This document outlines a student's undergraduate project to develop a restaurant management system. It includes details of the project such as deliverables submitted, aims and objectives, proposed features of the system, and the research methodology to be used. The student plans to use a mixed methods approach including literature reviews, interviews, surveys and prototyping using an iterative development process. The goal is to develop a software application to help restaurants minimize problems and increase profits by improving order management and communication between front-of-house and kitchen staff. Key deliverables will include functional and non-functional requirements analysis, system design documentation, a working prototype, testing results and a final evaluation report.




![6
Action research ..................................................................................................................................................................................... 31
Use of Systematic Approach:........................................................................................................................................................... 32
3.6.1 Data Collection Methods used for the completion of this project ....................................................................... 32
3.6.2 Use of Systematic Approach................................................................................................................................................. 32
4.1 Project Management........................................................................................................................................................ 33
4.1.1 Activity List............................................................................................................................................................................. 34
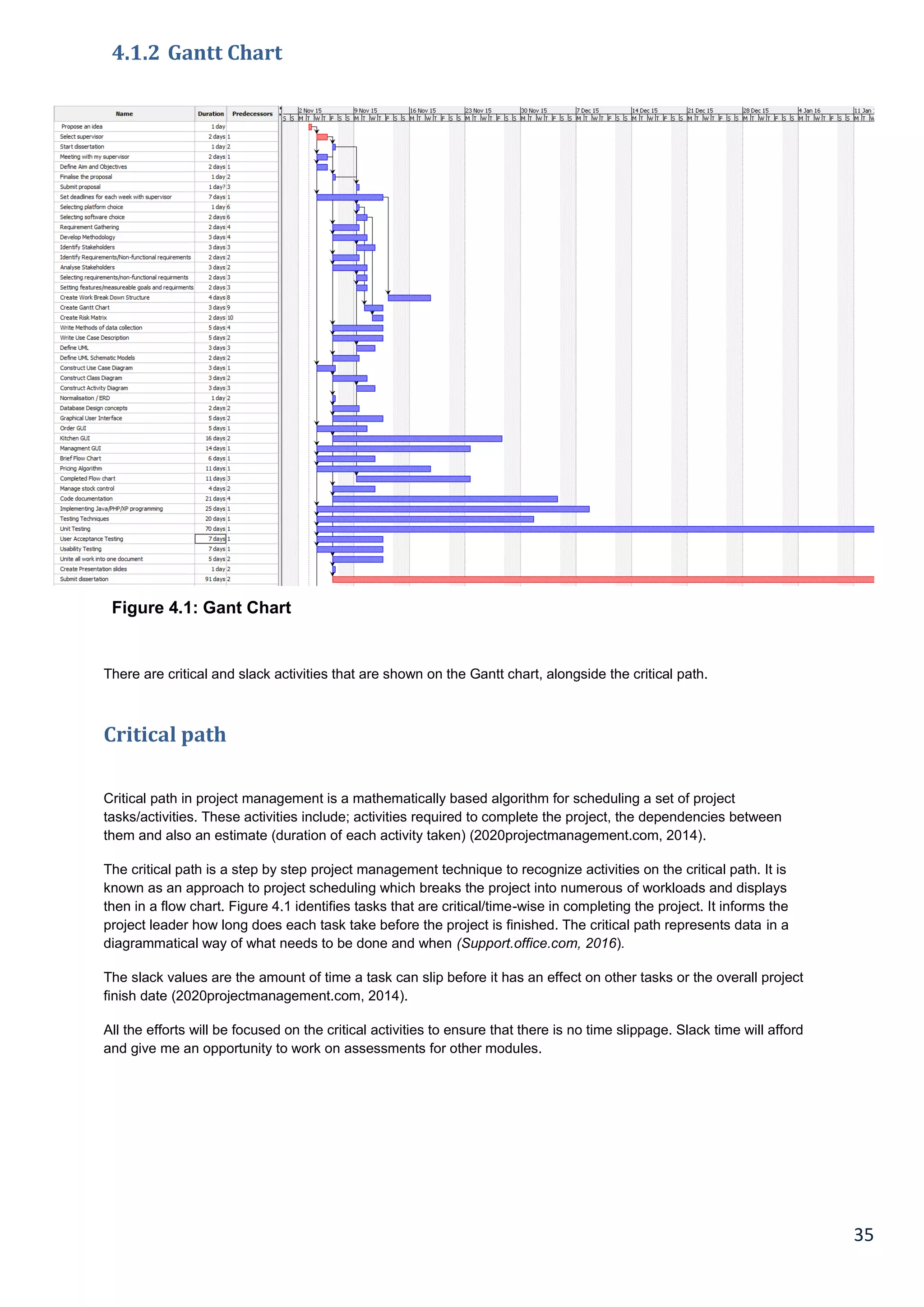
4.1.2 Gantt Chart.............................................................................................................................................................................. 35
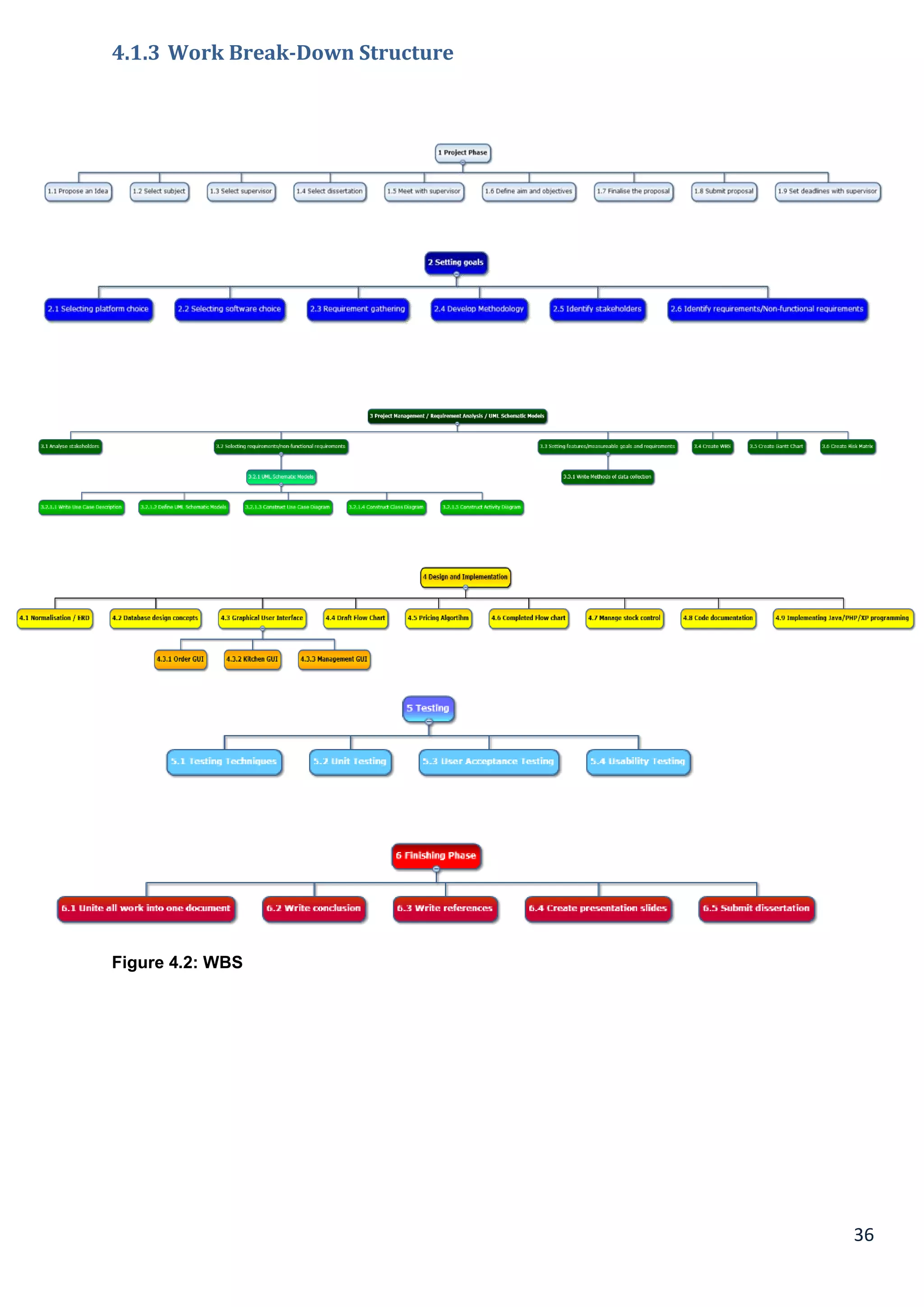
4.1.3 Work Break-Down Structure.......................................................................................................................................... 36
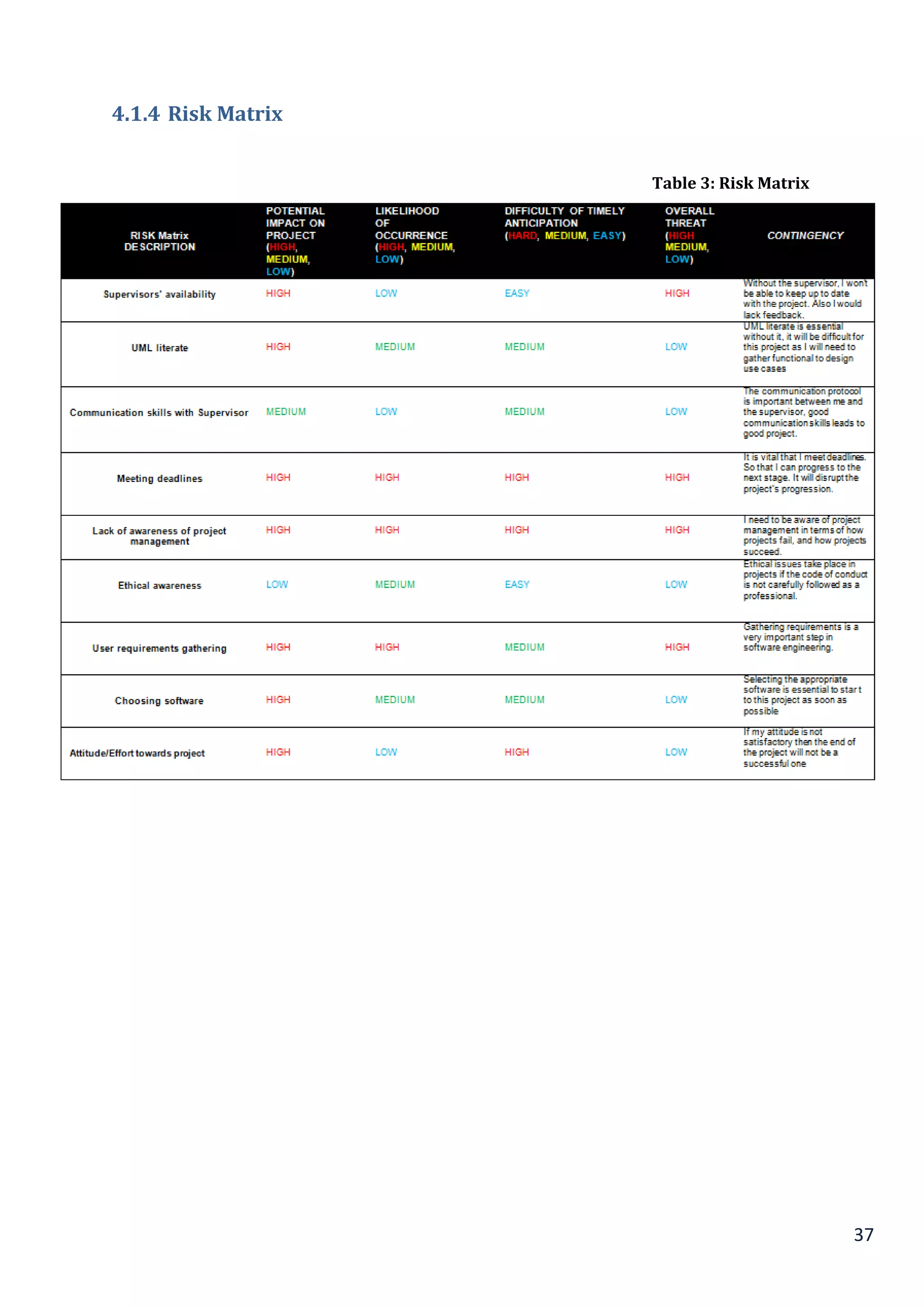
4.1.4 Risk Matrix.............................................................................................................................................................................. 37
5.1 Analysis & Design.............................................................................................................................................................. 38
5.2 System Analysis .................................................................................................................................................................... 38
5.2.1 System Design............................................................................................................................................................................. 38
5.3 Functional and Non-functional requirements......................................................................................................... 39
5.4 Data Method for Collecting Functional Requirements........................................................................................ 39
5.4.1 Questionnaires ........................................................................................................................................................................... 39
5.4.2 Focus Groups/Workshops ............................................................................................................................................... 39
5.4.3 Interviews .................................................................................................................................................................................... 39
5.4.4 How Functional and Non Functional Requirements are collected: .................................................................... 40
5.4.5 Formal Methods of Data Collection for Functional Requirements................................................................. 40
5.5 Definition of Terms ............................................................................................................................................................. 40
5.5.1 Use Case.................................................................................................................................................................................... 40
5.5.2 Class Diagram ........................................................................................................................................................................ 40
5.5.3 Activity Diagram........................................................................................................................................................................ 40
Functional requirements for the restaurant:........................................................................................................................... 41
Non-Functional requirements for the restaurant: ................................................................................................................ 41
5.6 Business case statement ................................................................................................................................................... 42
5.7 Business case statement [2]............................................................................................................................................ 43
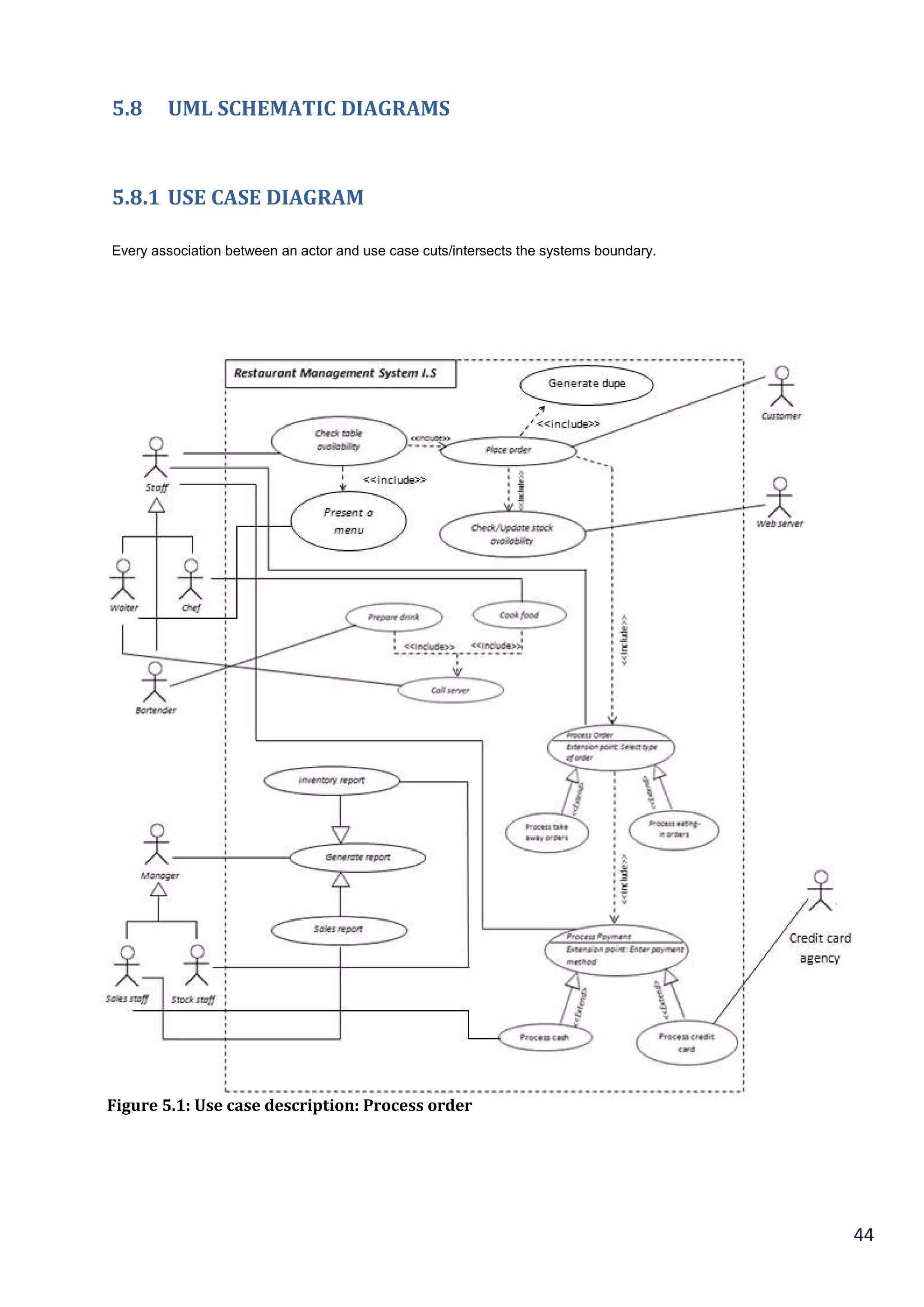
5.8 UML SCHEMATIC DIAGRAMS......................................................................................................................................... 44
5.8.1 Use case diagram.................................................................................................................................................................. 44
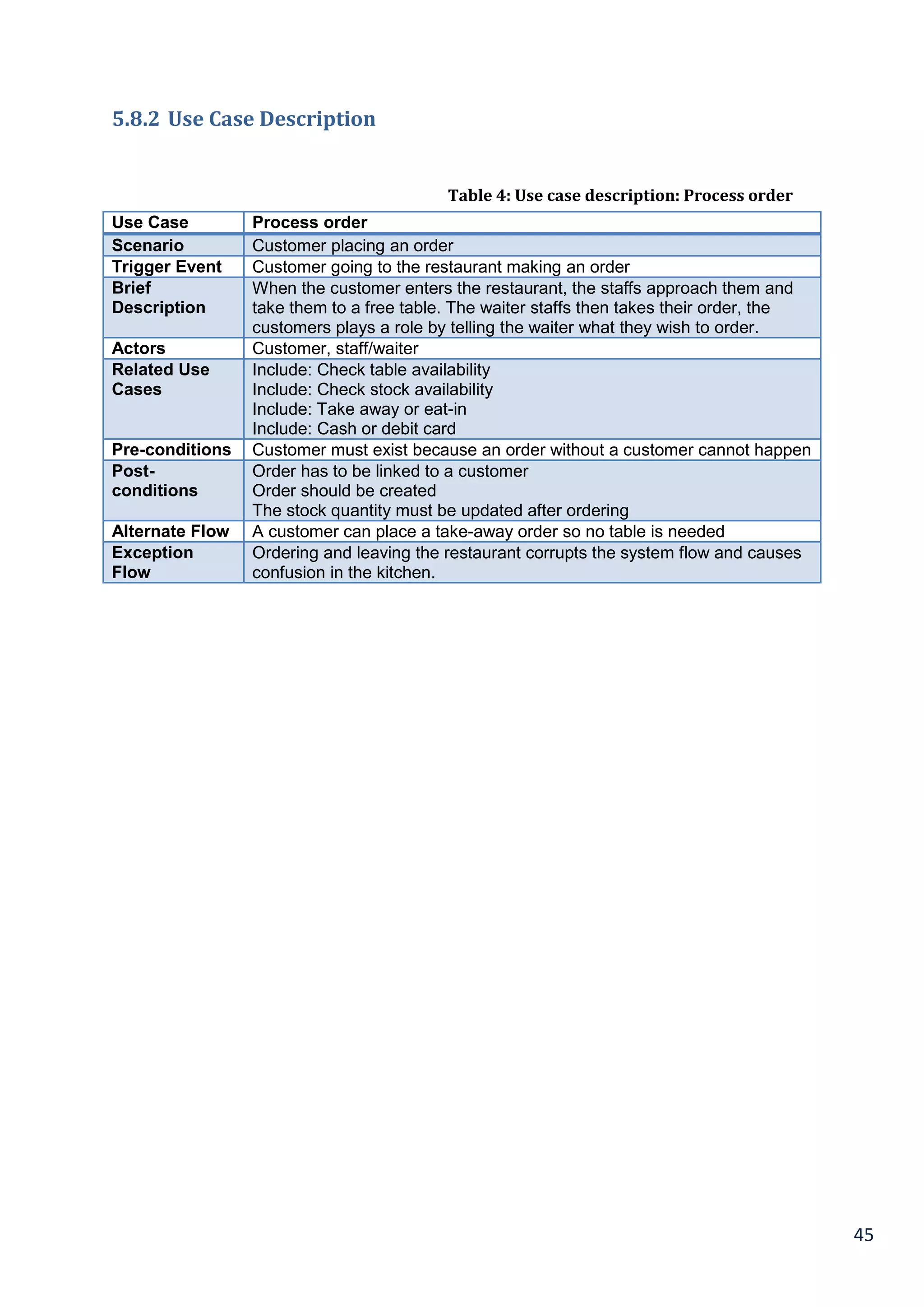
5.8.2 Use Case Description.......................................................................................................................................................... 45
5.8.3 Class Diagram ........................................................................................................................................................................ 46
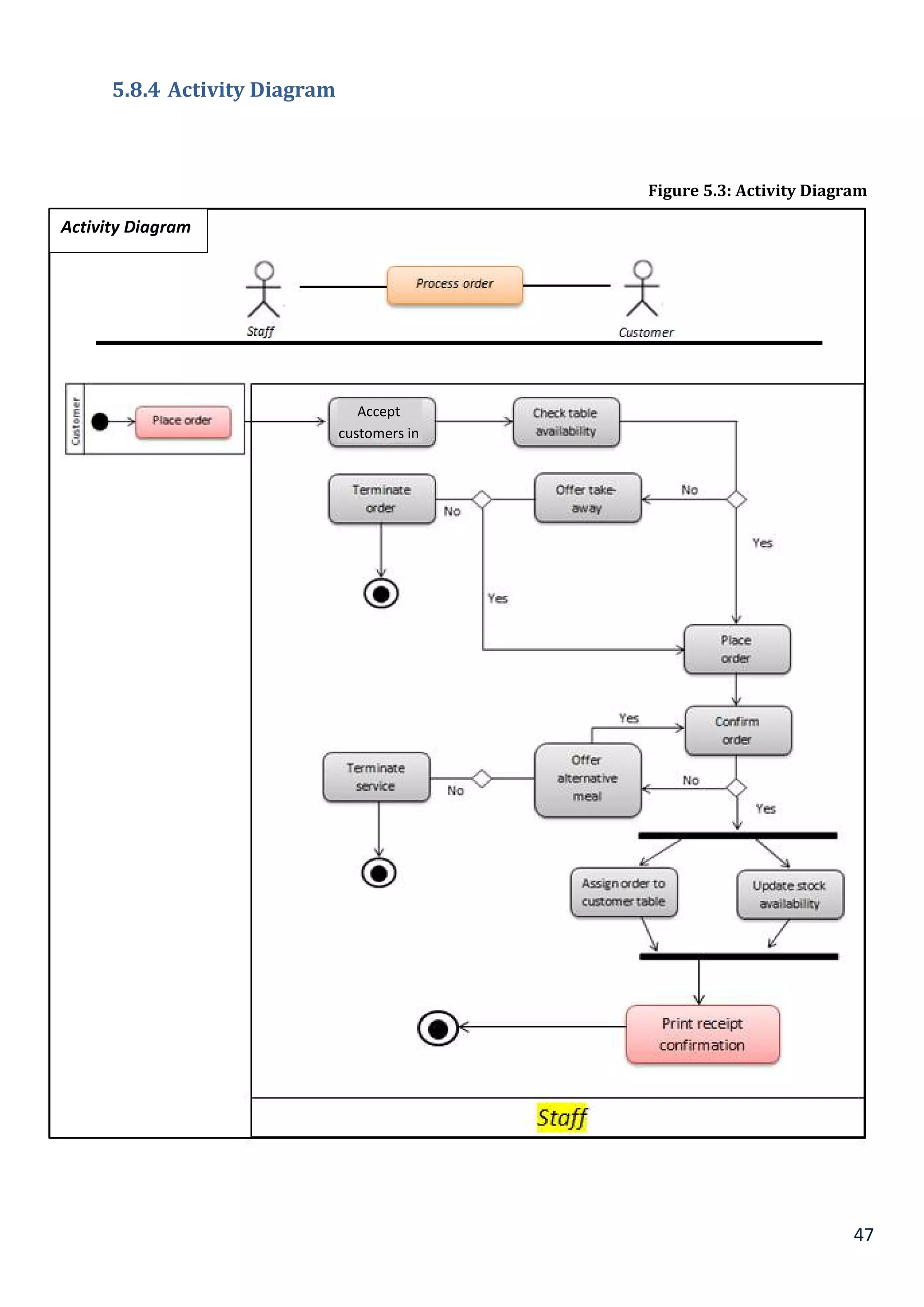
5.8.4 Activity Diagram................................................................................................................................................................... 46
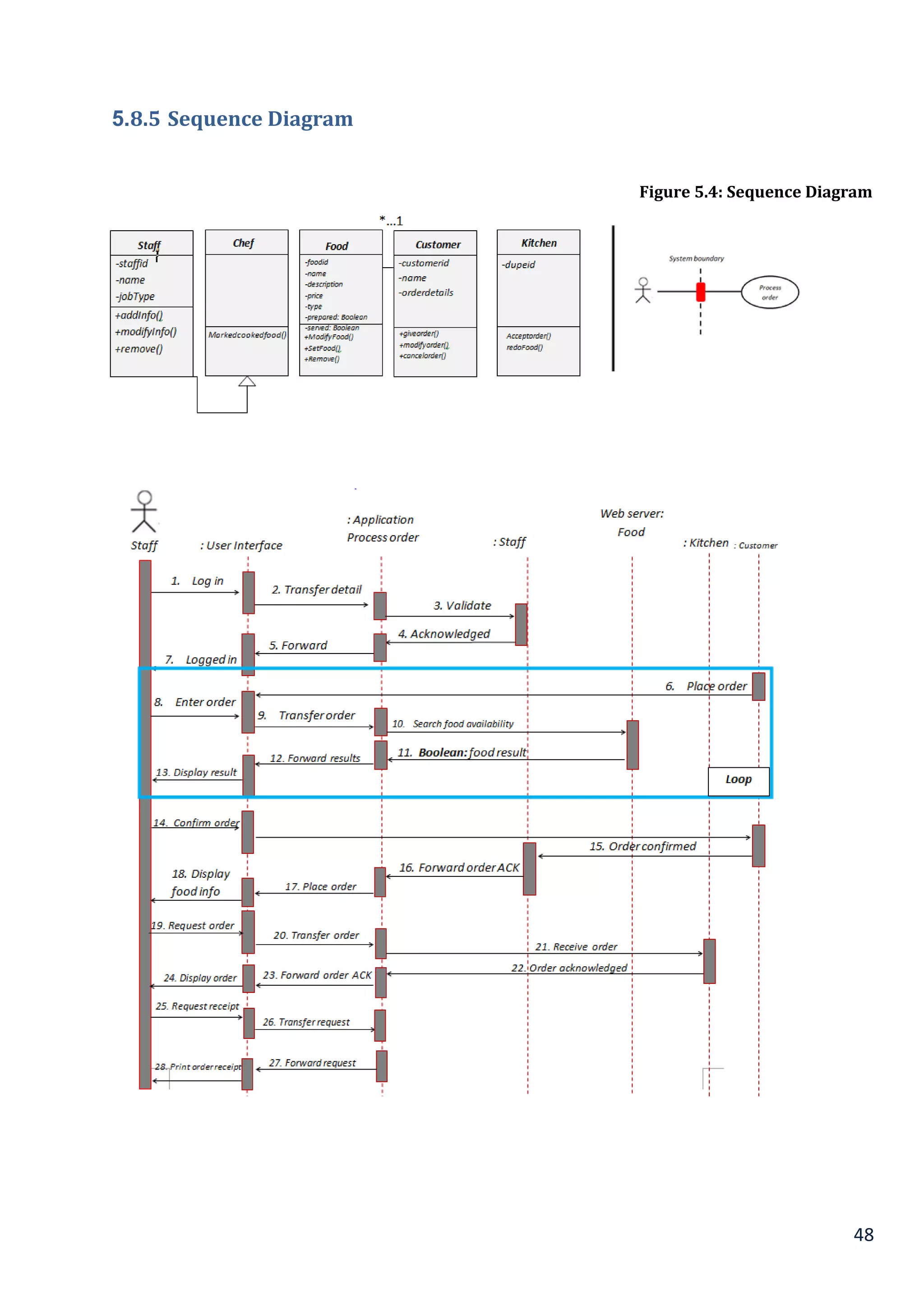
5.8.5 Sequence Diagram............................................................................................................................................................... 48
5.9 Web Interface Design ......................................................................................................................................................... 49
5.9.1 Design Principles for User Interface............................................................................................................................ 49
5.9.2 Nielsen’s Heuristics............................................................................................................................................................. 49
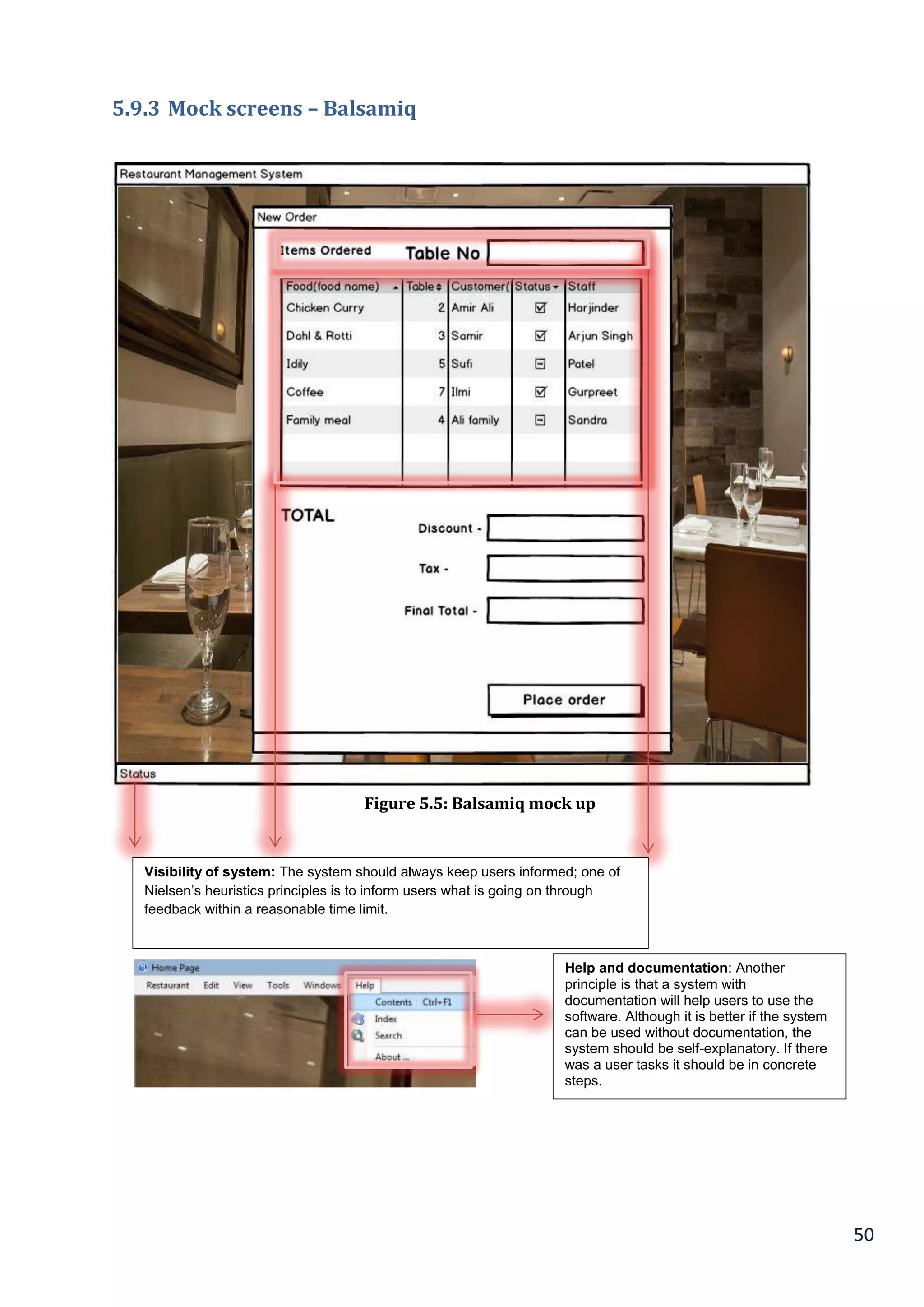
5.9.3 Mock screens – Balsamiq.................................................................................................................................................. 50
5.9.4 Accessibility (DDA ACT 1995 & EQUALITY LEGILSATION).............................................................................. 51
Disability Discrimination Act 1995.............................................................................................................................................. 51
Equality Legislation............................................................................................................................................................................. 51](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-6-2048.jpg)



![10
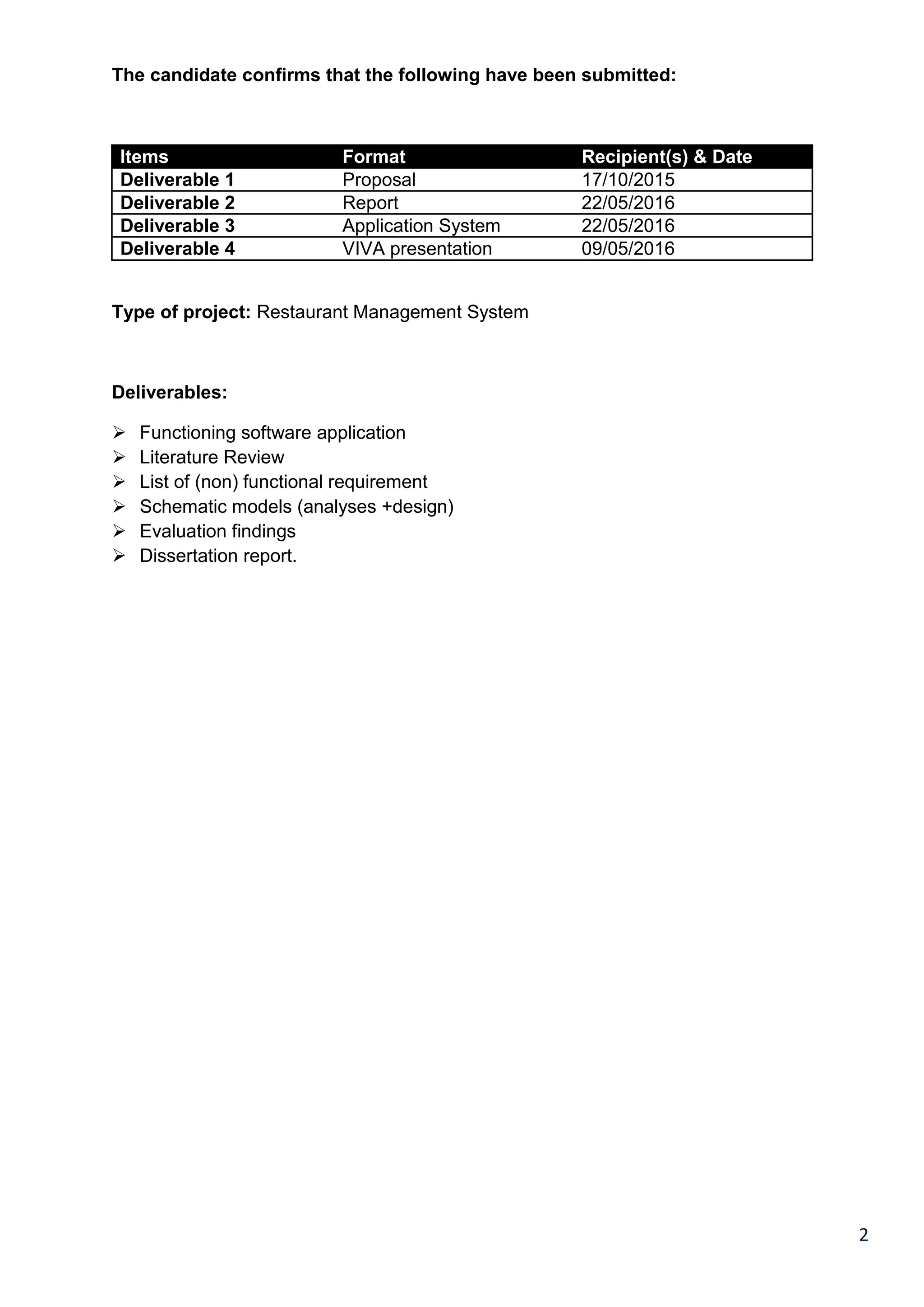
1.4 Project Proposal
The point of this project is to outline and make an restaurant management system using most of the systems and
techniques from the field guaranteeing that no common slip-ups are repeated. This improves client fulfilment which
results to profit gain.
There are recorded proposed features that can be found in table 1.1.
The main objective is to maximise profit by increasing efficient and decreasing the mistakes that take place in the
kitchen, this will be done without compromising customer satisfaction. At this moment of time, there are still
numerous restaurants that still use a paper-based system to get messages across between the restaurant and the
kitchen, this way of communication is one of the least efficient methods. However, this approach may be
implemented and designed in a successful profitable restaurant but there are numerous problems which might be
seen as reducing the restaurant's efficiency, they are the following problems:
The lack of communication that is caused by handwriting
Uncontrolled order logging(poor order taking)
Unproductive communication between restaurant & kitchen
Faults with order tracking and lack of time management
Lack of good quality stock management
Limited statistical output
1.5 Aim and Objectives
In order to complete this undergraduate project the following aim and objectives have been formulated and stated,
as follows:
Aim: To develop an IS application for a Small to Medium Sized Enterprise [SME] restaurant
Objectives:
Conduct a literature review in order to ascertain what the salient issues are concerning the analysis, design
and implementation of IS application for SMEs and in particular Restaurants
Use primary research methods in order to collect functional and non-functional requirements from the client
[restaurant business]
Complete an analysis and design of the IS application.
Complete testing, implementation and evaluation of the IS application
Complete a self-evaluation of the under graduate project experience](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-10-2048.jpg)













![32
Six principles used for an action research:
1. Reflexive critique: this involves noticing and being aware of our individual perceptual biases.
2. Dialectical Critique: This is a way of understanding the relationship between the various components that
make up the phenomena in the present context.
3. Collaborative Resources: In this situation, the views and opinions of everyone are respected as individually
contributing to a better understanding of the scenario in question.
4. Risking Disturbance: In this situation, the researcher should accept the reality of his work being criticized after
it has been submitted.
5. Creating Plural Structures: This is concerned with the creation of several accounts and multiple critiques
instead of a single individual and authoritative translation.
6. Internalization of Theory and Practice: This is a situation in which theory and practice is seen in the light of
two interdependent and complementary phase of the process of change.
Use of Systematic Approach:
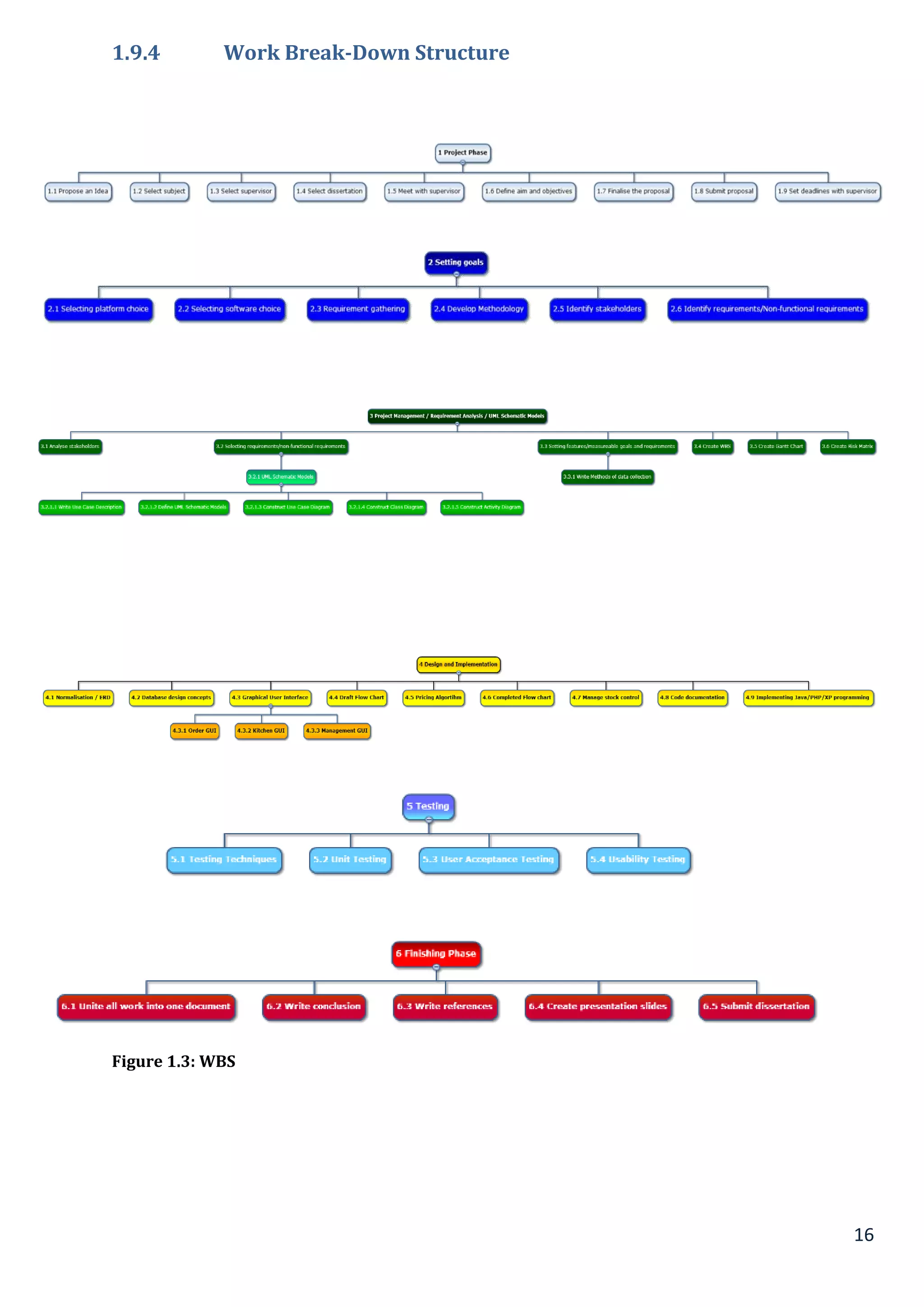
Referring to the undergraduate project that is in the process of completion, formal research methods were not
consciously adhered to. This doesn’t mean that the project wasn’t completed in a structurally organised manner.
The project was divided into milestones that were further sub-divided into manageable tasks (See Chapter 1,
Figure 1.3: Work Breakdown Structure).
In order to accomplish this project, project management models were developed. See Chapter 4.
3.6.1 Data Collection Methods used for the completion of this project
The primary data to be acquired for this project would include:
Functional and non-functional requirements
User requirements and evaluations
The secondary data collected for this project include information. These data can be regarded as the most
important part of this project. They include: systems development (design, analysis, evaluation and
implementation), projecting management, ethical considerations, project write up and so on. The secondary data
would be gotten from:
Books and Journals [hard and soft copies]
Conference proceedings
The internet [blogs, wikis etc.]
Trade magazine, Newspapers etc.
The different sources of secondary data would be adequately listed in the Bibliography and References.
3.6.2 Use of Systematic Approach
Referring back to the undergraduate project that is on the journey of completion, a formal research method was
not consciously followed. However this does not mean the project was not completed in an organised structure.
The project was broken down to milestones that were further broken down into manageable tasks (See Chapter 1,
Figure 1.3: Work Breakdown Structure).
Project management models were developed in order to support this project to be accomplished. See chapter 4.](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-32-2048.jpg)





![42
5.6 Business case statement
ALI BABA FOOD - Restaurant Business Case Statement
Situational Assessment and Problem Statement:
Ali Baba have not provided easy ways of taking orders from customers, we have some high standard chefs who
can’t read handwritings and find it difficult to do their job efficiently and on time. Customers don’t want to wait for a
long time for their food to be served; therefore by including a digital form of taking orders will make the
communication between the waiter and kitchen productive.
The lack of communication that is caused by handwriting
Uncontrolled order logging(poor order taking)
Unproductive restaurant-kitchen communication
Problems with order tracking and lack of time management
Lack of good quality stock management
Limited statistical output
Project description:
The project goal is to maximize profit by increasing efficient and decreasing the mistakes that take place in the
kitchen, this will be done without compromising customer satisfaction. At this moment of time, there are still
numerous restaurants that use a paper-based system to communicate between the restaurant and kitchen which
can be shown to be one of the least efficient methods. However, this approach may be implemented and designed
in a successful profitable restaurant but there are numerous problems which could be seen as reducing the
restaurant's efficiency.
This project will be completed by [April 2016].
Costs for the project also include staff, costs, ongoing costs, hardware/software and implementation.
Solution description:
Within the restaurant sector, customers are likely to return to the restaurant depending on the service they get
such as receiving quality food, the customer service the waiter delivers to the customer. However, the problem
arises if they had to wait for an unreasonable amount of time which results to the food being cold, or a mistake in
the order. These problems make it unlikely for the customer to return.
Therefore a solution to this problem would be to minimise mistakes within the bill and order. Another solution is to
reduce delays; this comes through team work and communication within the team.
An increase in efficiency
Aiding communication between the waiter and the kitchen
Elevated profits
Better controlled order logging
Productive restaurant-kitchen communication
Good quality stock management
Unlimited statistical output
Construct reports that can be utilised to determine value of electronic resources as well as training needed by
staff members
Built-in smart TV in the kitchen to see orders that are sent by the waiter/waitress](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-42-2048.jpg)
![43
5.7 Business case statement [2]
Cost and benefit analysis:
This includes the cost of the project alongside any benefits and any return on investment. The cost of the solution
is £19000 including software, hardware, etc. A breakdown of each component of the purchase will be shown. The
implementation of the software will enhance and improve management.
250+ electronic systems for which Ali Baba’s need to pay for.
Improved management in the user of IDs and passwords for staffs, it is important each staff has their own log
in details to track performance.
An increase in efficiency
Aiding communication between the waiter and the kitchen
Elevated profits
Better controlled order logging
Productive restaurant-kitchen communication
Good quality stock management
Unlimited statistical output
Implementation timeline:
Set up and propose a database which will hold user IDs and passwords [March 2016]
Set up a system which deals with the billing system (payment e-commerce) [March 2016]
Build a system that keeps a record of stock availability [March 2016]
Build a pricing algorithm to calculate the price of the food [March 2016]
Begin Testing [Feb 2016]
Install and other components also providing training to staffs by [March 2016]
Second Testing [March 2016]
Release date [April 2016]
Risk Assessment:
The system may fail to deliver on its promised time.
The system may not evolve as expected
Conclusions and recommendations:
The benefits and advantages of the system outweigh the costs and the risks
The company should go ahead with the proposal](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-43-2048.jpg)
![46
5.8.3 Class Diagram
<<use>>
+calculateTotal ()
Figure 5.2: Class Diagram
Order line [Dupe]
-ordernumber
-dupeid
-dupedescrition
+Generatedupe()
Food
-foodid
-name
-description
-price
-type
-prepared: Boolean
-served: Boolean
1...1 1...1
+modifyFood()
+setFood()
1...1 1...1
Table Reservation
*...1
1...1
1...1
*...1
-customerid
-bookingid
+reserveTable()
+cancelreservation()
+viewBooking
Kitchen
-Dupeid
+Acceptorder()
+RedoFood
<<use>>](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-46-2048.jpg)












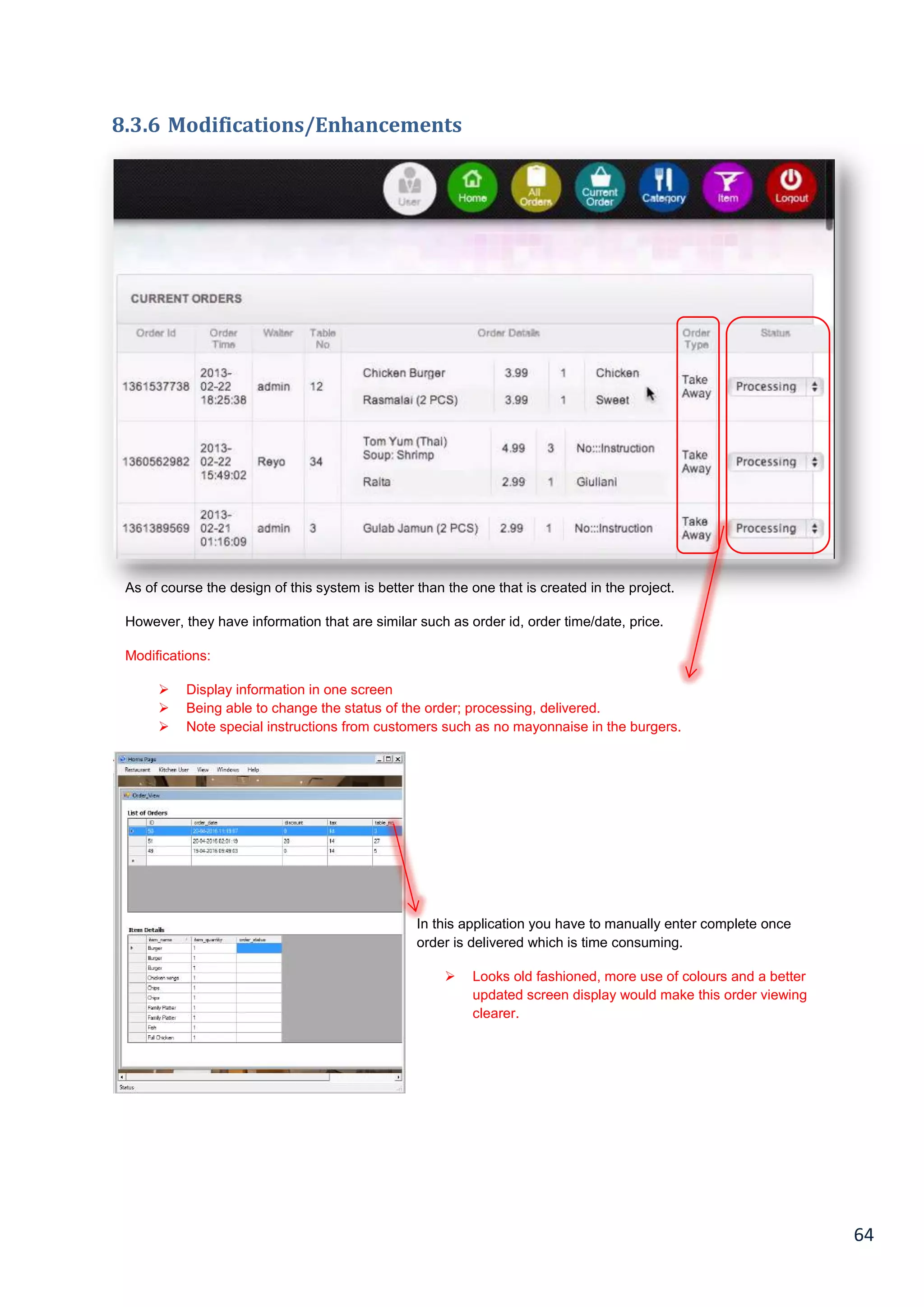

![66
References
Acunetix, (2016). What Are Web Applications?. [Online] Available at:
http://www.acunetix.com/websitesecurity/web-applications/ [Accessed 26 Jan. 2016].
Allison, B. (1996). Research skills for students. London: Kogan Page, p.17.
Arora, N. (2015). South Asian Journal of Management. AMDISA Secretaiat.
Bbc.co.uk, (2015). BBC Bitesize - GCSE Computer Science - Programming software and the IDE - Revision 4.
[online] Available at: http://www.bbc.co.uk/education/guides/zgmpr82/revision/4 [Accessed 20 Oct. 2015].
Bennett, S., McRobb, S. and Farmer, R. (2010). Object-oriented systems analysis and design. Maidenhead,
Berkshire: McGraw-Hill Higher Education, p.154.
Chappel, D. (2001). WHAT IS AN APPLICATION PLATFORM? New York: Microsoft Corporation.
Craig Murphy (2015). Improving Application Quality Using Test-Driven Development (TDD). [online] Available at:
http://www.methodsandtools.com/archive/archive.php?id=20 [Accessed 3 Nov. 2015].
Creative Educator. (2016). Embrace Action Research. [online] Available at:
http://www.thecreativeeducator.com/v07/articles/Embracing_Action_Research [Accessed 22 Mar. 2016].
Crowther, D., Lancaster, G. and Lancaster, G. (2009). Research methods. Amsterdam: Butterworth-Heinemann,
pp.89-91.
Cutler, Z. (2014). The 4 Biggest Challenges Facing E-Commerce Businesses | Cutler PR. [online] Cutlerpr.co.
Available at: http://www.cutlerpr.co/4-biggest-challenges-facing-e-commerce-businesses/ [Accessed 20 Apr.
2016].
Designmodo, (2015). 20+ Examples of Web Application Interface Designs - Designmodo. [Online] Available at:
http://designmodo.com/web-application-interface/ [Accessed 26 Jan. 2016].
Docs.joomla.org, (2015). Category: IDÉE (Integrated development environment) - Joomla! Documentation.
[Online] Available at: https://docs.joomla.org/Category:IDE_%28Integrated_development_environment%29
[Accessed 14 Nov. 2015].
Drcath.net. (2016). Document Analysis. [Online] Available at: http://www.drcath.net/toolkit/document.html
[Accessed 22 Mar. 2016].
Fowler, M. and Highsmith, J. (2001). The Agile Manifesto. 1st ed. [eBook] Martin Fowler and Jim Highsmith, p.3.
Available at: http://dimsboiv.uqac.ca/8INF851/web/part1/introduction/The_Agile_Manifesto.pdf [Accessed 23 Jan.
2016].
Greenstein, M. and Feinman, T. (2000). Electronic commerce. Boston: Irwin/McGraw-Hill, p.3.
Informit.com. Available at: http://www.informit.com/articles/article.aspx?p=473452&seqNum=5 [Accessed 28 Jan.
2016]. Achieve Software Engineering Best Practices | InformIT. [Online]](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-66-2048.jpg)
![67
Istqbexamcertification.com, (2016). What is RAD model- advantages, disadvantages and when to use it?. [Online]
Available at: http://istqbexamcertification.com/what-is-rad-model-advantages-disadvantages-and-when-to-use-it/
[Accessed 26 Jan. 2016].
Ischool.utexas.edu. (2016). The Case Study as a Research Method. [Online] Available at:
https://www.ischool.utexas.edu/~ssoy/usesusers/l391d1b.htm [Accessed 22 Mar. 2016].
Itinfo.am, (2016). Software Development Methodologies. [Online] Available at: http://www.itinfo.am/eng/software-
development-methodologies/ [Accessed 29 Jan. 2016].
Iwh.on.ca. (2016). Primary data and secondary data | Institute for Work & Health. [Online] Available at:
http://www.iwh.on.ca/wrmb/primary-data-and-secondary-data [Accessed 16 Mar. 2016].
Knowthis.com. (2016). Primary Research - Advantages - KnowThis.com. [Online] Available at:
http://www.knowthis.com/data-collection-primary-research-methods/primary-research-advantages [Accessed 16
Mar. 2016].
Learning, I. (2016). 9. The advantages and disadvantages of questionnaires. [Online] Libweb.surrey.ac.uk.
Available at:
http://libweb.surrey.ac.uk/library/skills/Introduction%20to%20Research%20and%20Managing%20Information%2
0Leicester/page_51.htm [Accessed 21 Mar. 2016].
MacIsaac, B. and Kroll, P. (2006). Unified Process Lifecycle | Leveraging Key Development Principles
Maguire, K., 2013. A Review of User-Interface Design Guidelines for Public Information Kiosk Systems,
Loughborough: HUSAT Research Institute.
Manangi, S., & Chaurasia, P. (2010). Analysis of Security Features in 5 Layer Internet Report. International
Journal on Computer Science and Engineering, 777-781.
Natalya's QA Blog, (2012). The differences between life cycle models- Advantages and Disadvantages. [Online]
Available at: https://narbit.wordpress.com/2012/06/10/the-differences-between-life-cycle-models-advantages-
and-disadvantages/ [Accessed 26 Jan. 2016].
Neil, S. (2009). Electronics:A Systems Approach. 4th ed. Pearson Prentice Hall.
Neil, S. (2009). Electronics:A Systems Approach. 4th ed. Pearson Prentice Hall.
Papazoglou, M. and Ribbers, P. (2006). E-business. Chichester, England: John Wiley, p.129.
Papazoglou, M. and Ribbers, P. (2006). E-business. Chichester, England: John Wiley, p.23.
Pmi.org, (2015). What is Project Management? | Project Management Institute. [Online] Available at:
http://www.pmi.org/About-Us/About-Us-What-is-Project-Management.aspx [Accessed 17 Oct. 2015].
Pinto, J. and Mantel, S. (1990). The causes of project failure. IEEE Transactions on Engineering Management,
37(4), pp.269-276.
2020projectmanagement.com. (2014). What is the critical path?. [online] Available at:
http://2020projectmanagement.com/2014/05/what-is-the-critical-path/ [Accessed 4 Apr. 2016].
Qualitative research methodologies: ethnography. (2016). QUALITATIVE RESEARCH. [Online] Available at:
http://www.allgemeinmedizin.unijena.de/content/education/equip_summer_school/equip_2009/e4100/2008-
010_Reevesetal_Qualitativeresearchmethodologies-ethnography.pdf [Accessed 22 Mar. 2016].](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-67-2048.jpg)
![68
Referenceforbusiness.com,. "Electronic Data Interchange And Electronic Funds Transfer - Organisation, System,
Examples, Advantages, Company, Business, System, History, How Edi Works". N.p., 2016. Web. 8 Jan. 2016.
Schneider, G. (2006). Electronic commerce. Boston, Mass.: Course Technology, p.7.
Scribd, (2015). Ethical Issues in Software Development. [online] Available at:
http://www.scribd.com/doc/10880744/Ethical-Issues-in-Software-Development#scribd [Accessed 15 Oct. 2015].
Schneider, G. (2006). Electronic commerce. Boston, Mass.: Course Technology, p.7.
Smith, S., 1986. Guidelines for Designing User Interface Software, Massachusetts: The MITRE Corporation
Bedford.
Support.office.com. (2016). Manage your project's critical path - Project. [online] Available at:
https://support.office.com/en-ie/article/Manage-your-project-s-critical-path-bc692e65-6245-45cf-86b7-
f7115c965d2f#bm_1 [Accessed 4 Apr. 2016].
W. Boehm, B. (1988). A Spiral Model of Software Development and Enhancement. p.7.
Winter, R. (2016). New Directions in Action Research. [Online] Google Books. Available at:
https://books.google.co.uk/books?hl=en&lr=&id=moeRAgAAQBAJ&oi=fnd&pg=PA9&dq=Reflexive+critique:++Di
alectical+critiue:++Collaborative+resources:++Risk:&ots=AjuzNKrjlP&sig=t3H6tGZw_KcrEg72T01Iy5Ghphs
#v=onepage&q=Reflexive%20critique%3A%20%20Dialectical%20critique%3A%20%20Collaborative%20re
sources%3A%20%20Risk%3A&f=false [Accessed 22 Mar. 2016].
Write.com, (2015). Data Triangulation: How the Triangulation of Data Strengthens Your Research Write.com.
[Online] Available at: http://www.write.com/writing-guides/research-writing/research-process/data-triangulation-
how-the-triangulation-of-data-strengthens-your-research/ [Accessed 14Nov. 2015].
Yin, R. K. (1984). Case study research: Design and methods. Newbury Park, CA: Sage](https://image.slidesharecdn.com/31a86c9a-d31d-4400-8558-c191910df931-161214030252/75/ITX3999-Restaurant-Management-System-Disseration-compressed-1-ilovepdf-compressed-68-2048.jpg)