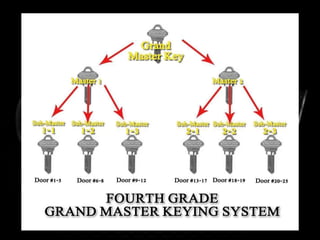
This document discusses different types of locks and keys used for security purposes. It describes common locks like warded locks, disc tumbler locks, pin tumbler locks, lever locks, combination locks, code-operated locks, card-operated locks and padlocks. Keys are metal devices with a blade and bow that open locks. There are different types of keys like change keys, submaster keys, master keys and grandmaster keys. The document also discusses key control methods to ensure only authorized people can access keys and locks.