This document provides an overview of a tutorial and hands-on session about configuration management using Puppet. The session will cover why configuration management is useful, the Puppet DSL for writing configuration files, how Puppet runs work, using Puppet both with and without a master server, and a hands-on demonstration of setting up NTP with Puppet modules.








![package{„ntp“:
ensure => installed
}
file{„/etc/ntp.conf“:
ensure => present,
user => root,
group => root,
mode => 644,
source => puppet://...,
require => Package[‚ntp‘]
}
service{„ntpd“:
ensure => running,
require => File[‚/etc/ntp.conf‘]
}](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-12-2048.jpg)
![*
before after
without refresh before => Resource[‚name‘] require => Resource[‚name‘]
with refresh notify => Resource[‚name‘] subscribe => Resource[‚name‘]
in our resources
chaining syntax
Resource[‚‘] -> Resource[‚name‘] ~> Resource[‚name‘]](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-13-2048.jpg)

![*
[root@puppet ~]# facter
architecture => x86_64
augeasversion => 0.9.0
bios_release_date => 12/01/2006
bios_vendor => innotek GmbH
bios_version => VirtualBox
blockdevice_sda_model => VBOX HARDDISK
blockdevice_sda_size => 214748364800
blockdevice_sda_vendor => ATA
domain => example.com
facterversion => 1.7.2
filesystems => ext4,iso9660
fqdn => puppet.example.com
hardwareisa => x86_64
hardwaremodel => x86_64
hostname => puppet
id => root
interfaces => eth0,lo
ipaddress => 10.0.2.15
ipaddress_eth0 => 10.0.2.15
ipaddress_lo => 127.0.0.1
is_virtual => true
kernel => Linux](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-17-2048.jpg)



![[root@puppet ~]# puppet help
Usage: puppet <subcommand> [options] <action> [options]
Available subcommands:
agent The puppet agent daemon
apply Apply Puppet manifests locally
cert Manage certificates and requests
master The puppet master daemon
module Creates, installs and searches for modules on the Puppet Forge.
parser Interact directly with the parser.
puppet apply:
• apply manifests locally
• no master needed
• no centralized fileserver
• test
• headless puppet
• no SSL-communication allowed](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-25-2048.jpg)
![[root@puppet ~]# puppet help
Usage: puppet <subcommand> [options] <action> [options]
Available subcommands:
agent The puppet agent daemon
apply Apply Puppet manifests locally
cert Manage certificates and requests
master The puppet master daemon
module Creates, installs and searches for modules on the Puppet Forge.
parser Interact directly with the parser.
puppet master:
• starts https service
• TCP/8140
• internal webserver (ruby)
• scalable (mod_passenger)
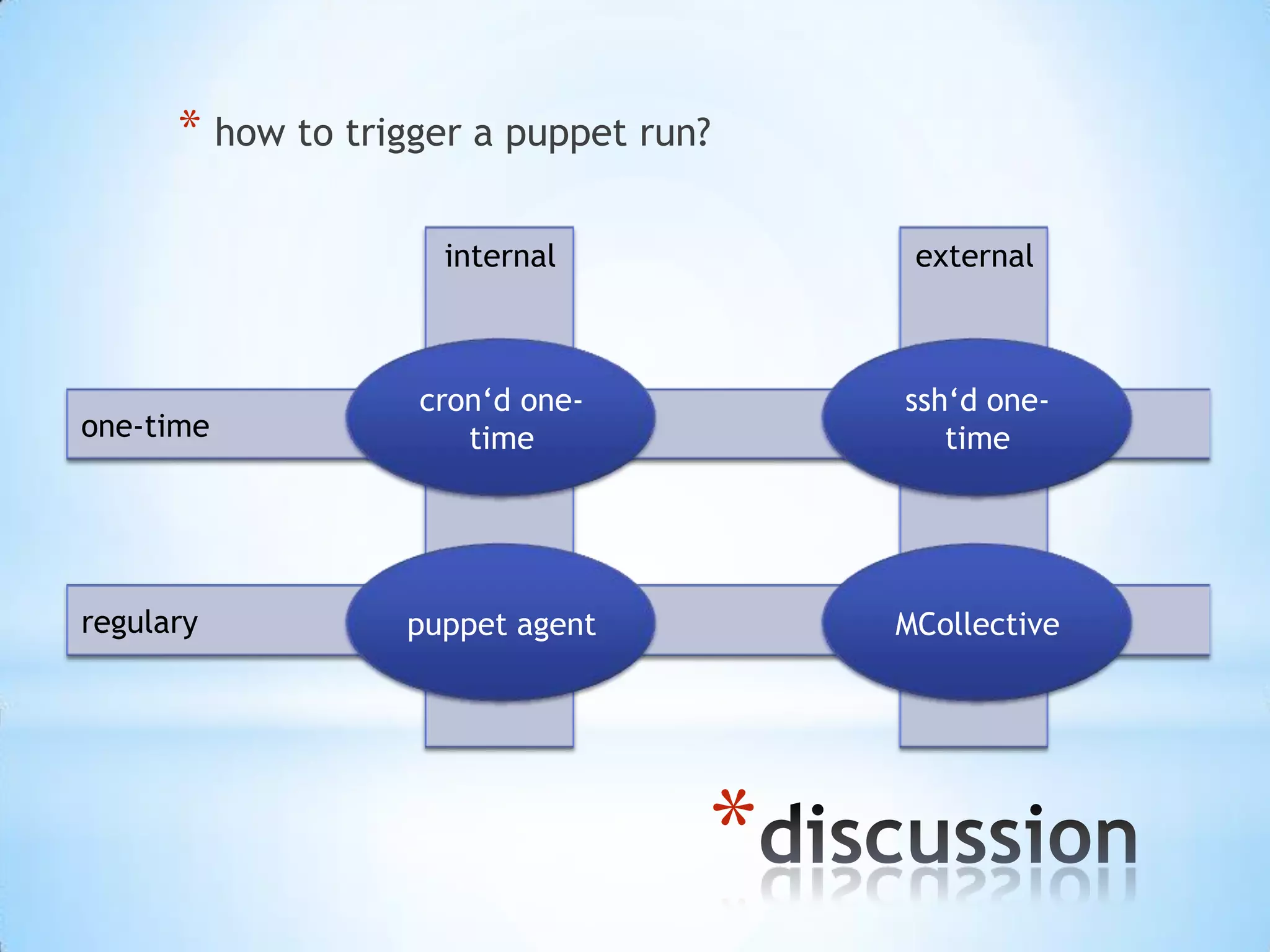
puppet agent:
• manages puppet runs on client
• regularly
• one-time](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-26-2048.jpg)
![[root@puppet ~]# puppet help
Usage: puppet <subcommand> [options] <action> [options]
Available subcommands:
agent The puppet agent daemon
apply Apply Puppet manifests locally
cert Manage certificates and requests
master The puppet master daemon
module Creates, installs and searches for modules on the Puppet Forge.
parser Interact directly with the parser.
puppet module:
• interacts with puppetlabs module repository
puppet parser validate:
• syntax check manifests](https://image.slidesharecdn.com/slides20130303-140311043358-phpapp02/75/Introduction-to-puppet-Hands-on-Session-at-HPI-Potsdam-27-2048.jpg)