iScan Online HIPAA Solutions Brief
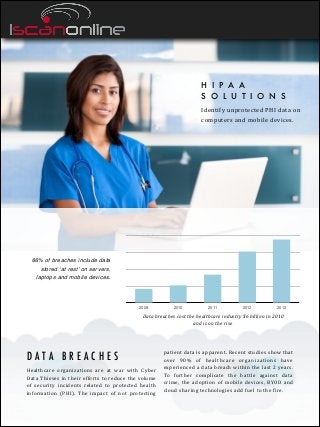
- 1. H I P A A S O L U T I O N S Identify unprotected PHI data on computers and mobile devices. 66% of breaches include data stored ‘at rest’ on servers, laptops and mobile devices. 2009 2010 2011 2012 2013 Data breaches cost the healthcare industry $6 billion in 2010 and is on the rise DATA BREACHES Healthcare organizations are at war with Cyber Data Thieves in their efforts to reduce the volume of security incidents related to protected health information (PHI). The impact of not protecting patient data is apparent. Recent studies show that over 90% of healthcare organizations have experienced a data breach within the last 2 years. To further complicate the battle against data crime, the adoption of mobile devices, BYOD and cloud sharing technologies add fuel to the fire.
- 2. HIPAA COMPLIANCE The HIPAA Security & Privacy Rule includes several safeguards to assure the confidentiality, integrity and availability of electronic protected health information. iScan Online provides security scanning solutions to address the Administrative and Technical safeguards. DATA BREACH SUMMARY PHI DISCOVERY SCAN The number of data breaches and security i n c i d e n t s c o n t i n u e t o r i s e , w i t h H I PA A regulations pushing for transparency. All signs are pointing to 2014 being a critical year for organizations to prevent becoming yet another headline. S c a n y o u r c o m p u t e r a n d m o b i l e d e v i c e s , immediately uncovering unprotected data that is at risk. We include pre-‐defined popular data type discovery for credit card, drivers license, social security numbers and even can add your own sensitive data patterns. Over the past decade we have experienced an explosion of incidents affecting all sizes of healthcare organizations. The end of last year showed no signs of slowing down. HIPAA safeguards explicitly call out an Audit Control standard for implementing a solution that examines information systems containing or using electronic PHI. To better prepare for tomorrow’s threat while aiding in HIPAA compliancy, iScan Online, 1 recently awarded security innovator of the year, has stepped up to the challenge to proactively identify and eliminate PHI related incidents. ISCAN RESPONDS TO HIPAA SAFEGUARDS iScan Online specializes in the identification of u n p ro t e c t e d P H I d a t a a n d v u l n e ra b i l i t i e s , outlined in the Administrative and Technical safeguards to mitigate data loss should a security incident occur. Here at iScan, we call this Data Discovery and Vulnerability Scanning. What’s unique is the fact that we can do this without requiring hardware or complex software and provide healthcare organizations to know exactly what data is at risk within minutes. ! ! ! ! MOBILE AND BYOD To d ay, m o s t h e a l t h c a r e o r g a n i z a t i o n s a r e utilizing smartphones, tablets and computers. Don’t dismiss the mobile threat as it is very real. Mobile risks include traditional vulnerabilities a n d u n p r o t e c t e d s e n s i t i v e d a t a j u s t a s traditional computers do. In fact, mobile devices present new dangers that one might not have previously anticipated. iScan Online is the industry’s first security scanning solution identifying both PHI data and i t s v u l n e ra b i l i t y p o s t u re s i m p l e , fa s t a n d affordable for all of your endpoints including BYOD. QUESTION FOR YOU How important is it for you to know what u n p r o t e c t e d d a t a i s a t r i s k o n y o u r computers, laptops and mobile devices? iScan Online, Inc.! 5600 Tennyson Pkwy, #380! phishing, malware, hacking and Plano, TX 75024! vulnerability exploitation. 19% 19% of breaches include 214-276-1150! www.iscanonline.com 1. SC Magazine awards iScan Online Industry Innovator of the Year - 2013
