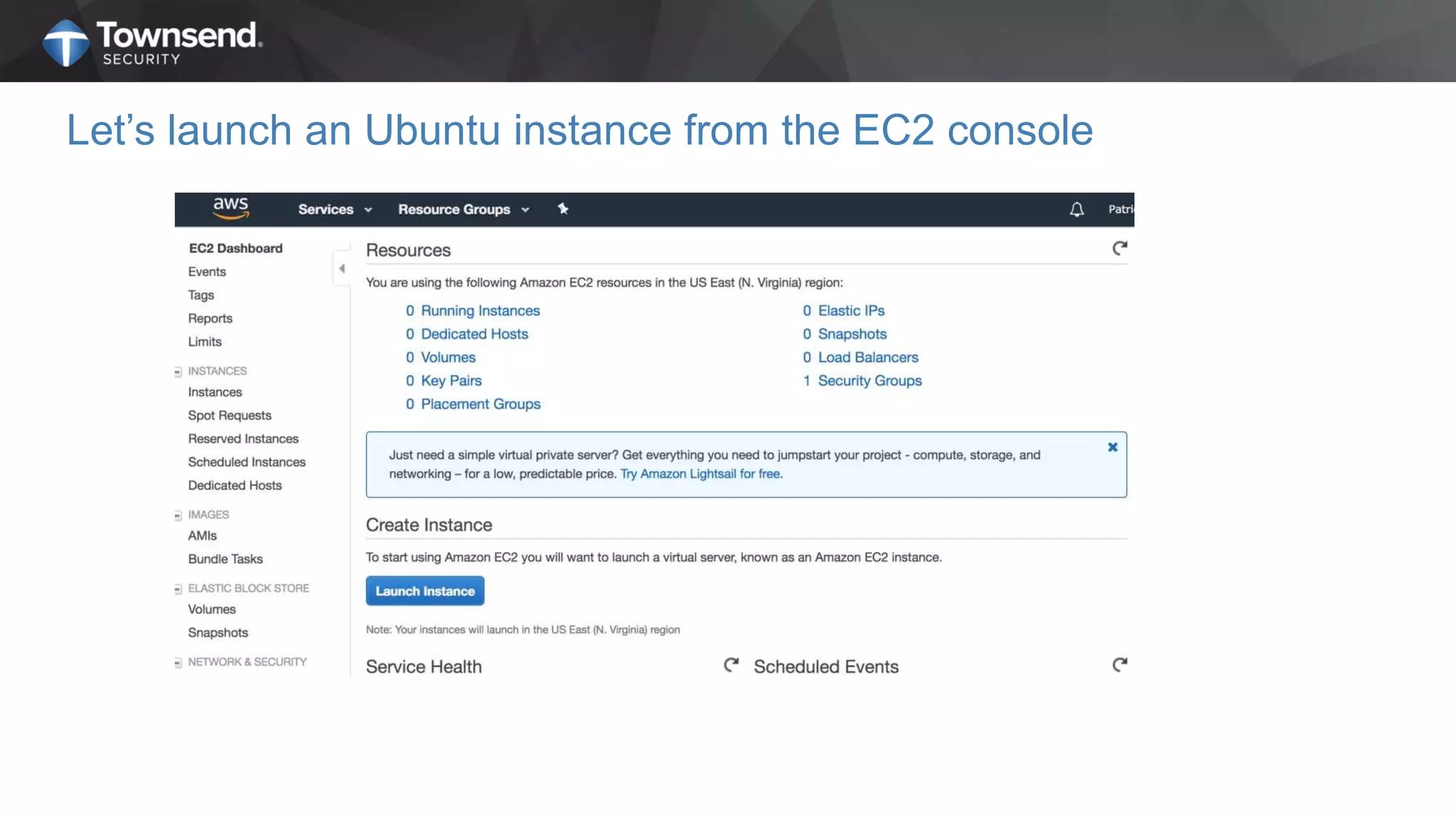
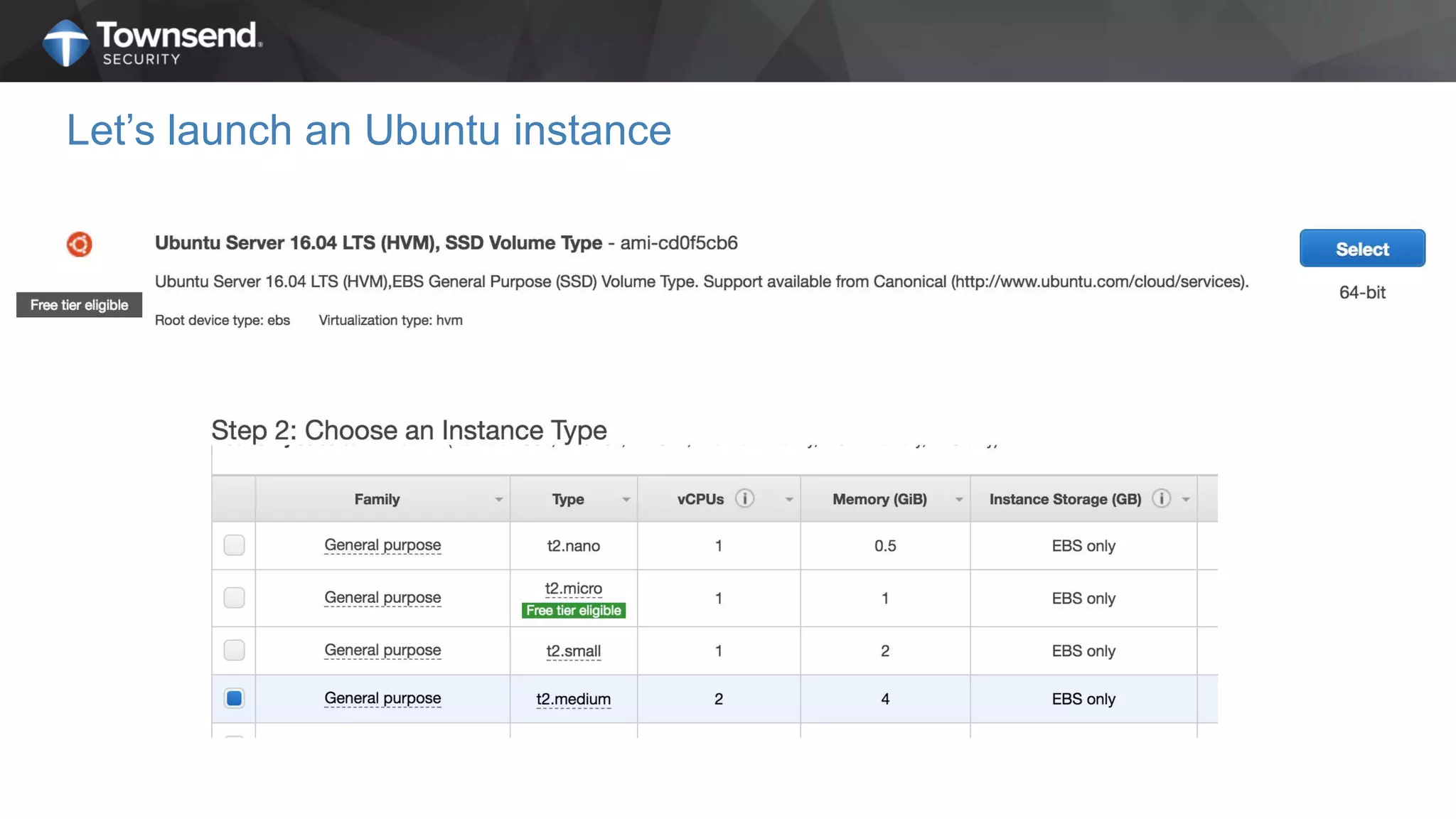
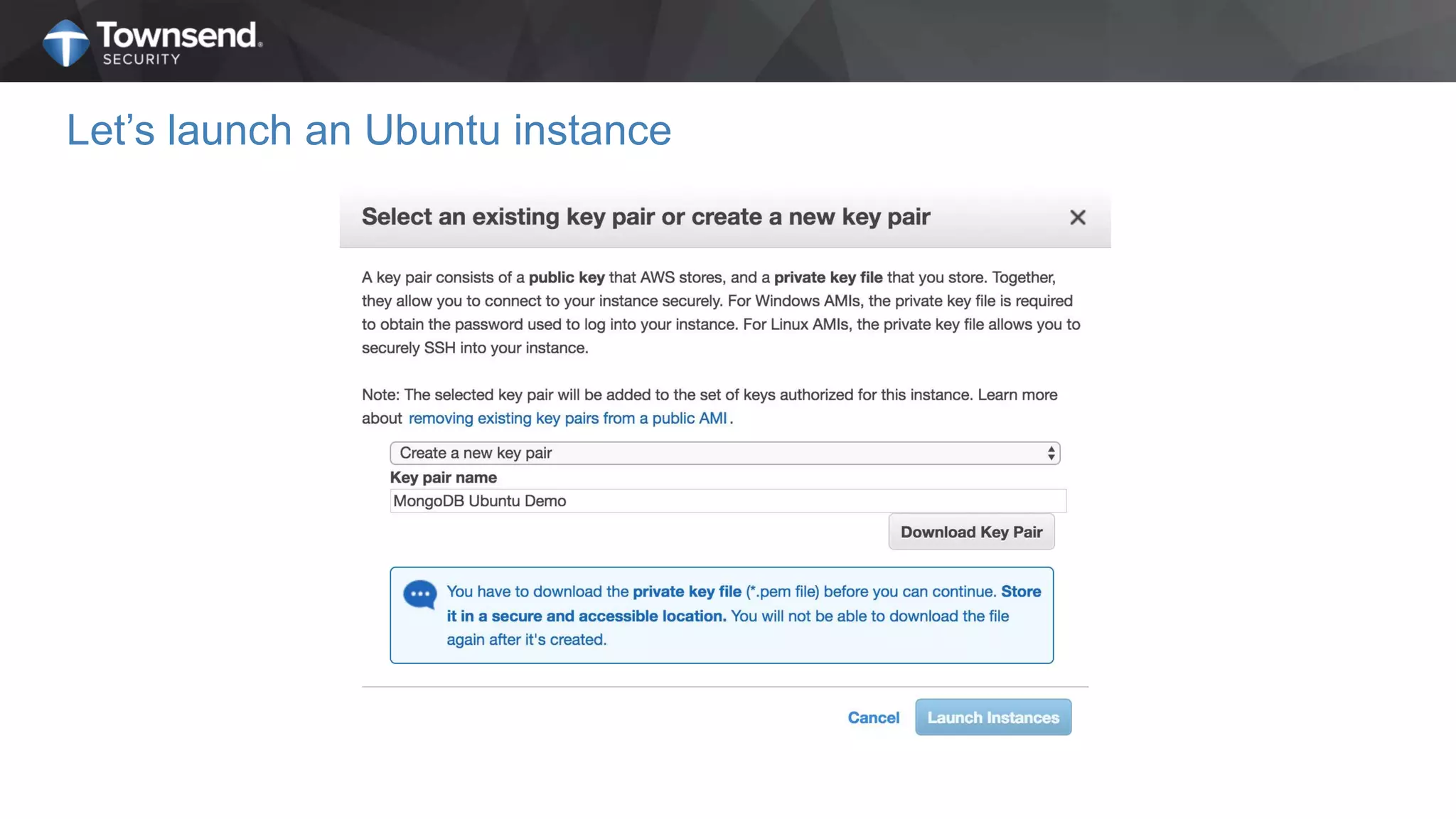
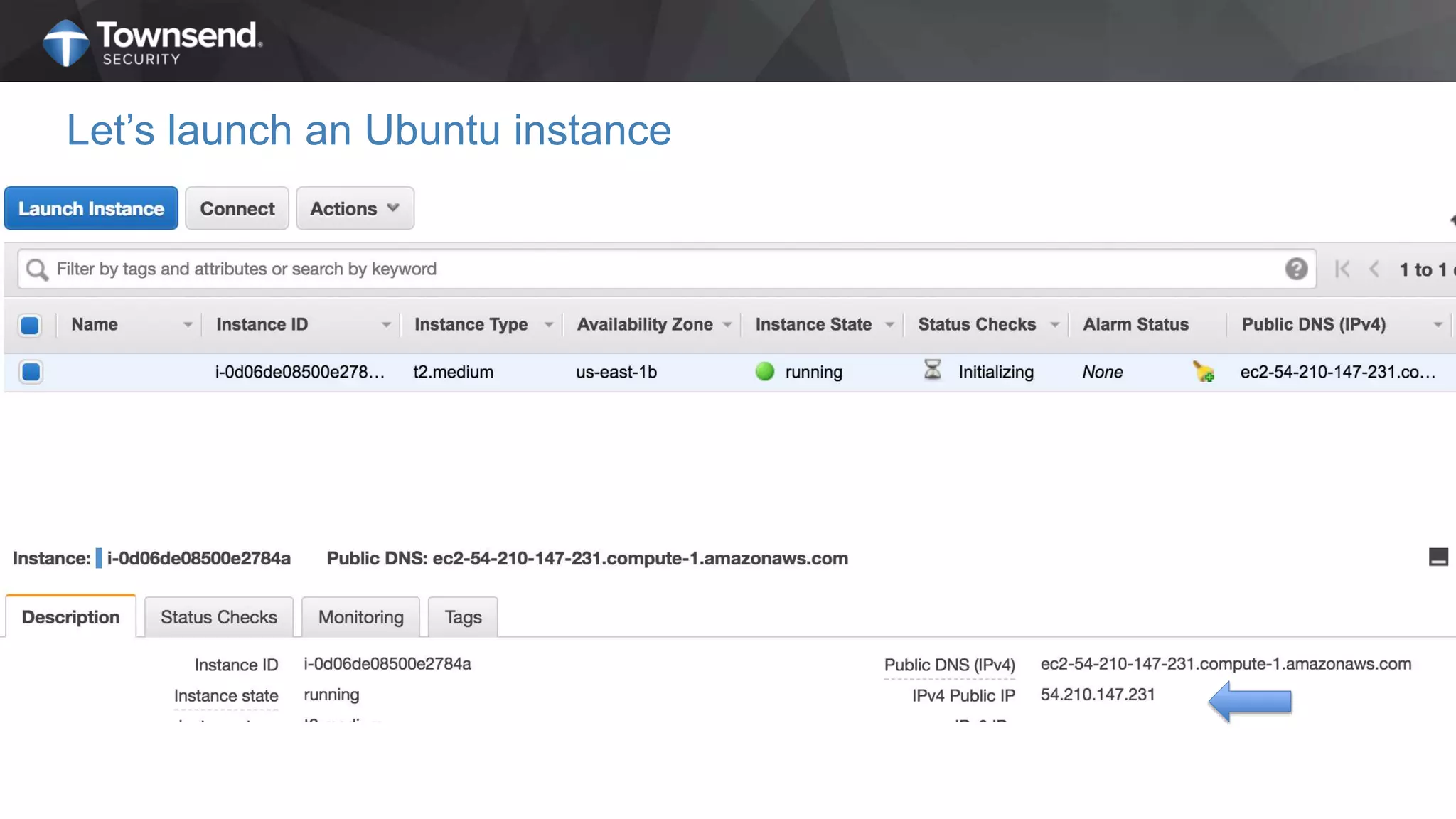
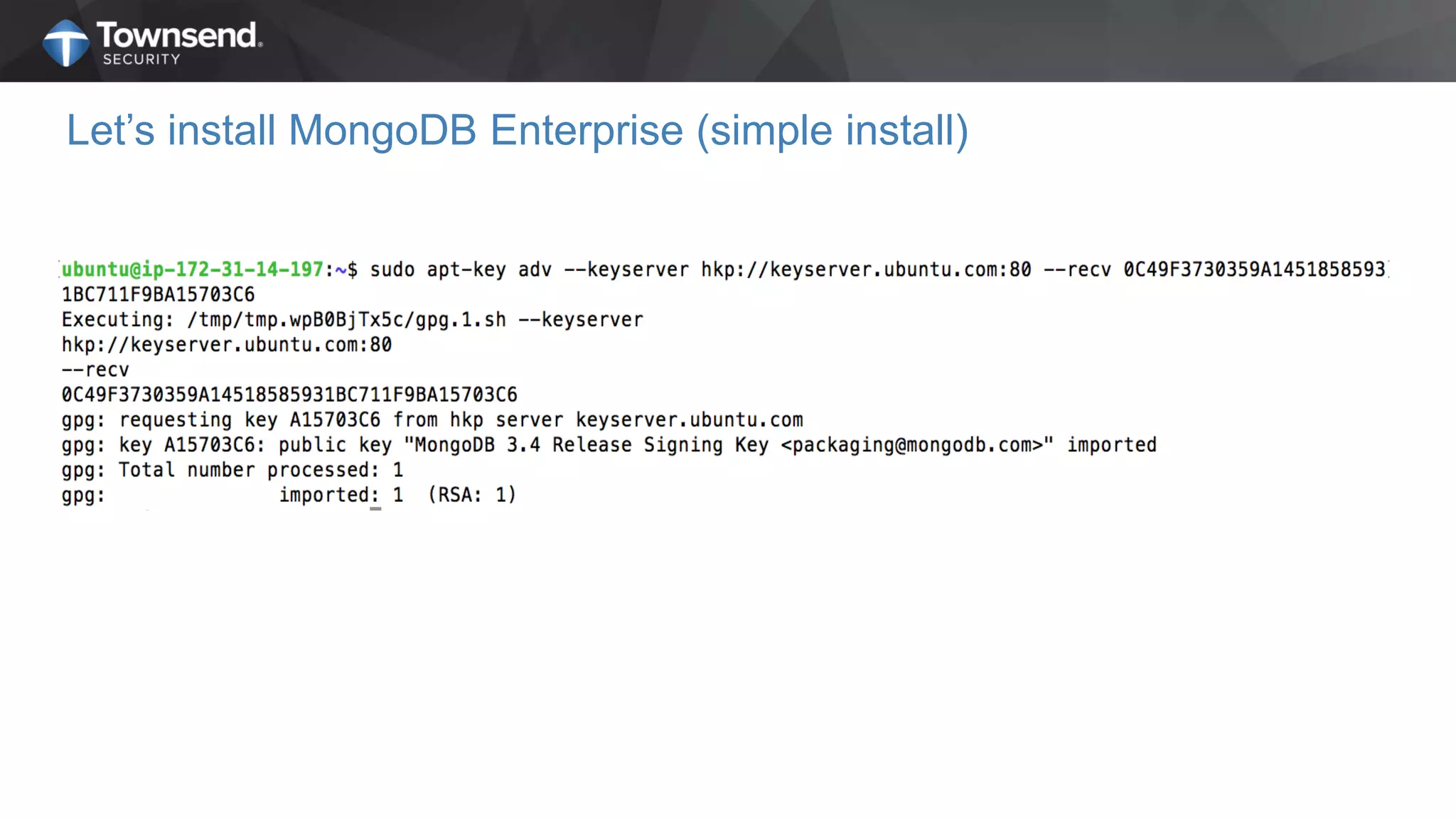
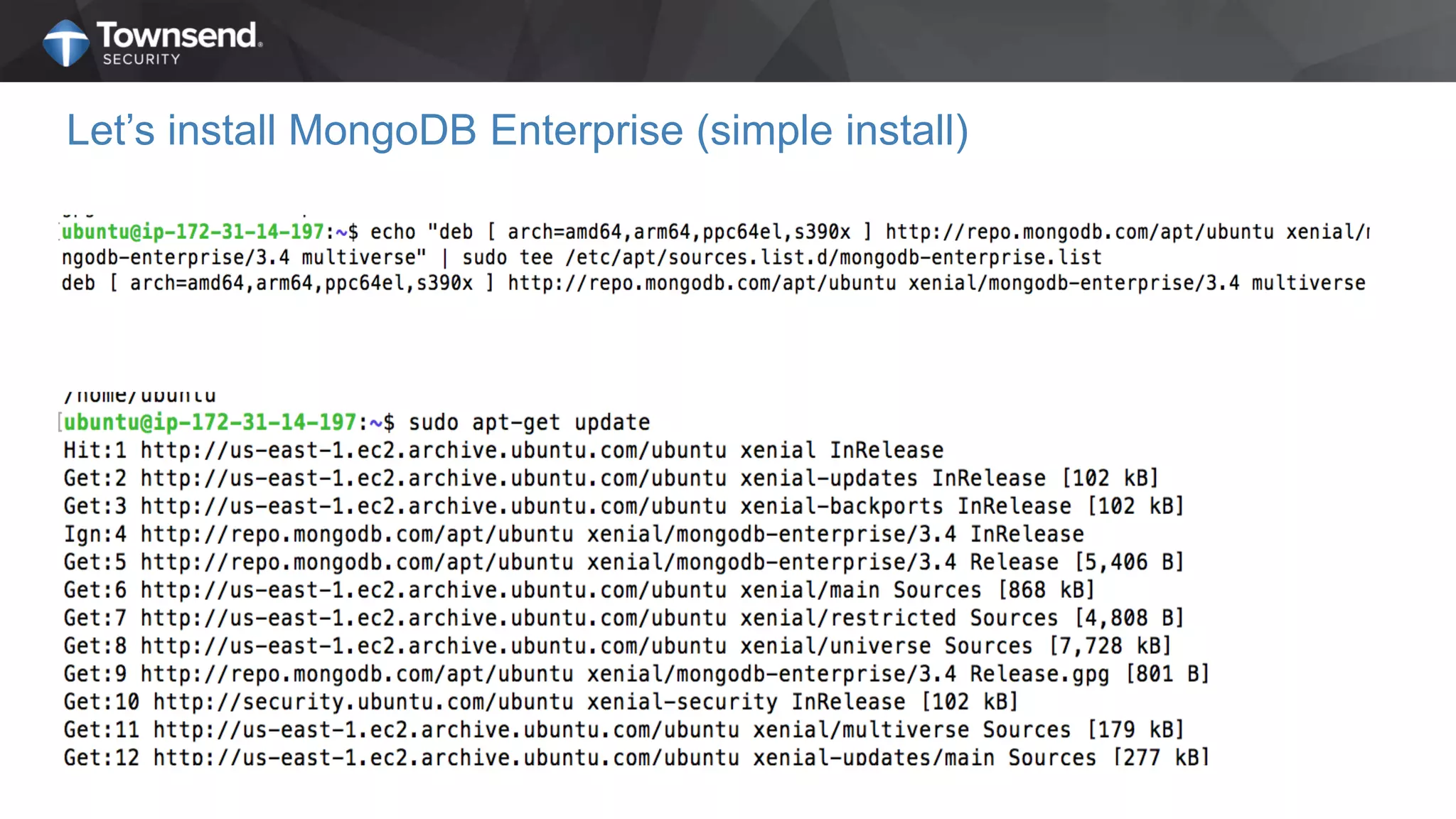
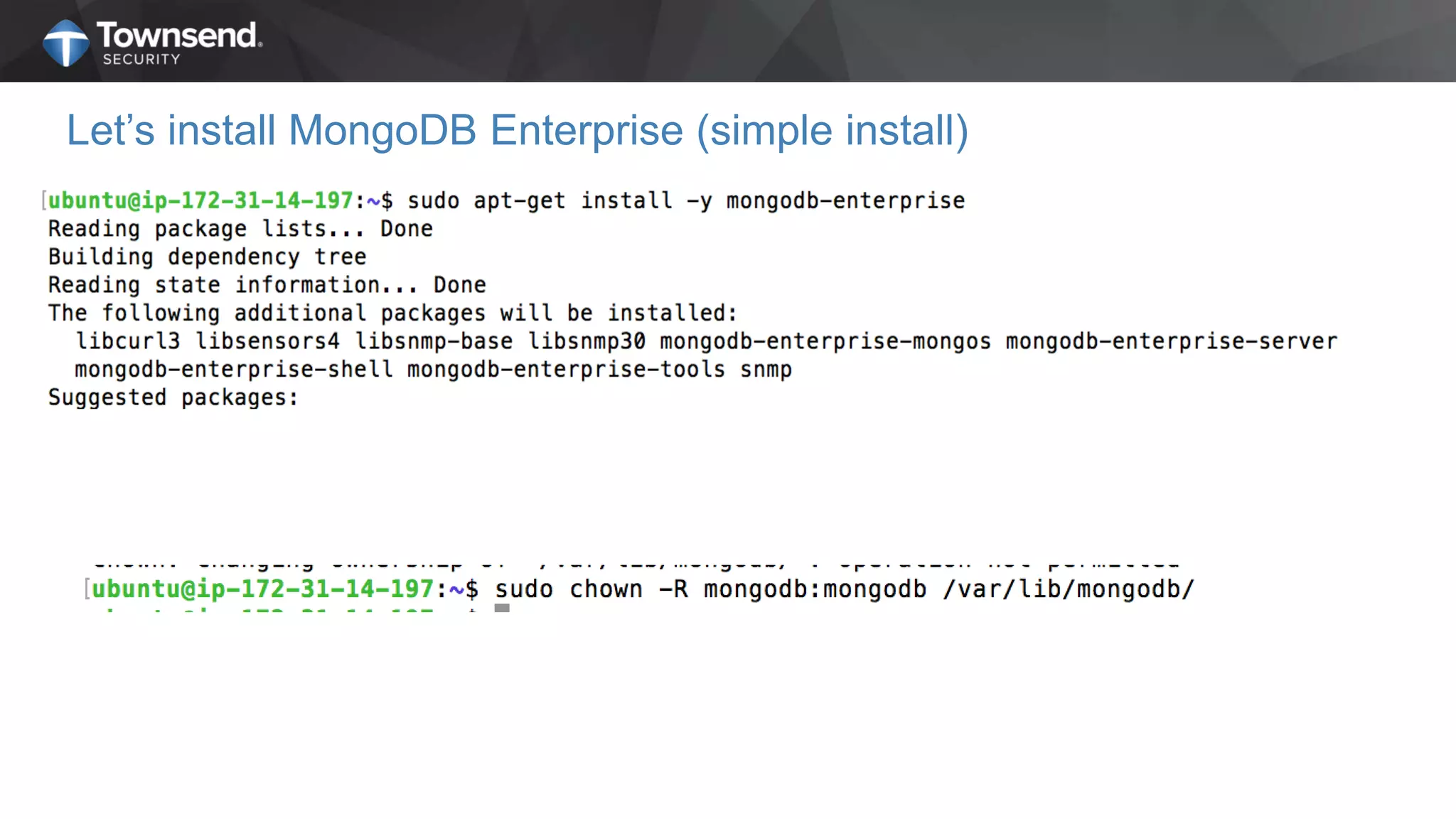
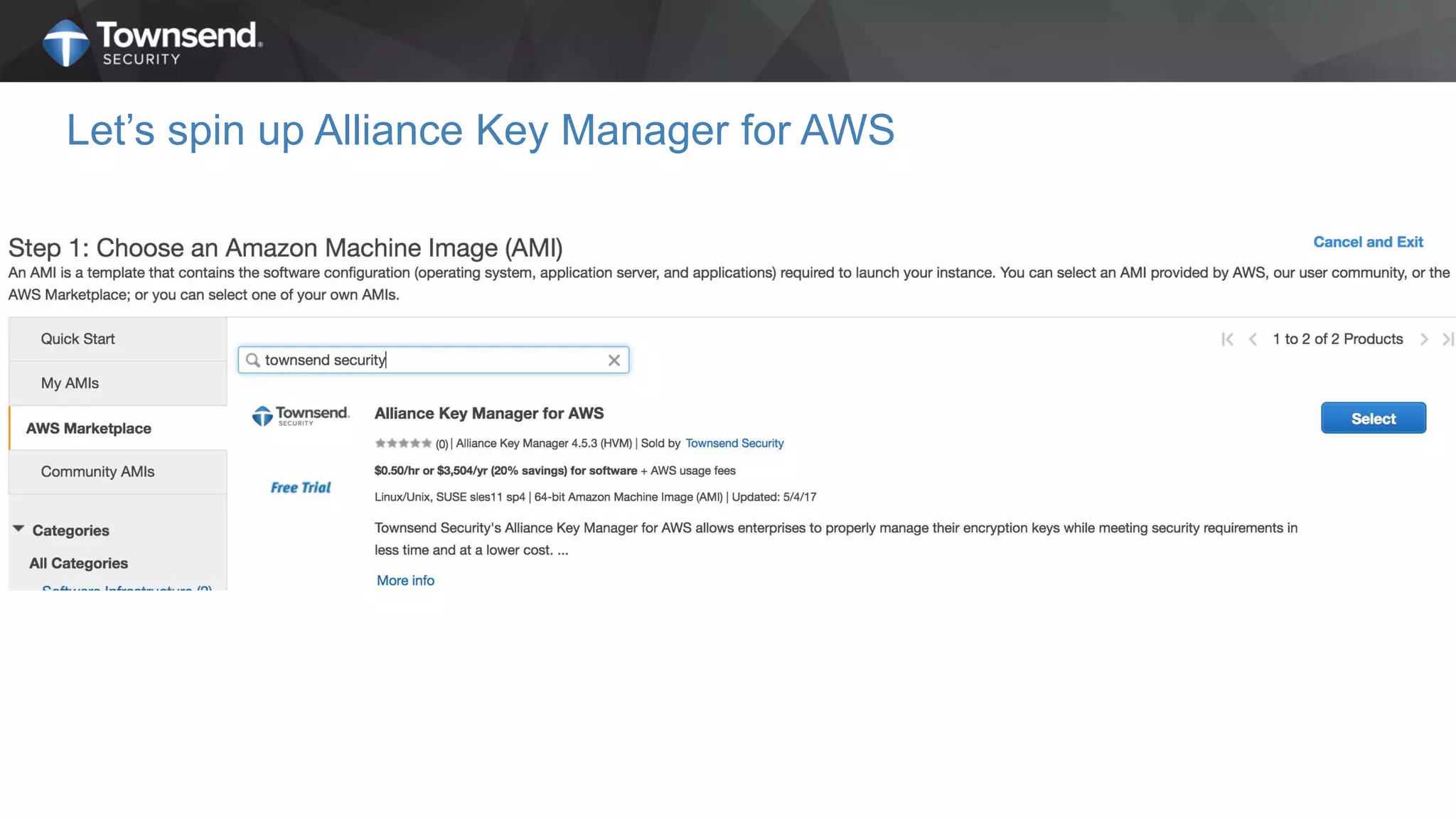
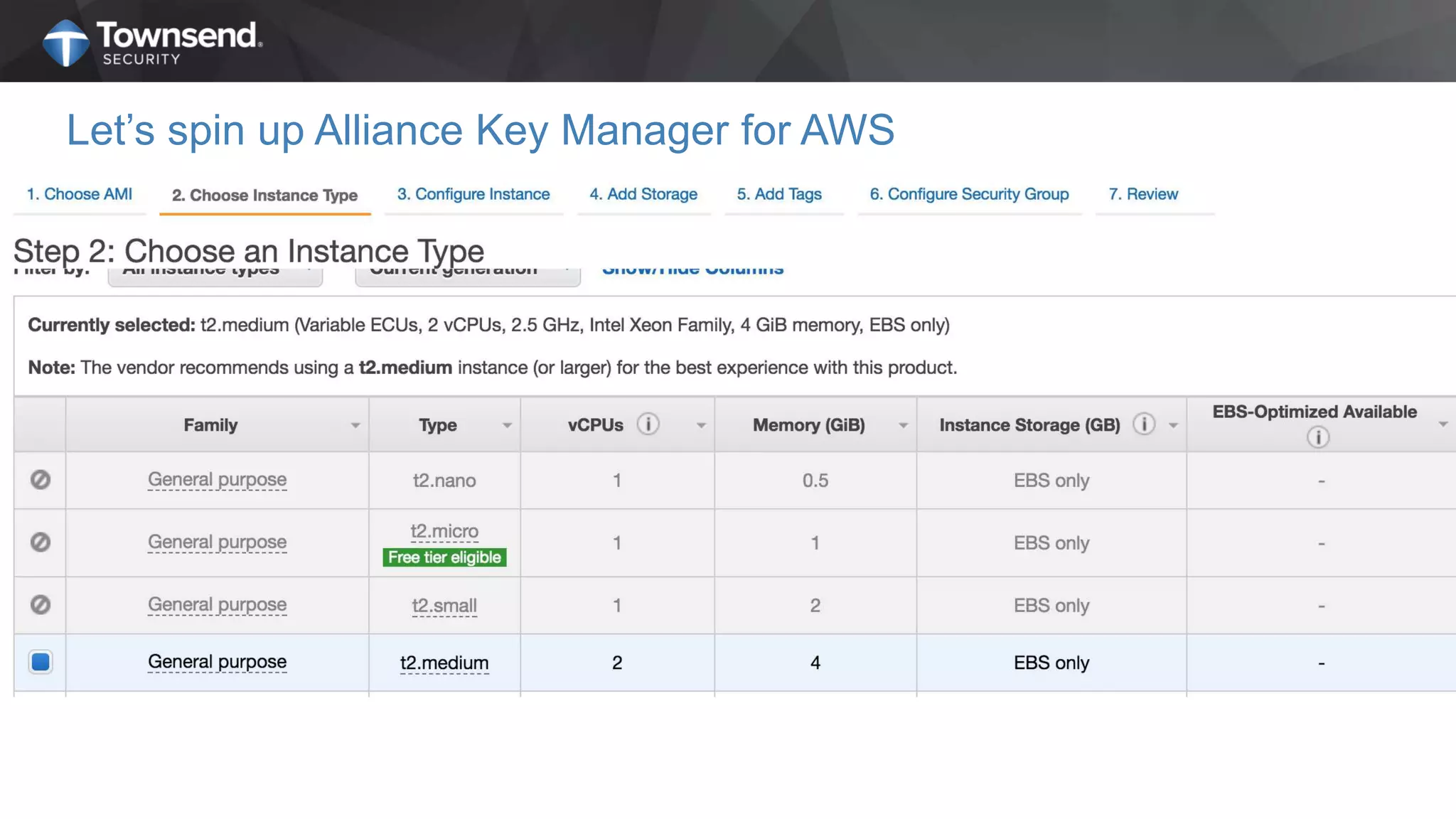
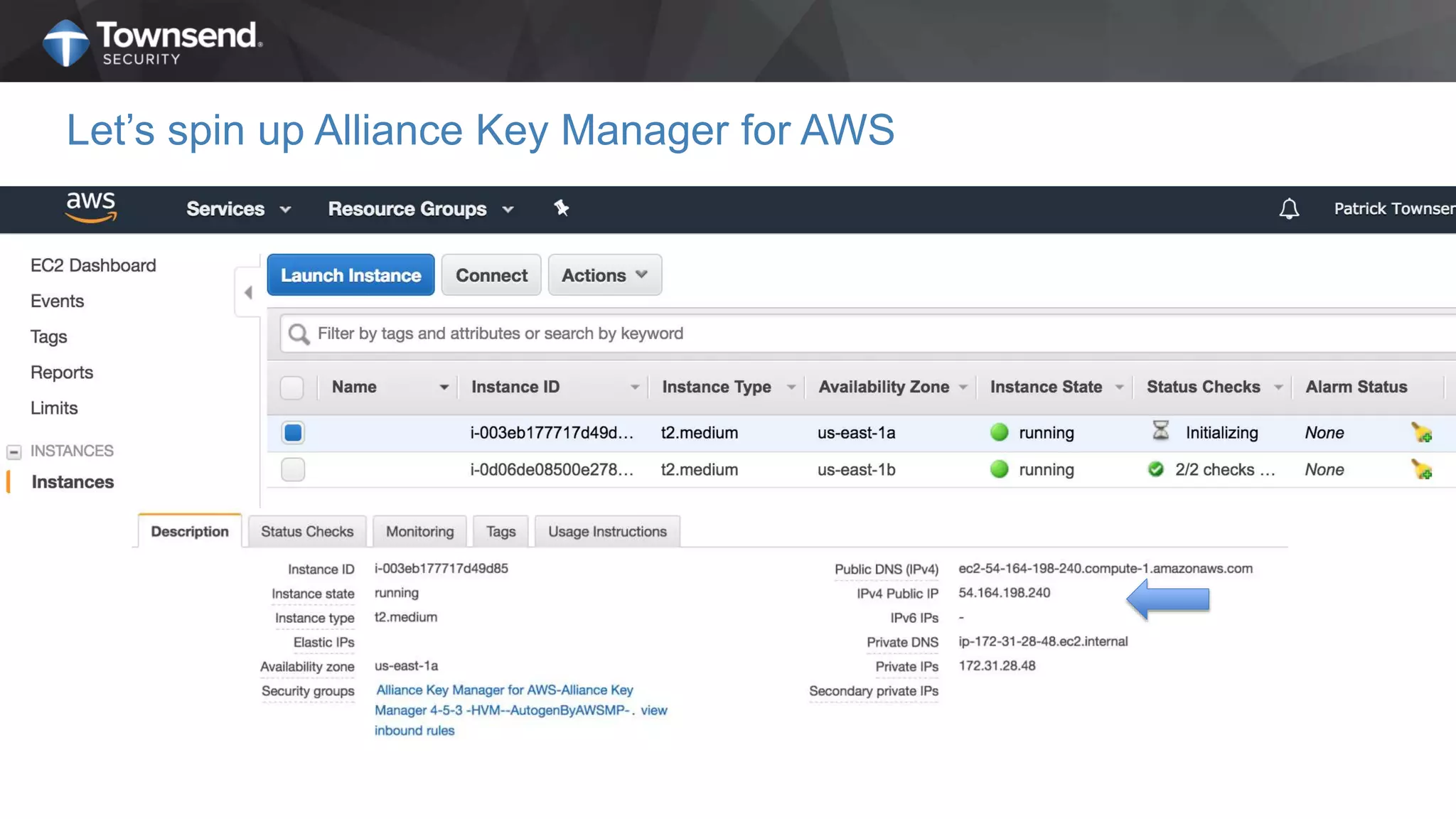
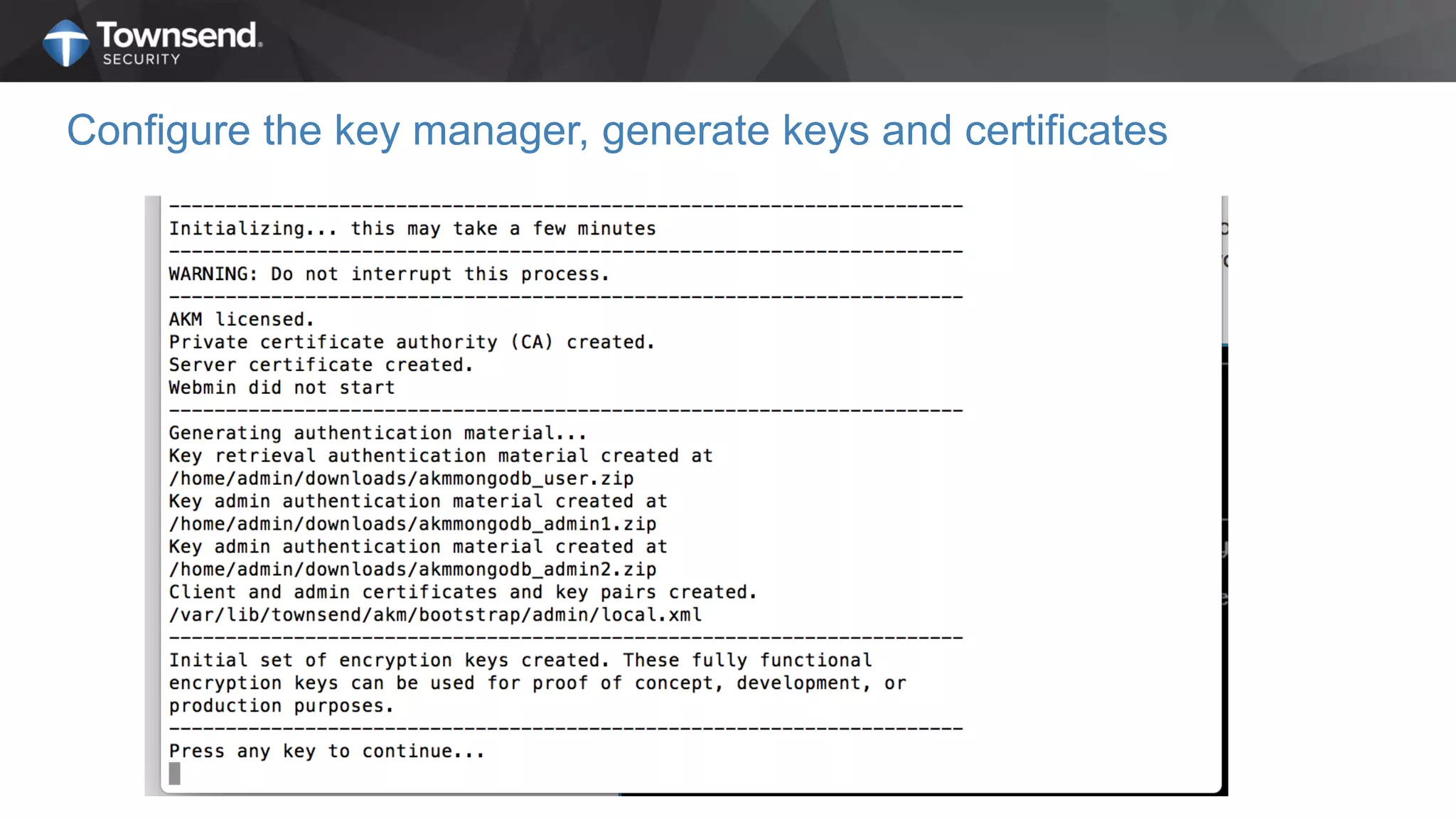
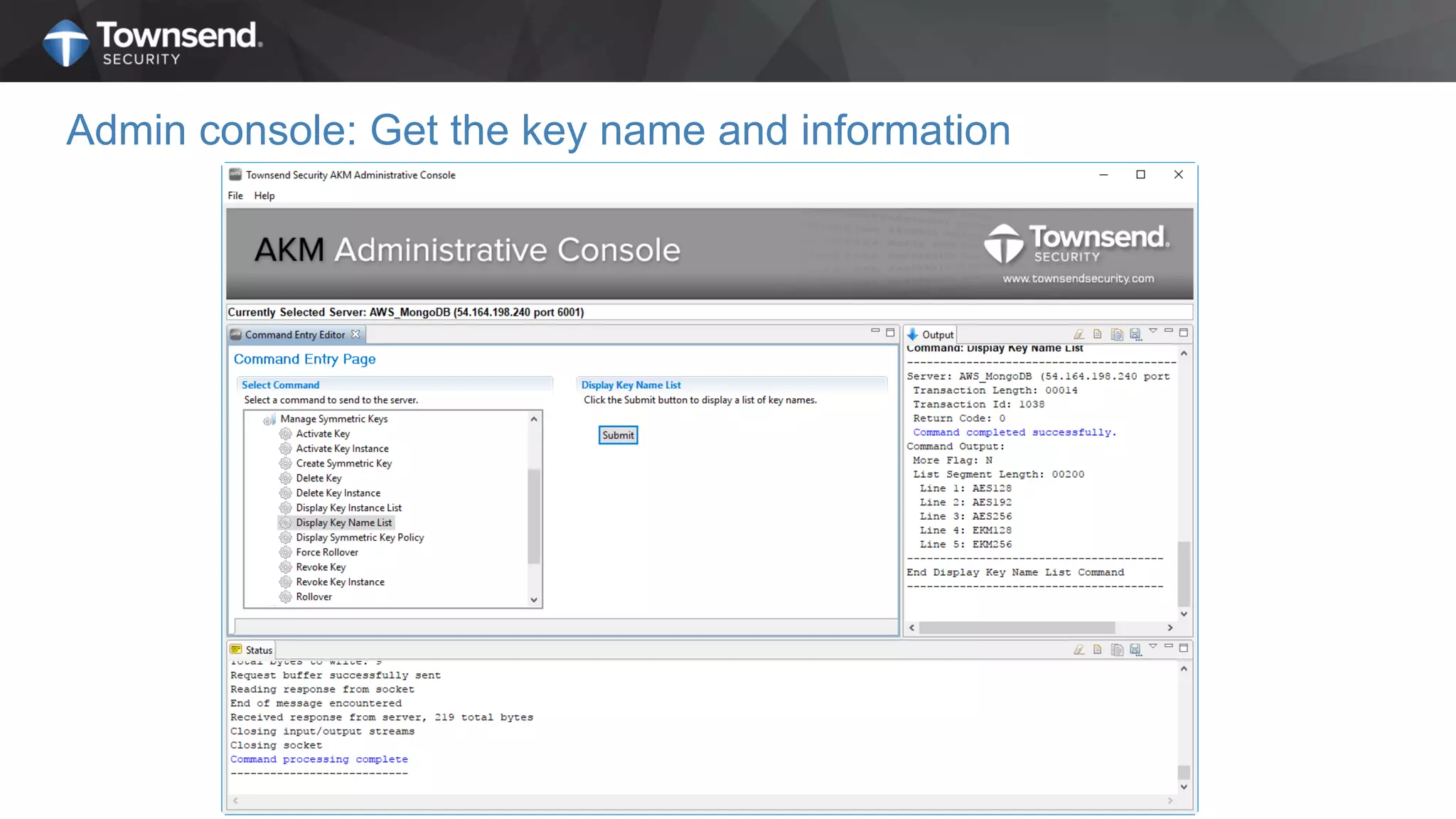
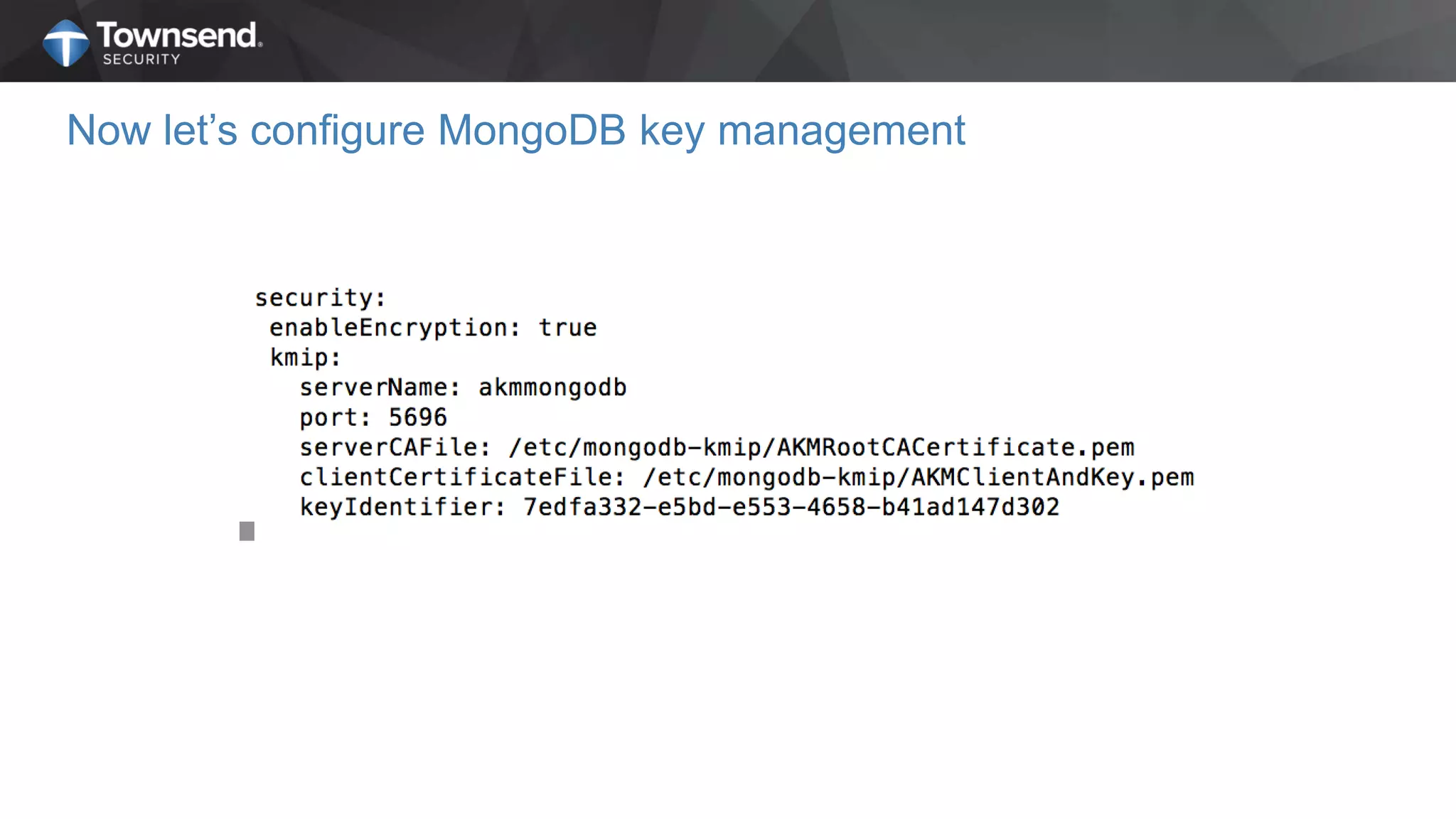
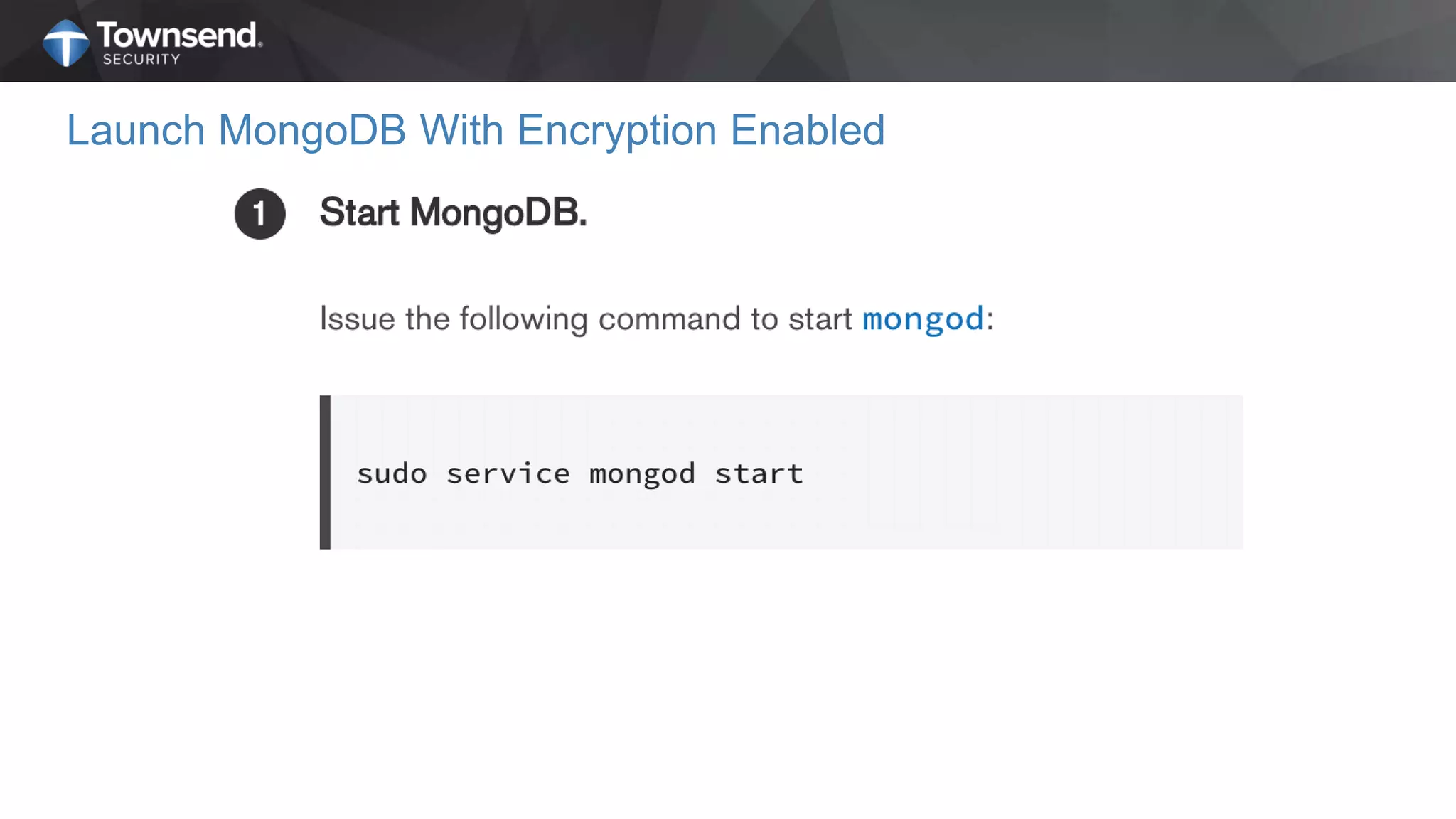
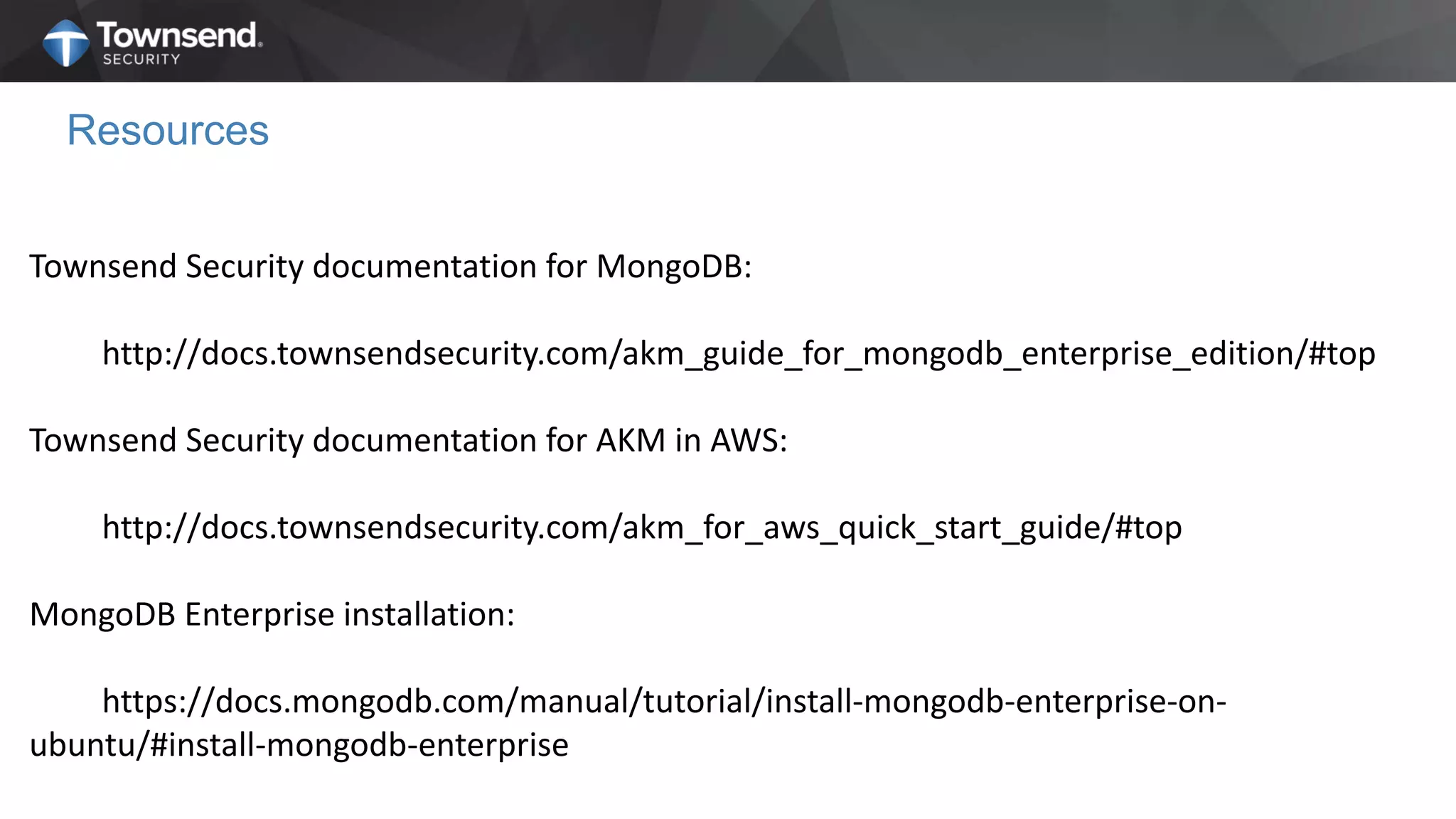
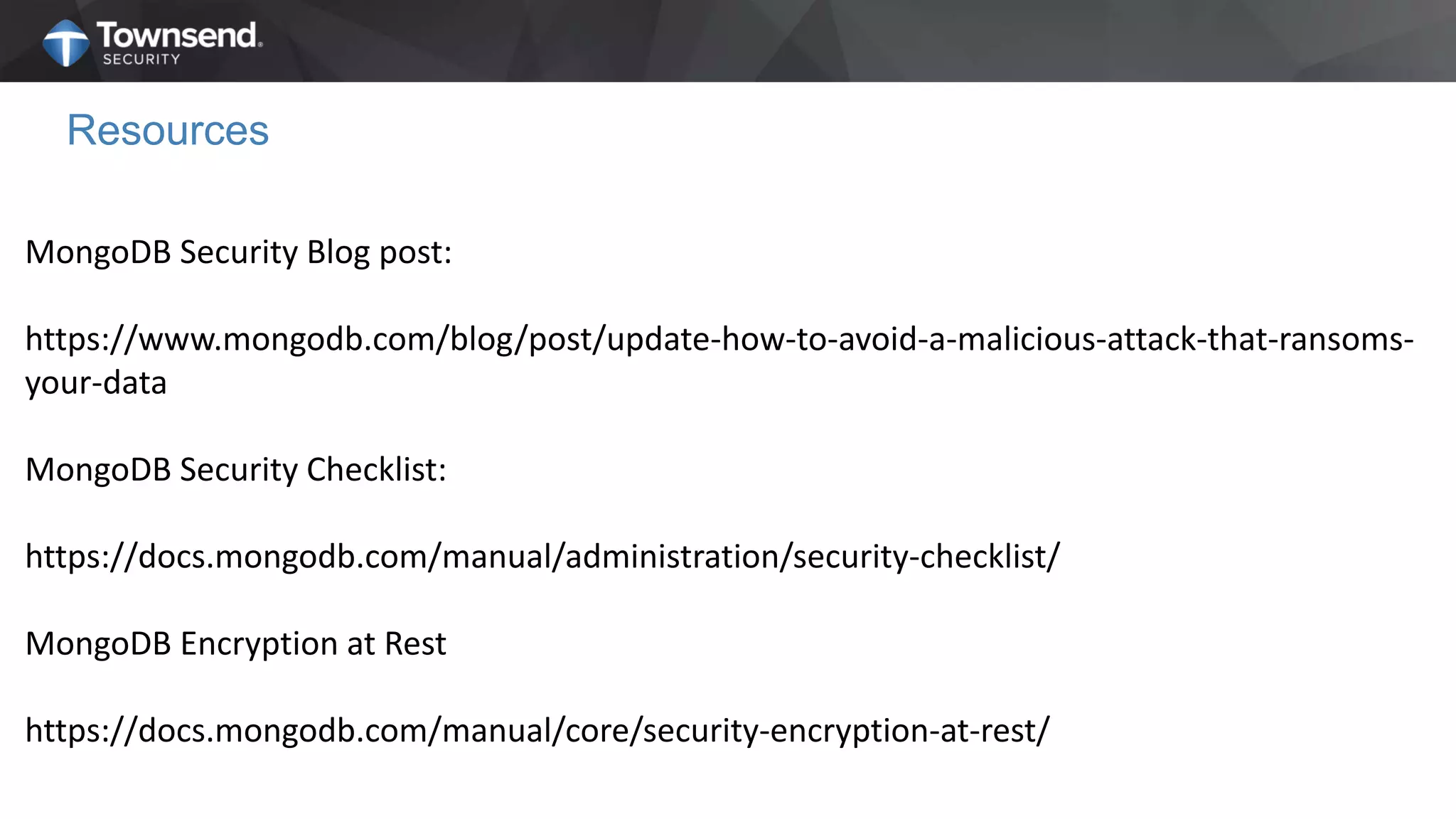
The document presents a session on simplified encryption and key management for MongoDB, led by Patrick Townsend, a data security expert. It highlights the importance of key management, compliance requirements, best practices, and strategies for managing encryption in cloud environments, particularly focusing on MongoDB deployments. Additionally, it provides resources for further reading and guidance on implementing these practices effectively.