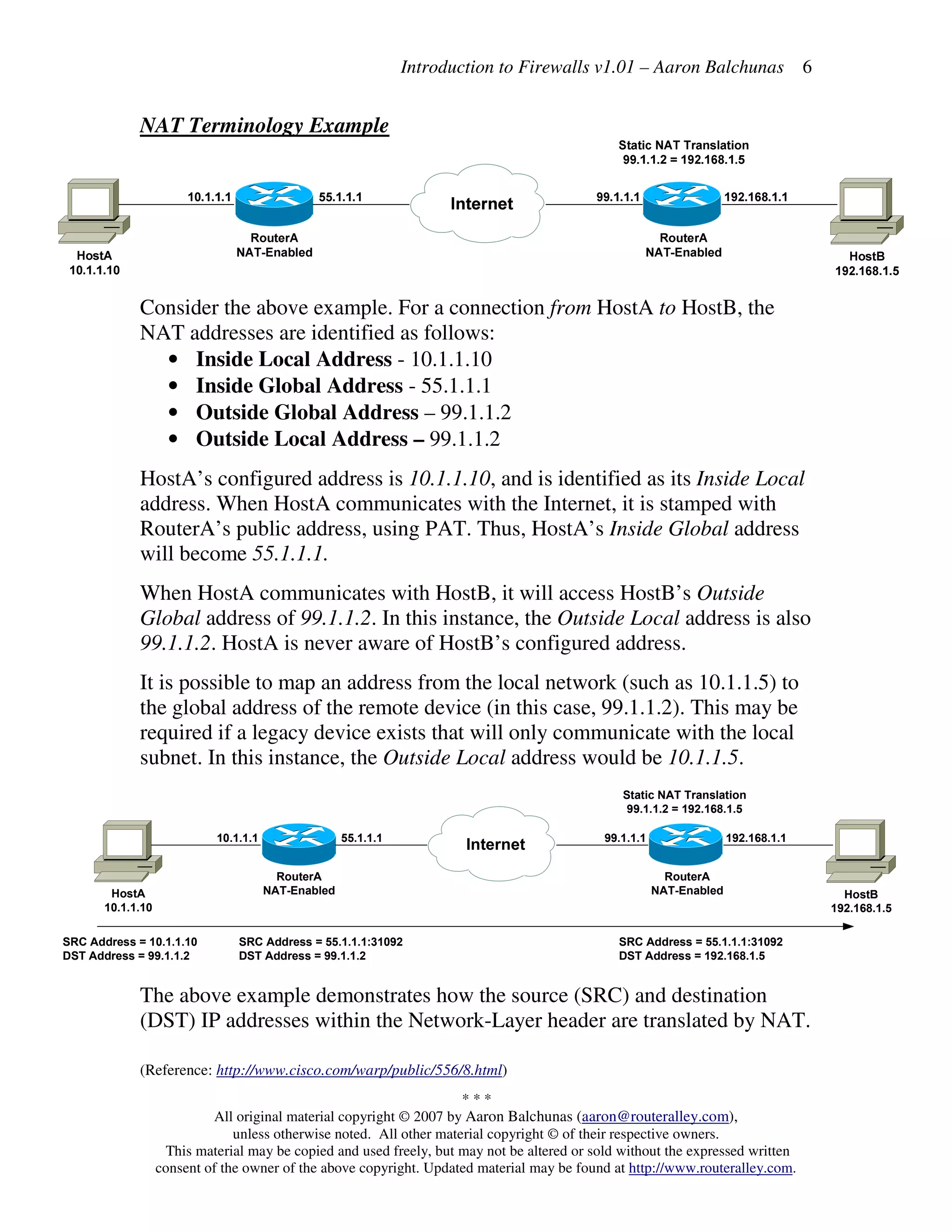
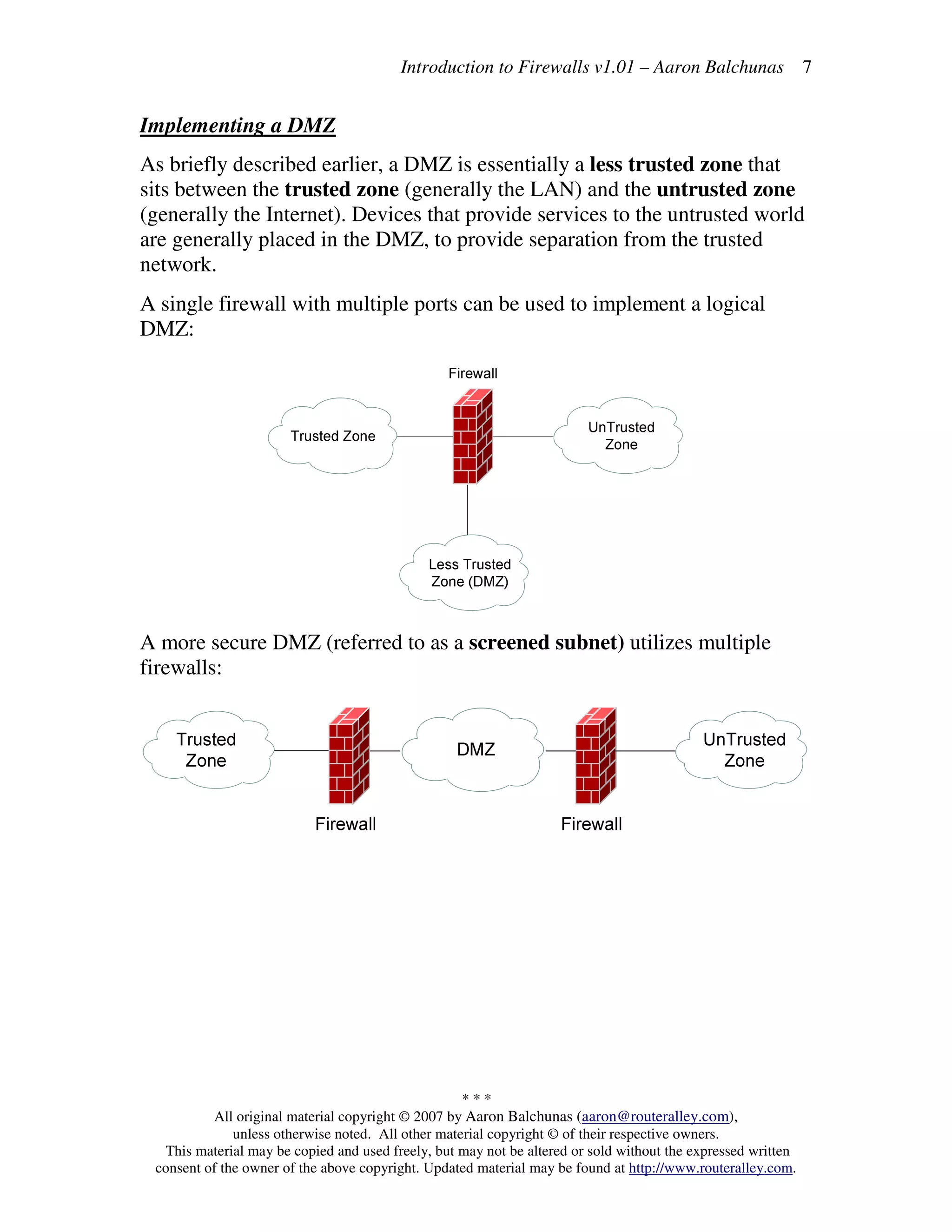
Firewalls filter network traffic between trusted and untrusted zones, allowing traffic into less trusted zones but requiring explicit configuration for traffic to pass from less trusted to more trusted zones. Firewalls perform packet filtering, stateful packet inspection, proxy services, and network address translation. They implement rules to allow or deny traffic based on source/destination addresses and ports.