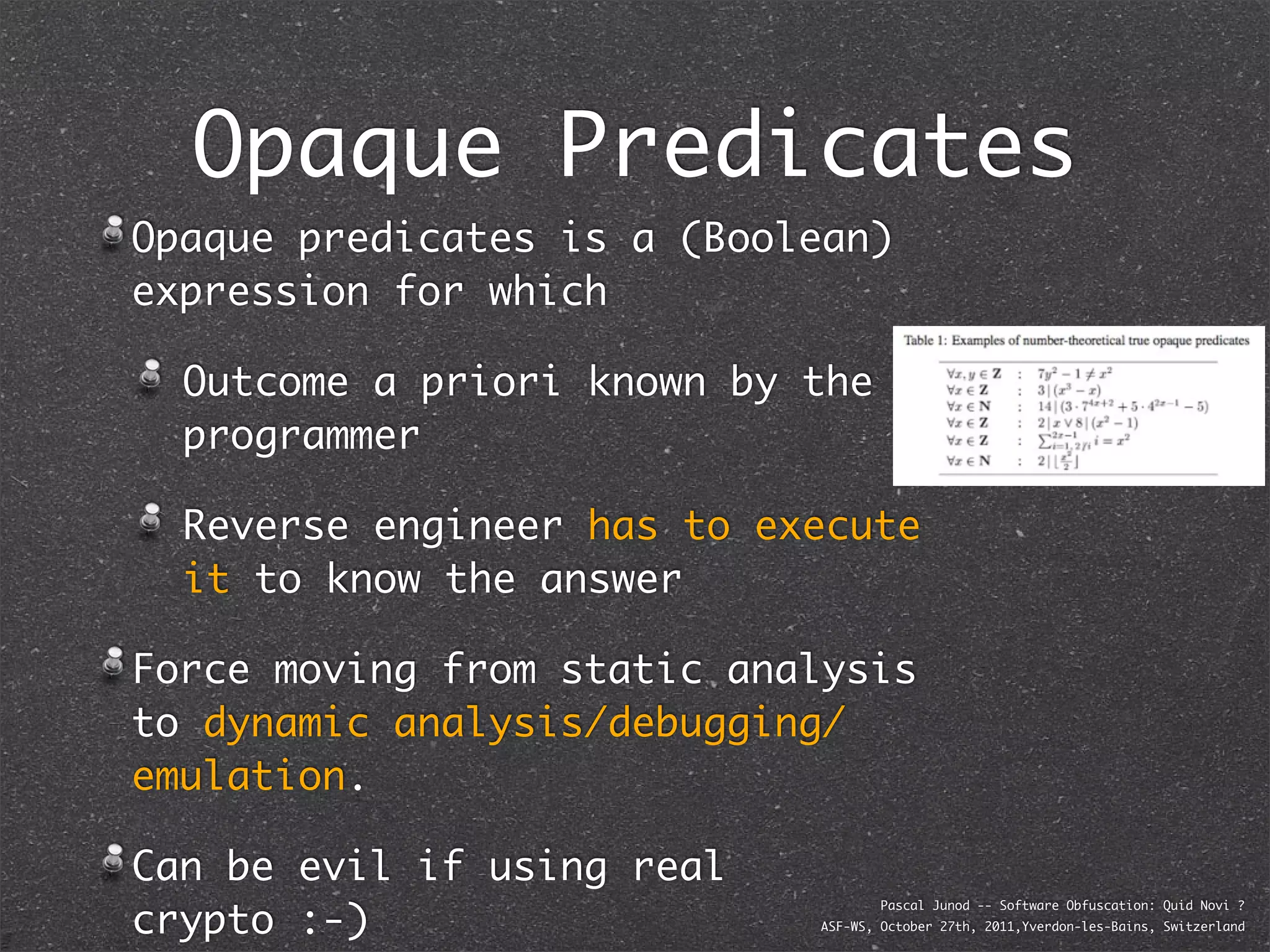
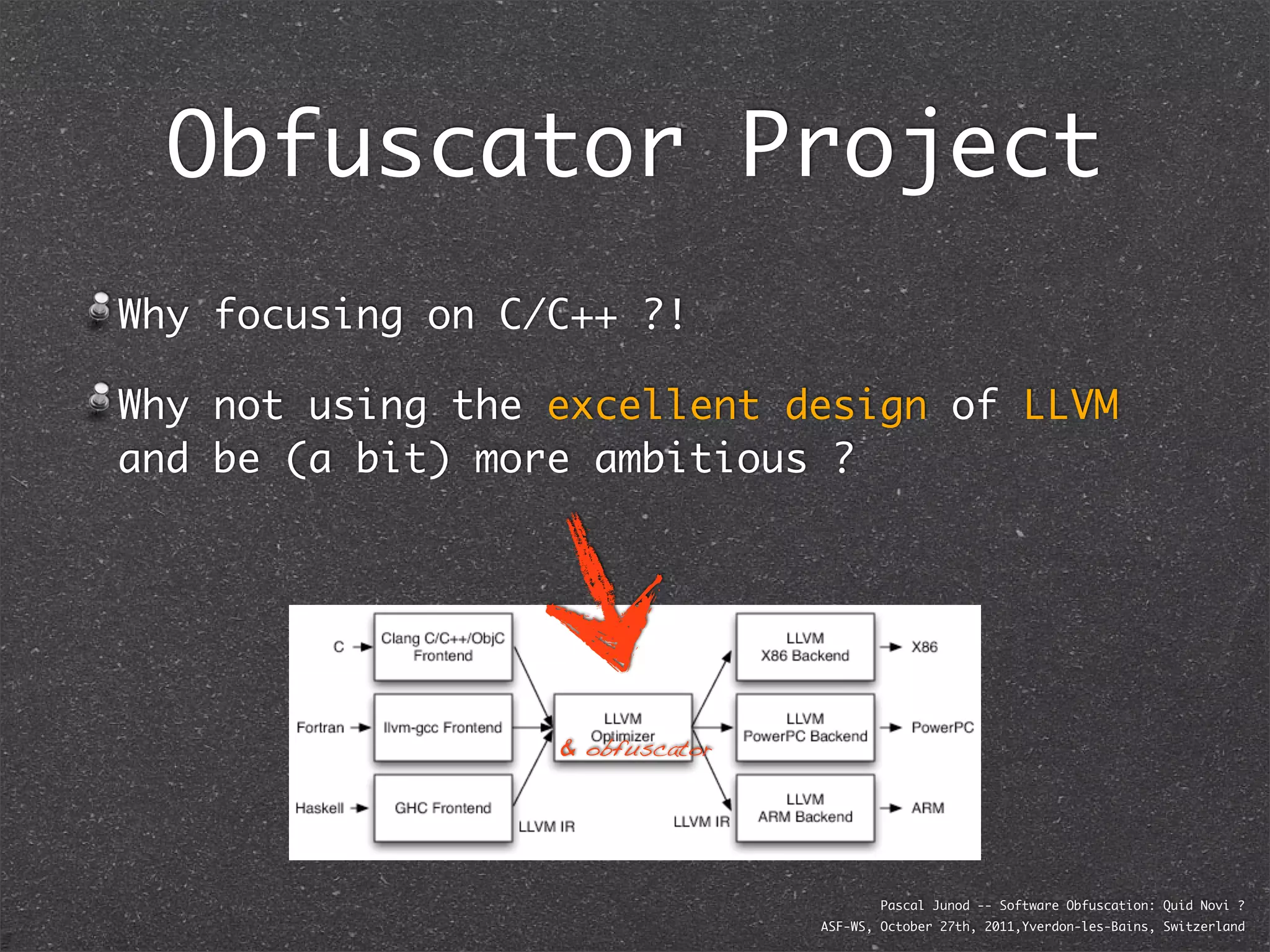
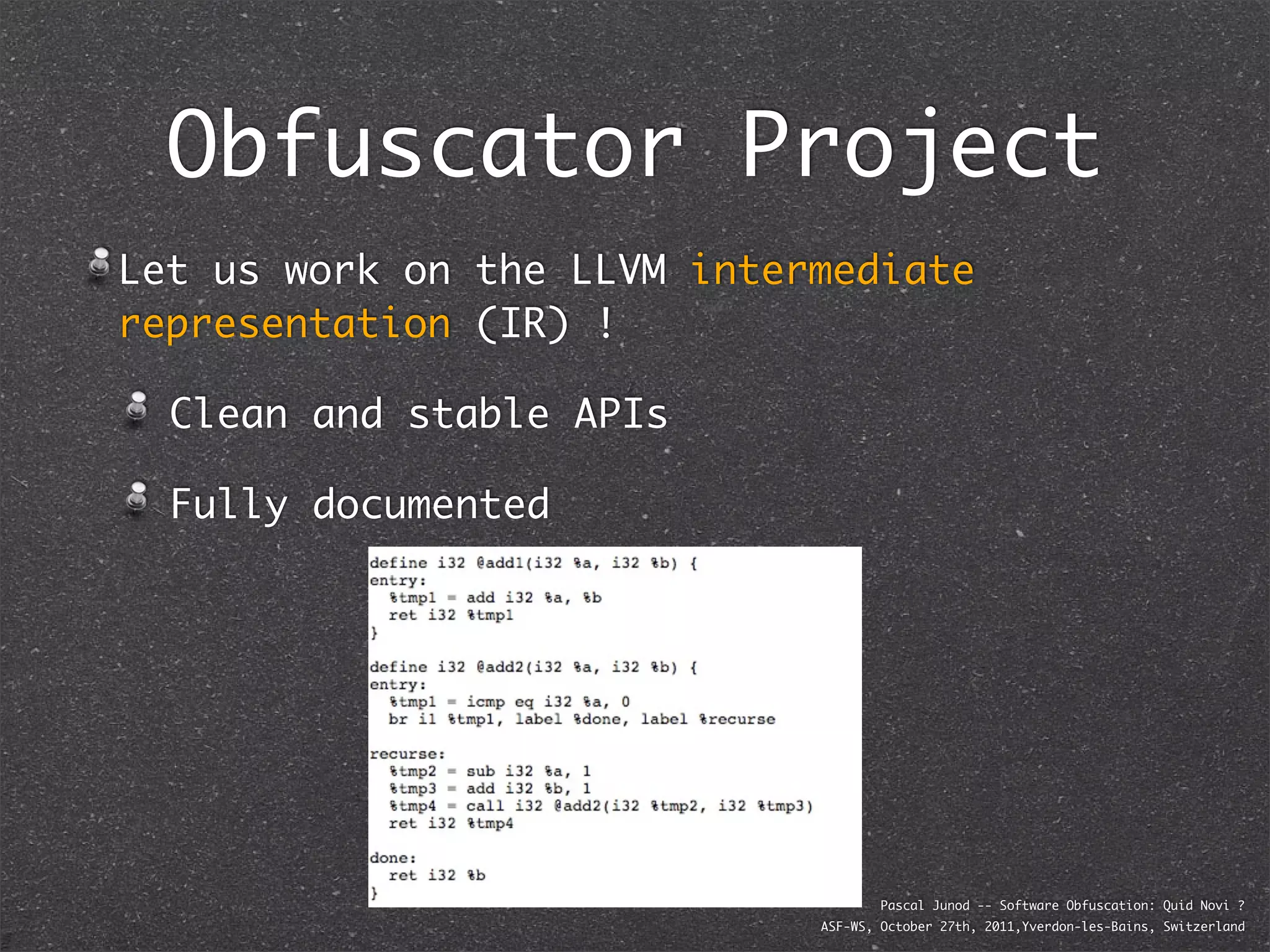
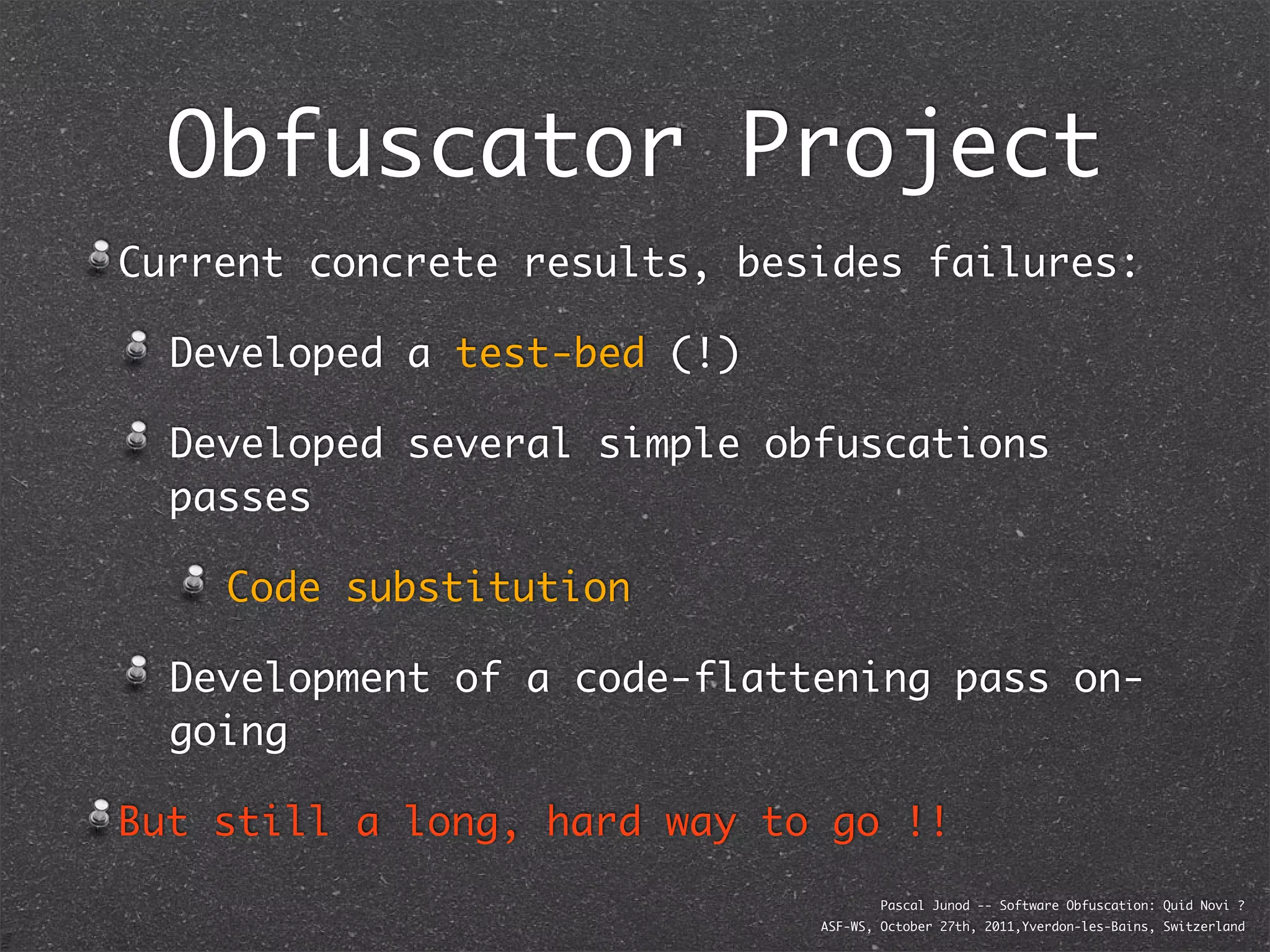
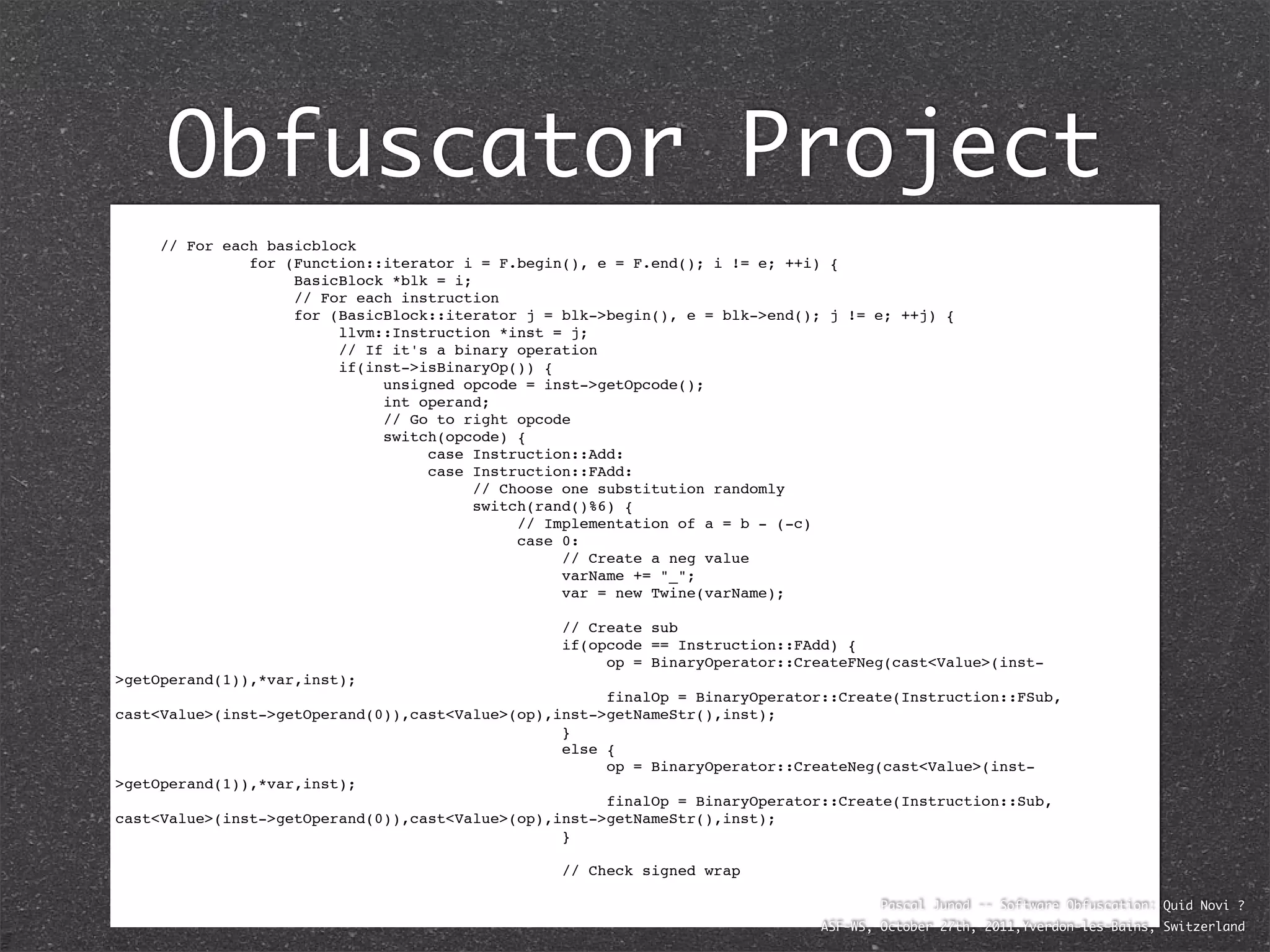
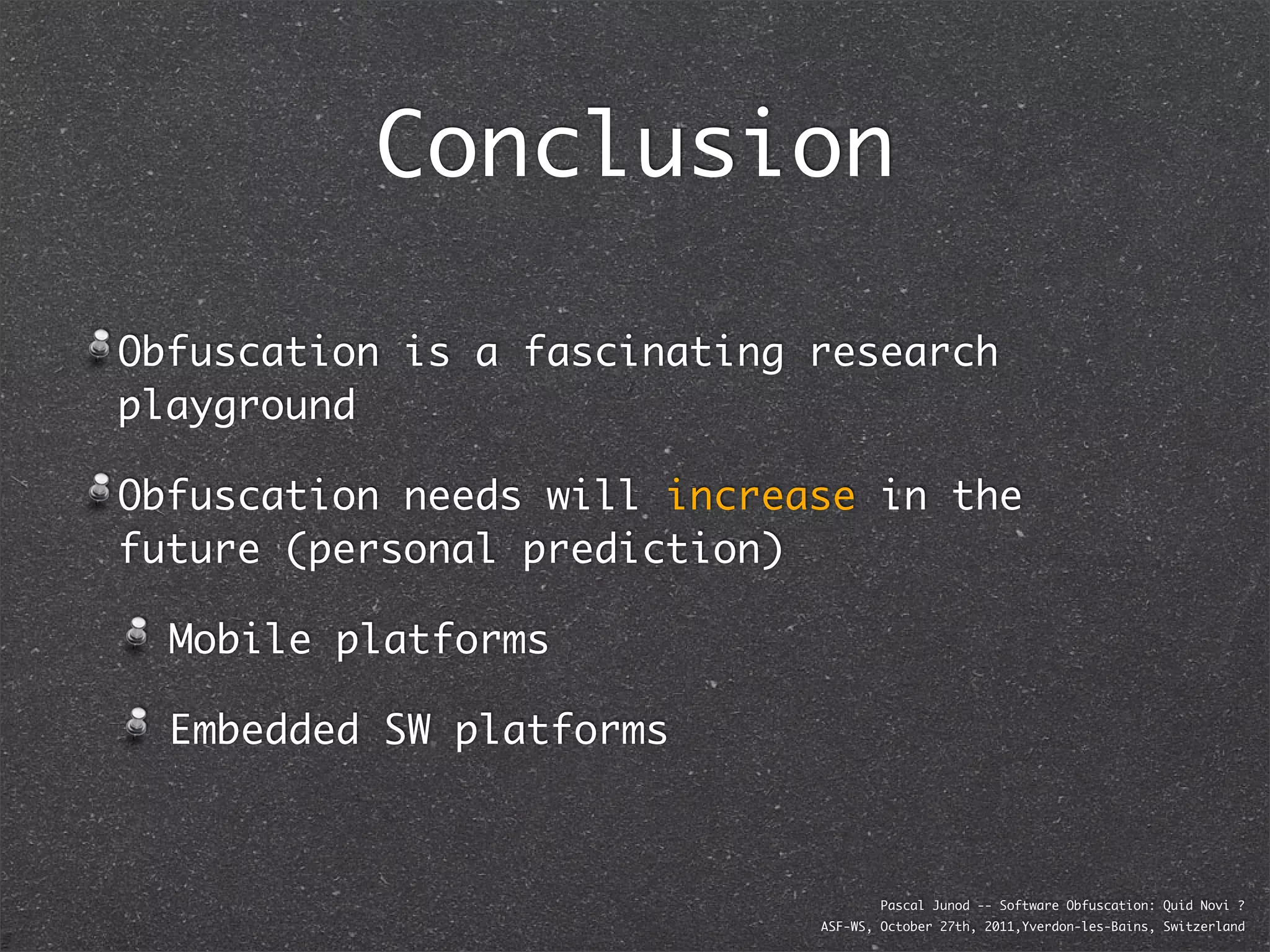
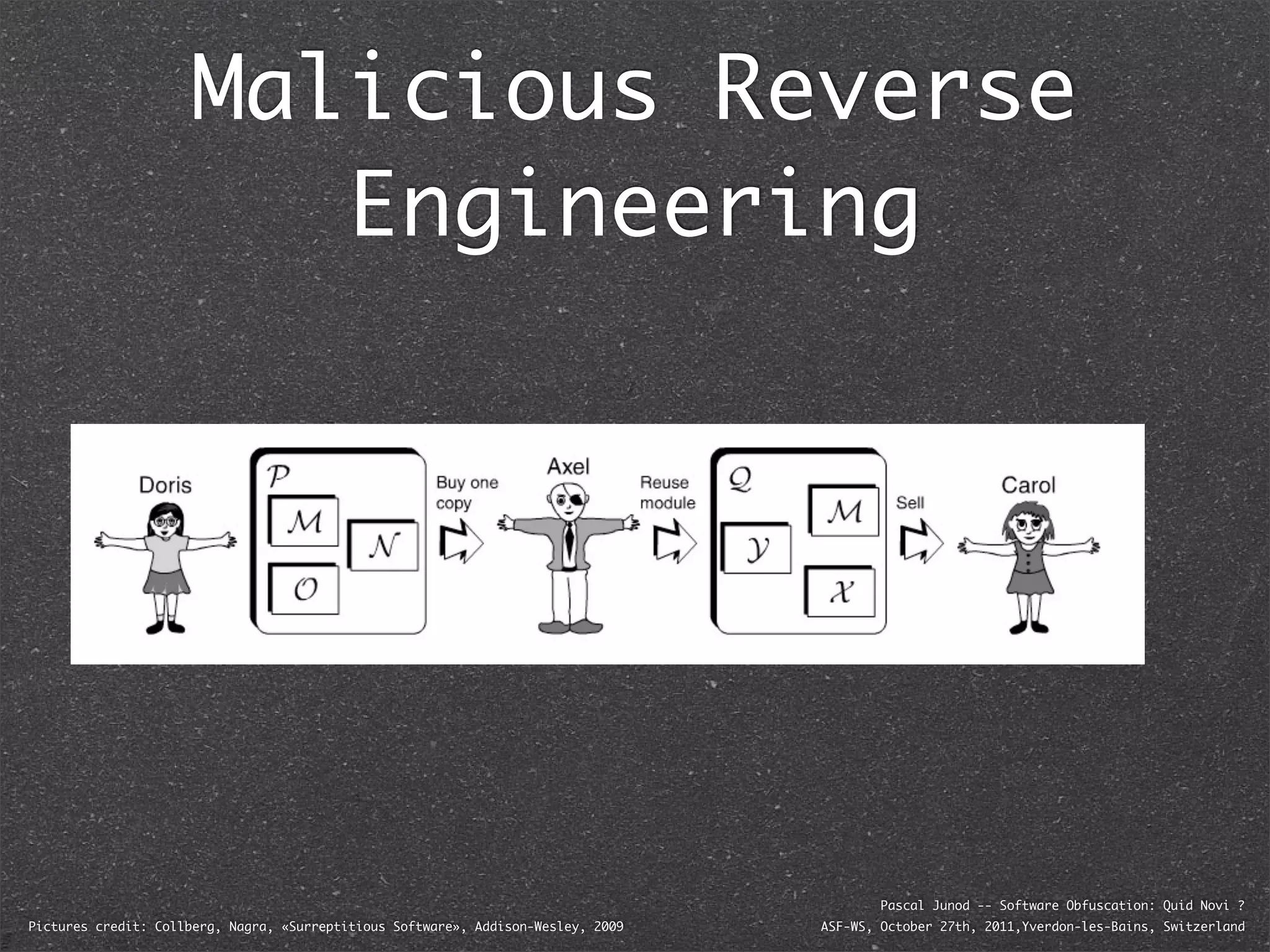
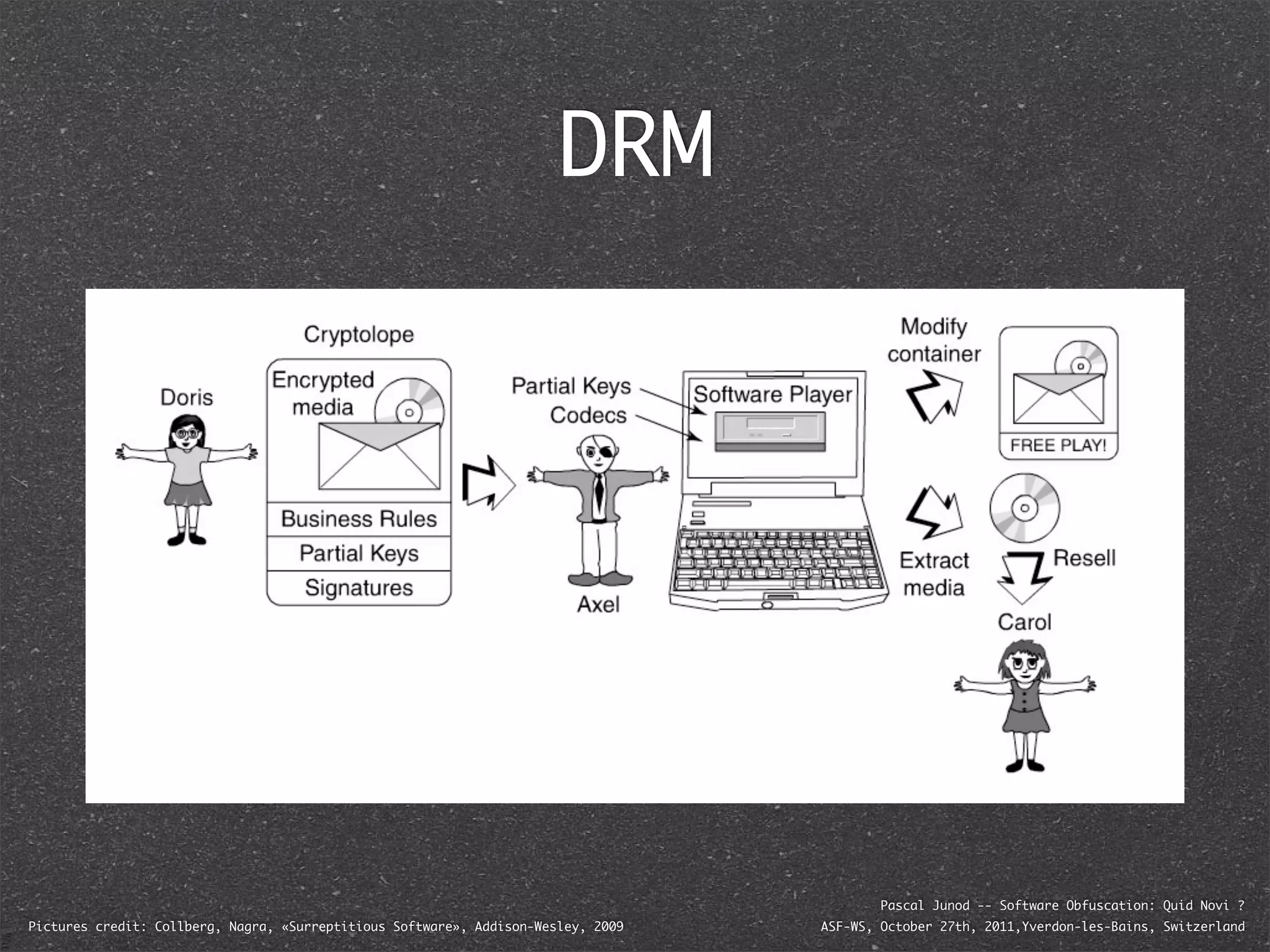
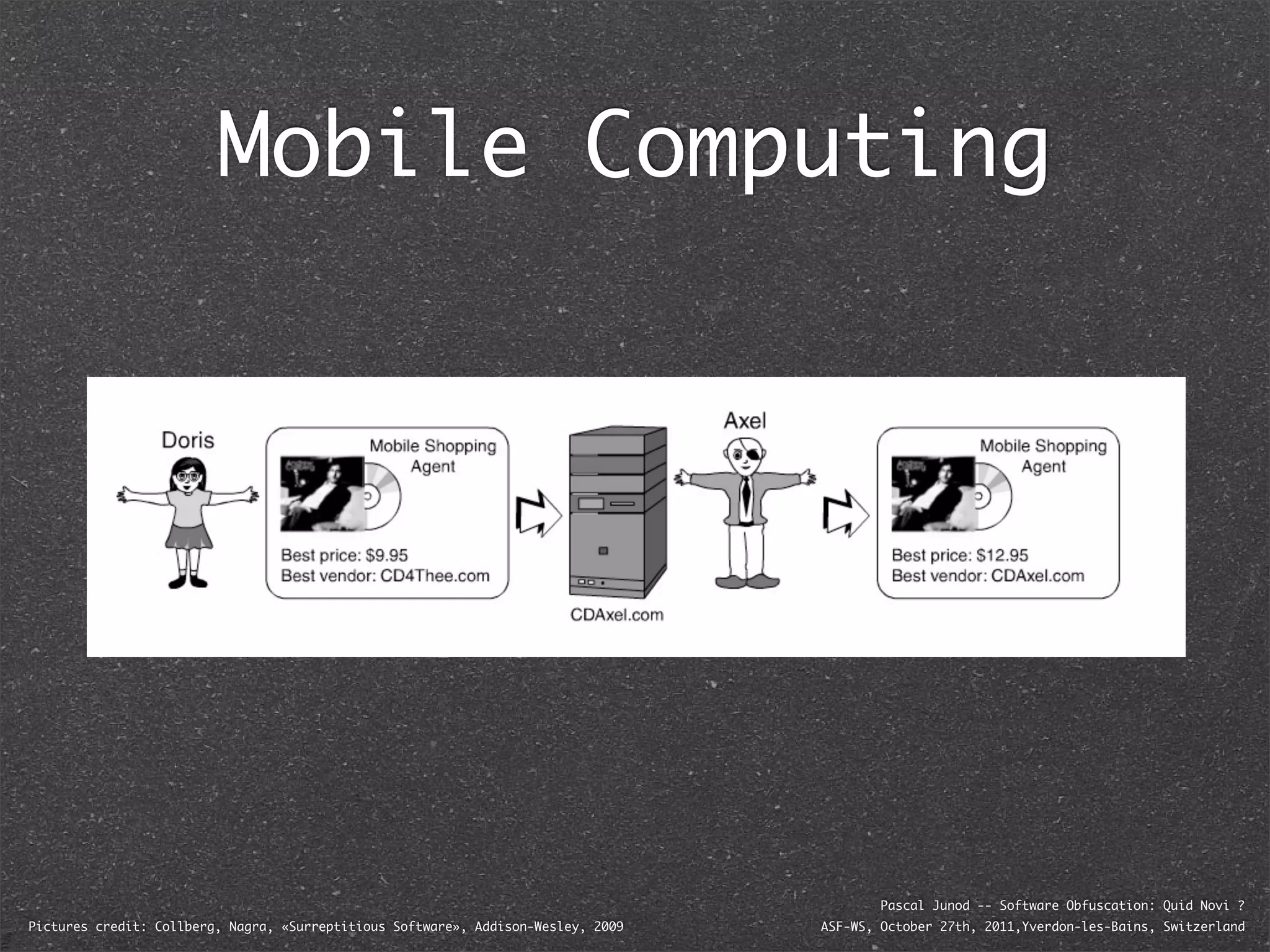
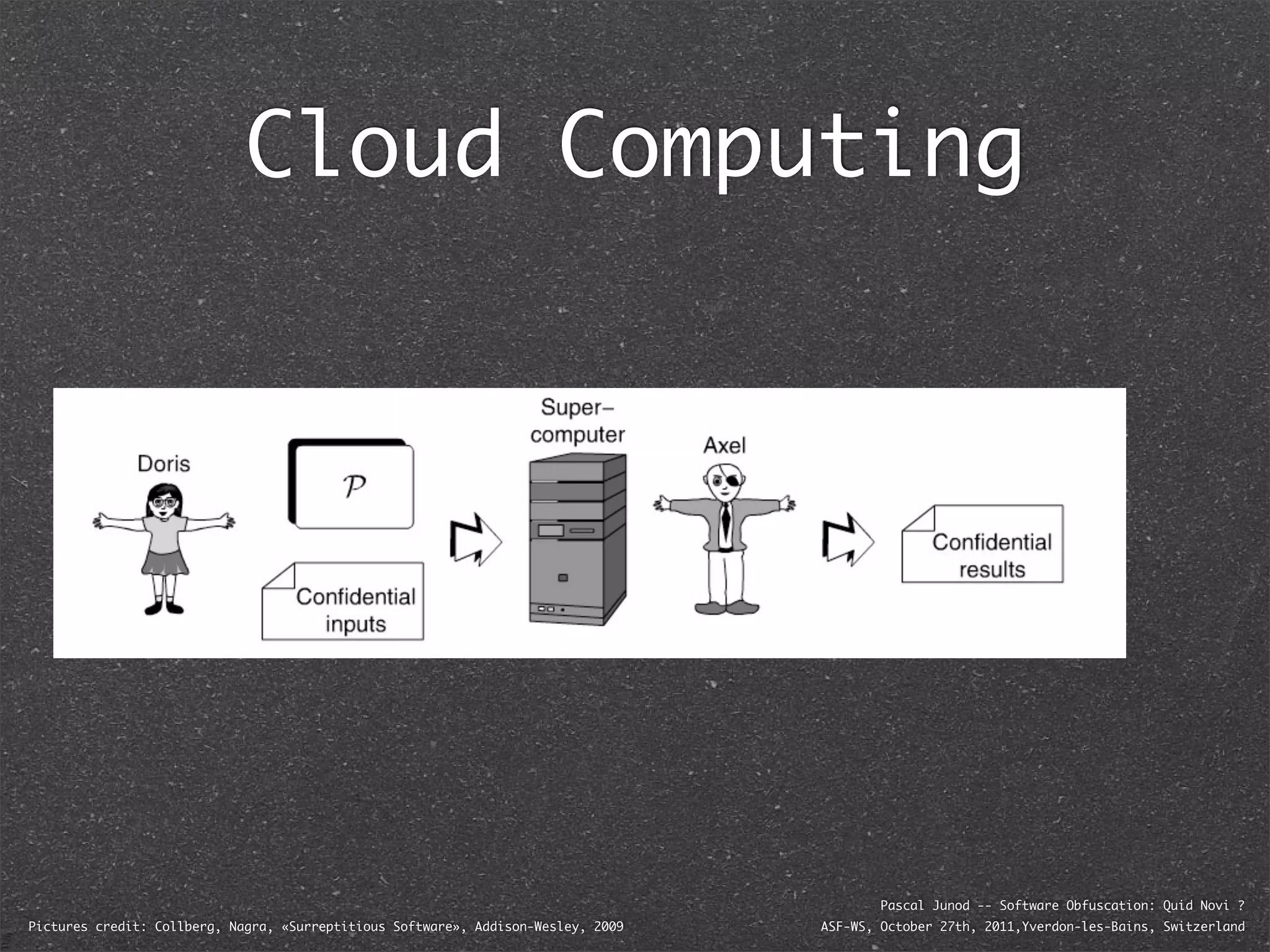
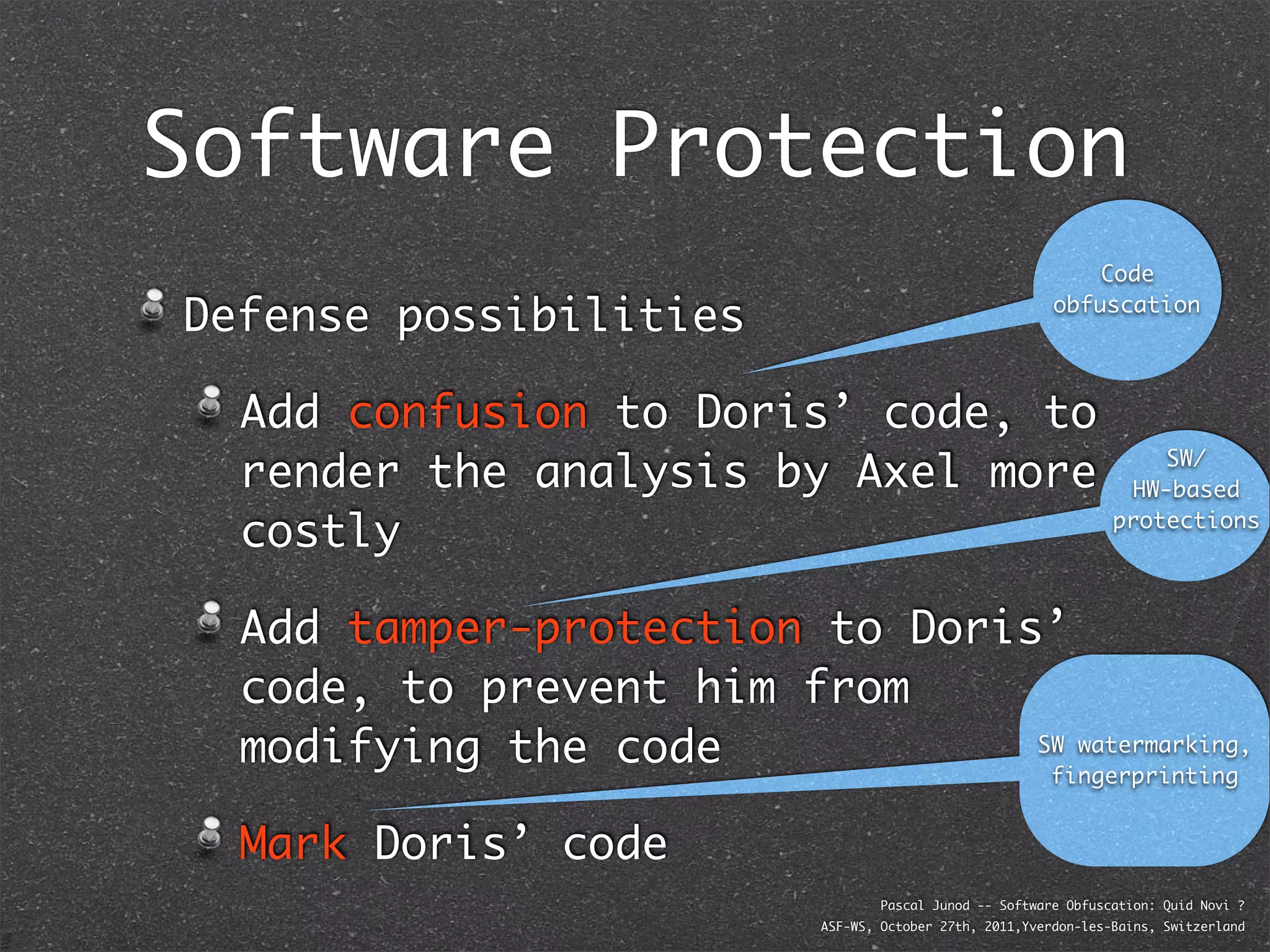
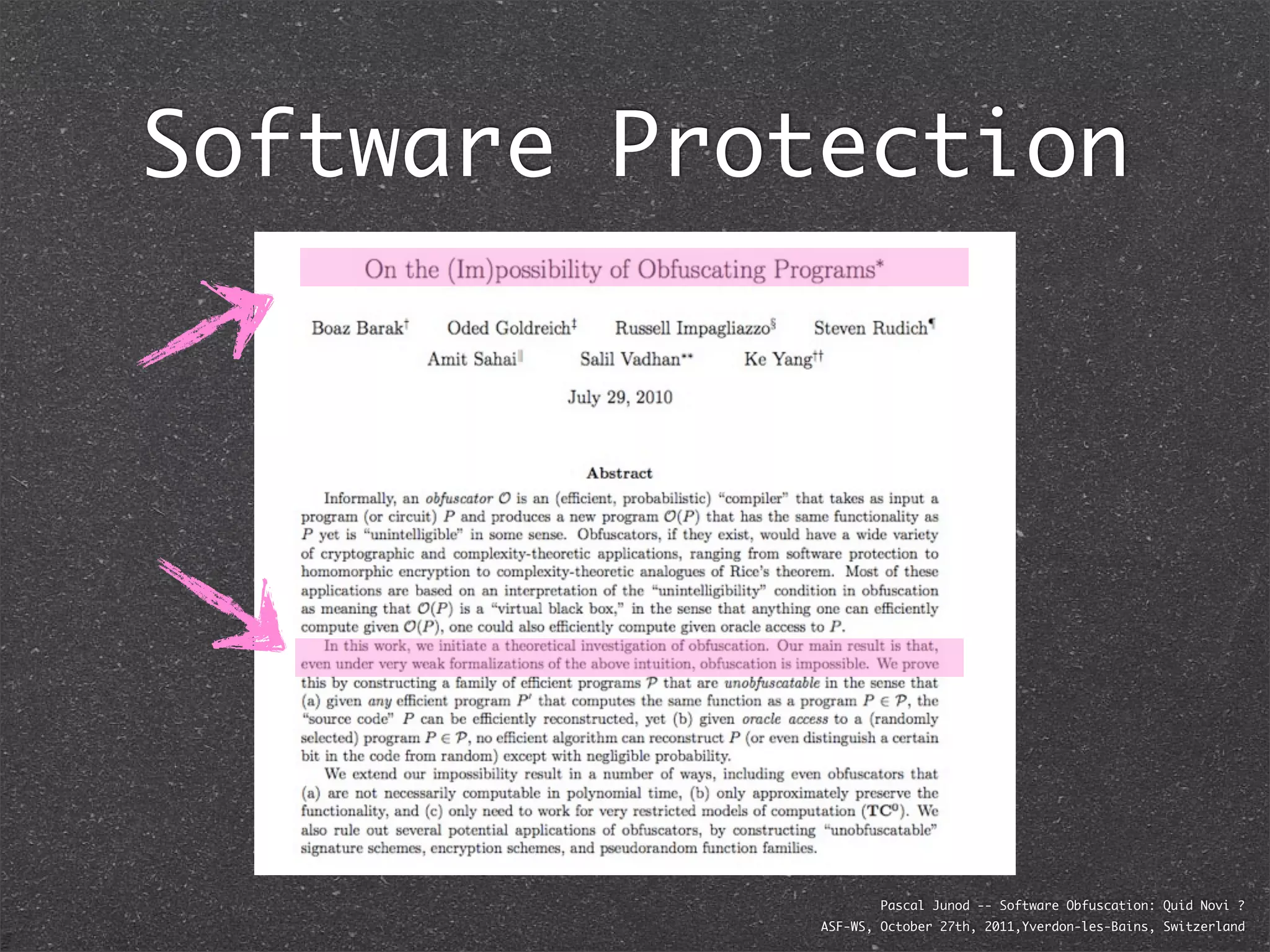
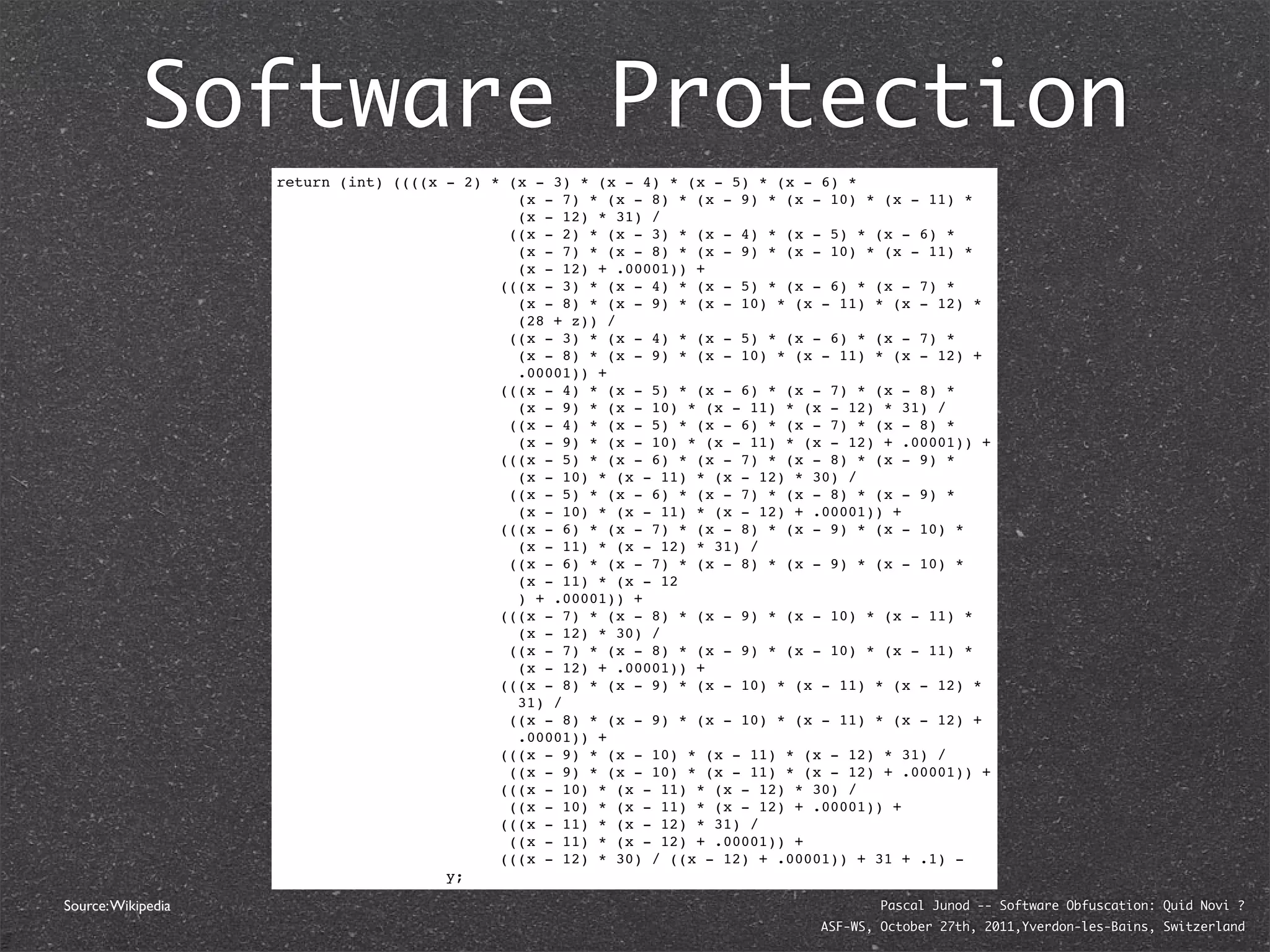
The document discusses various software obfuscation techniques and adversary models, including black-box, grey-box, and white-box adversaries that interact with software in different ways. It emphasizes the importance of robust security measures against these adversaries through obfuscation, coding best practices, and constant-time coding. Additionally, it highlights examples of real-world attacks and provides insights into software protection strategies and their complexities.

















![Software Protection
@P=split//,".URRUUc8R";@d=split//,"nrekcah xinU /
lreP rehtona tsuJ";sub p{
@p{"r$p","u$p"}=(P,P);pipe"r$p","u$p";++$p;($q*=2)+=
$f=!fork;map{$P=$P[$f^ord
($p{$_})&6];$p{$_}=/ ^$P/ix?$P:close$_}keys
%p}p;p;p;p;p;map{$p{$_}=~/^[P.]/&&
close$_}%p;wait until$?;map{/^r/&&<$_>}%p;$_=
$d[$q];sleep rand(2)if/S/;print
This tiny Perl program displays the text «Just another
Perl/Unix hacker», multiple characters at a time, with
delays.
Source: Wikipedia
Pascal Junod -- Software Obfuscation: Quid Novi ?
ASF-WS, October 27th, 2011,Yverdon-les-Bains, Switzerland](https://image.slidesharecdn.com/junod0seclight-111031153100-phpapp01/75/ASFWS-2011-Code-obfuscation-Quid-Novi-33-2048.jpg)