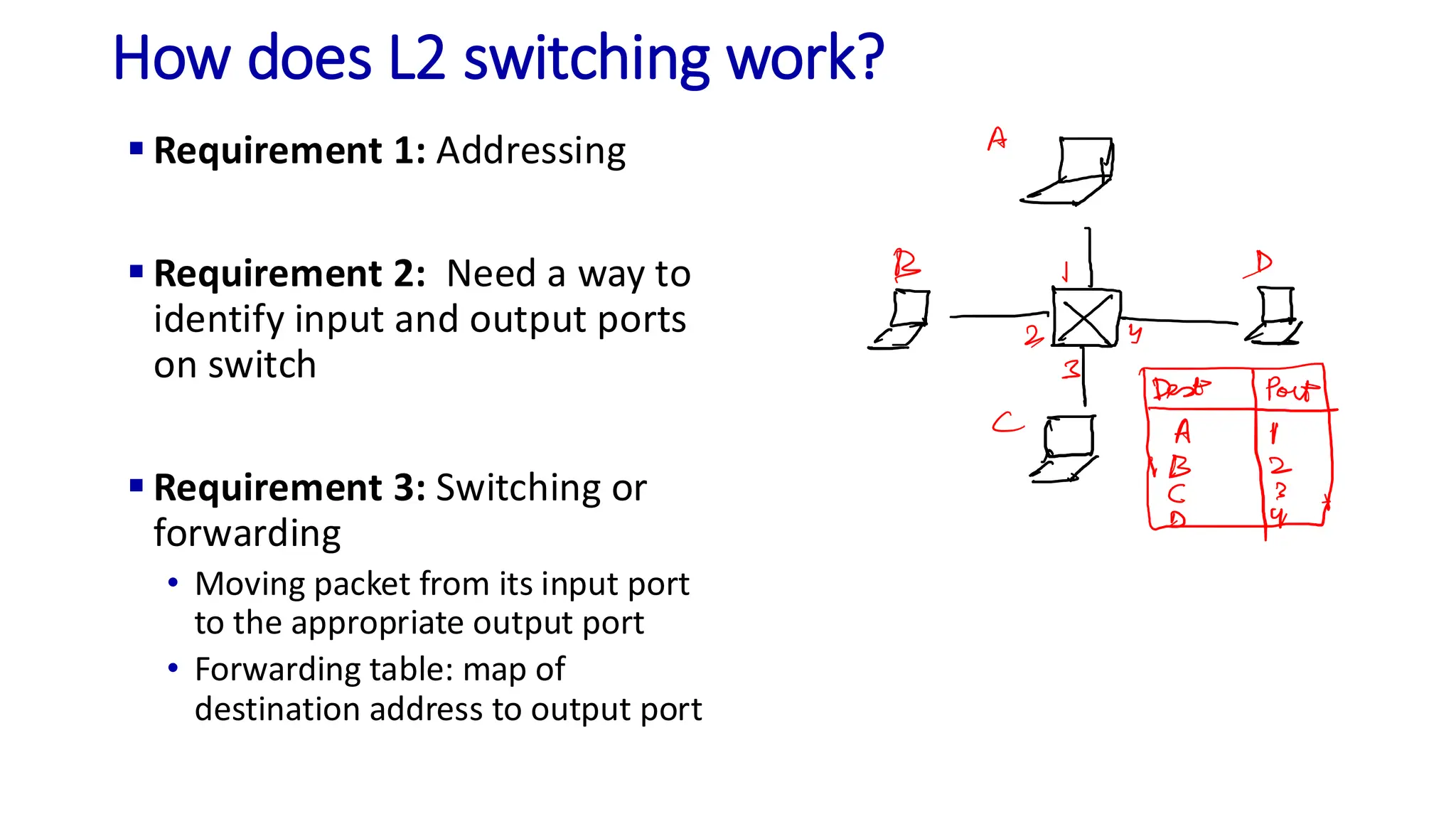
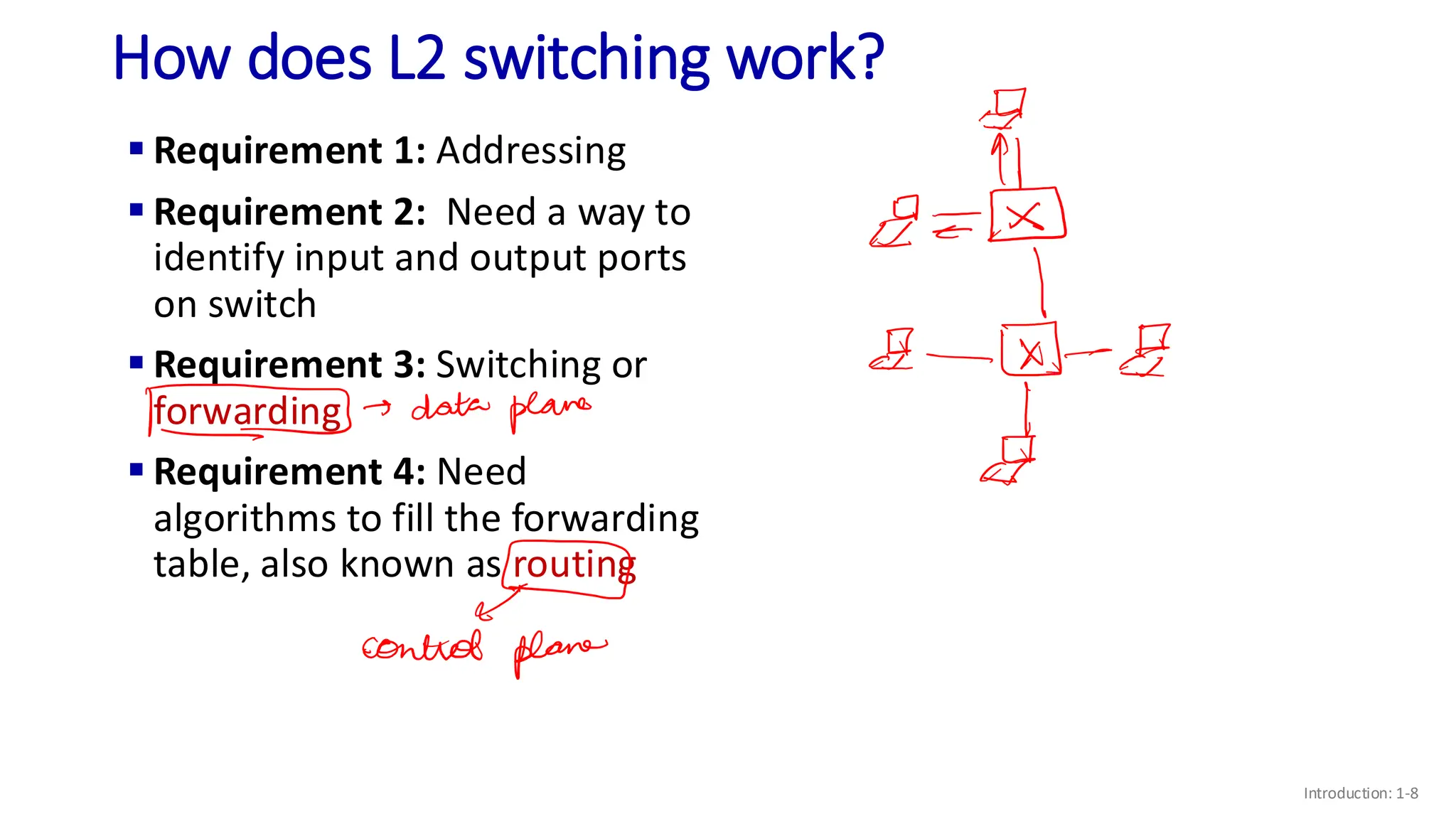
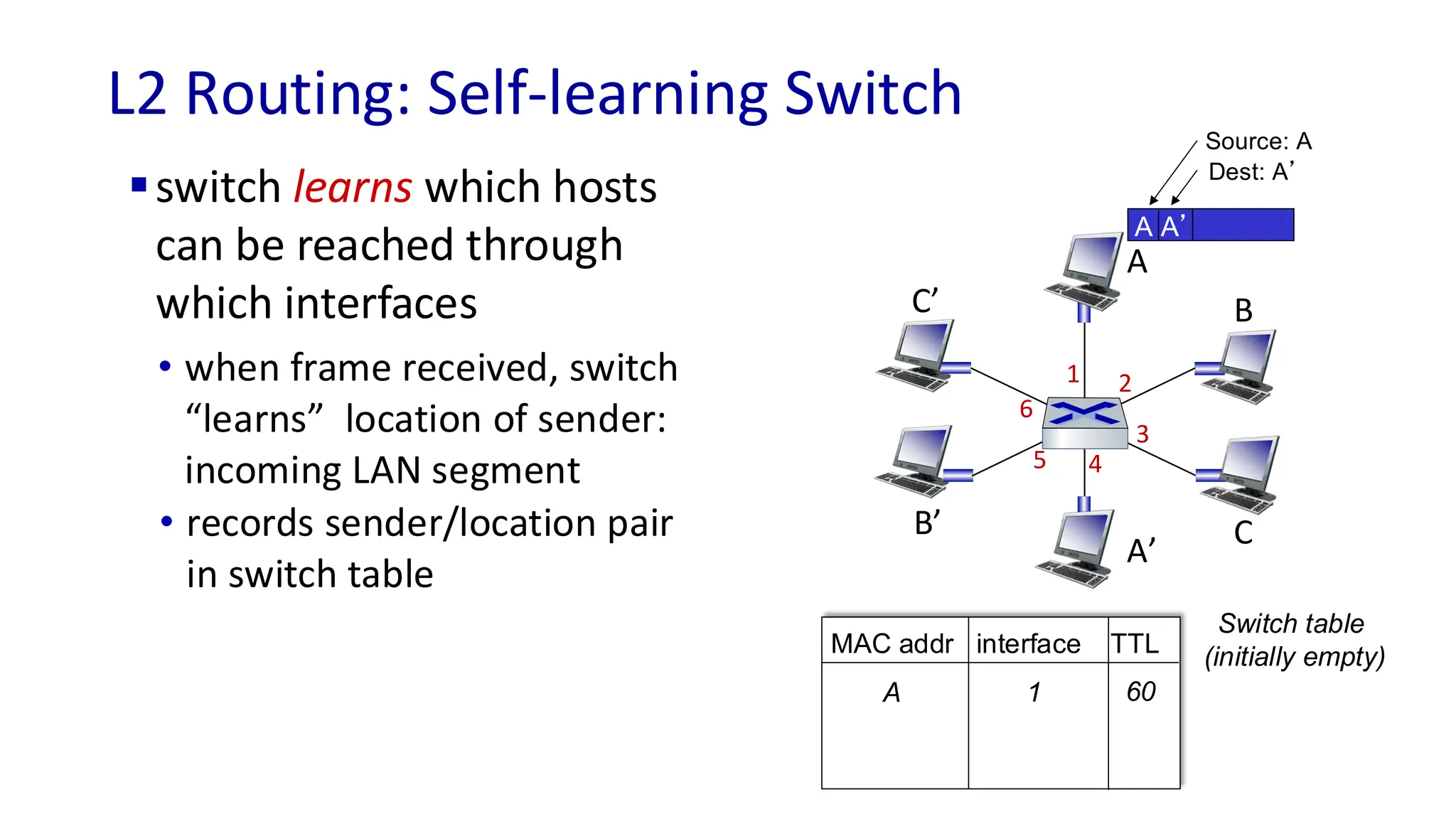
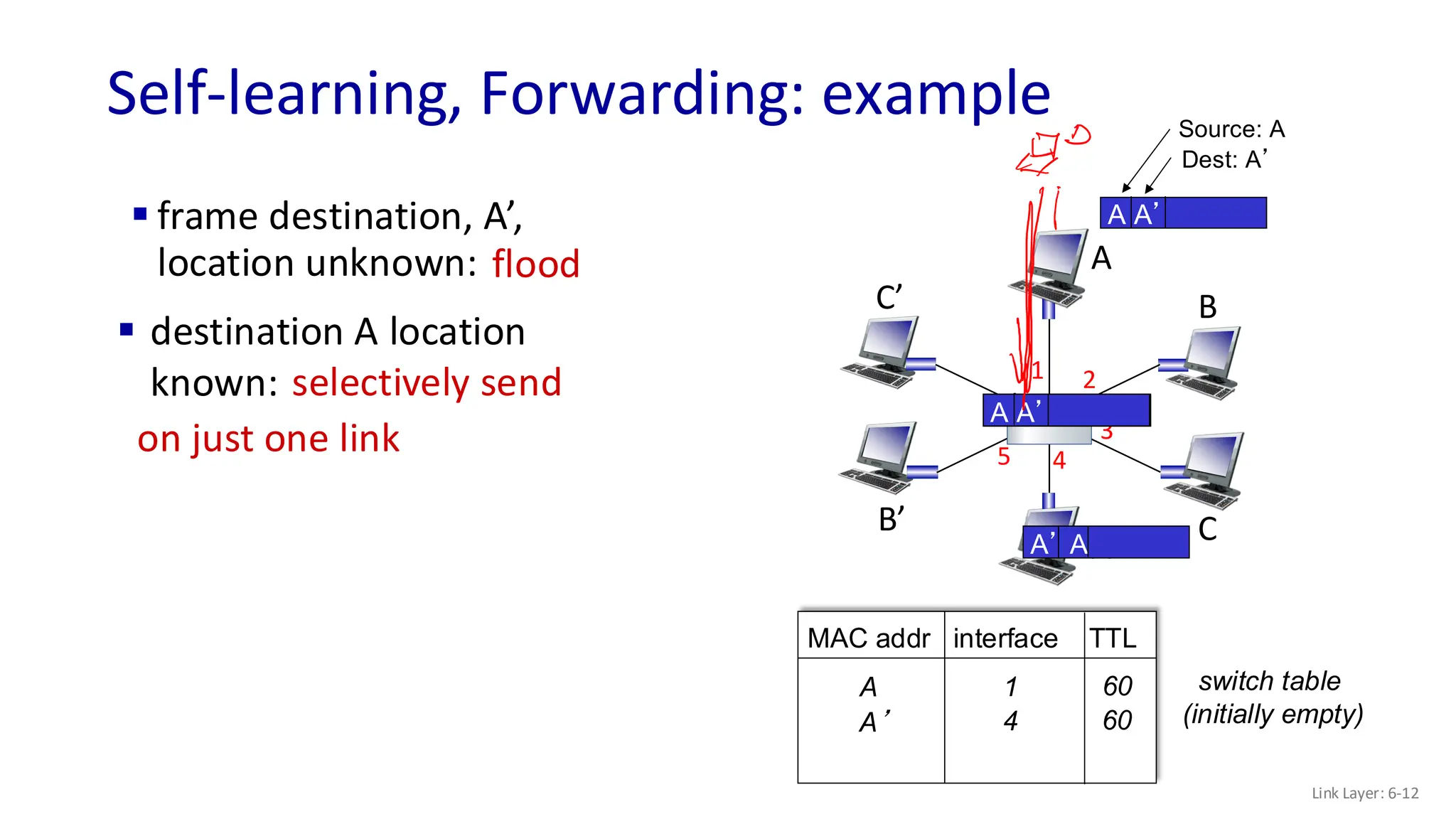
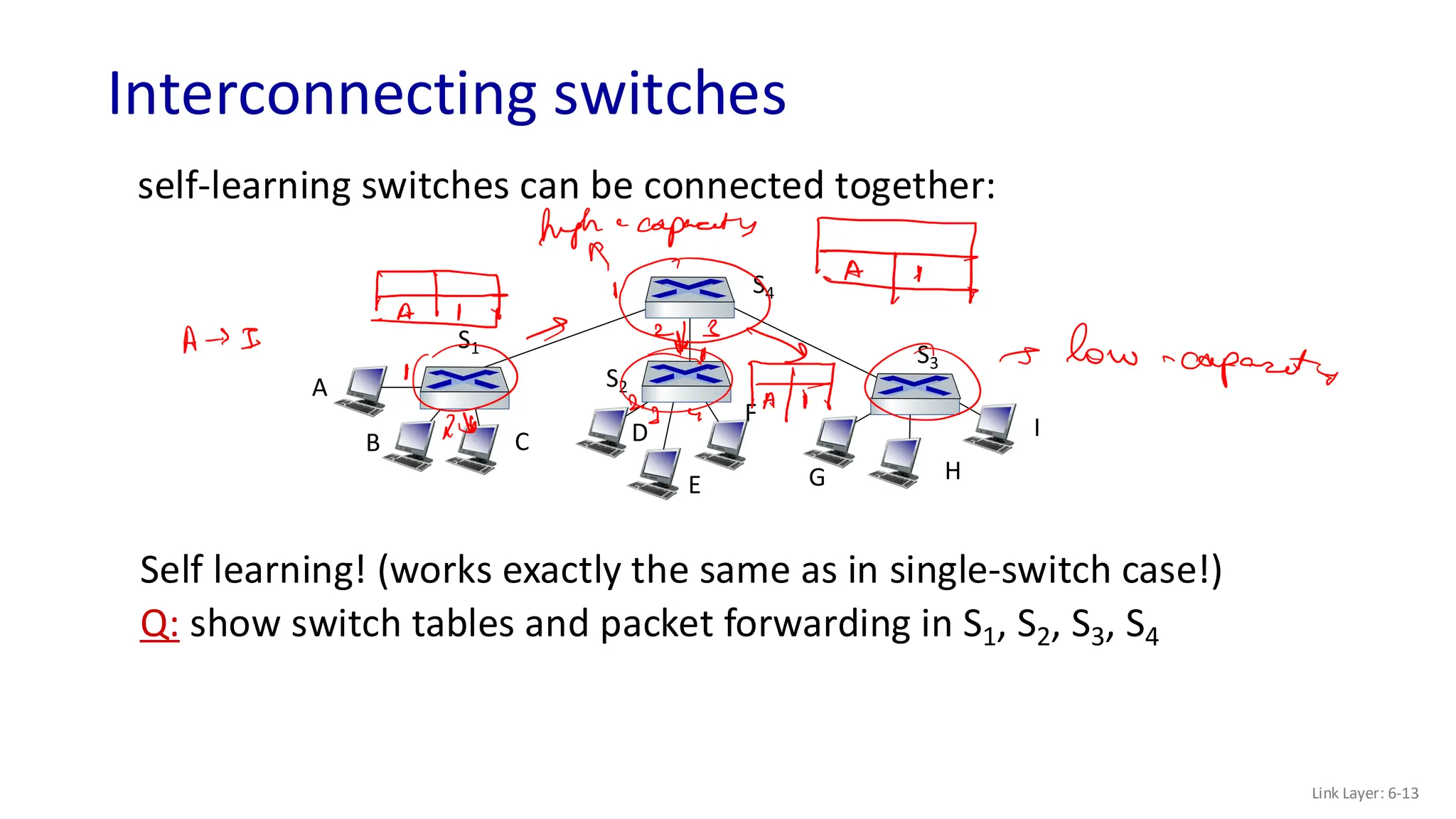
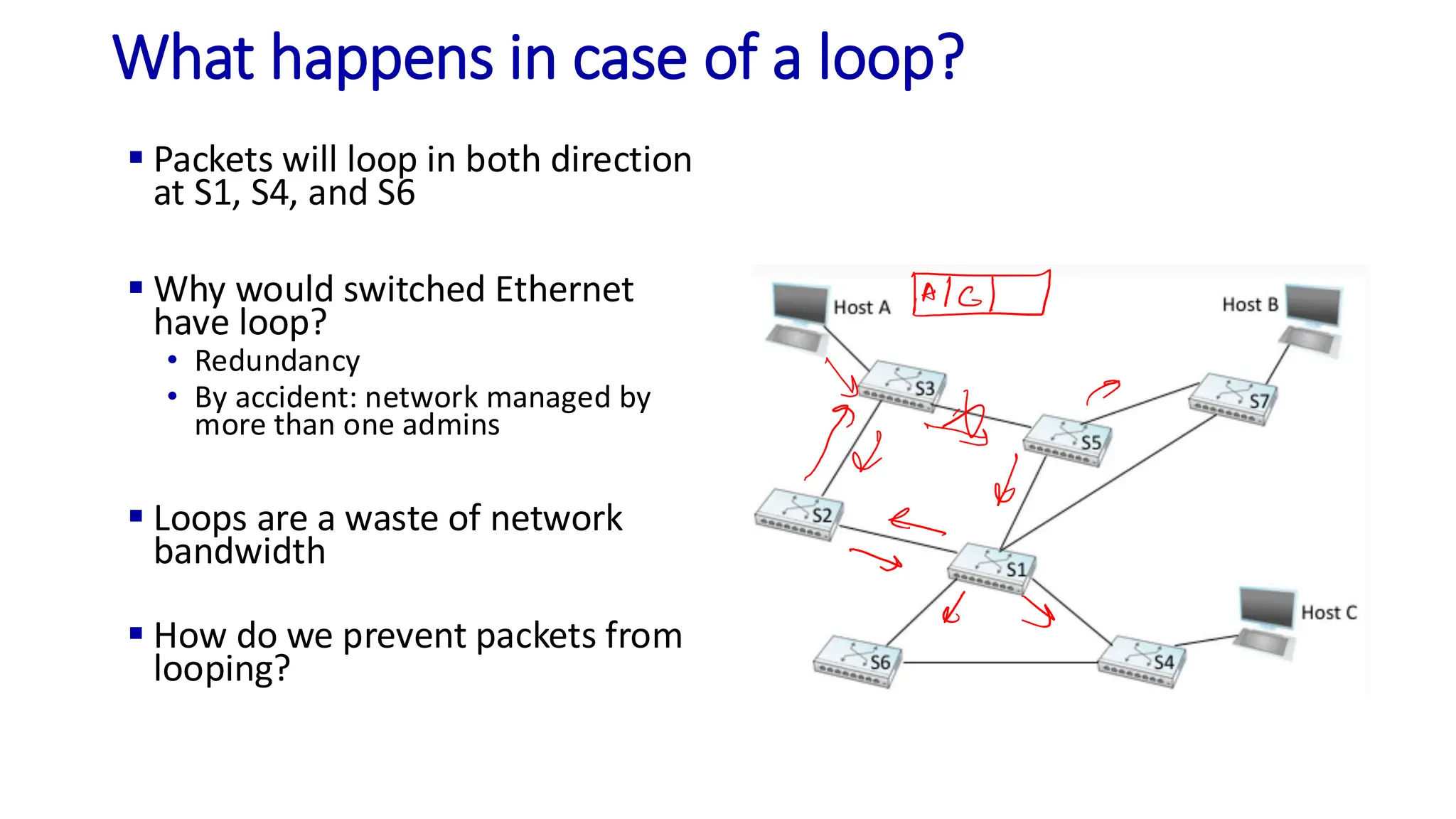
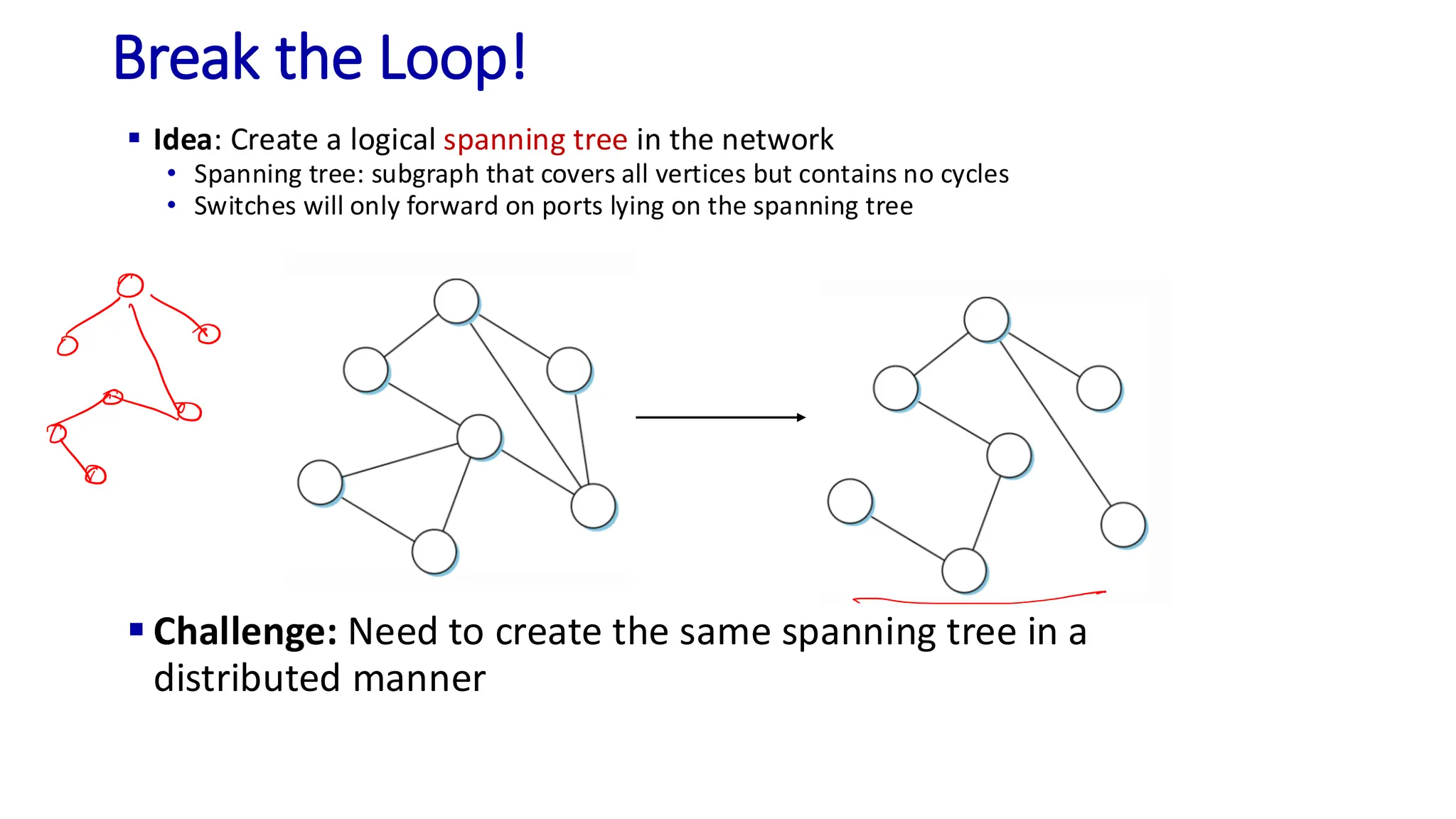
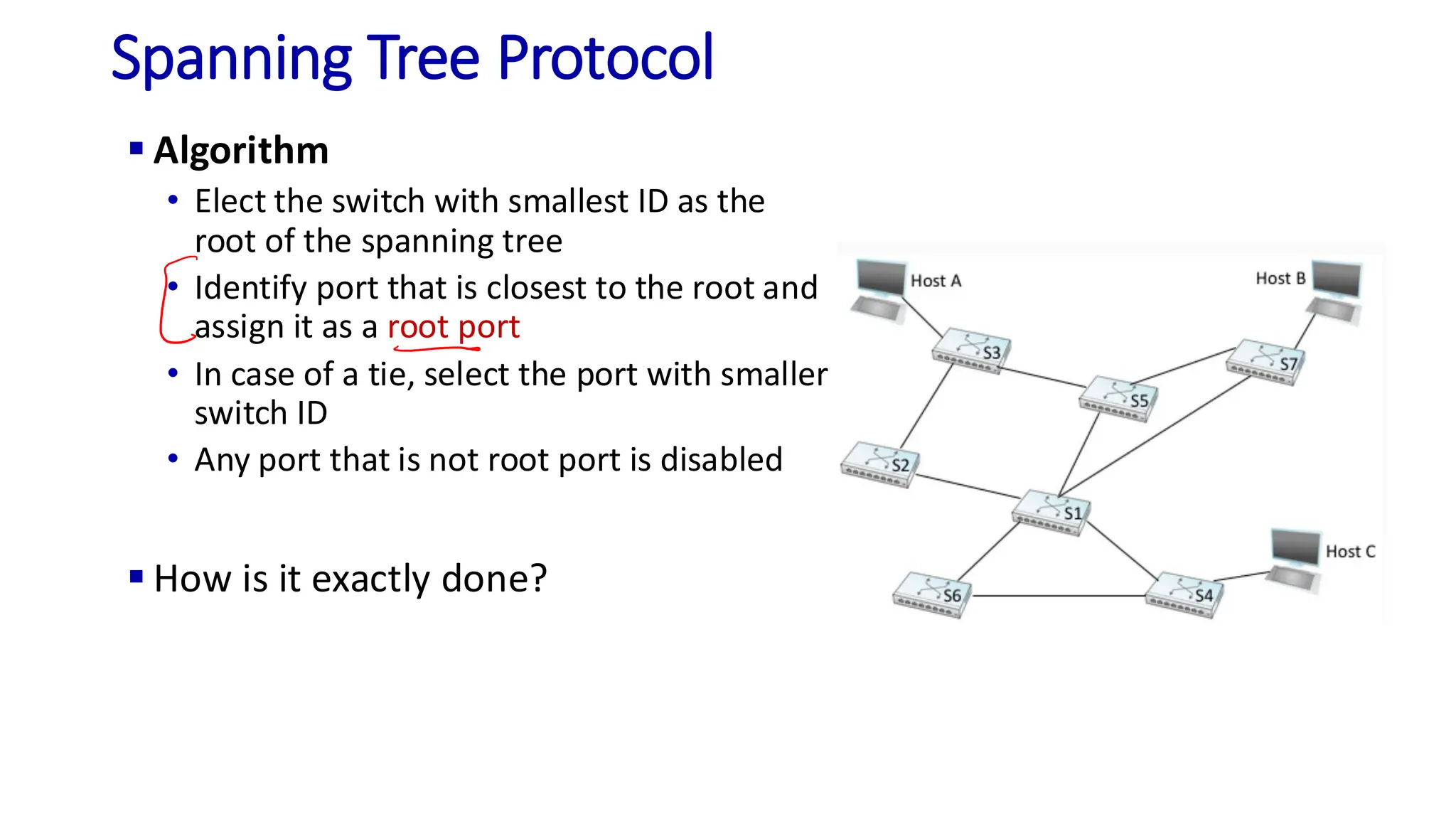
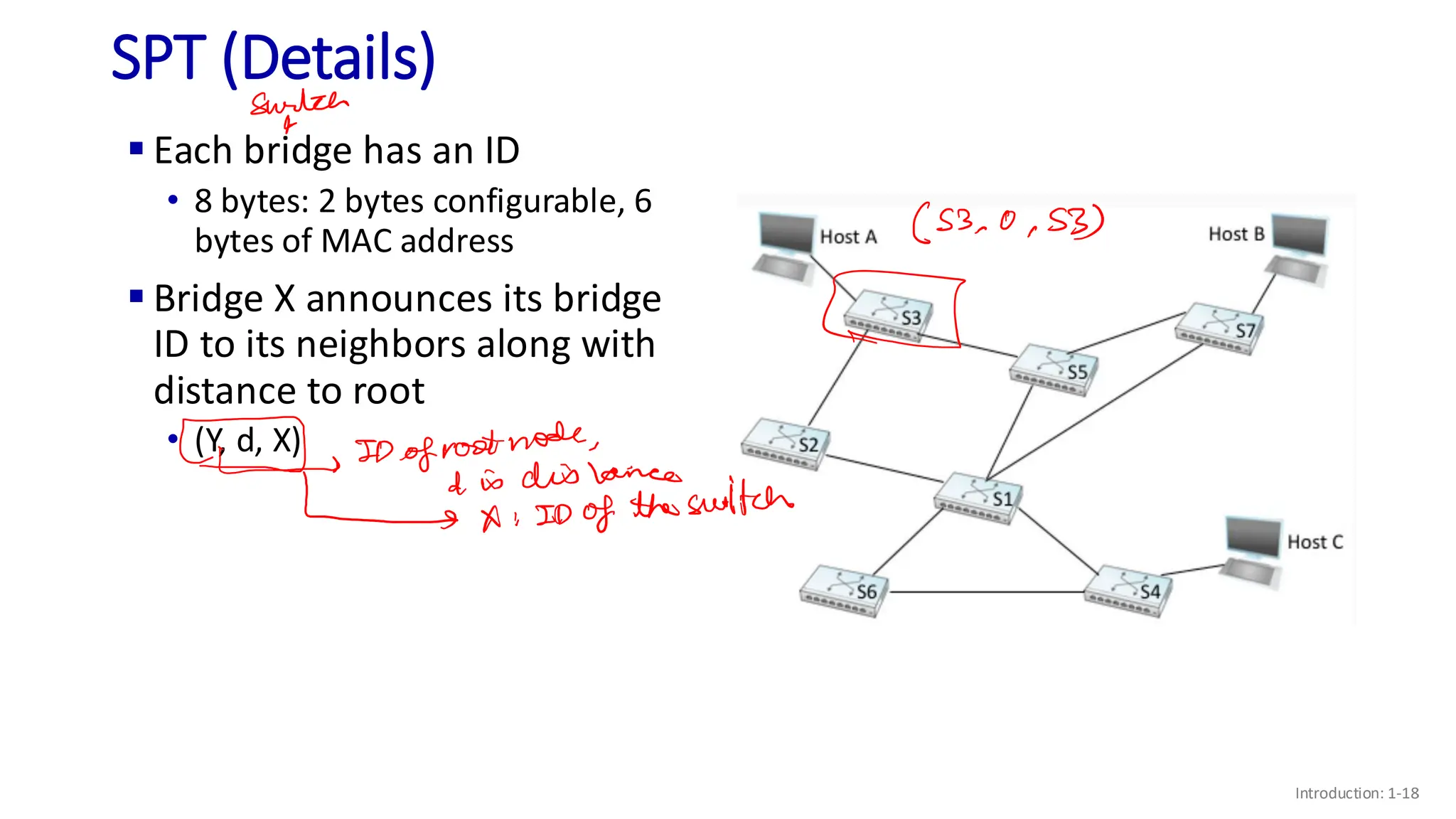
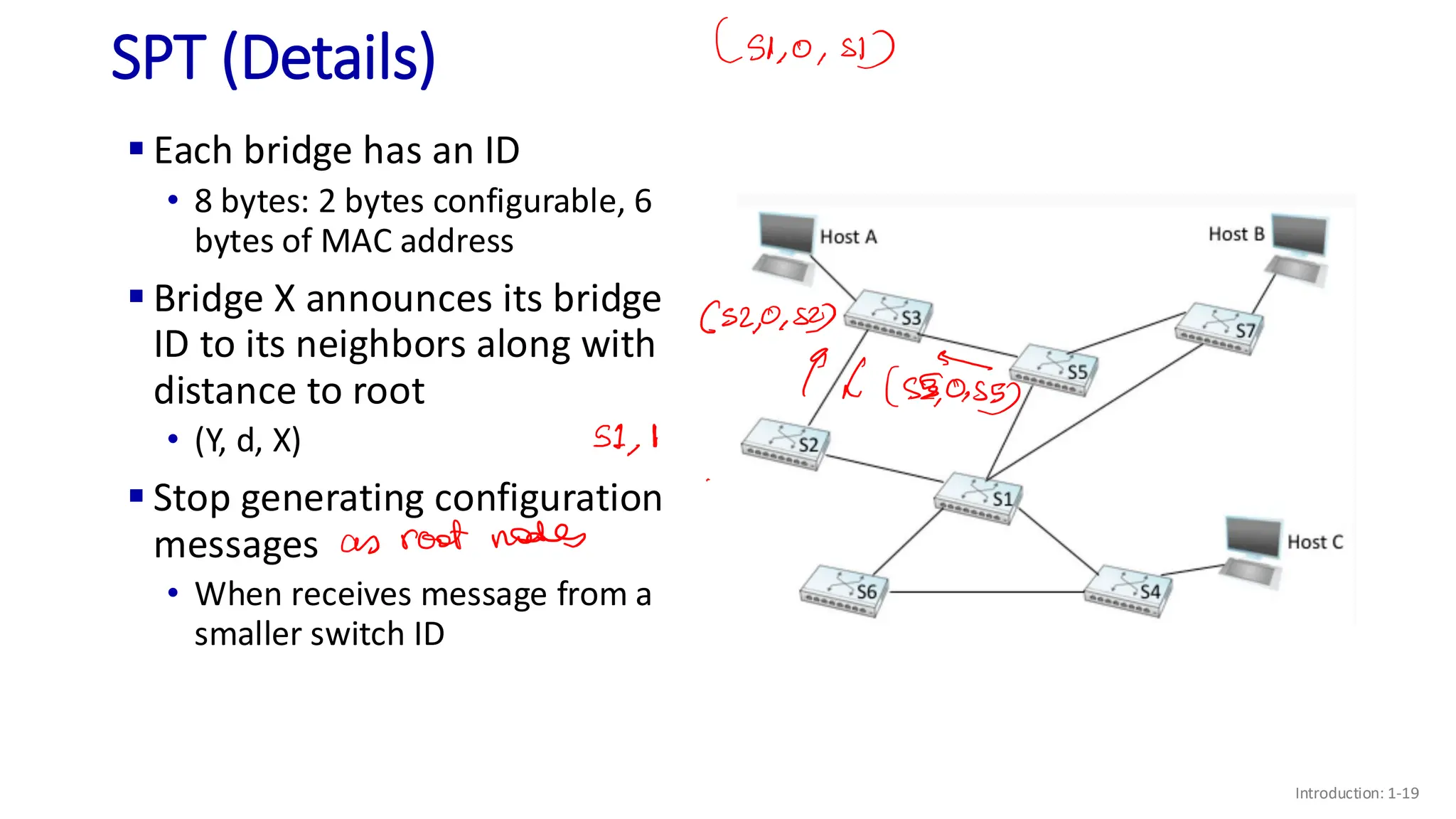
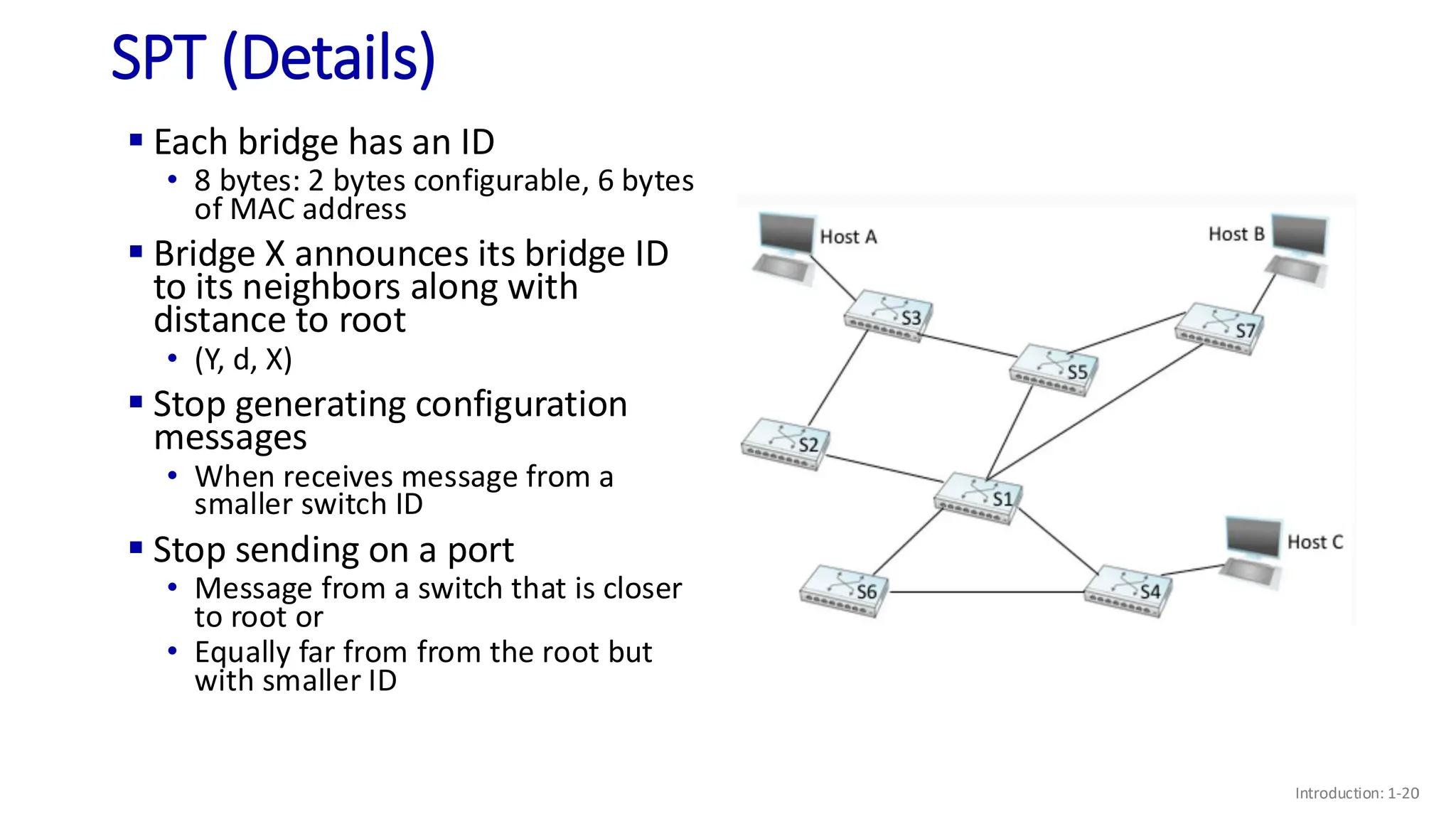
The document discusses the principles of local area networks (LAN) focusing on link-layer services like framing, error detection, and medium access control. It explains the functioning of layer 2 (L2) switches, including their requirements for addressing, port identification, and packet forwarding, while also introducing self-learning switches and the spanning tree protocol for loop prevention. The conclusion emphasizes the significance of various link-layer services and their implications for networking technologies.