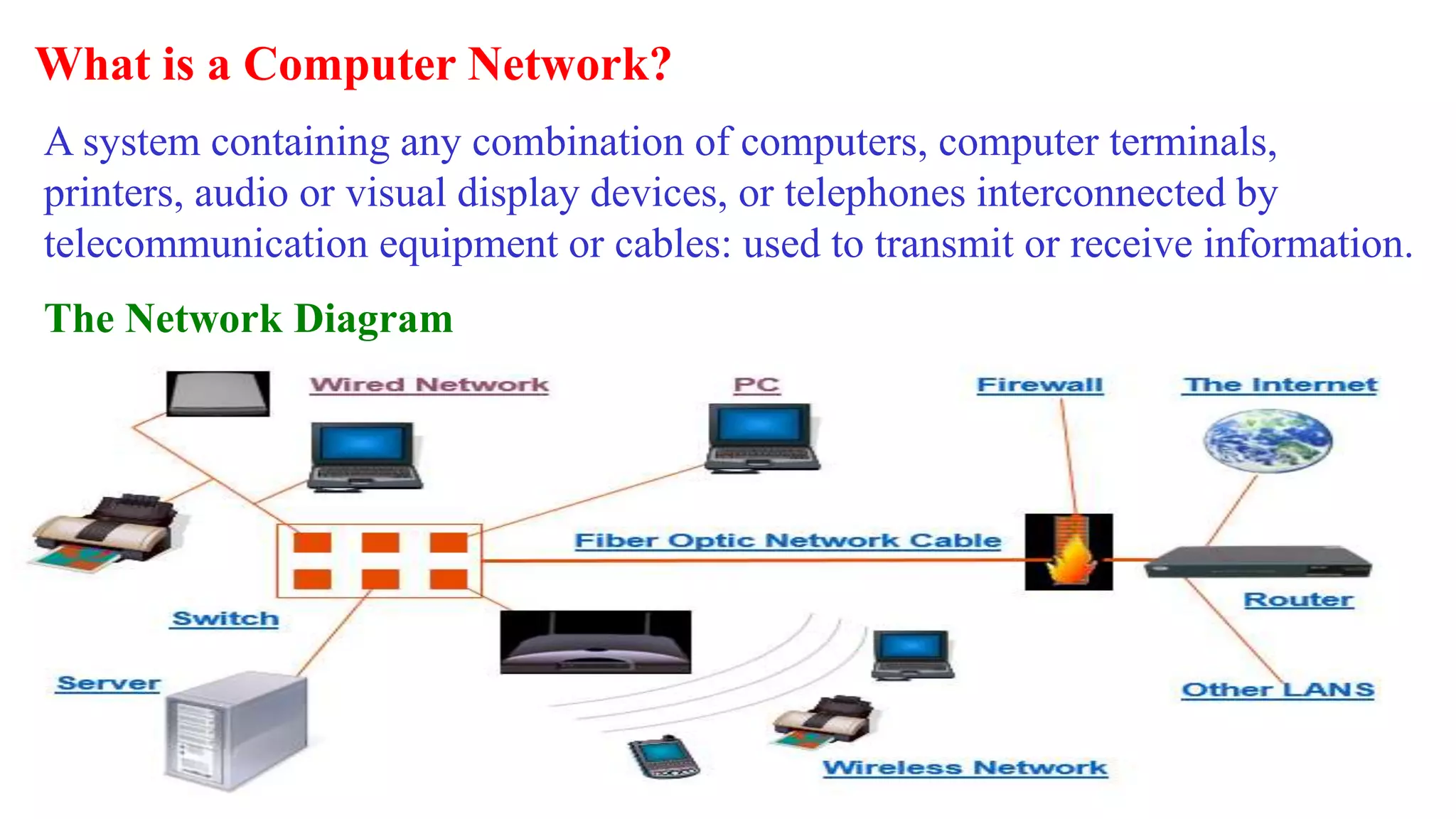
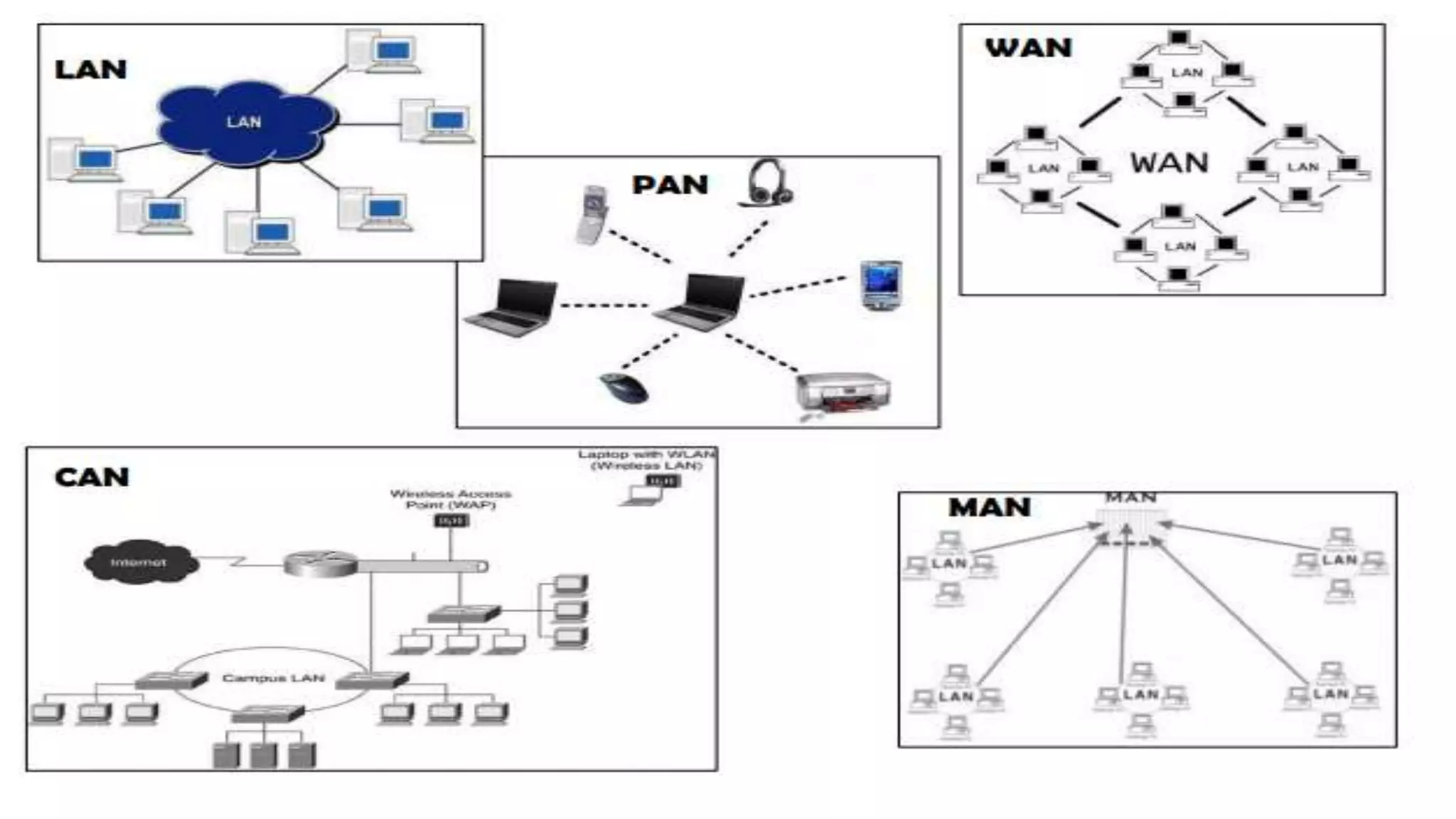
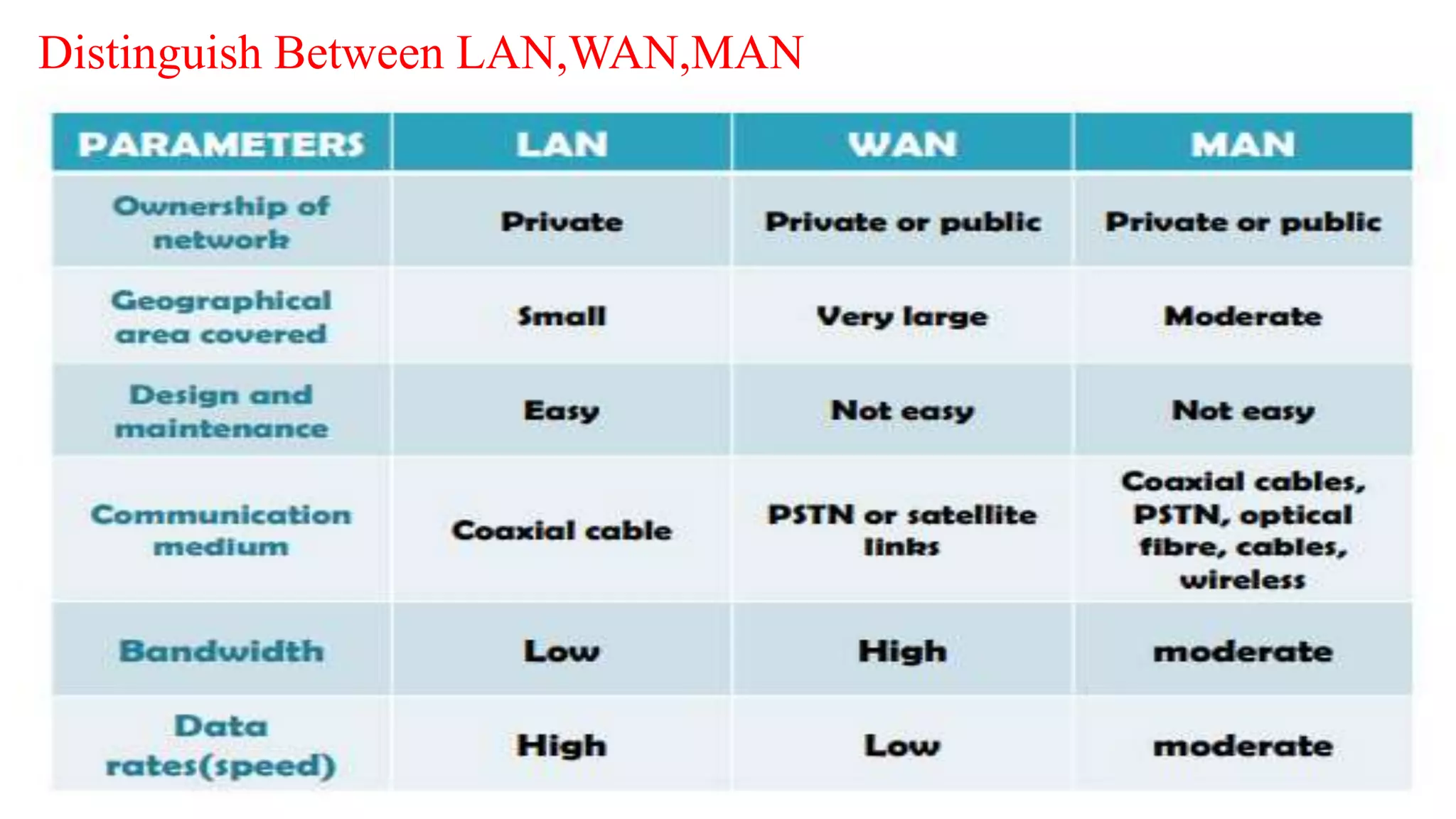
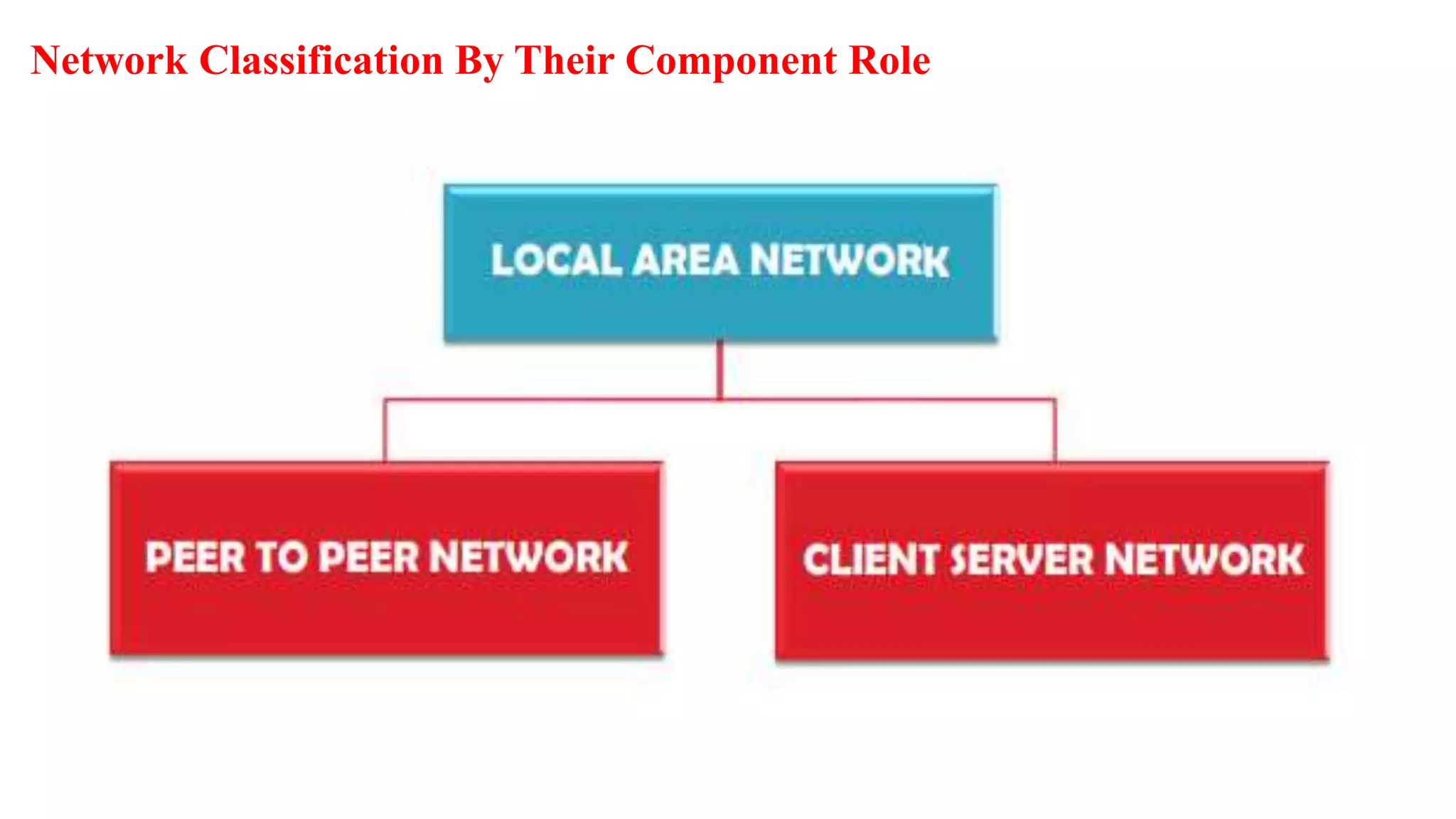
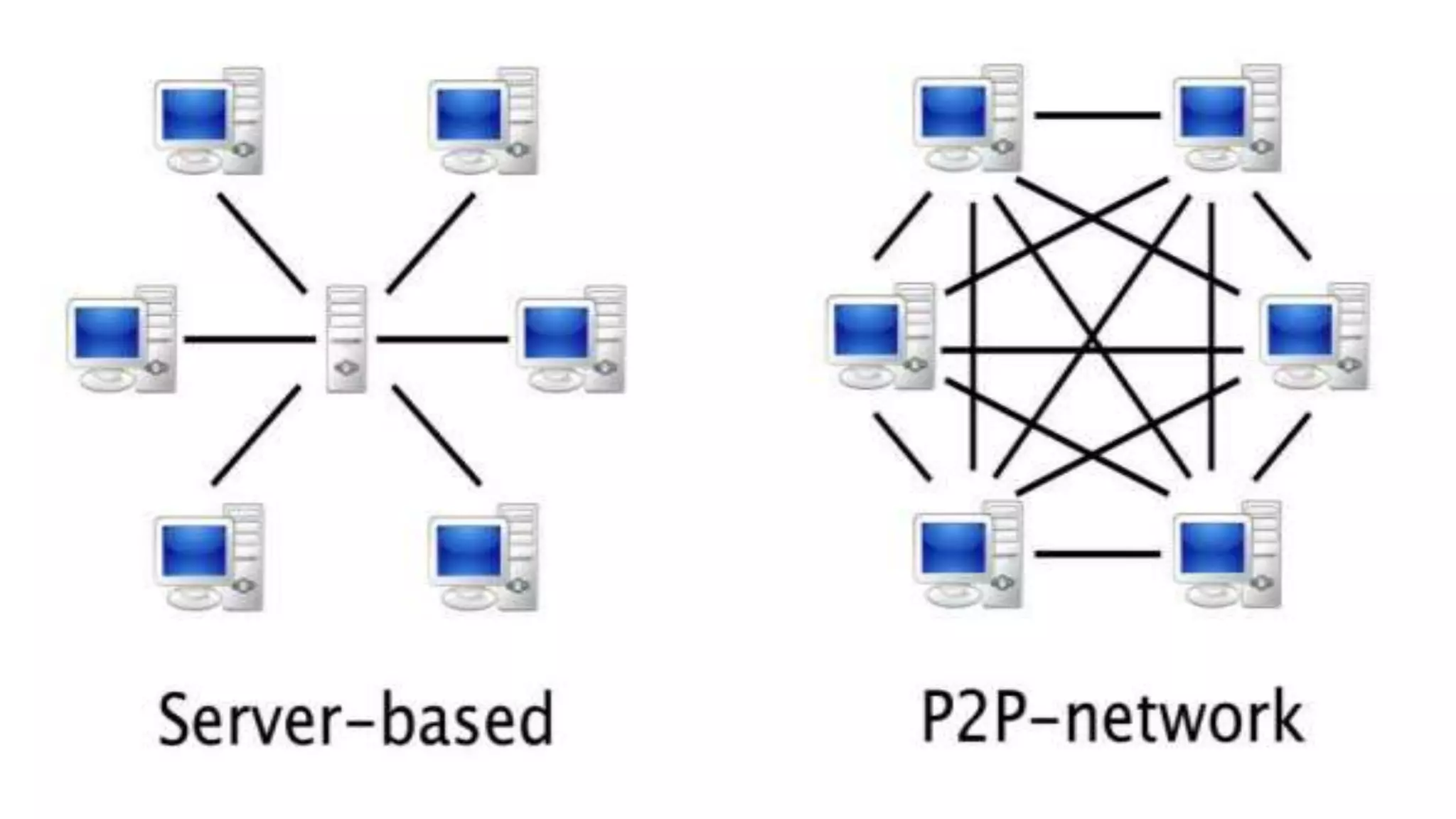
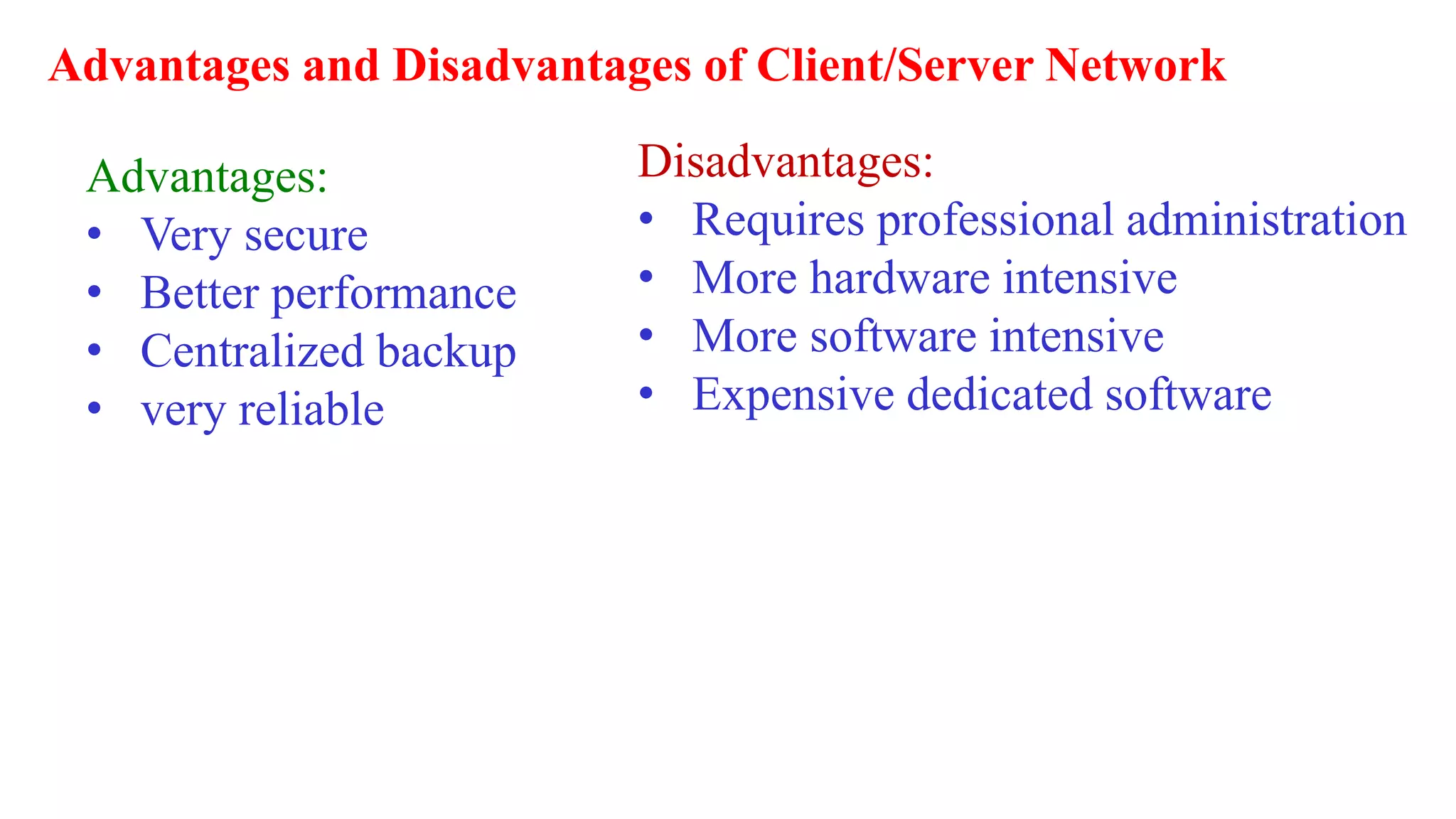
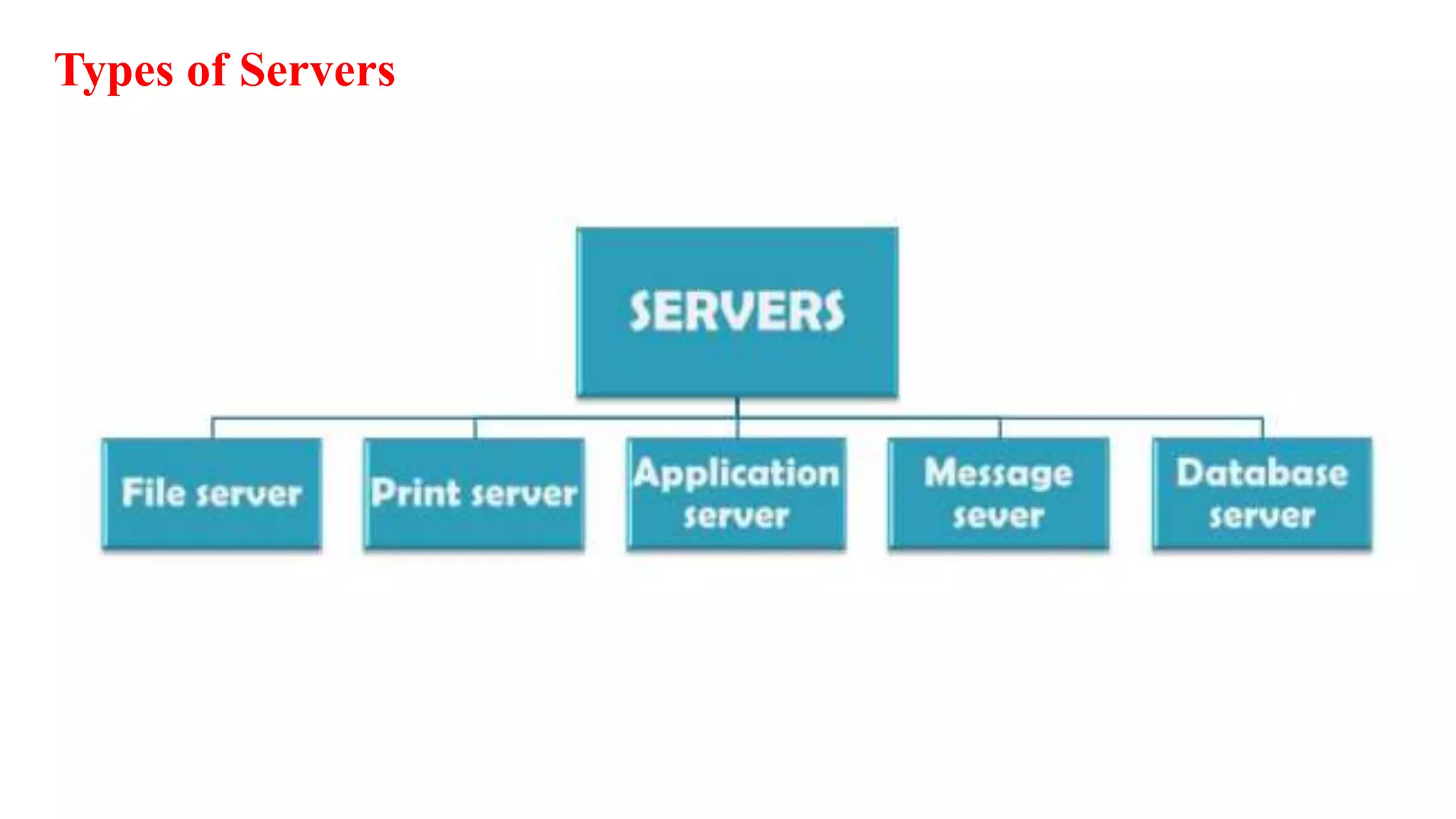
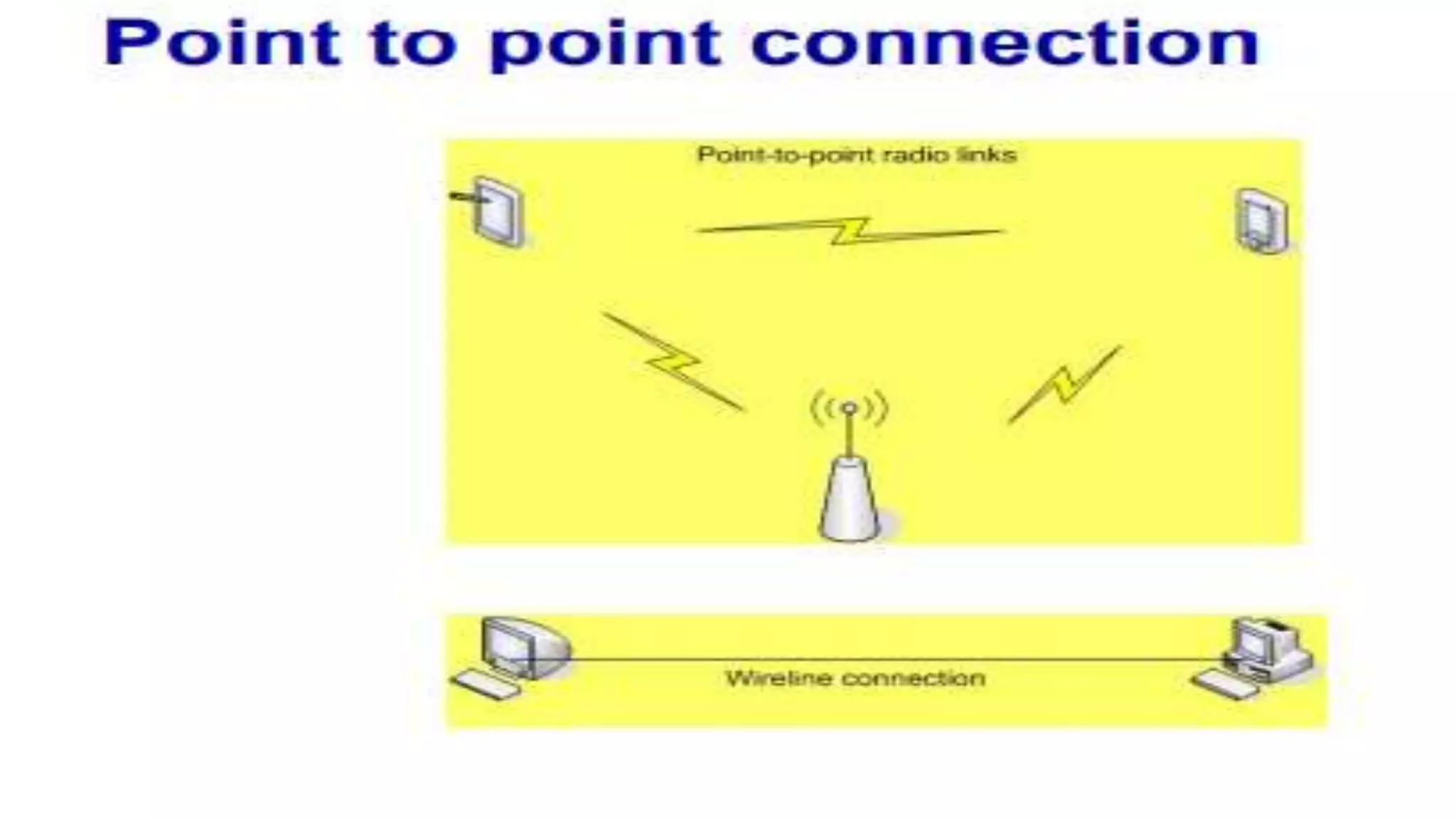
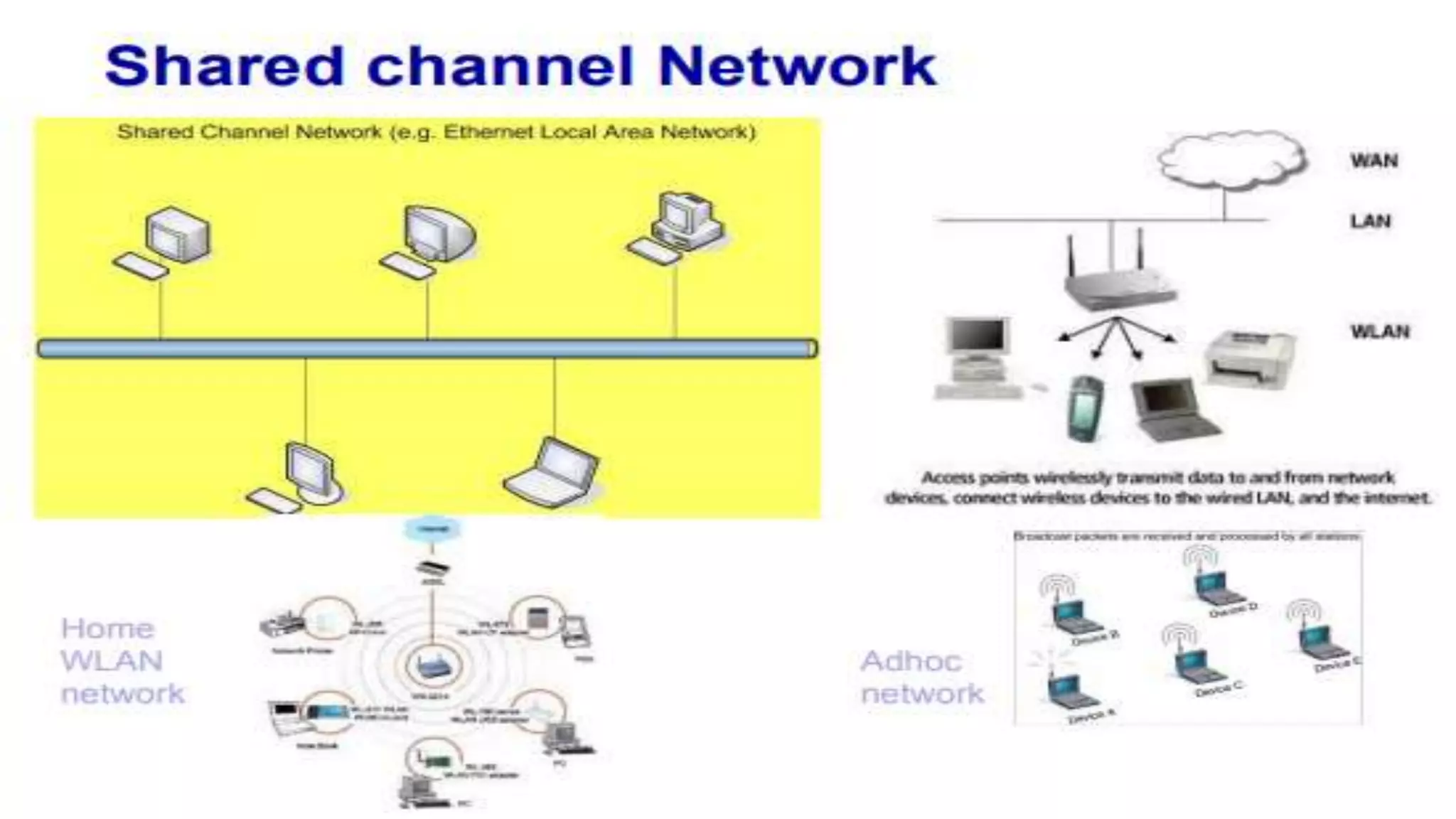
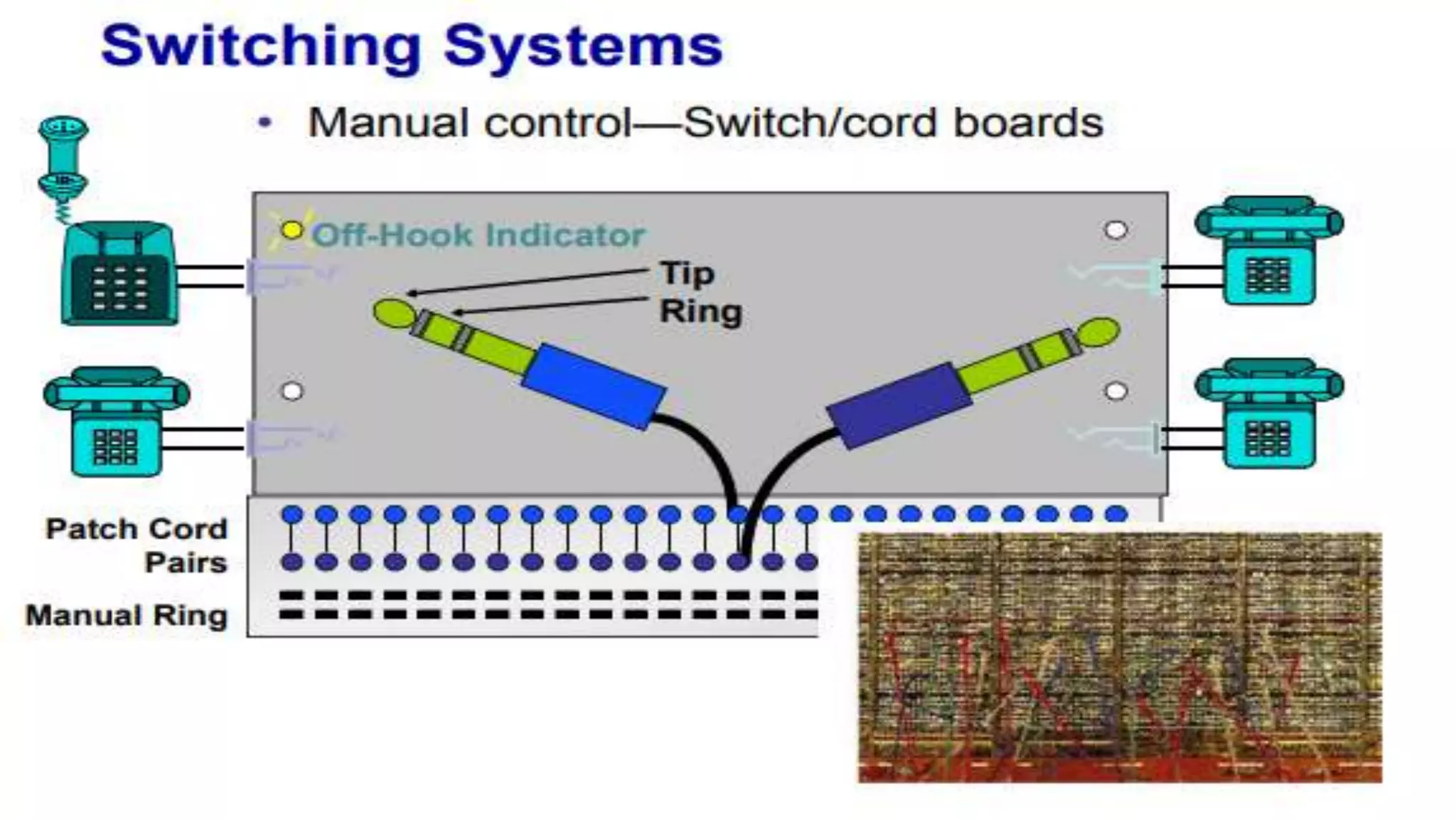
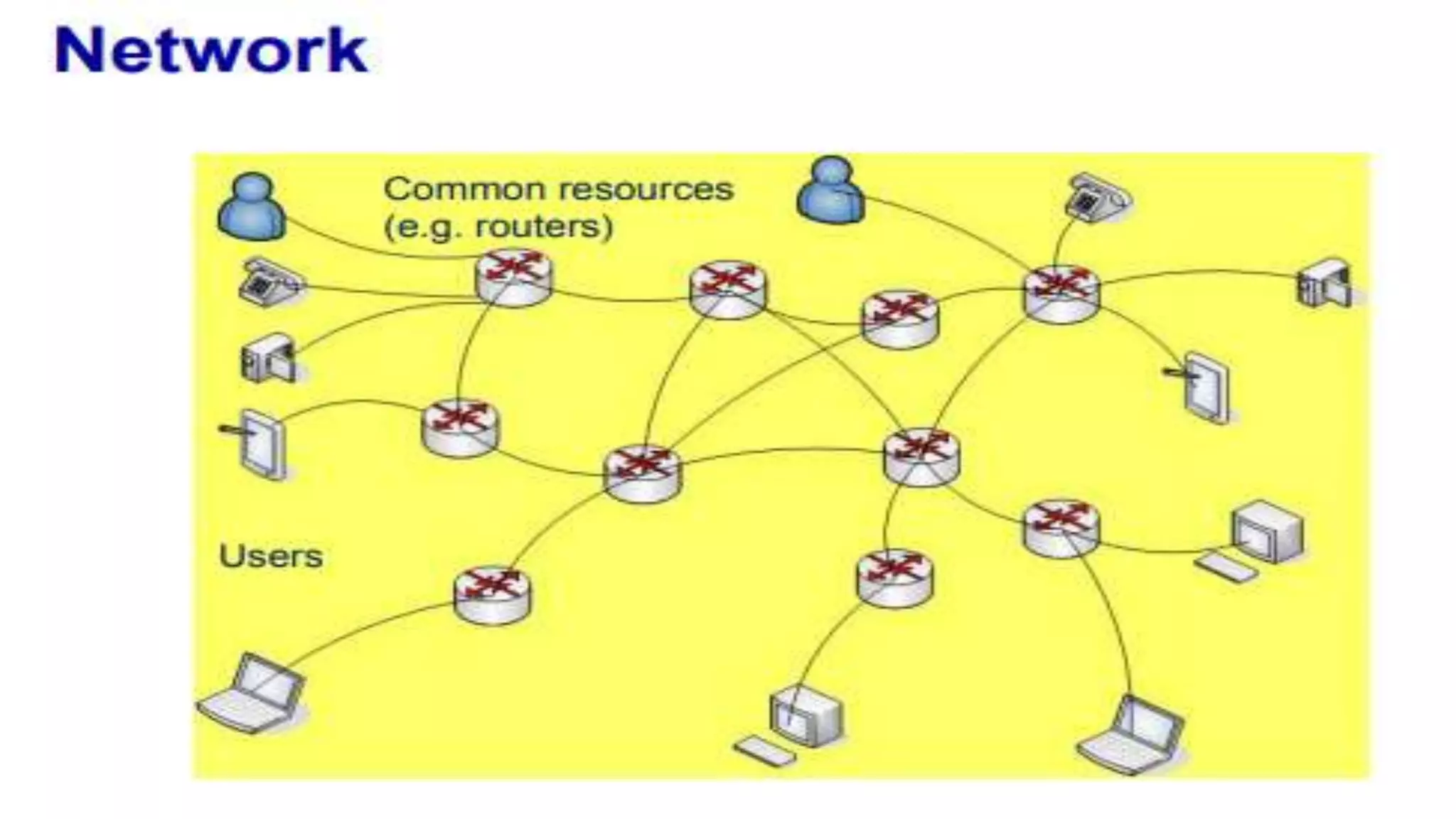
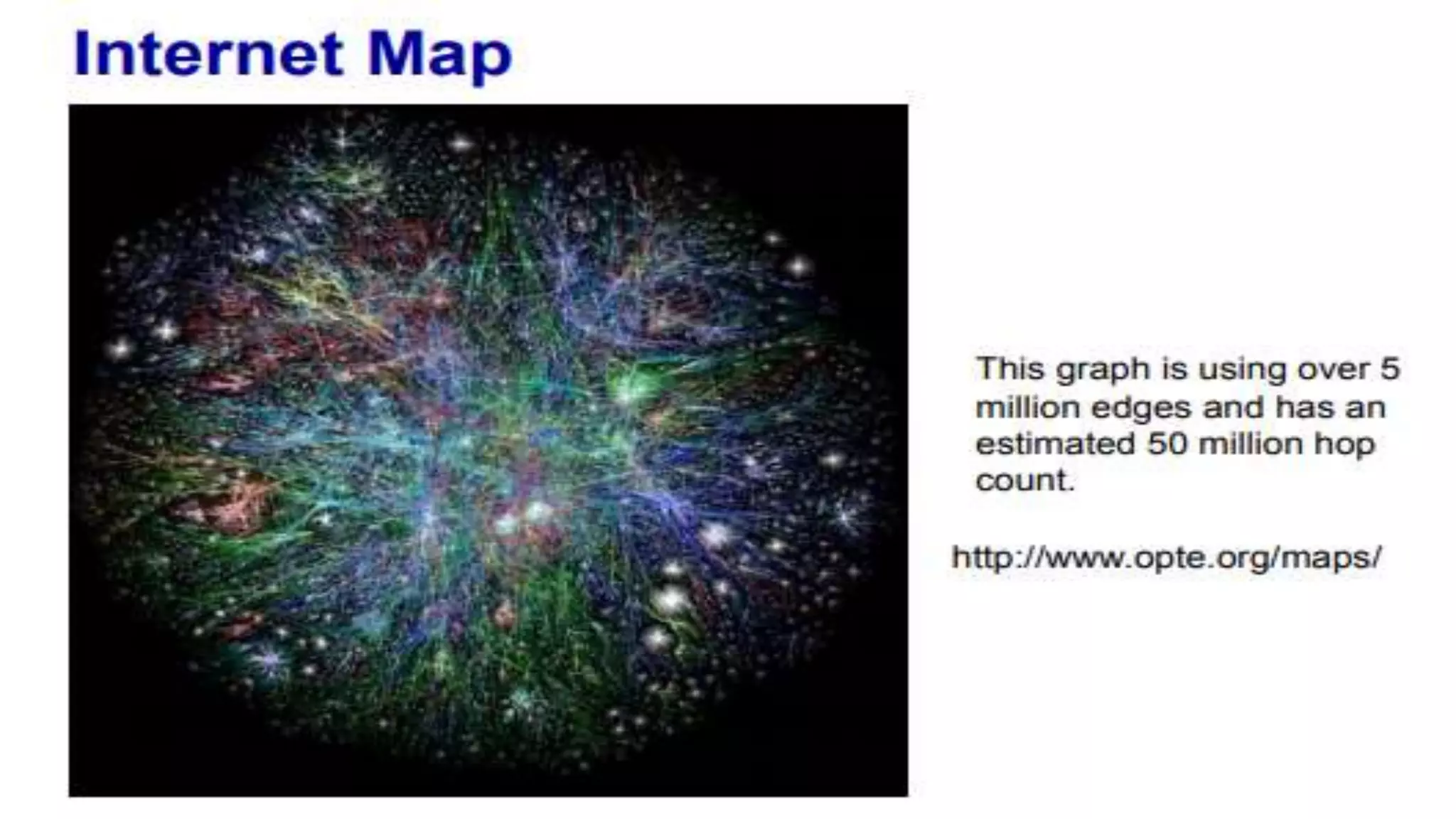
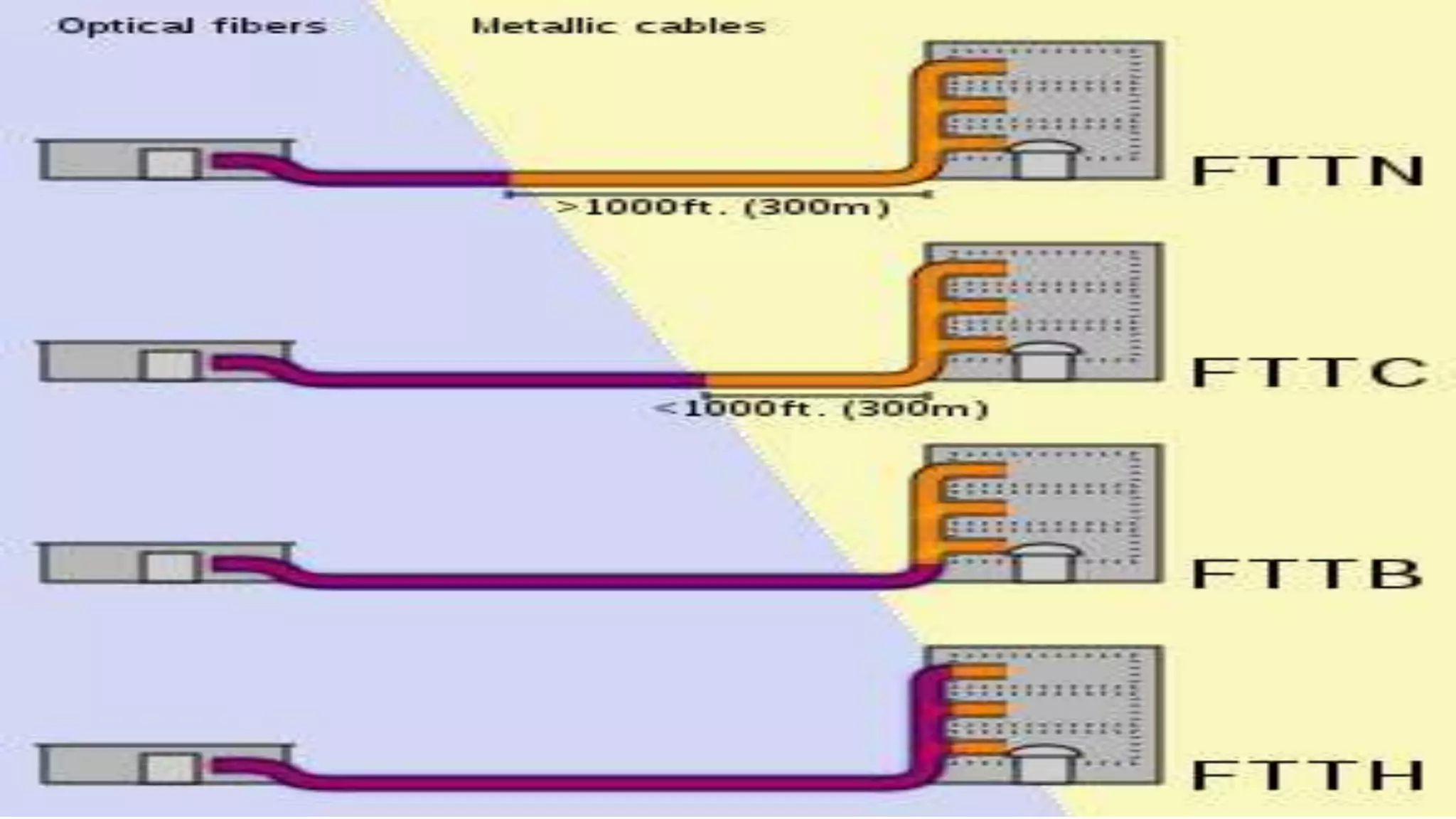
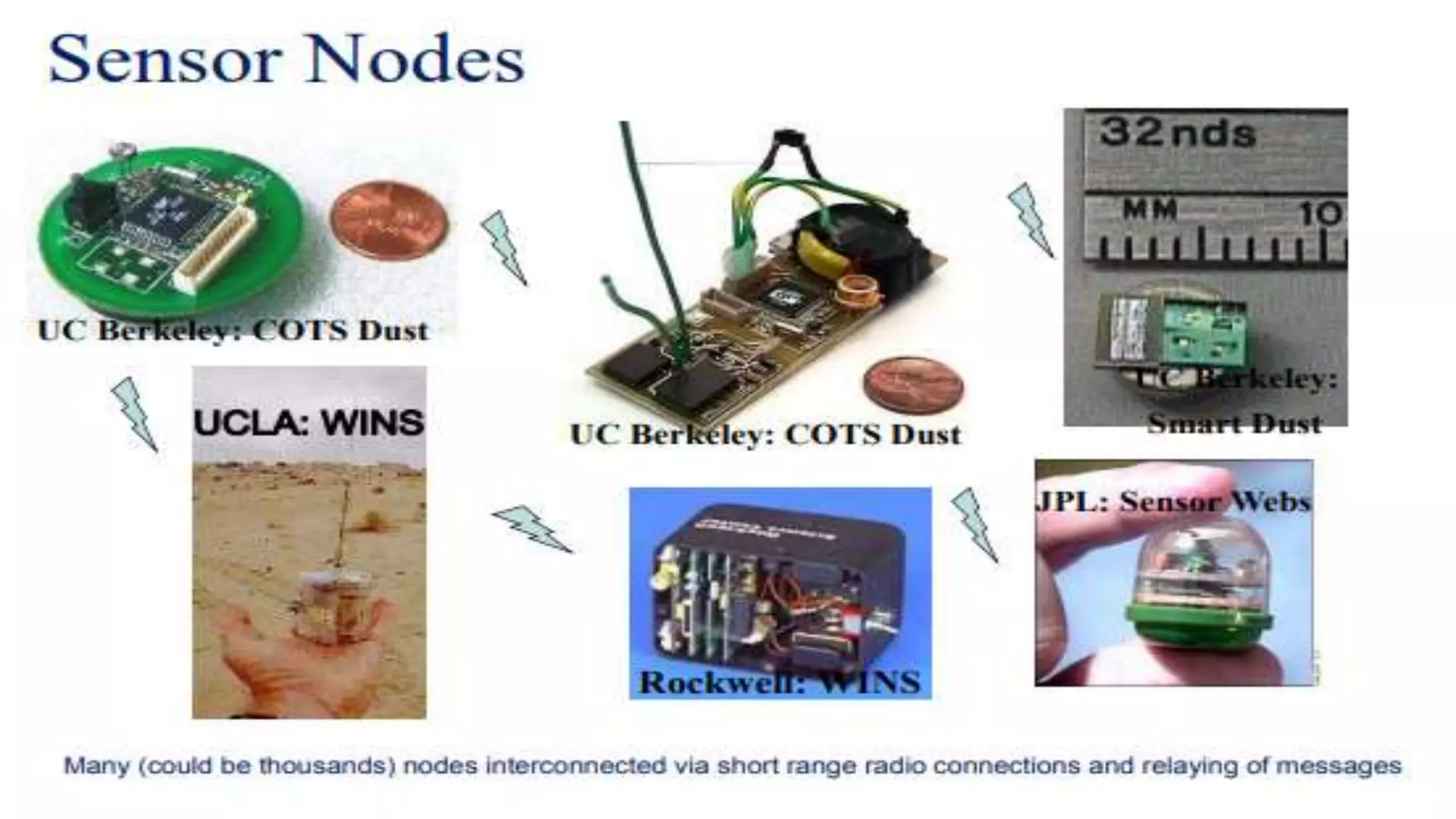
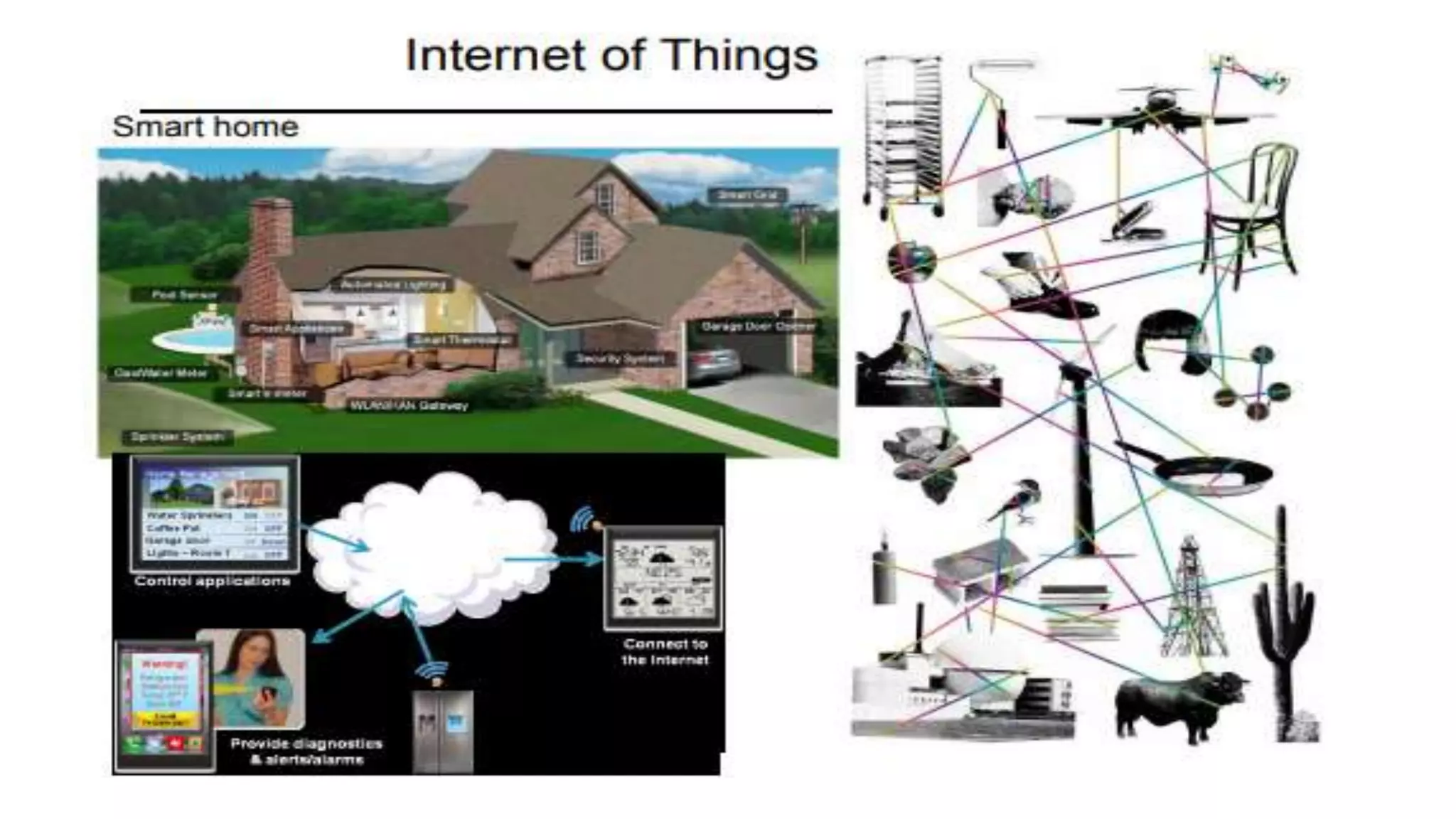
A computer network connects multiple devices together through various communication methods to share resources and information. There are several types of networks including LAN, WAN, MAN, and PAN. In a peer-to-peer network, each computer shares its own resources directly with other computers. In a client-server network, servers centralize resources and services that clients can access. Computer networks allow for sharing of hardware, software, data and provide benefits like increased speed, reduced costs, and improved security and collaboration between users.