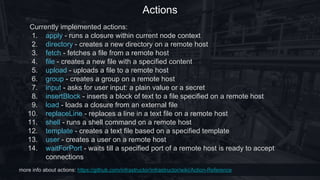
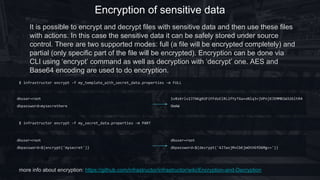
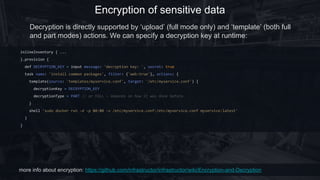
Infrastructor is an open-source infrastructure as code framework that utilizes Groovy to manage and provision Unix-based hosts. It supports various inventory methods, including inline, AWS, and Docker inventories, allowing flexible task execution with minimal host-side dependencies. The framework includes capabilities for encrypting sensitive data, executing commands on remote hosts, and defining provisioning plans with filtering and parallel execution options.


![Introduction: an example
inlineInventory { // define an inventory
node host: '10.0.0.10', port: 22, username: 'devops', keyfile: 'devops/private.key'
}.provision { // define a provisioning plan
task('install common packages') { // define a task - a group of actions to run on each inventory node
shell sudo: true, command: 'apt update'
['tmux', 'mc', 'htop'].each {
shell "sudo apt install $it -y"
}
}
}
~ $ infrustructor run -f example.groovy
A provisioning script usually consists of two main parts:
1. An inventory definition - a set of nodes (servers, VMs) you want to provision
2. A provisioning plan definition - which actions to run on the nodes
There is no limitation on inventory and provisioning plan number a single script can
contain
A provisioning script can be executed using infrastructor command line interface:](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-3-320.jpg)
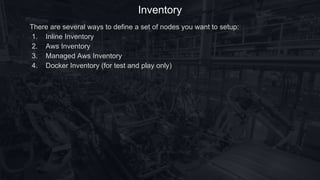
![Inline Inventory
inlineInventory {
node host: '10.0.0.10', port: 22, username: 'devops', keyfile: 'devops/private.key', tags: [db: true, env: 'test']
node host: '10.0.0.11', port: 22, username: 'devops', keyfile: 'devops/private.key', tags: [db: true, env: 'live']
['10.0.1.10', '10.0.1.11', '10.0.1.12'].each { ip ->
node(host: ip, port: 22) {
username = 'devops'
keyfile = 'devops/private.key'
tags = [service: true, env: 'live']
}
}
}.provision {
// some tasks here
}
Inline Inventory defines a set of nodes in the same file where a provisioning plan is
defined. You can use loops and other Groovy tricks to organize the definition:](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-5-320.jpg)
![Aws Inventory
awsInventory(AWS_ACCESS_KEY_ID, AWS_ACCESS_SECRET_KEY, AWS_REGION) {
username = 'devops'
keyfile = 'devops/private.key'
tags = [managed: 'true'] // each AWS instance with tag 'managed:true' will be added to the inventory
usePublicIp = true
}.provision {
task('print all nodes') {
info "$it.id: $it.host" // let’s print all nodes from the inventory
}
}
Aws Inventory can read a set of EC2 instances from AWS and convert it to a set of
nodes. A provisioning plan will be applied to this set of nodes (i.e. EC2 instances):
$ infrastructor run -f aws_example.groovy -v AWS_ACCESS_KEY_ID="XXXXXX" -v AWS_SECRET_KEY_ID="YYYYYY" -v AWS_REGION="eu-central-1"](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-6-320.jpg)
![Managed Aws Inventory: EC2 support
managedAwsInventory(AWS_ACCESS_KEY_ID, AWS_SECRET_KEY_ID, AWS_REGION) {
ec2(tags: [managed: true], parallel: 2) { // all EC2 instances with the tag 'managed:true' will be considered as existing nodes
(1..5).each {
node(name: "aws-node-$it") {
imageId = 'ami-12345678'
instanceType = 't2.small'
subnetId = 'sb-12345678'
securityGroupIds = ['sg-00000001', 'sg-00000002']
keyName = 'devops_private_key'
username = 'devops'
keyfile = 'devops/devops.key'
}
}
}
}.provision { ... }
With Managed Aws Inventory we can define a target state of inventory. Infrastructor
will create, update and remove EC2 instances to reach the target state:
$ infrastructor run -f aws_example.groovy -v AWS_ACCESS_KEY_ID="XXXXXX" -v AWS_SECRET_KEY_ID="YYYYYY" -v AWS_REGION="eu-central-1"](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-7-320.jpg)
![Managed Aws Inventory: Route53 support
managedAwsInventory(AWS_ACCESS_KEY_ID, AWS_SECRET_KEY_ID, AWS_REGION) {
ec2(tags: [managed: true]) {
node(name: 'web-host-1', tags: ['front-server': true]) { ... }
node(name: 'web-host-2', tags: ['front-server': true]) { ... }
}
route53(hostedZoneId: 'ZZZZZZZZZZZZZZ') {
recordSet(type: 'A', name: 'myservice.infrastructor.io') {
ttl = 600 // seconds
resources = {'front-server:true'} // IPs of instances with tag 'front-server:true' will be added to the record set
usePublicIp = true
}
}
}.provision { ... }
There is an initial support for AWS Route53. Infrasrtuctor can automatically create,
update and remove DNS records in accordance to the current inventory state:
$ infrastructor run -f route53_example.groovy](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-8-320.jpg)
![Docker Inventory
def inventory = inlineDockerInventory { // random ports and container ids will be used
node image: 'infrastructor/ubuntu-sshd', tags: [os: 'ubuntu'], username: 'root', password: 'infra'
node image: 'infrastructor/centos-sshd', tags: [os: 'centos'], username: 'devops', password: 'devops'
}.provision {
task(parallel: 2) { shell command: "apt update" }
task(filter: {'os:ubuntu'}) { shell command: "apt install tmux -y" }
task(filter: {'os:centos'}) { shell command: "apt install htop -y" }
}
inventory.shutdown()
Docker Inventory might be useful for some preliminary testing: then you want to
check your provisioning plan quickly:
$ infrastructor run -f docker_inventory_example.groovy](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-9-320.jpg)
![Provisioning Plan
inlineInventory { ...
}.provision {
task(name: 'install common packages', tags: {'db:true' || 'web:true'}, parallel: 2) {
shell 'sudo apt install docker.io -y'
}
task(name: 'install MySQL', tags: {'db:true'}) {
shell "sudo docker run -d -p 3306:3306 -e MYSQL_ROOT_PASSWORD=$MYSQL_ROOT_PASSWORD mysql:latest"
}
task(name: 'install My Service', tags: {'web:true'}) {
template(source: 'templates/myservice.conf', target: '/etc/myservice.conf') {
bindings = [dbhost: 'storage.internal.infrastructor.io', dbport: 3306, dbuser: 'root', dbpassword: MYSQL_ROOT_PASSWORD]
}
shell 'sudo docker run -d -p 80:80 -v /etc/myservice.conf:/etc/myservice.conf myservice:latest'
}
}.provision { ... }
$ infrastructor run -f provisioning_plan_example.groovy -v MYSQL_ROOT_PASSWORD=XXXXX
A provisioning plan consists of a list of tasks which are executed one by one. It is
possible to define several provisioning plans for the same inventory in a single file:](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-10-320.jpg)
![Provisioning Plan: Tasks
inlineInventory {
node id: 'database', host: '10.0.0.10', tags: [db: true, priority: 1], username: 'devops', keyfile: 'devops/private.key'
node id: 'service', host: '10.0.0.11', tags: [service: true, priority: 2], username: 'devops', keyfile: 'devops/private.key'
node id: 'gateway', host: '10.0.0.12', tags: [loadbalancer: true, priority: 1], username: 'devops', keyfile: 'devops/private.key'
...
}.provision {
task(name: 'install common packages', filter: {'db:true' || (!'service:true' || !'priority:2')}, parallel: 2) {
shell 'sudo apt install htop tmux mc -y'
}
...
}
A task definition usually consists of:
1. A human readable task name
2. A filtering expression to define a subset of nodes to run actions on
3. A level of parallelism - amount of nodes to provision in parallel
4. A list of actions to run on the nodes](https://image.slidesharecdn.com/infrastructor-170716135106/85/Bring-your-infrastructure-under-control-with-Infrastructor-11-320.jpg)