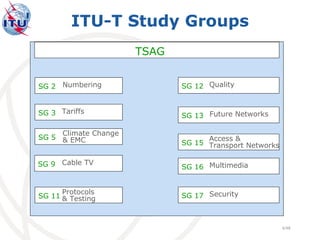
This document summarizes Abbie Barbir's presentation on ITU-T's work regarding privacy and personally identifiable information. ITU-T is an international standards organization that develops standards for information and communication technologies. Several of ITU-T's study groups address issues relating to privacy and security in emerging technologies such as RFID, Internet of Things, and machine-to-machine communication. ITU-T has published recommendations that identify privacy threats and provide guidelines for protecting personally identifiable information in applications using tag-based identification and RFID systems. ITU-T is continuing its work on privacy issues through various study groups and initiatives.







![ITU-T X.1275
Guidelines on protection of personally identifiable information
in the application of RFID technology
Privacy principles (based on privacy principles of: Council of
Europe], EC Directive 95/46, EC Directive 2002/58/EC,
OECD, and UNHCR)
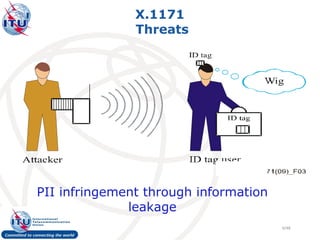
Threats and infringements of PII in RFID
Typical RFID applications and possible threats to PII
Supply-chain management
Transportation and logistics
Healthcare and medical application
e-government
Information service
Guidelines on protection for personally identifiable
information
10/48](https://image.slidesharecdn.com/itu-ics-pii-121019083430-phpapp01/85/Itu-ics-pii-10-320.jpg)