Embed presentation
Download as PDF, PPTX



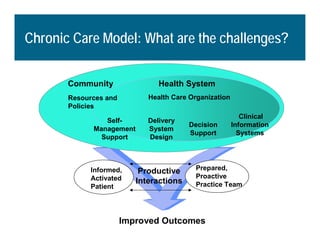




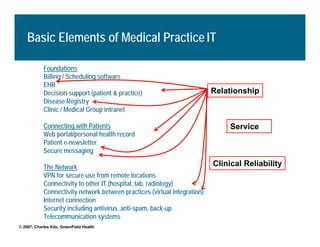
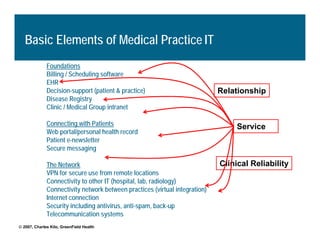
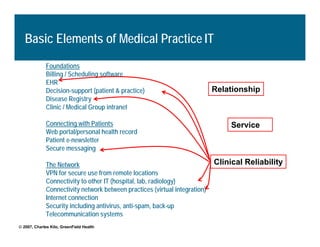
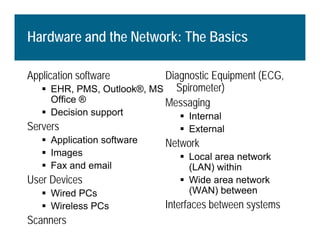




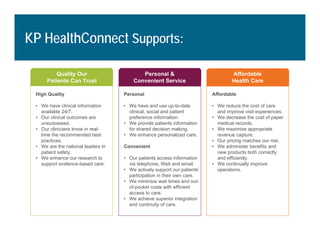
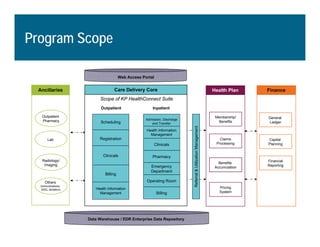
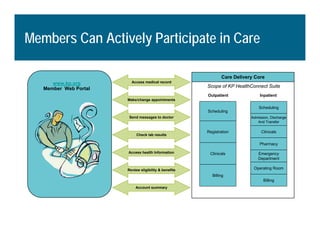
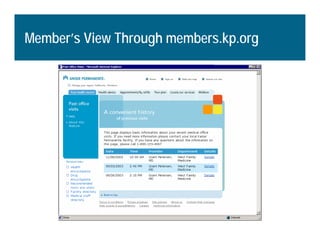
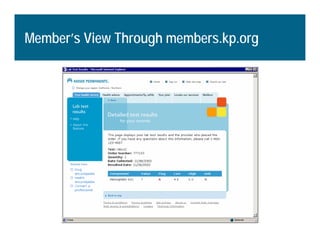

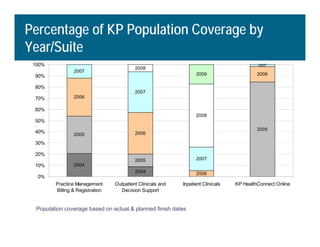



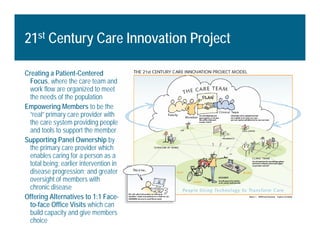

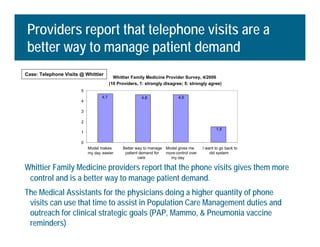


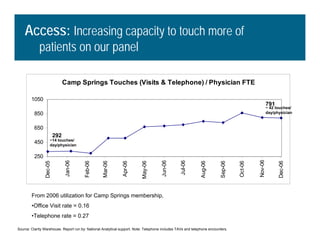
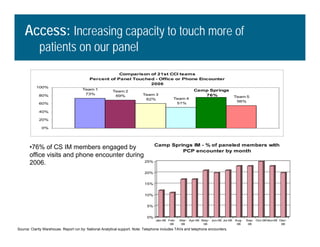
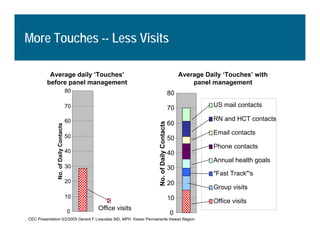






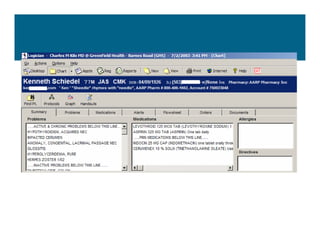
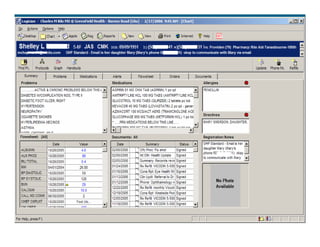
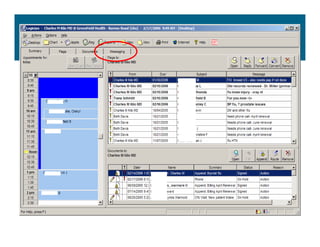
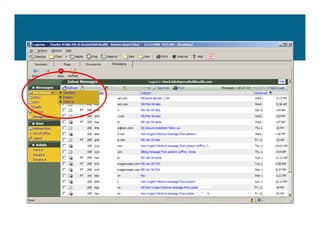
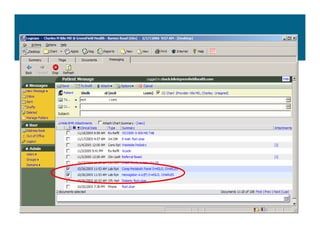
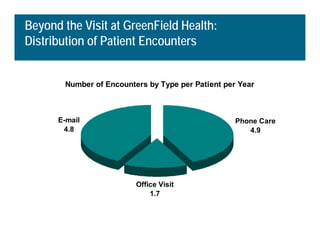




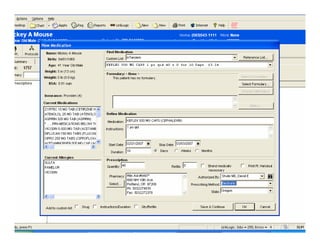
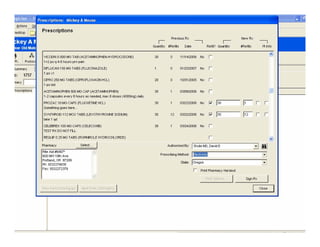
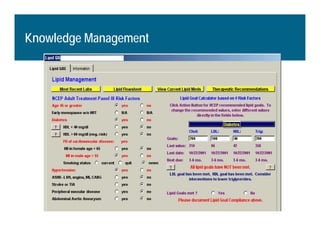
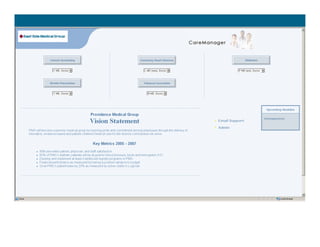
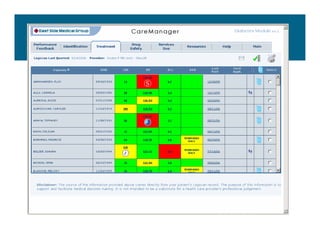
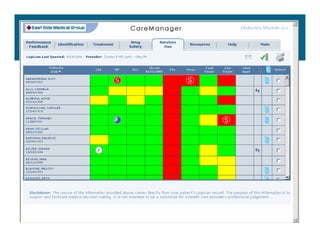
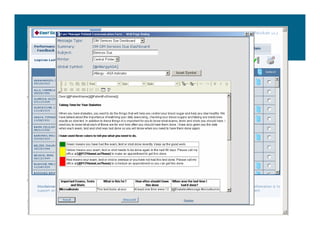
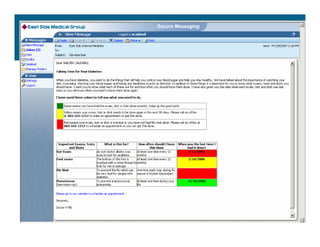


[1] KP HealthConnect is an integrated electronic medical record and business system that aims to improve quality, service, and affordability. [2] It includes elements such as a patient portal, secure messaging, and connectivity between clinics, hospitals, and other providers. [3] Early results show increases in online access for members, reductions in office visits and calls, and high member satisfaction with virtual care options such as telephone visits.































































