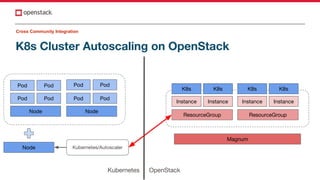
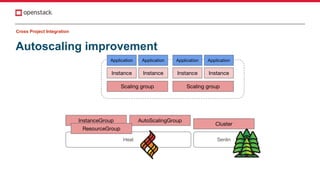
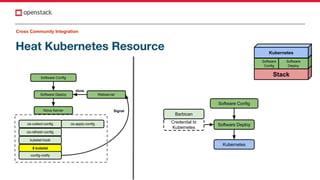
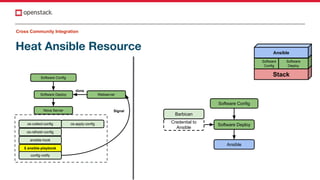
The document discusses improvements in OpenStack integration for application developers, focusing on cross-site, project, and community integration. It highlights features like application credentials for scoped authentication, pre-signed URLs for limited resource access, and self-healing capabilities with Heat. The need for enhanced collaboration across teams and projects to streamline application management in cloud environments is emphasized.






![Application Credentials [more]
clouds:
openstack:
auth:
auth_url: https://cloud.example.com/identity/v3
username: "Rico"
user_domain_name: "openstack.de"
application_credential_name:
"volume_backups_001"
application_credential_secret: "{Credential ID}"
region_name: "RegionOne"
interface: "public"
identity_api_version: 3
auth_type: "v3applicationcredential"
Cross Site/Platform Integration
An application credential is a scoped auth method
that a user creates to delegate a subset of their role
assignments on a single project to something else -
whoever or whatever possesses knowledge of the
identifier and the secret belonging to the application
credential.
● Has its own secret
● Can only access one project, no matter how
many projects the user is in
● Can have all or a subset of the roles the user
has on that project
● Is user-lived - when the user is deleted, the app
credential dies
● User can have many](https://image.slidesharecdn.com/8d9cf173-d41c-4177-a936-e38bdc9b5884-181120104053/85/Improvements-in-OpenStack-Integration-for-Application-Developers-7-320.jpg)

![server:
type: OS::Nova::Server
properties:
...
alarm_queue:
type: OS::Zaqar::Queue
error_event_alarm:
type: OS::Aodh::EventAlarm
properties:
event_type: compute.instance.update
query:
- field: traits.instance_id
value: {get_resource: server}
op: eq
- field: traits.state
value: error
op: eq
alarm_queues:
- {get_resource: alarm_queue}
alarm_subscription:
type: OS::Zaqar::MistralTrigger
properties:
queue_name: {get_resource: alarm_queue}
workflow_id: {get_resource: autoheal}
input:
stack_id: {get_param: "OS::stack_id"}
root_stack_id:
if:
- is_standalone
- {get_param: "OS::stack_id"}
- {get_param: "root_stack_id"}
autoheal:
type: OS::Mistral::Workflow
properties:
description: >
Mark a server as unhealthy and commence a stack update
to replace it.
input:
stack_id:
root_stack_id:
type: direct
tasks:
- name: resources_mark_unhealthy
action:
list_join:
- ' '
- - heat.resources_mark_unhealthy
- stack_id=<% $.stack_id %>
- resource_name=<%
env().notification.body.reason_data.event.traits.where($[0] =
'instance_id').select($[2]).first() %>
- mark_unhealthy=true
- resource_status_reason='Marked by alarm'
on_success:
- stacks_update
- name: stacks_update
action: heat.stacks_update stack_id=<% $.root_stack_id
%> existing=true
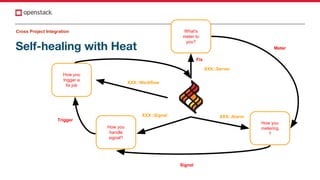
Self-healing with Heat](https://image.slidesharecdn.com/8d9cf173-d41c-4177-a936-e38bdc9b5884-181120104053/85/Improvements-in-OpenStack-Integration-for-Application-Developers-12-320.jpg)

![OpenStack site A
Multi-Cloud Orchestration
Cross Site/Platform Integration
Stack2Stack
Stack2
OpenStack site B
resources:
app_stack_at_site_B:
type: OS::Heat::Stack
properties:
context:
credential_secret_id: {Barbican Secret ID}
openstack secret store -n site-b-cred --payload
'{
"auth_type": "v3applicationcredential",
"auth": {
"auth_url": "URL",
"application_credential_id": "Credential ID",
"application_credential_secret": "sec"},
"roles": ["admin"],
"project_id": "Project_ID"
}'](https://image.slidesharecdn.com/8d9cf173-d41c-4177-a936-e38bdc9b5884-181120104053/85/Improvements-in-OpenStack-Integration-for-Application-Developers-15-320.jpg)