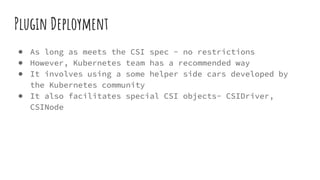
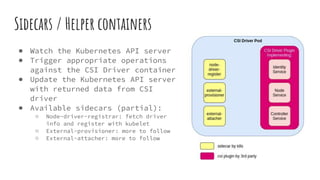
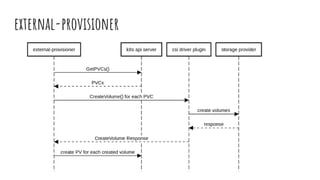
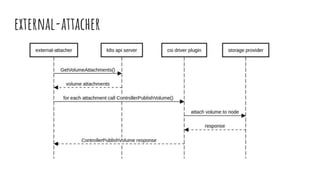
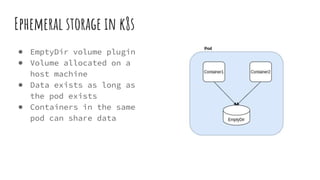
The document provides an overview of stateful and stateless applications in containers, illustrating their differences and the challenges posed by ephemeral storage. It discusses Kubernetes storage solutions, including the use of volume plugins like EmptyDir and EBS for persisting data, along with an introduction to the Container Storage Interface (CSI) and its services. Key points include defining storage classes, persistent volume claims, and the advantages of out-of-tree plugins for better flexibility in managing storage across different orchestrators.








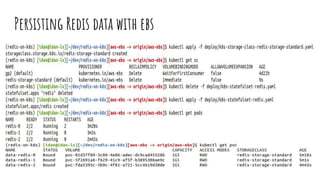
![Deploying Redis
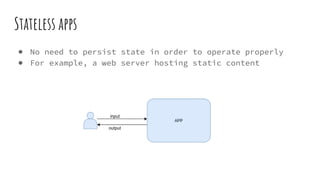
● Redis is an in-memory key-
value store that can
persist data on disk
● We deploy a cluster of 3
redis nodes - 1 master and
2 replicas
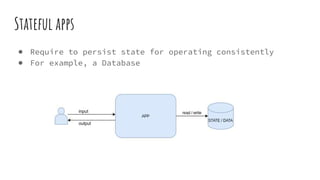
● At first, we use an
EmptyDir volume for
storage
apiVersion: apps/v1
kind: StatefulSet
metadata:
name: redis
…
containers:
- command: [sh, -c, source /redis-
config/init.sh ]
image: redis:4.0.11-alpine
name: redis
ports:
- containerPort: 6379
name: redis
volumeMounts:
- mountPath: /redis-config
name: config
- mountPath: /redis-data
name: data
…..
volumes:
- configMap:
name: redis-config
name: config
- emptyDir: {}
name: data](https://image.slidesharecdn.com/publiccsiintro-motivationoverview-210622211853/85/Introduction-to-Container-Storage-Interface-CSI-12-320.jpg)





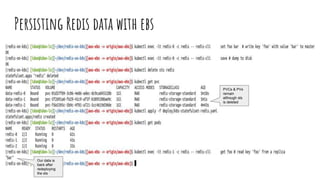
![Persisting Redis data with ebs
apiVersion: apps/v1
kind: StatefulSet
metadata:
name: redis
...
volumeMounts:
- mountPath: /redis-data
name: data
...
volumeClaimTemplates:
- metadata:
name: data
spec:
accessModes: [ "ReadWriteOnce" ]
storageClassName: "redis-storage-standard"
resources:
requests:
storage: 1Gi](https://image.slidesharecdn.com/publiccsiintro-motivationoverview-210622211853/85/Introduction-to-Container-Storage-Interface-CSI-18-320.jpg)