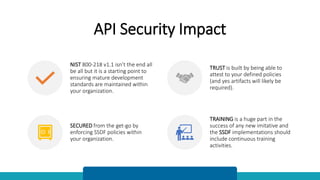
The document discusses the Secure Software Development Framework (SSDF) developed by NIST, focusing on practices for mitigating software vulnerabilities during development. It outlines key areas such as preparing the organization, protecting software, producing secure software, and responding to vulnerabilities, while emphasizing the importance of communication and training. Finally, it highlights the need for organizations to adapt their practices to align with the SSDF to build trust and ensure API security.

![What is the
SSDF?
• Secure Software Development
Framework – Recommendations for
Mitigating the Risk of Software
Vulnerabilities. *(In the Development
Environment)
• When we think about API security
often, we think about testing the APIs
with application penetration and other
static/dynamic testing techniques and
much more.
• We need to shift [insert direction] with
our focus and apply practices with
policies using the SSDF.
• Say Hello to the NIST 800-218.](https://image.slidesharecdn.com/sr-ssdf-2023-deck1-230711072246-1fa99240/85/INTERFACE-by-apidays-2023-Secure-Software-Development-Framework-SSDF-API-Security-Bill-Jones-Softrams-4-320.jpg)