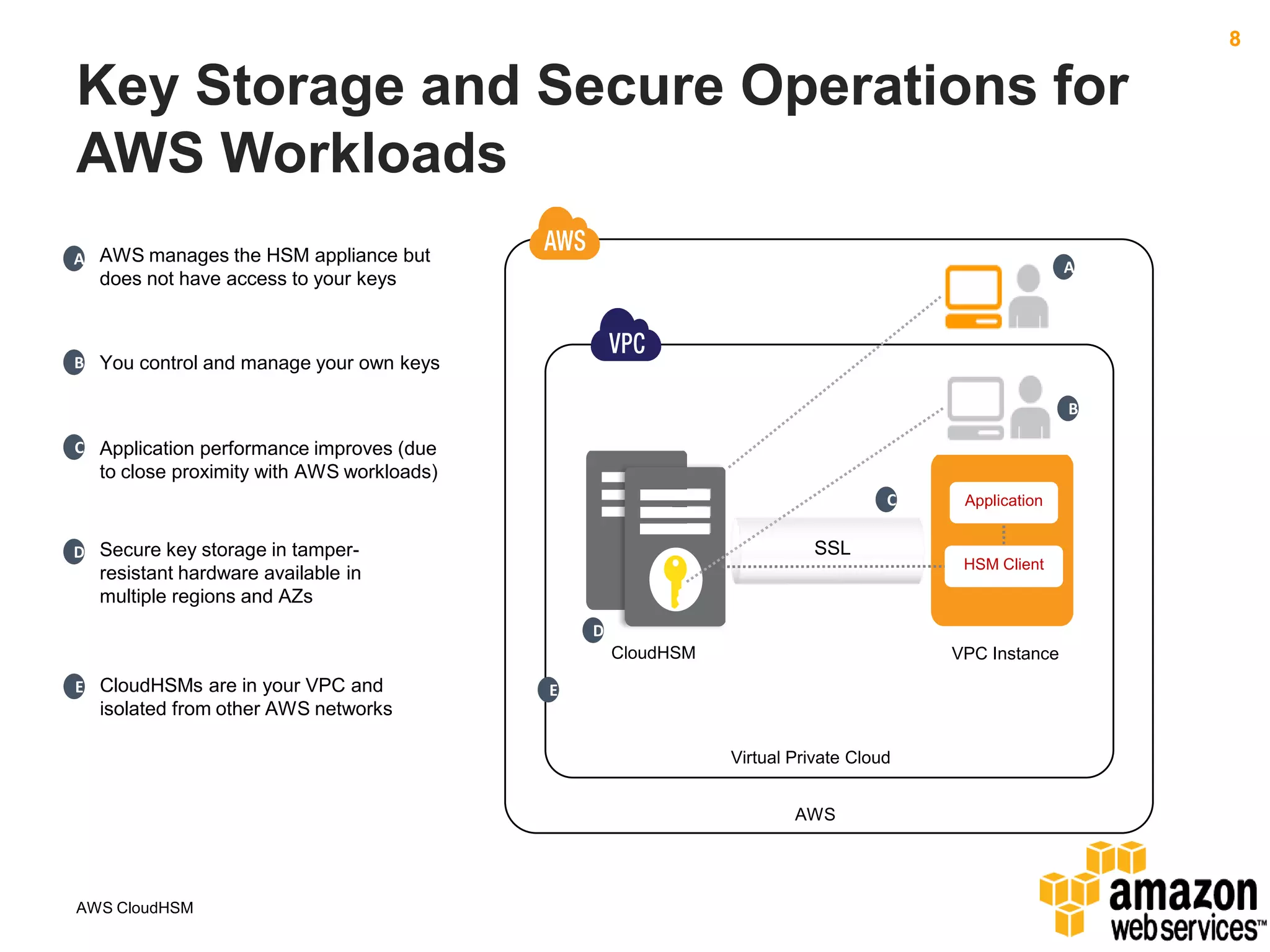
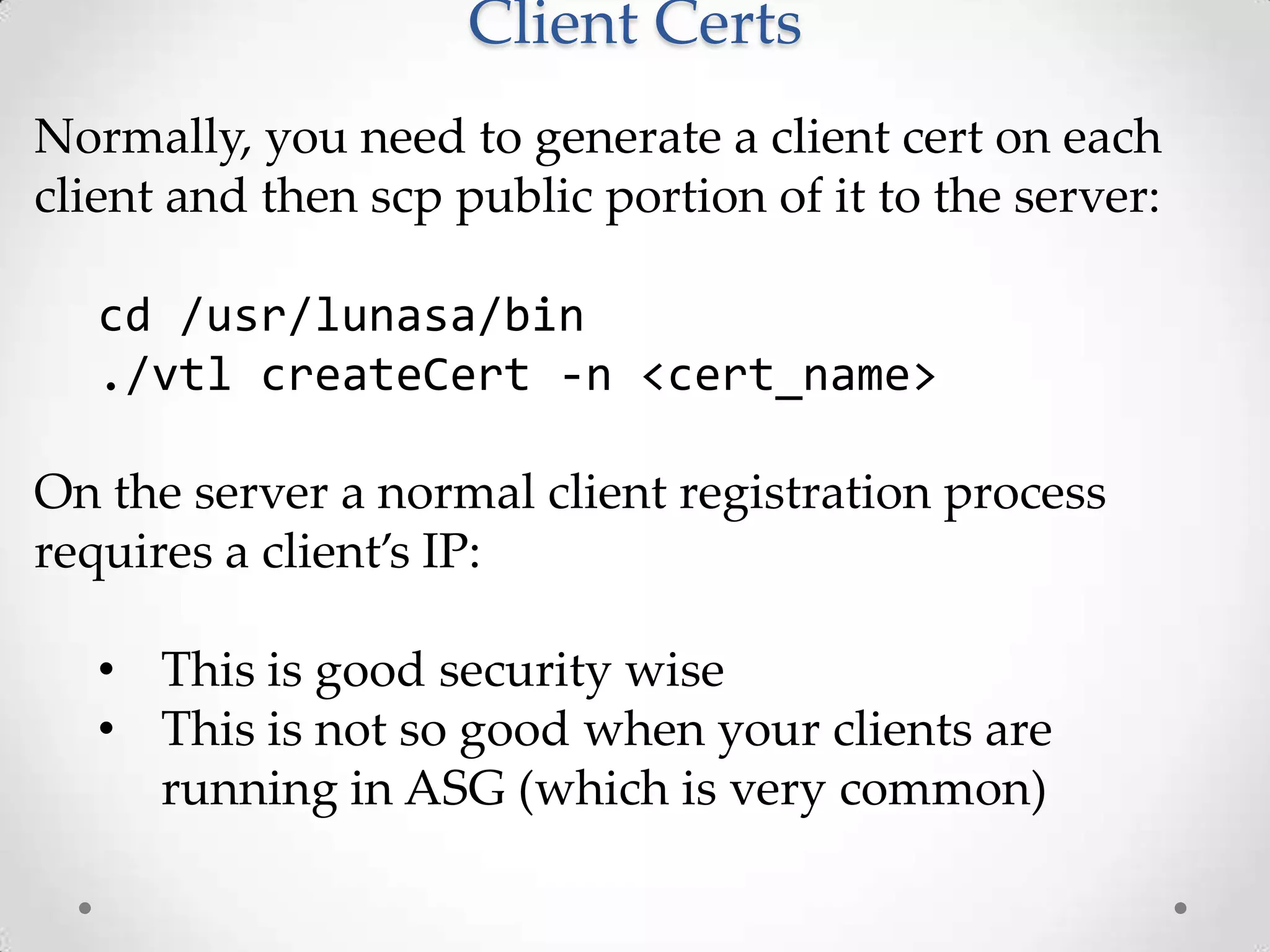
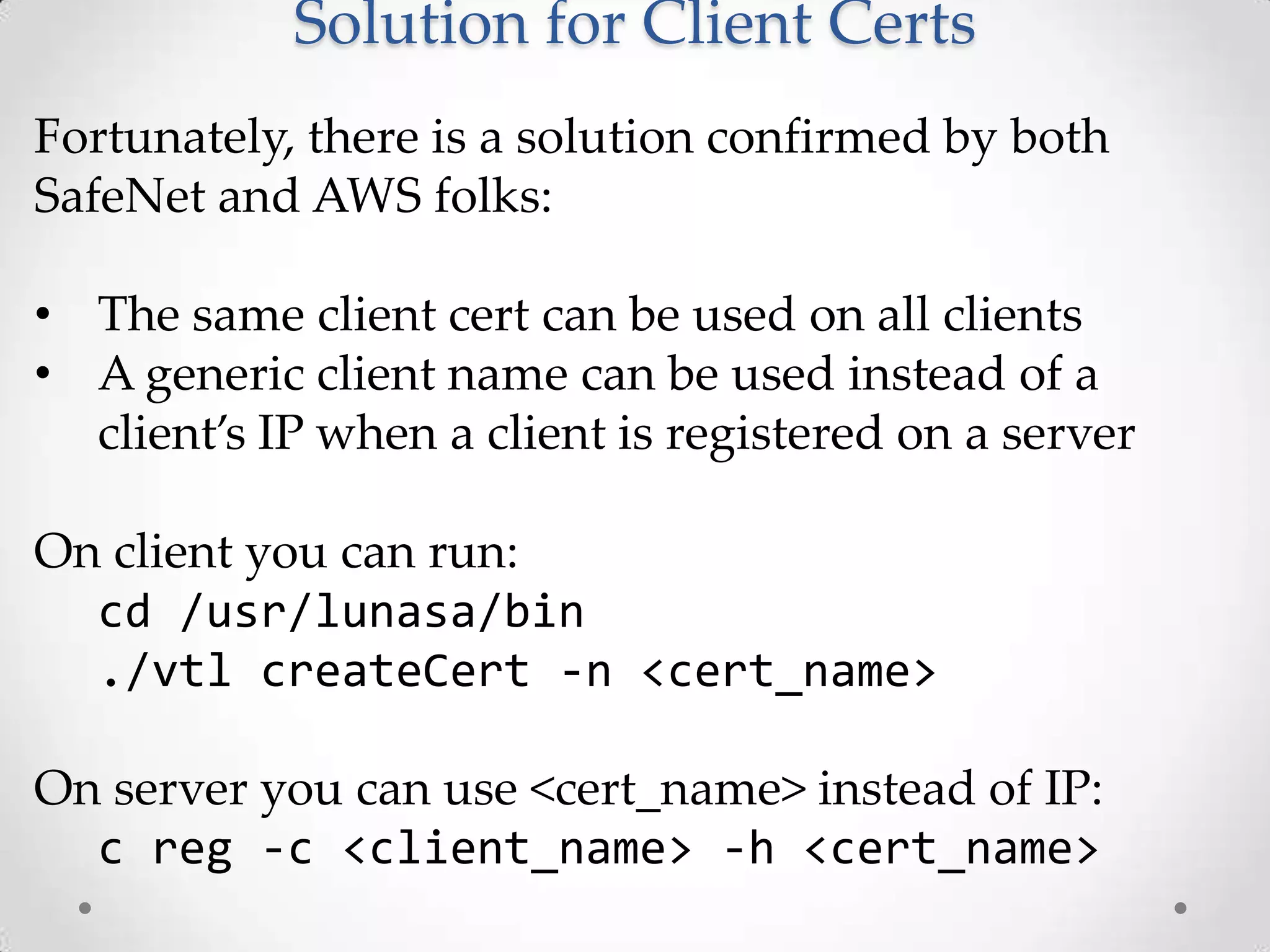
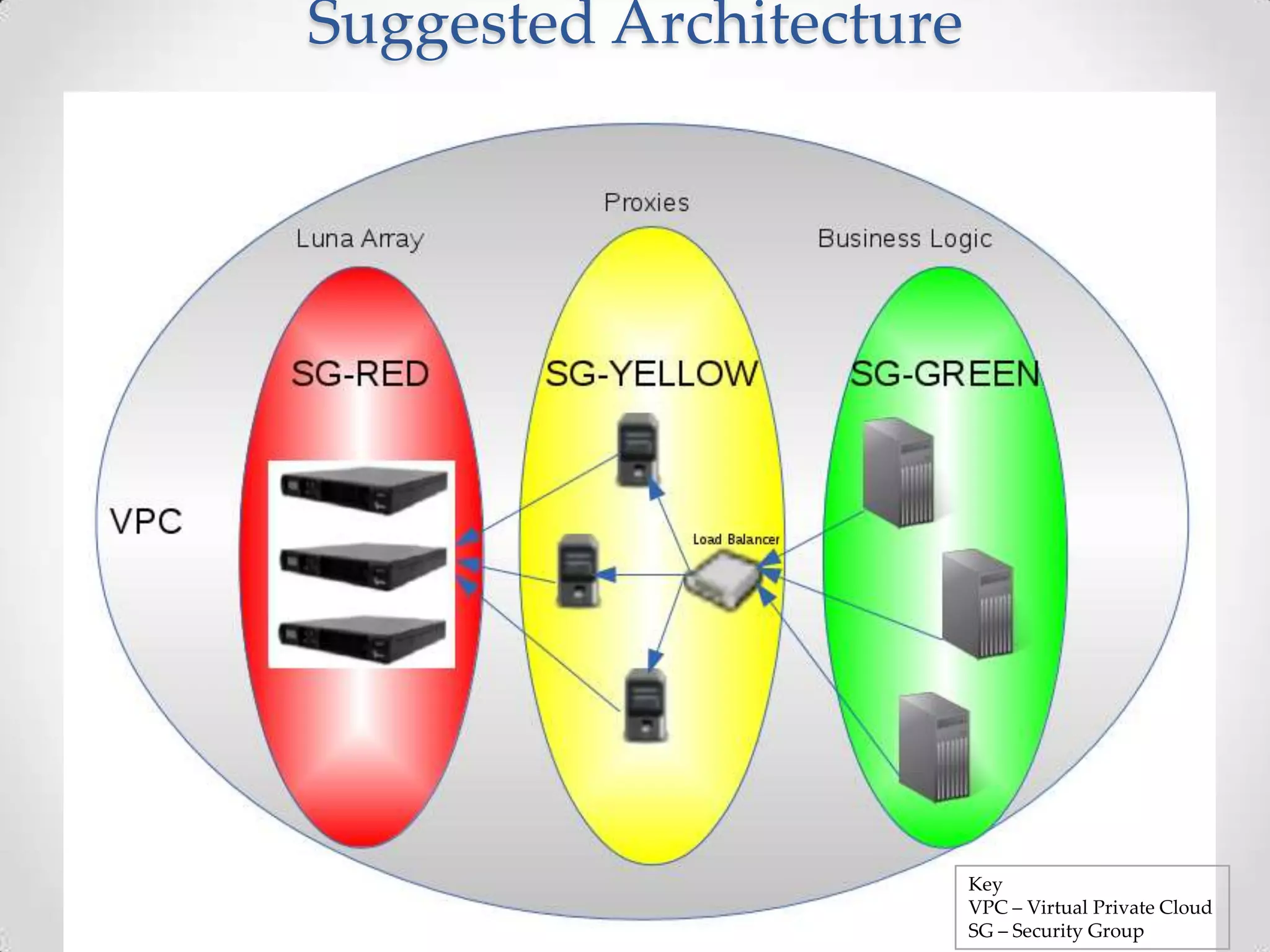
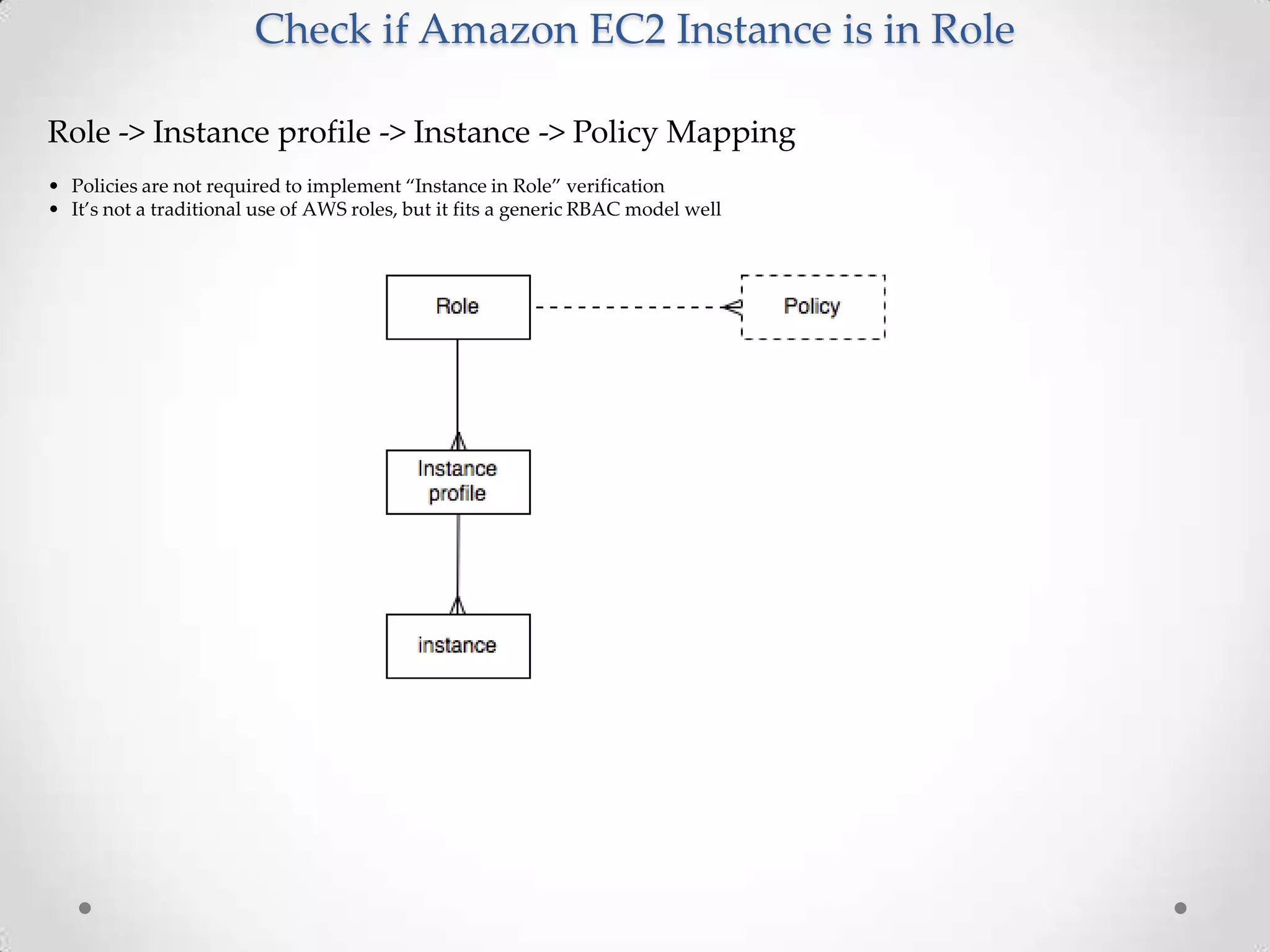
AWS CloudHSM allows customers to leverage dedicated Hardware Security Modules (HSMs) located within AWS data centers. This provides strong protection of encryption keys through physical and logical access controls. While AWS manages the HSM appliances, customers control and manage their own keys. Application performance can also improve through the close proximity of HSMs to workloads running in AWS. Customers have full control over key generation, storage, and use through APIs that integrate with their existing applications.















![Automation: JSON Layout
{
"name":"ha_group",
"vtl_path":"/usr/lunasa/bin/vtl”,
"lunas":[ {
"host":"xx.xx.xx.xx",
"internal_ip":"xx.xx.xx.xx",
"name":"keyman",
"mgr_user":"manager",
"mgr_pwd":"<?pwd>",
"old_admin_pwd":"<?pwd>",
"admin_pwd":"<?pwd>",
"key_files":["/home/ec2-user/.ssh/id_rsa"],
"cmd_timeout":20,
"cloning_domain":"keyman_clone",
"vtl_path":"/usr/lunasa/bin/vtl",
"client_cert_path":"/usr/lunasa/cert/client",
"server_cert_path":"/usr/lunasa/cert/server",
"server_cert_name":"server.pem",
"input_prompt_end":"> ",
"finish_prompt_end":"lunash:>",
"confirm_word":"proceed",
"ssh_user":"ec2-user",
"ssh_group":"ec2-user",
"ssh_bits":2048,
"ssh_type":"rsa",
"partitions":* …](https://image.slidesharecdn.com/lascon-oleg-todd-v3-131025165030-phpapp01/75/LASCON-2013-AWS-CLoud-HSM-25-2048.jpg)