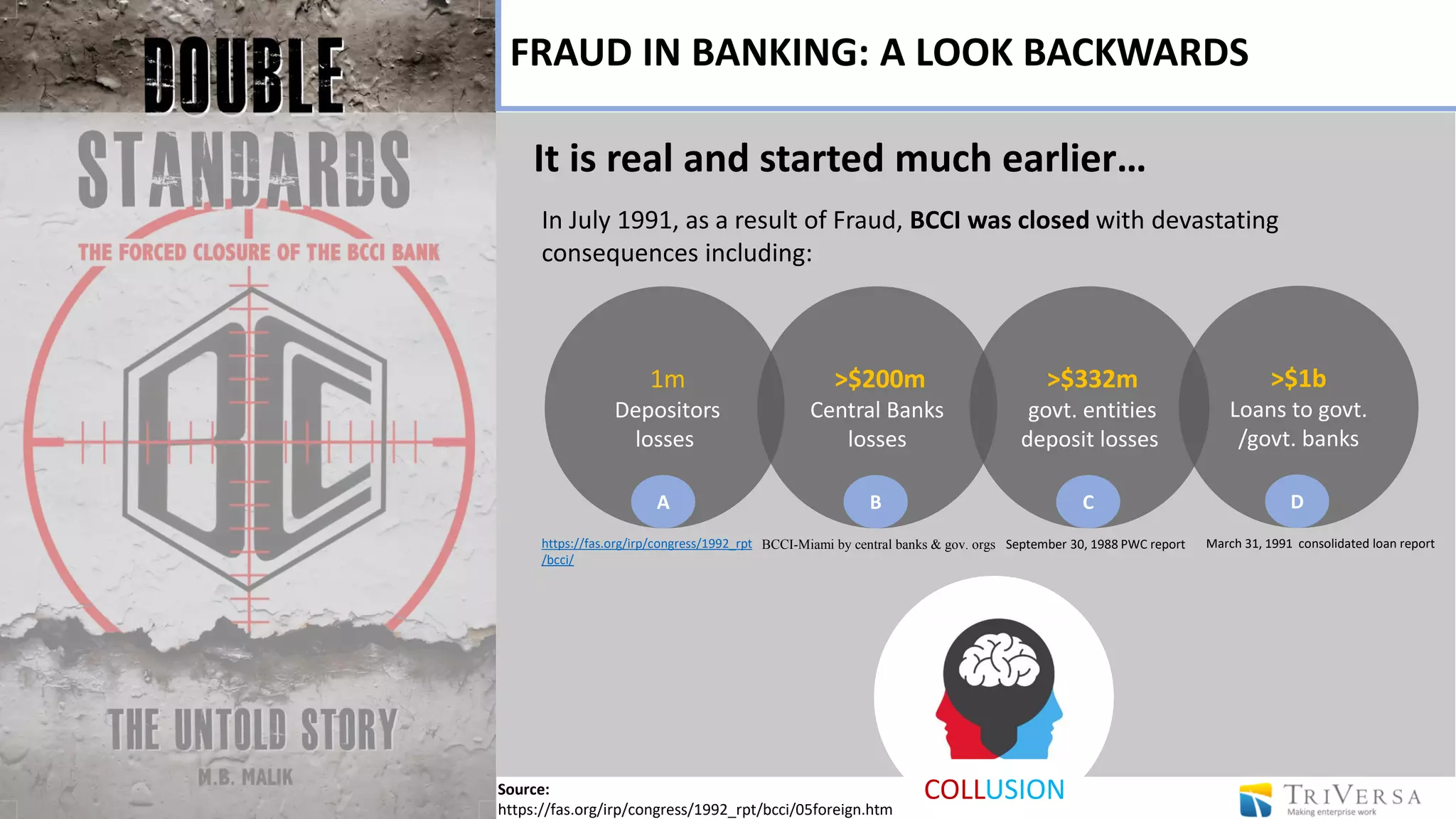
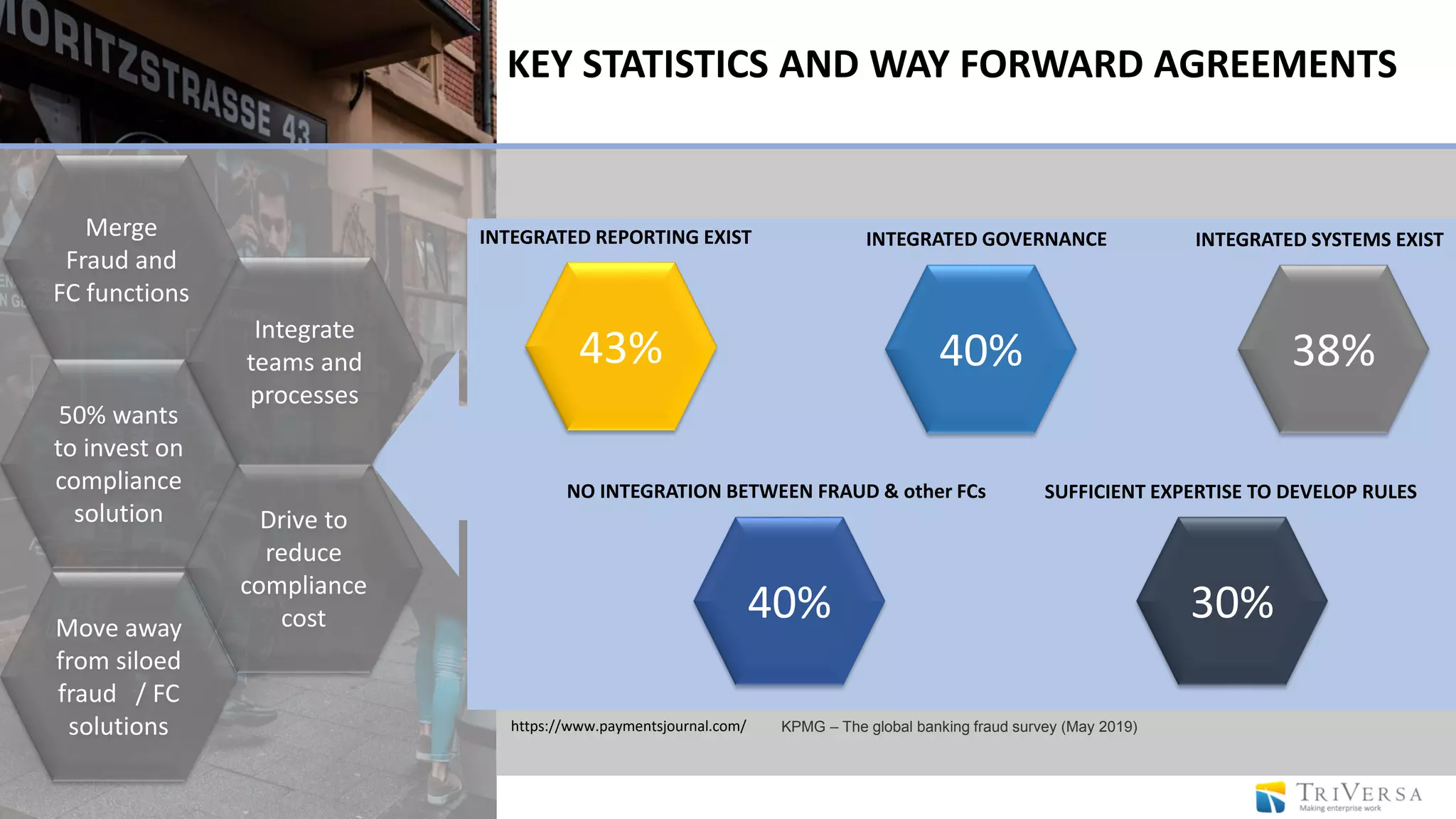
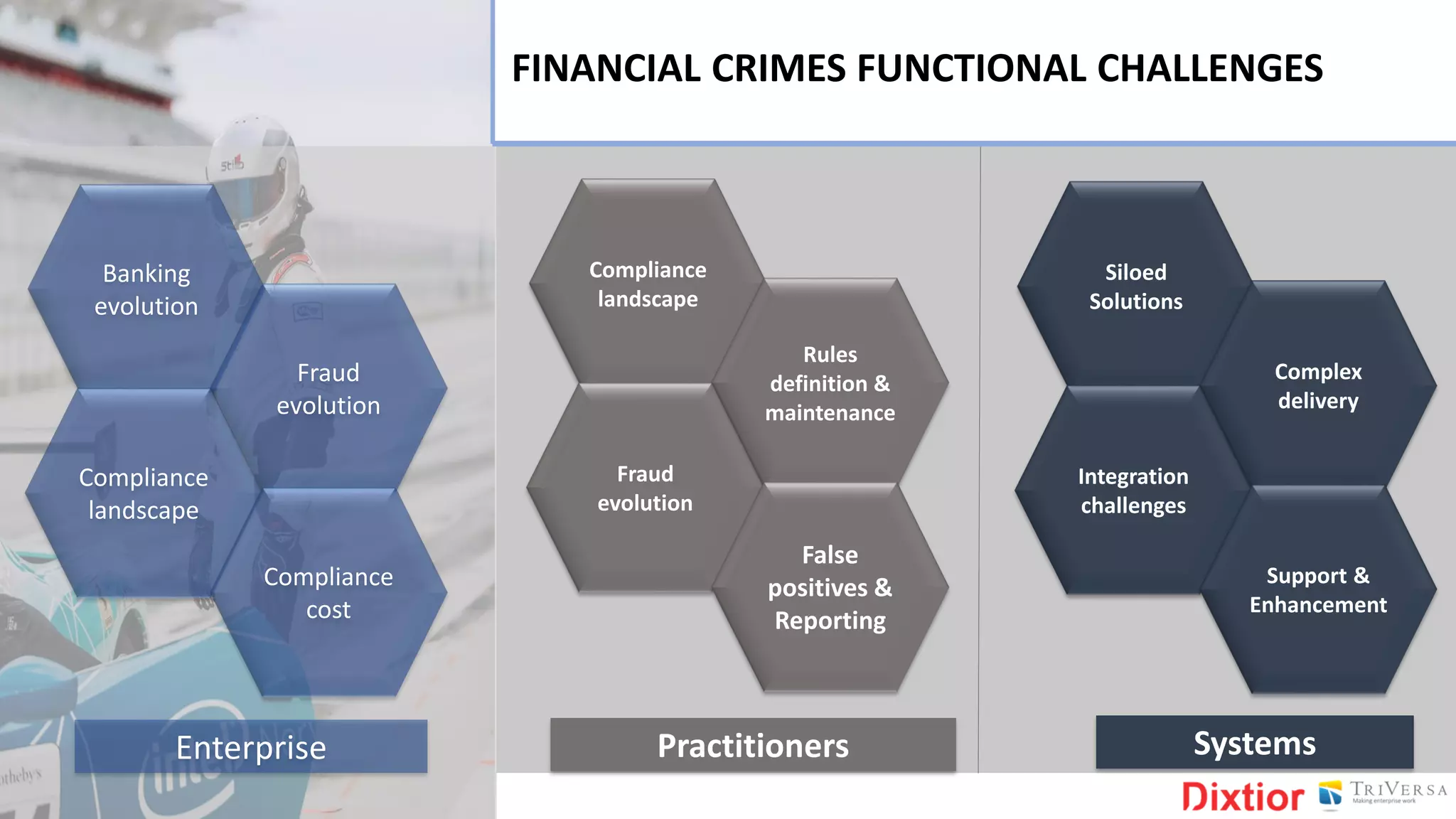
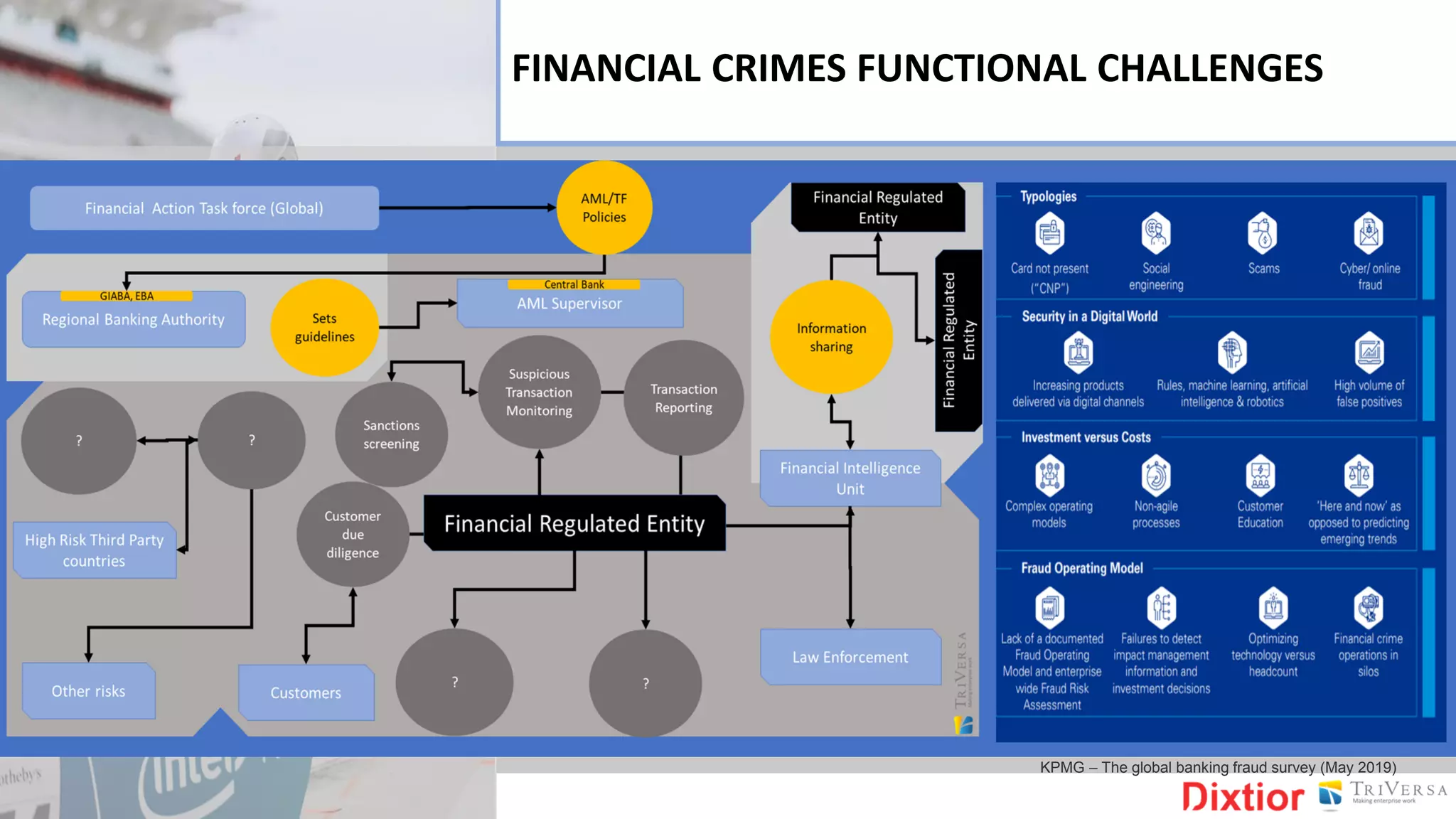
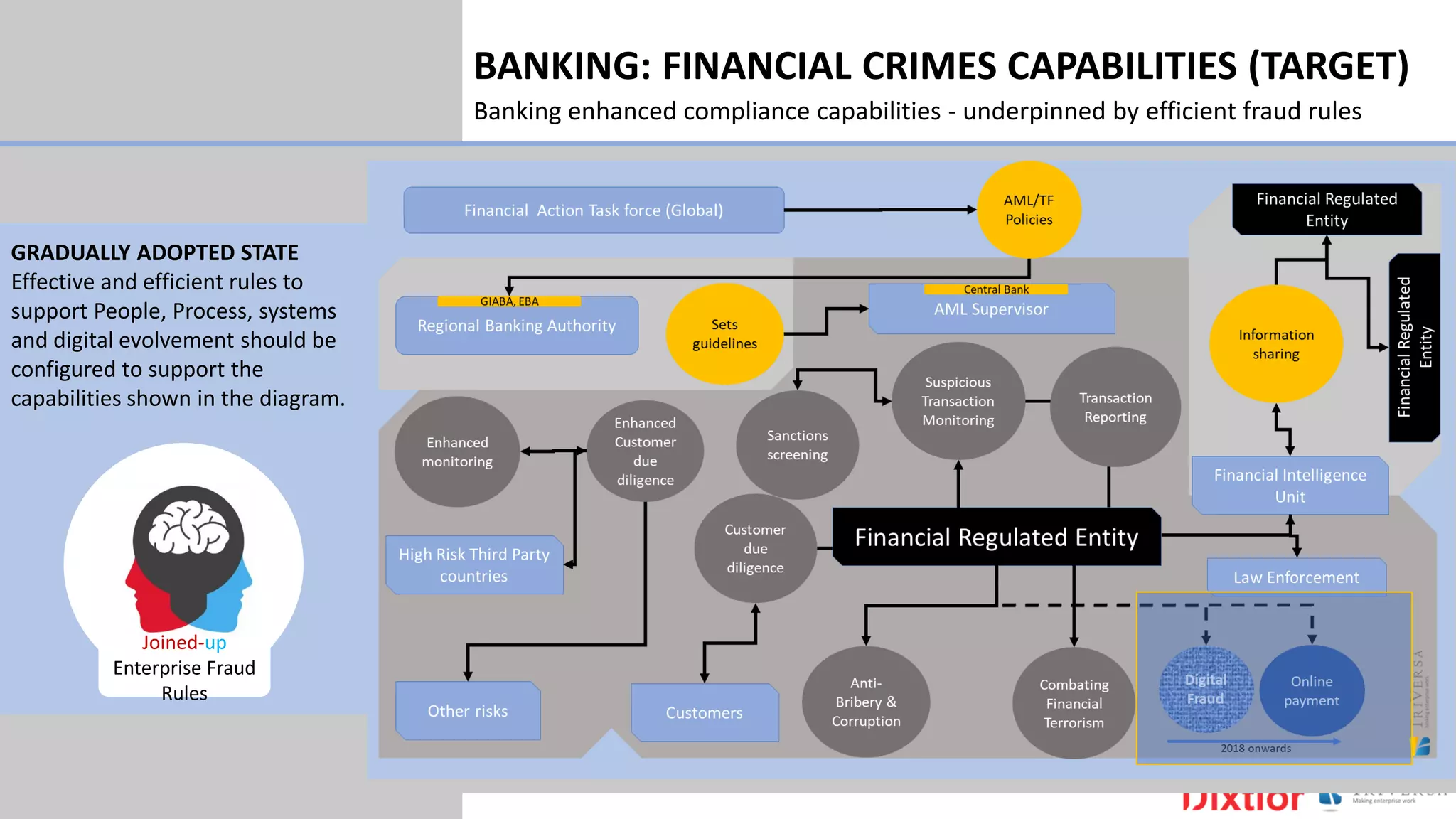
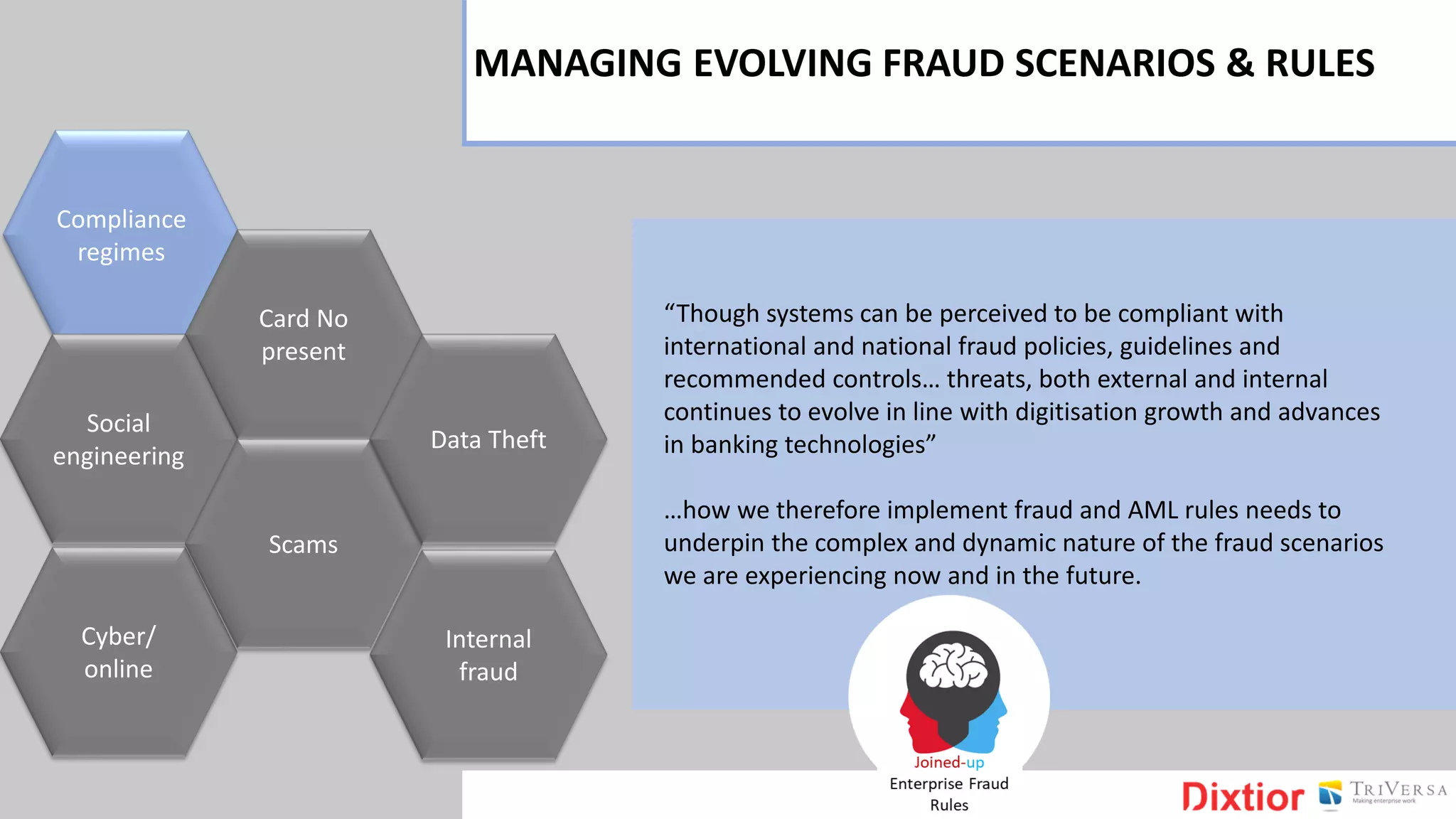
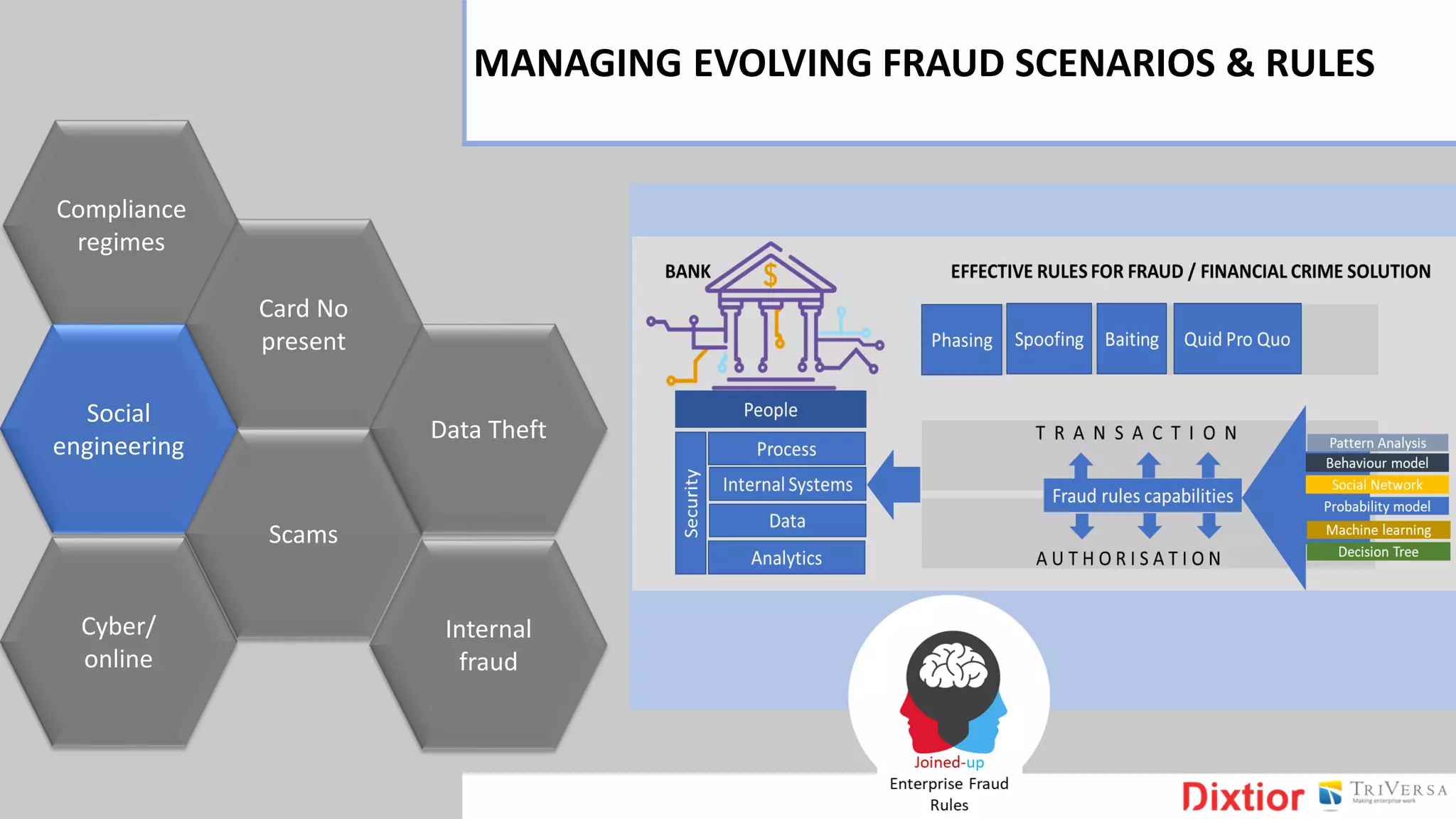
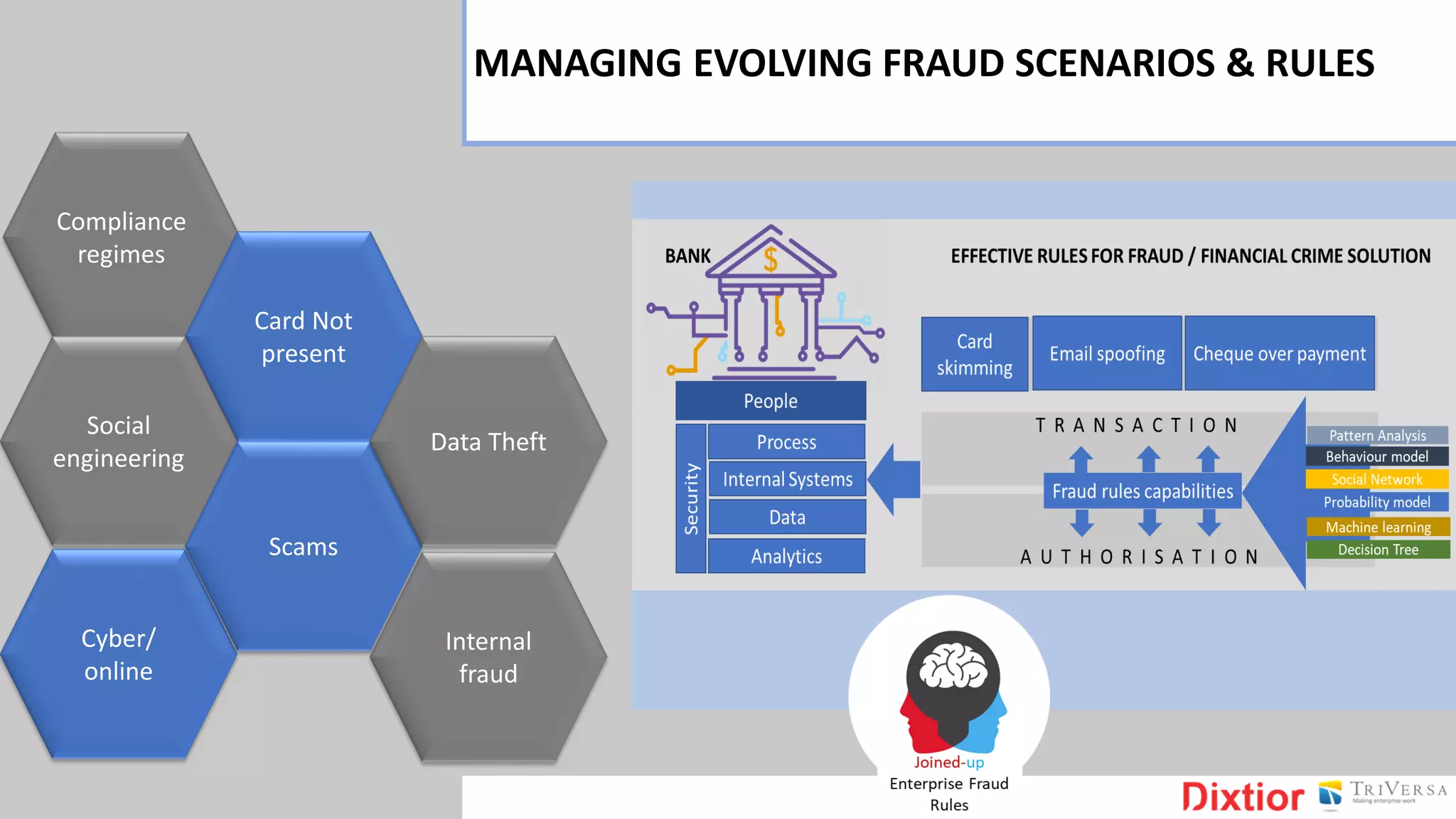
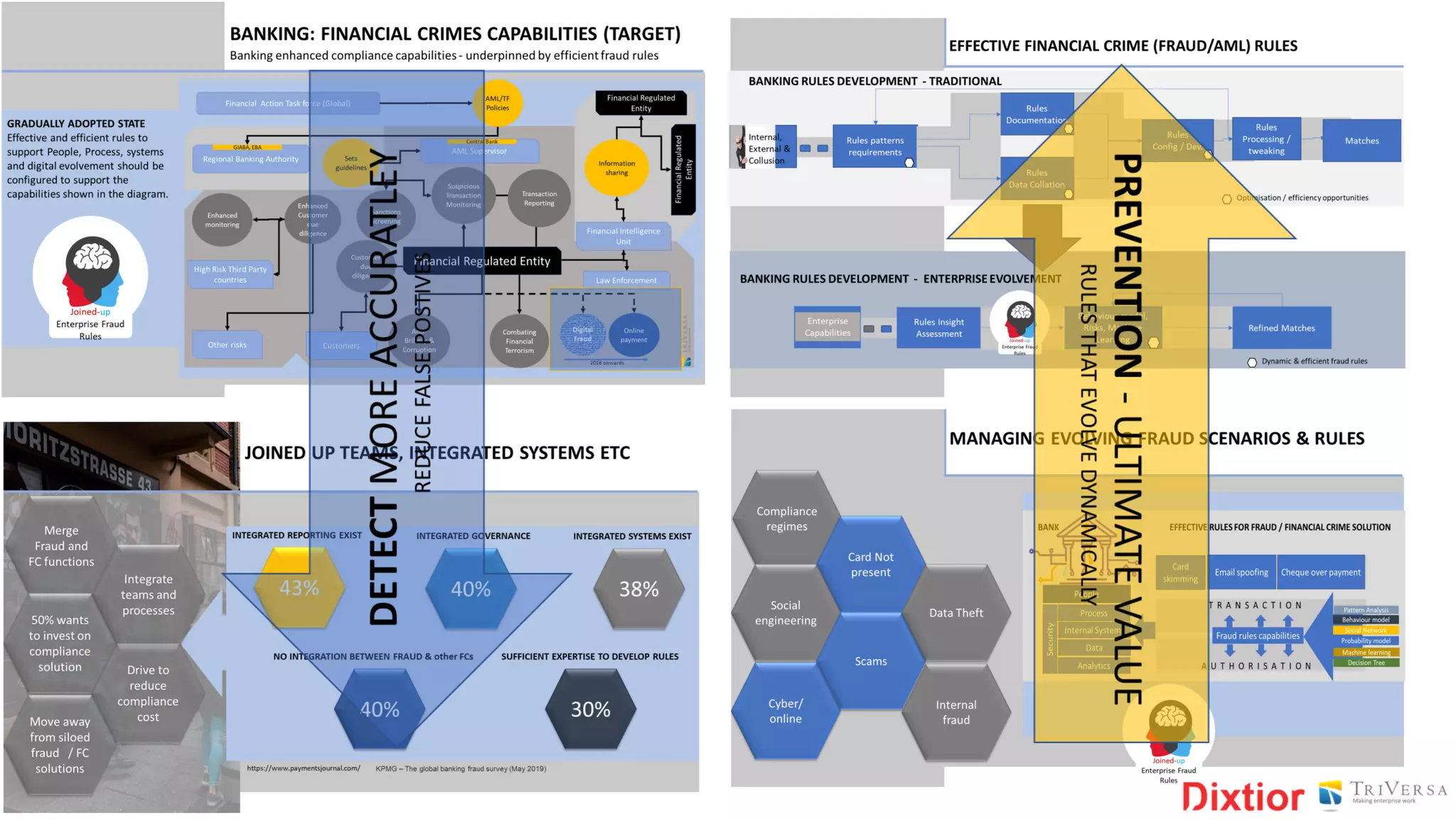
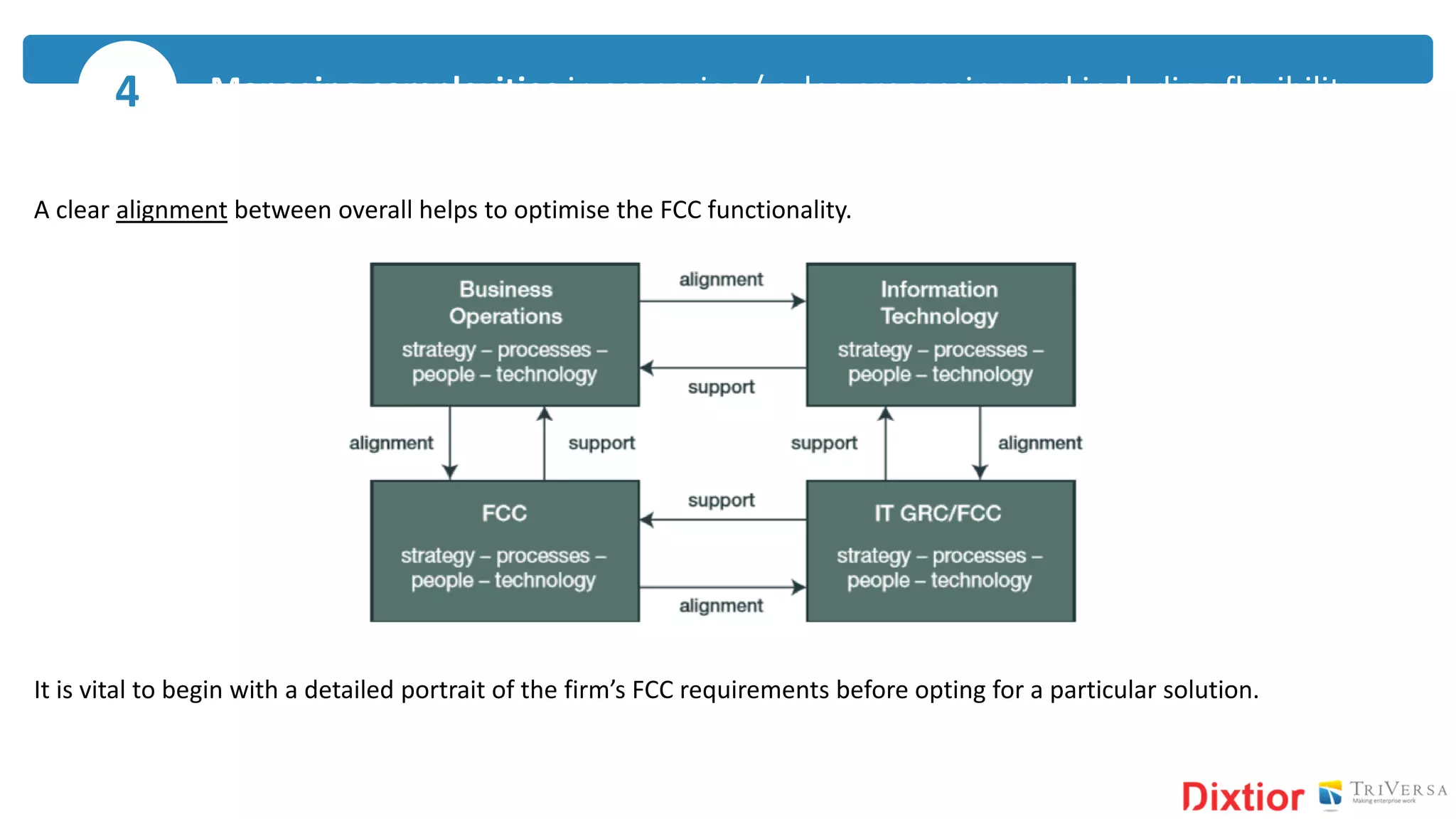
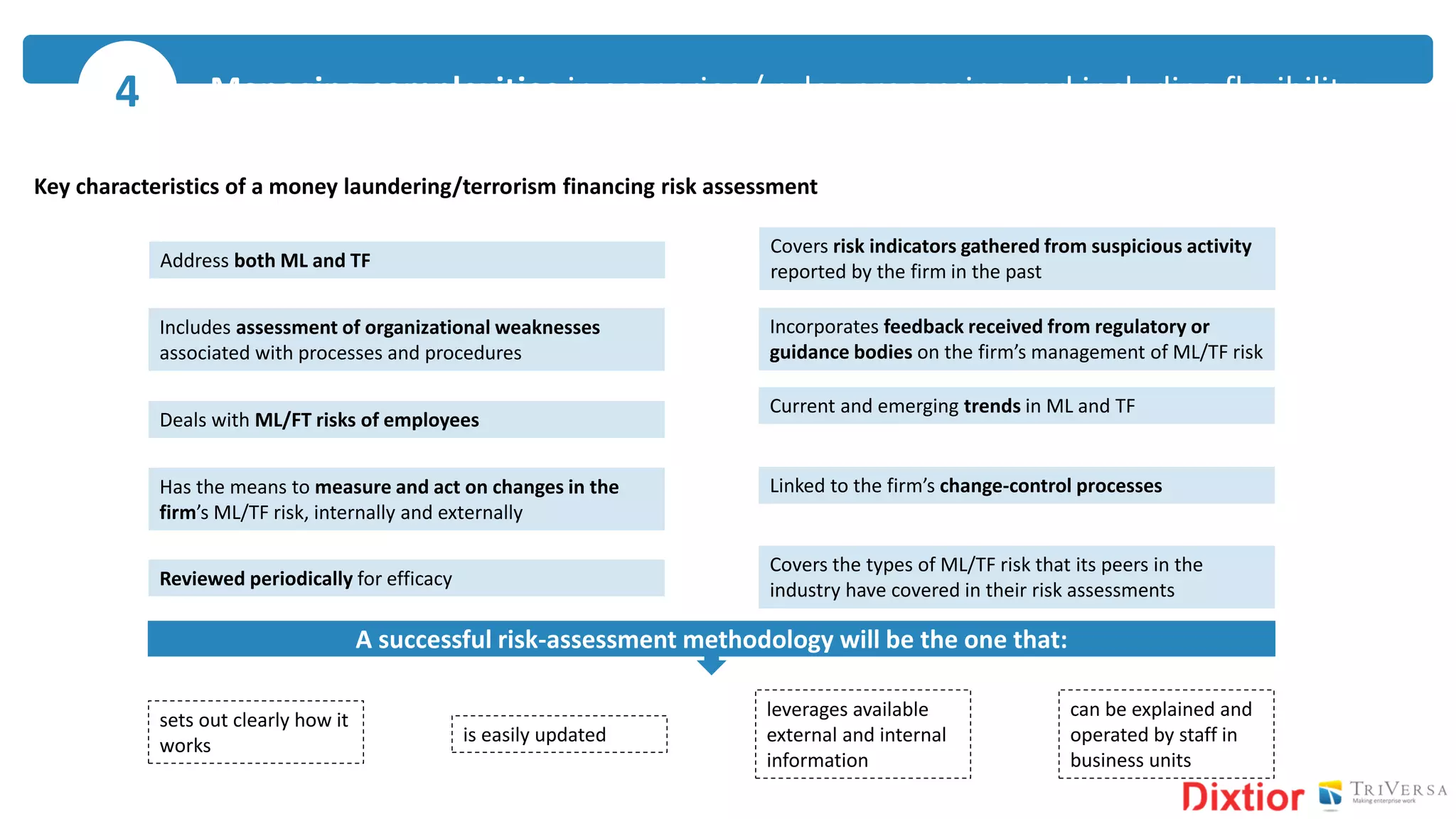
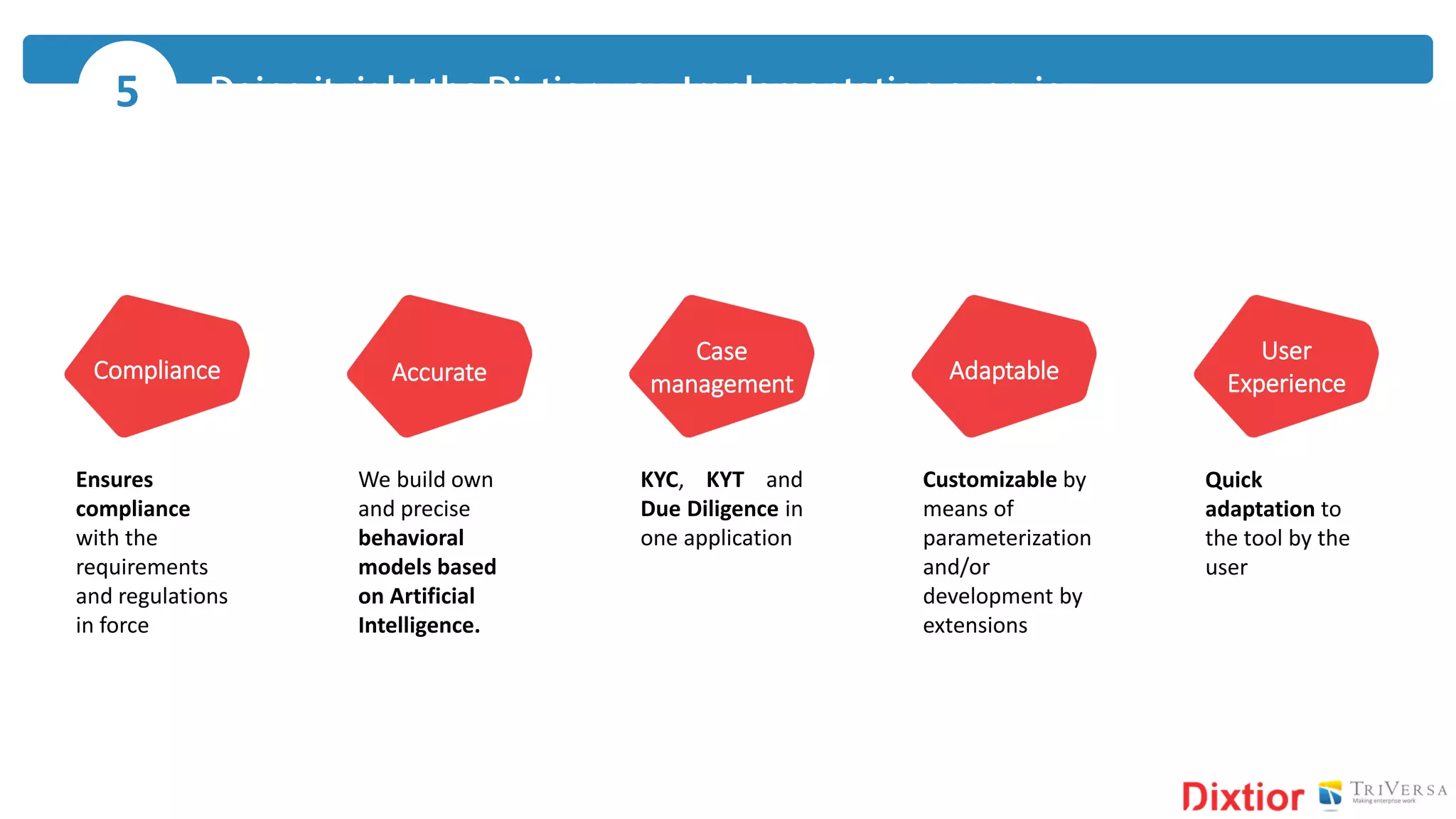
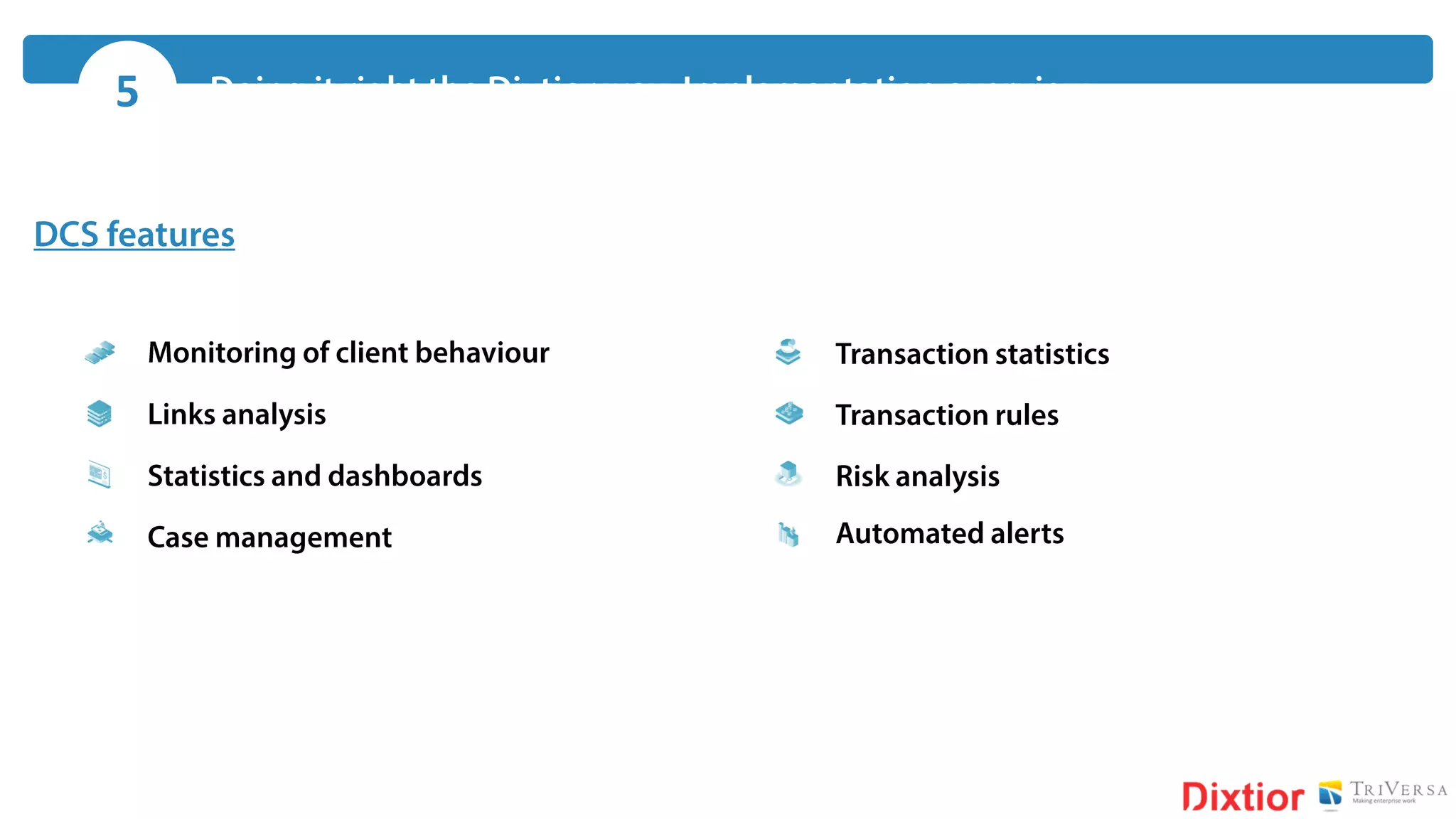
The document discusses the history and impact of banking fraud, particularly highlighting the fallout from the closure of BCCI in 1991 due to fraud that resulted in catastrophic financial losses. It emphasizes the importance of integrating compliance and fraud management solutions in banking to adapt to evolving financial crime threats. Additionally, it outlines best practices for conducting money laundering and terrorism financing risk assessments in financial institutions.