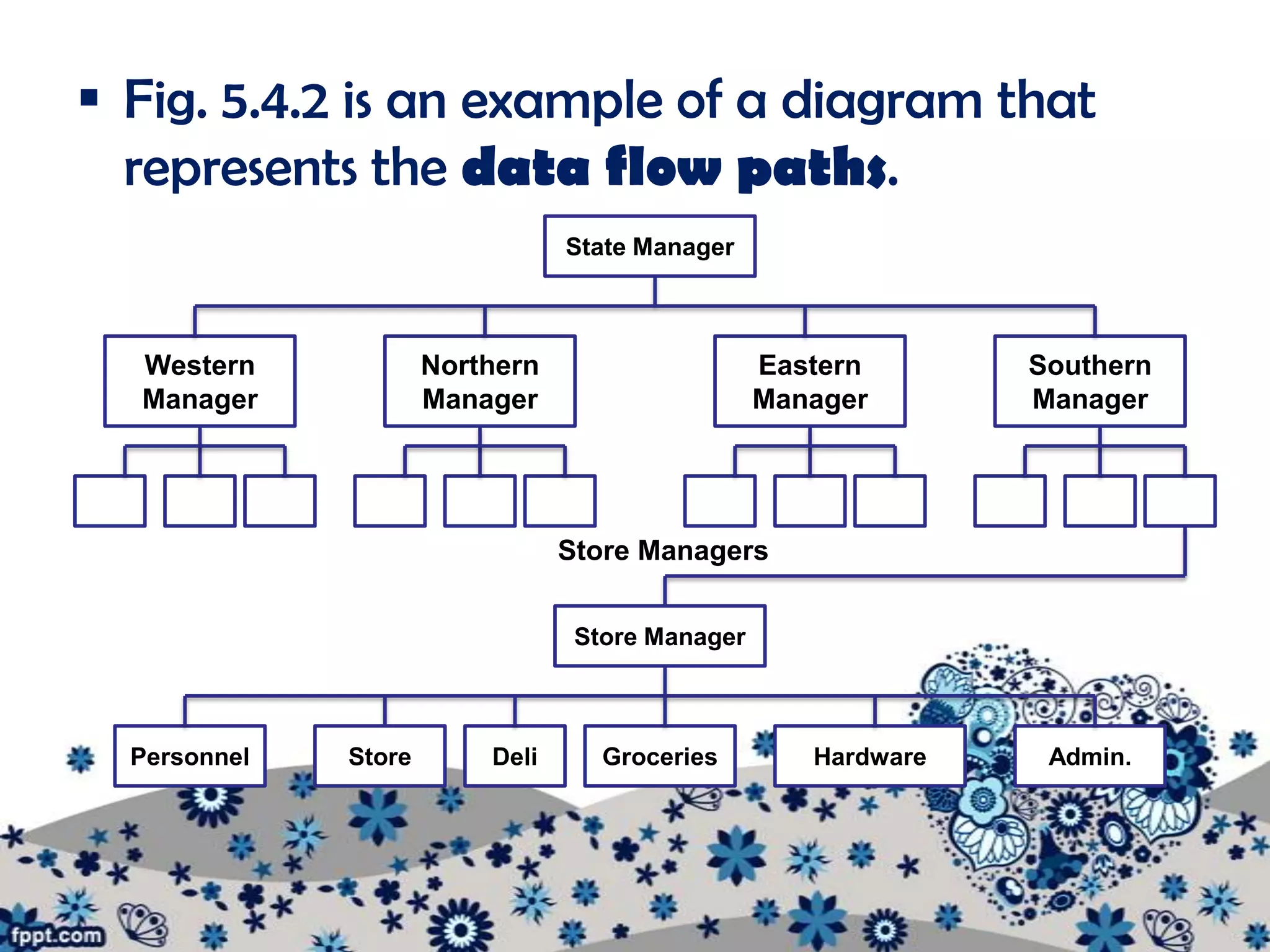
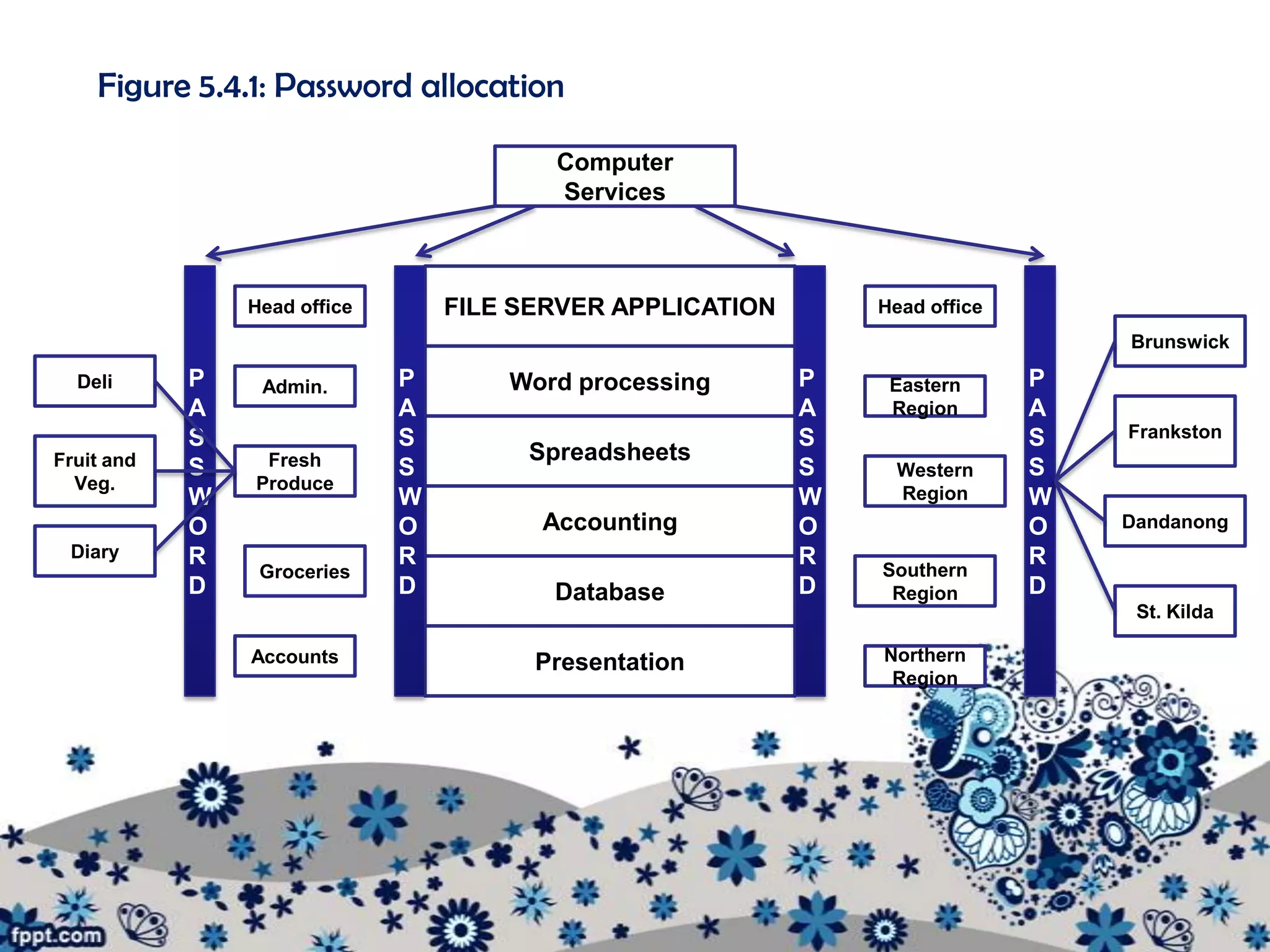
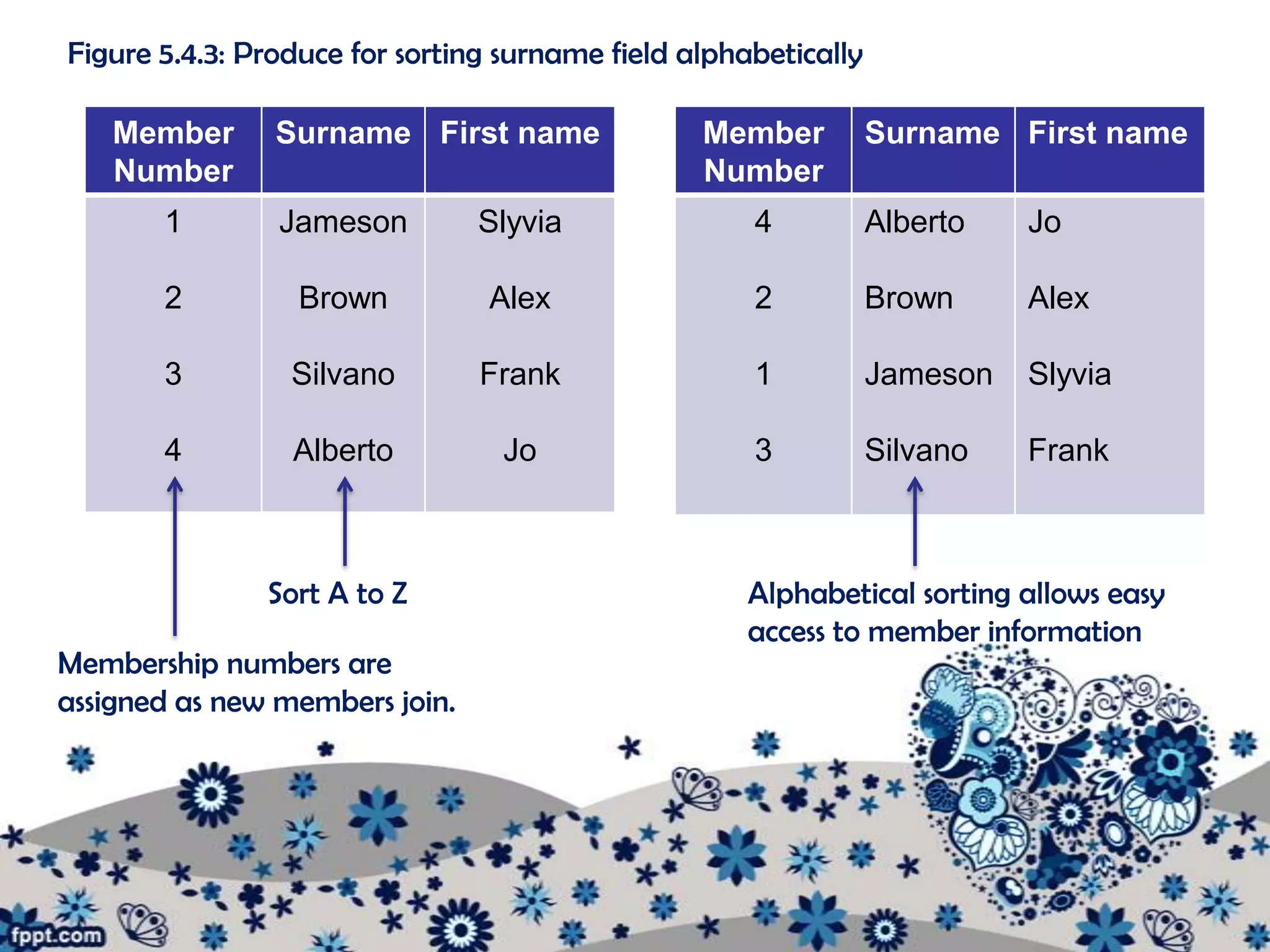
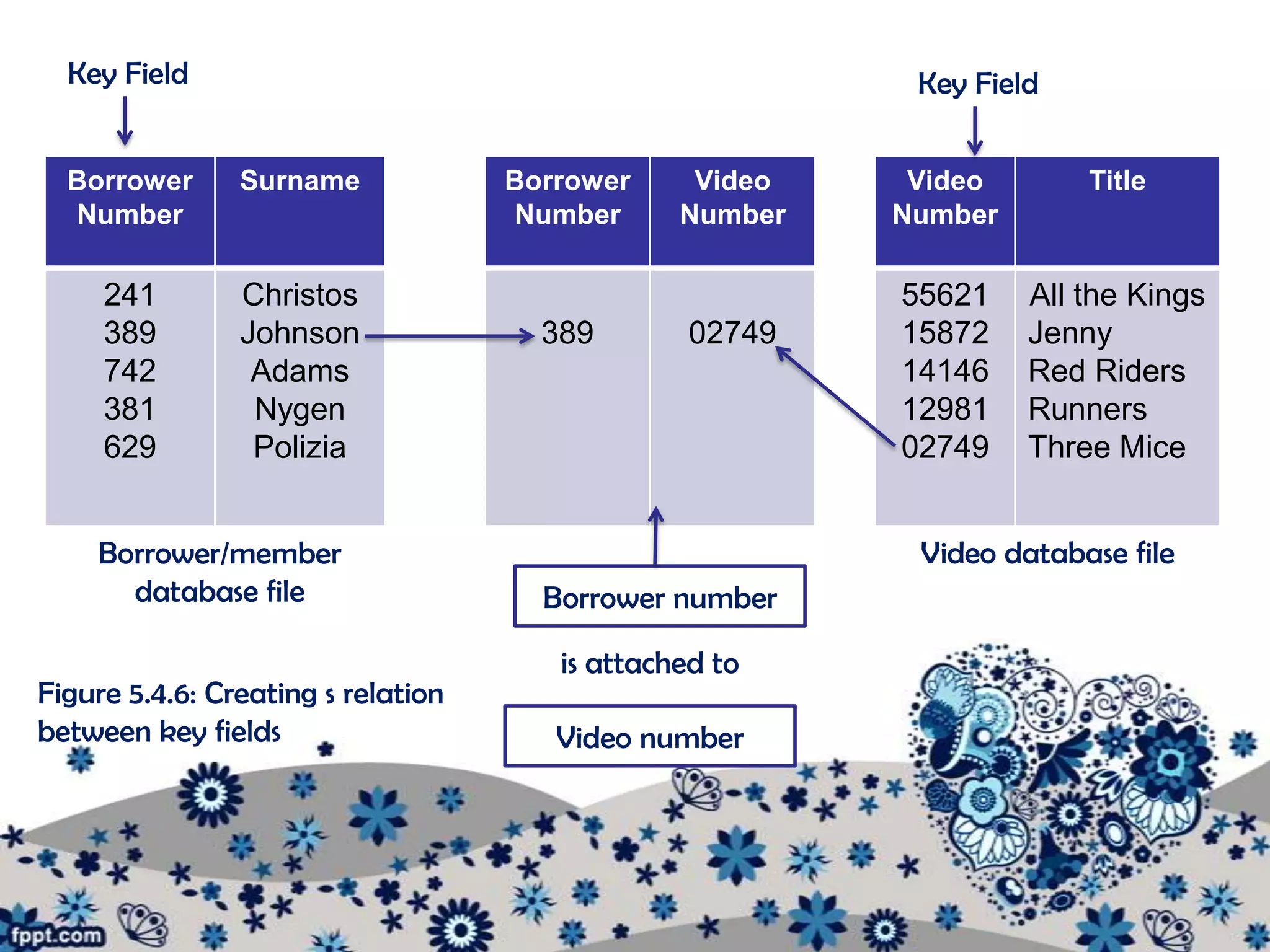
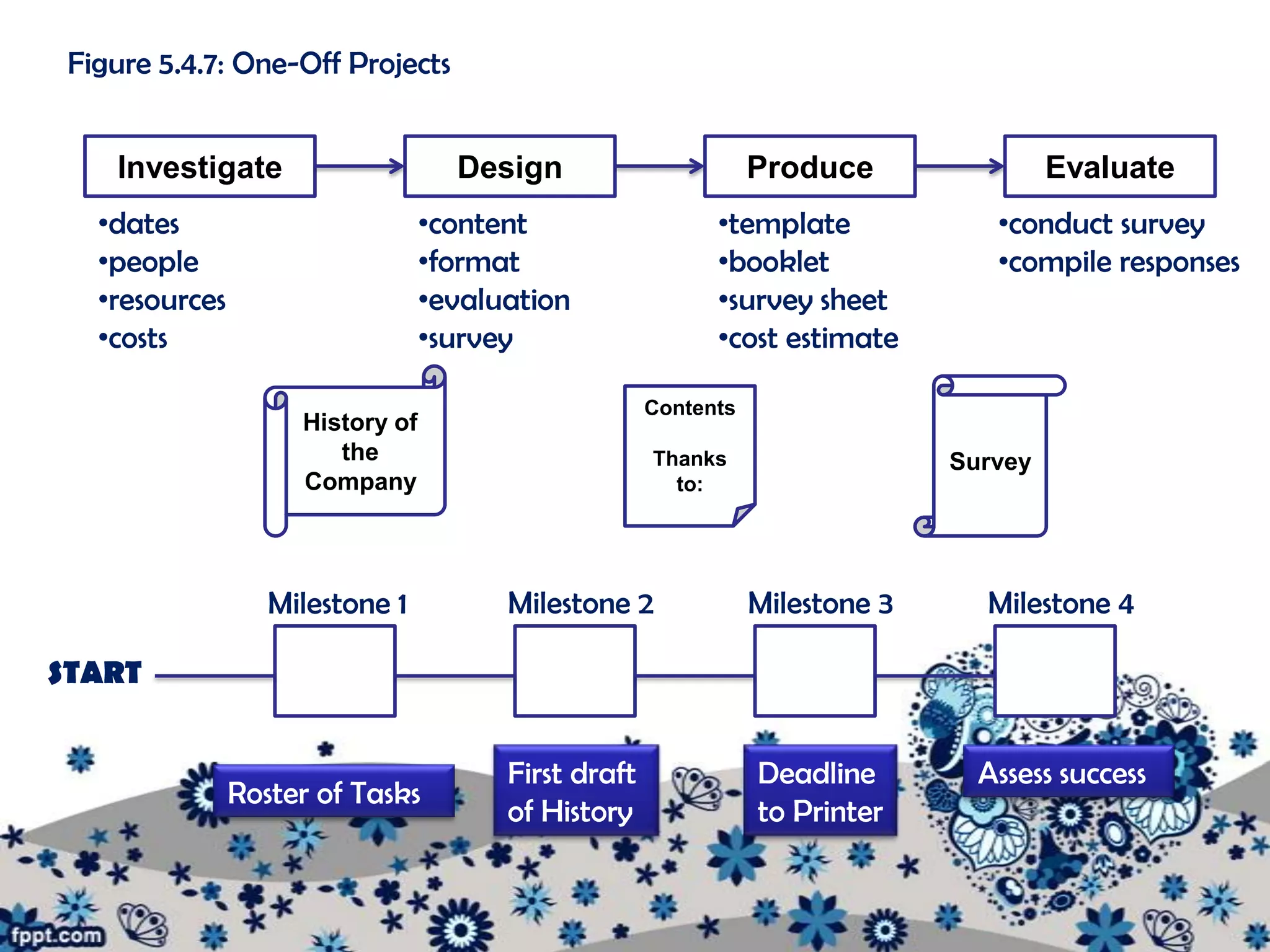
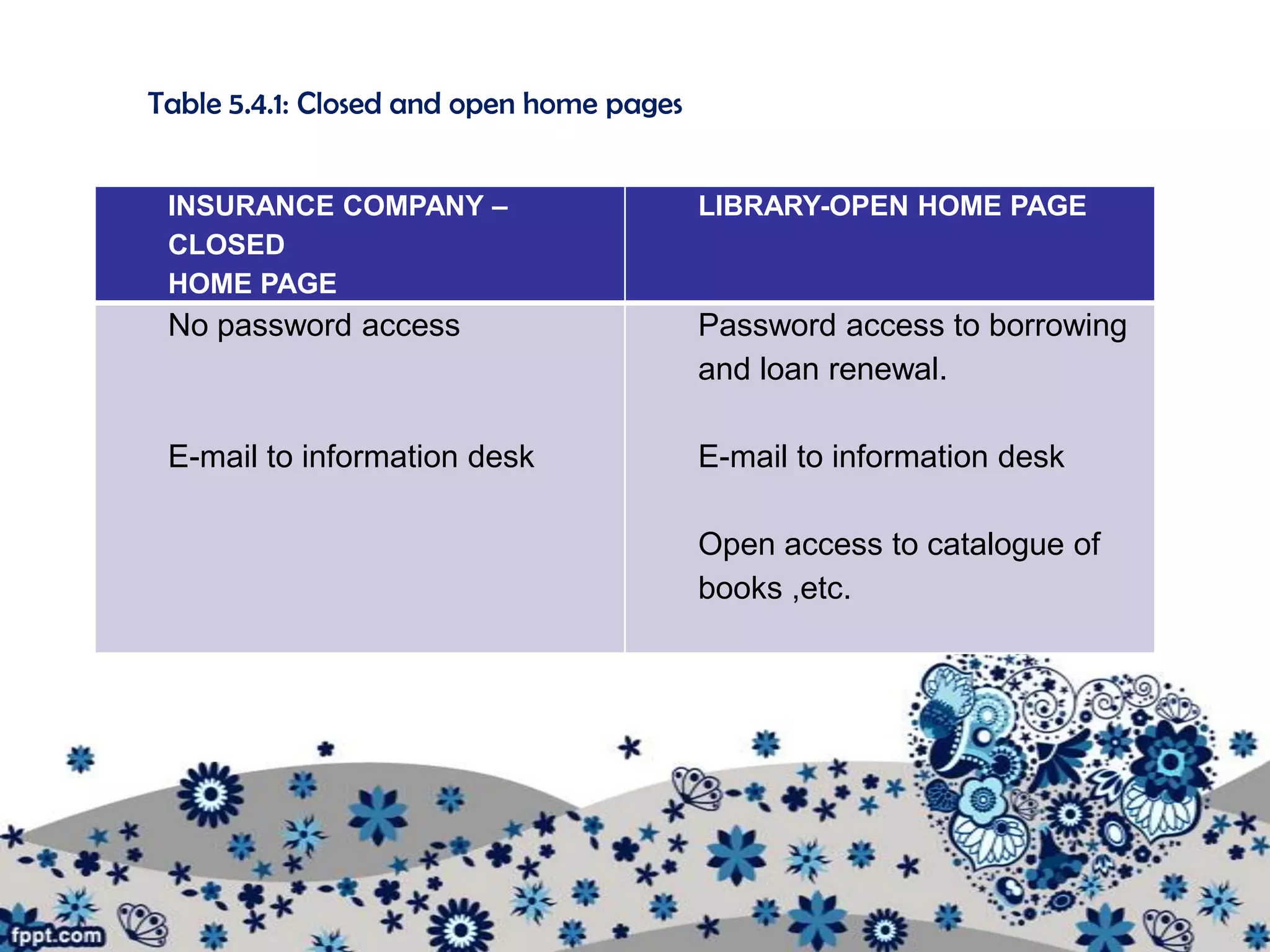
The document outlines various procedures for managing information in multi-user environments. It discusses setting information path flows, implementing records management systems, prioritizing jobs, and ensuring privacy and assigning passwords. Specifically, it provides examples of using data flow diagrams to show information paths, sorting data alphabetically for easy access, using relational databases to link borrower and item records, and setting different access permissions for files, programs, and networks using passwords.