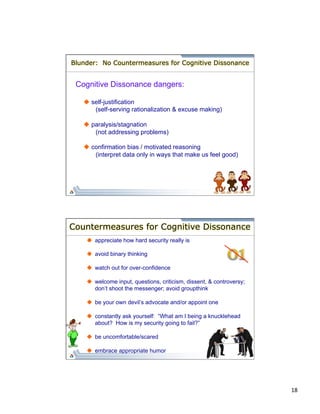
This document summarizes Roger Johnston's talk on under-utilized methods for mitigating the insider threat. Johnston discusses improving security culture and climate by welcoming security ideas from all employees and viewing vulnerabilities as opportunities. He also outlines examples of largely unstudied human factors in security like security awareness training, insider threat motivation and countermeasures, and mitigating employee disgruntlement. The document advocates applying insights from psychology, such as reducing cognitive dissonance, to strengthen security practices against both inadvertent and deliberate insider threats.