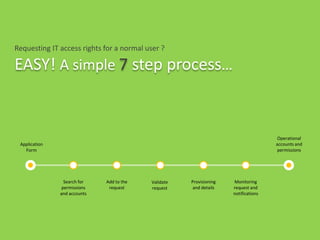
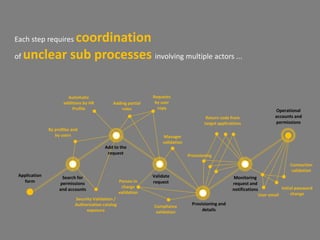
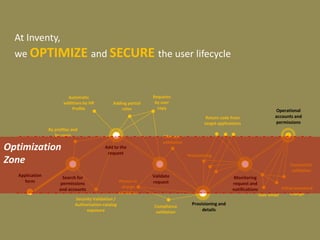
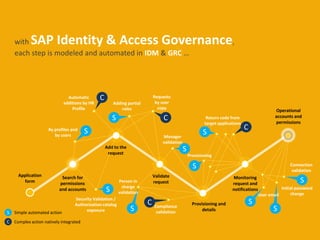
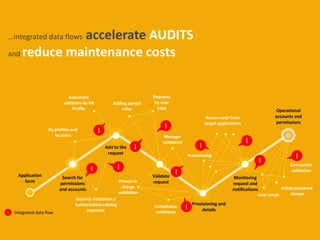
The document discusses optimizing and securing the user lifecycle process through automating steps with SAP Identity & Access Governance. It describes how traditionally the user lifecycle involved many unclear subprocesses and actors for tasks like requesting access, validating requests, and provisioning accounts. With SAP tools, each step can be modeled and automated, with integrated data flows to accelerate audits and reduce costs. The goal is providing a simple, compliant user experience with a low cost process.