1. The document presents Wongyos Keardsri's Ph.D. seminar on an IP address anonymization scheme based on privacy levels.
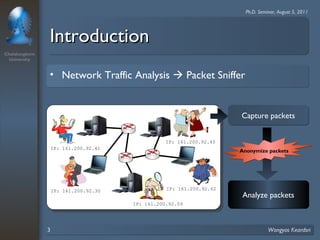
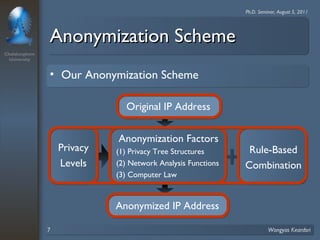
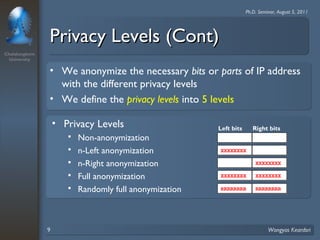
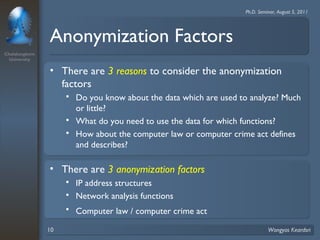
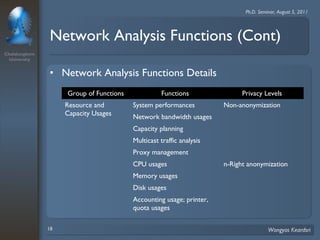
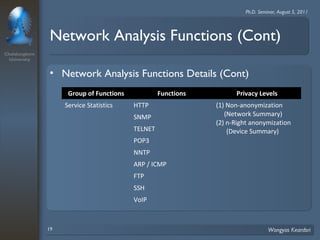
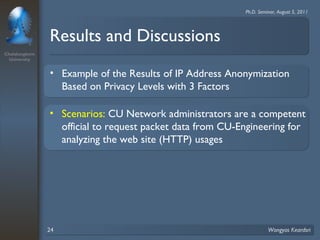
2. The scheme considers privacy levels and three anonymization factors - IP address structures, network analysis functions, and computer law - to determine how to anonymize IP addresses.
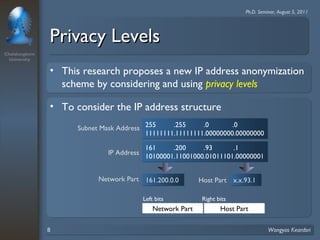
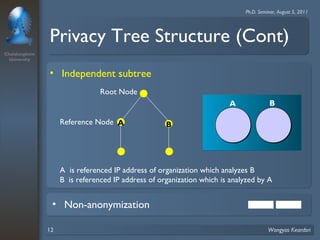
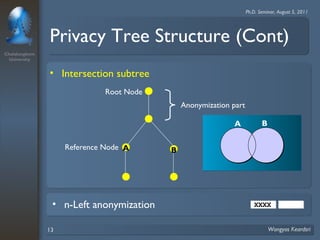
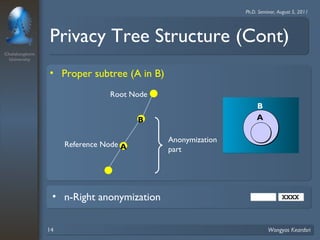
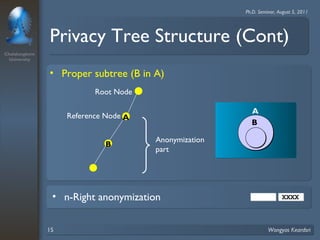
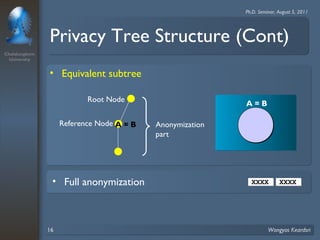
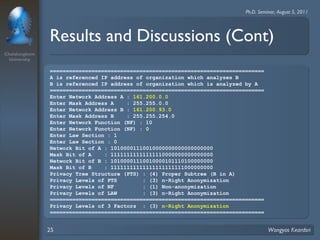
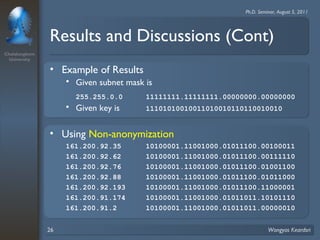
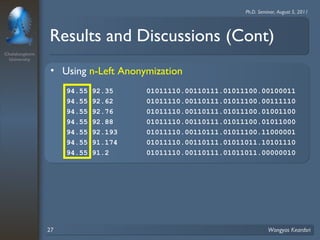
3. Privacy tree structures are used to represent IP address structures and determine appropriate anonymization levels for different parts of IP addresses based on the relationships between addresses.