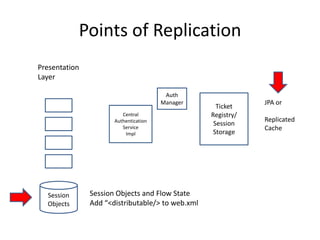
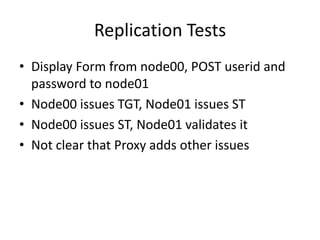
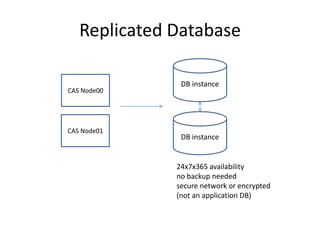
This document discusses high availability configurations for CAS using F5 load balancers and replicated databases across CAS nodes. It provides options for replicating session data and tickets using JBoss Cache or a replicated database. It also addresses testing and infrastructure considerations.








![Notcas-server-integration-jbossThat project uses JBoss Cache as a library, not a container serviceChange custom Cache<String,Ticket> to managed Cache<Object,Object>“cas-cache” configured along with session replication, etc., by JBoss admin [all the parameters are there, but they are someone else’s problem]](https://image.slidesharecdn.com/jasigcashighavailability-yaleuniversity-100908145802-phpapp01/85/Jasig-Cas-High-Availability-Yale-University-12-320.jpg)






